The Ultimate Java Jarsigner Guide: How Does It Work and How Can I Use It?

Explore and learn the power of Java Jarsigner. Master this code signing tool to reassure your customers that your Java ARchive files are secure, and achieve optimal malware and tampering protection
Expel’s latest report further underscores why it’s essential to adequately protect code from malware and tampering. Over half of all malware attacks investigated by the cybersecurity company in 2023 represented an “immediate and substantial risk” to organizations and their users alike.
Are cybercriminals sharpening their tradecrafts? No doubt. This is why organizations must keep on adapting their security posture. Signing your Java files is one such way to do this. Leveraging the power of Java Jarsigner code signing can effectively protect your Java files in this eternal cat-and-mouse game.
In this detailed guide, we’ll provide:
- A brief overview of what Jarsigner is and what it helps you do,
- Advice and techniques to help you get the most out of Jarsigner features,
- A clear, no-nonsense explanation of how it works, and
- A practical example of how to use this code signing tool like a pro.
Check it out now and become a Java Jarsigner ace in no time.
What Is Java Jarsigner? Jarsigner at a Glance
Jarsigner.exe is a multiplatform tool that allows you to digitally sign (and timestamp) any Java ARrchive (hence, JAR) file (i.e., a single ZIP file containing a Java application’s code) described in the table below:
| Characteristics | .jar (Java ARchive) | .war (Web Application Resource or Web Application aRchive) | .ear (Enterprise Application aRchive) | .sar (Service Archive) |
| Files Included | All components required to create a self-contained executable Java application (e.g., Java source codes, XML configuration data, manifests, JSON data files). | All web application components that can be deployed on a servlet/JSP container (e.g., .jar files, Servlet, JSP, XML, static web pages, CSS and JavaScript files). | Application modules and a metadata directory (META-INT), including one or more deployment descriptors in the form of XML files. | A JBoss service definition file (META-INF or jboss-service.xml) and other JBoss resources. |
| Purpose | Used for stand-alone Java applications and linkable libraries. | Distributes all files and resources that are part of a web application. | Employed to deploy modules on an application server simultaneously. | Used to deploy separate service components in JBoss application servers. |
| Benefits | Enables developers to deploy an entire application in a single request through Java Runtime Environment (JRE). | Makes web applications testing and deployment a child’s game. | Contributes to a coherent and seamless development of enterprise applications. | Allows you to create and run independent service components in JBoss. |
Fair enough, but how does Jarsigner.exe work?
Java Jarsigner: How Does It Work?
To sign a Java archive file, you’ll need Jarsigner.exe installed on your device and a secure hardware token containing:
- A code signing certificate purchased from a trusted certificate authority (CA).
- Your cryptographic key pair (public and private keys).
Java digital signatures leverage the power of public key cryptography to assert the publisher’s identity and confirm the authenticity and integrity of a code. During the signing process, the code’s hash value is encrypted with the developer’s private key. This serves as a checksum to convey the software’s integrity (i.e., that it hasn’t been altered since the publisher signed it).
Subsequently, it’s signed, timestamped, and bundled with the code signing certificate. The user’s client will then use the author’s public key to validate the signature and identity of the publisher. How? By comparing the newly generated hash with the one included in the bundle. If the hashes don’t match, the user will be alerted.
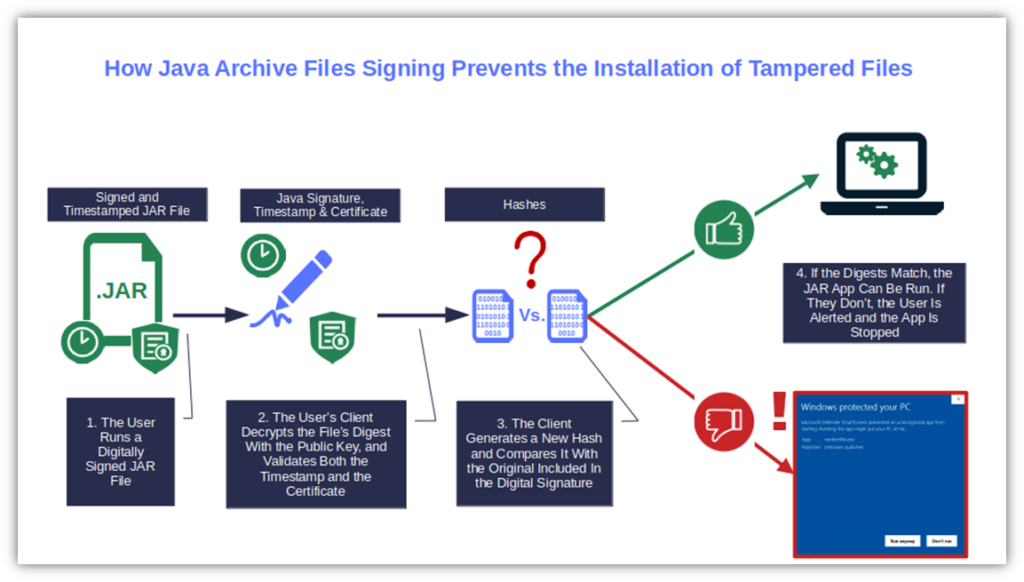
Hence, once signed, your application, applet, or Java library will have an additional layer of security against malware and unauthorized modifications. This is the case so long as you used a trusted code signing certificate issued by a known CA.
This is an extremely important point. Every time a CA issues a code signing certificate, it vouches for the identity of the entity that requested it. To accomplish it, the CA follows a more or less thorough (depending on the certificate chosen) validation process.
Self-signed certificates don’t have that kind of trust (nor should they). They’re issued by the developer/software publisher without any independent authenticity check. Anyone can forge them with no effort. Thus, all major browsers and OSes will still consider self-signed files unsigned. These are the main reasons you can use them for testing purposes only.
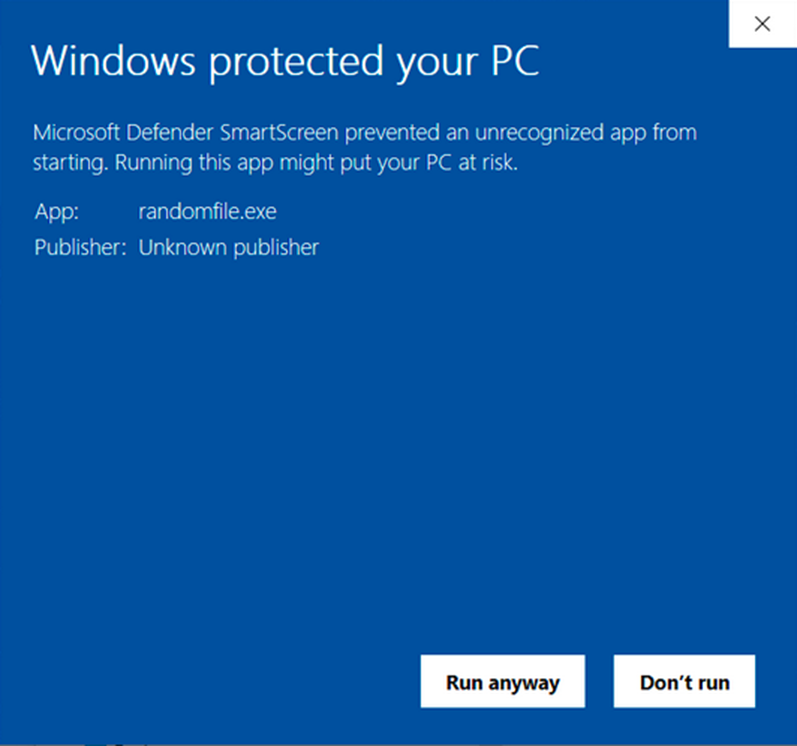
Image caption: This is the warning a user will see when trying to run a .jar file (or any file) that’s been signed with a self-signed certificate or hasn’t been solved with any code signing certificate at all.
How to Sign a Java File on Windows 10 With Java Jarsigner In 4 Steps
Now that you know Jarsigner nearly like the back of your hand, let’s put this abstract and theoretical knowledge into practice with a real-world scenario.
Imagine you’ve just bought a code signing certificate and completed the one-time secure token setup operations. Yes! Now you’re ready for action. And what better opportunity to inaugurate the certificate than to digitally sign the application you want to distribute as a single, executable .jar file?
Let’s do it together!
If you don’t have a Java code signing certificate yet, though, you can get one easily through CodeSigningStore.com.
Save Up to 21% on a Java Code Signing Certificate
Digitally sign unlimited JAR files and applications for as little as $211.46/year.
1. Check if Java Jarsigner Is Already Installed on Your Device
Did you build your Java app/applet using Java Development Kit (JDK)? Jarsigner.exe is embedded into it.
- Find out where it’s located on your machine (it’ll come in handy later in the process).
- Ensure you have administrative permission to access and make changes to the JDK bin folder on your device.
It isn’t installed? No worries — you can download and install it in three simple steps.
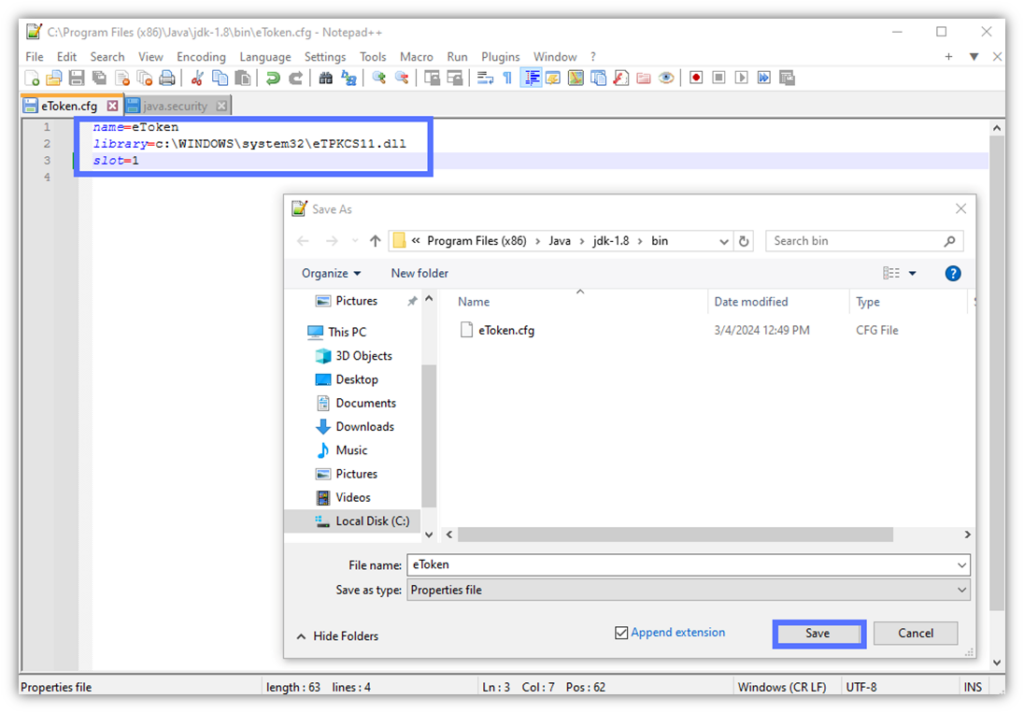
2. Enable JDK to Access Your Secure Token
- Open Notepad++ and type the three lines below:
name=eToken
library=c:\WINDOWS\system32\eTPKCS11.dll
slot=1Pro Tip: Do you know your device’s slot number? Replace the “1” with the digit related to your machine. If you don’t know your slot number, start with 0 and work your way up one number at a time (e.g., slot=0, slot=1, slot=2, etc.).
If you’re running into the error “java.security.KeyStoreException: PKCS11 not found” then check out our other resource that can help.
- Name the file “eToken.cfg” and save it in your JDK bin folder (e.g., C:\Program Files\Java\jdk-21\bin). Here’s what it’ll look like if you installed JDK in the default path:
3. Find Your Private Key’s Alias
- Open the command line (cmd) as administrator.
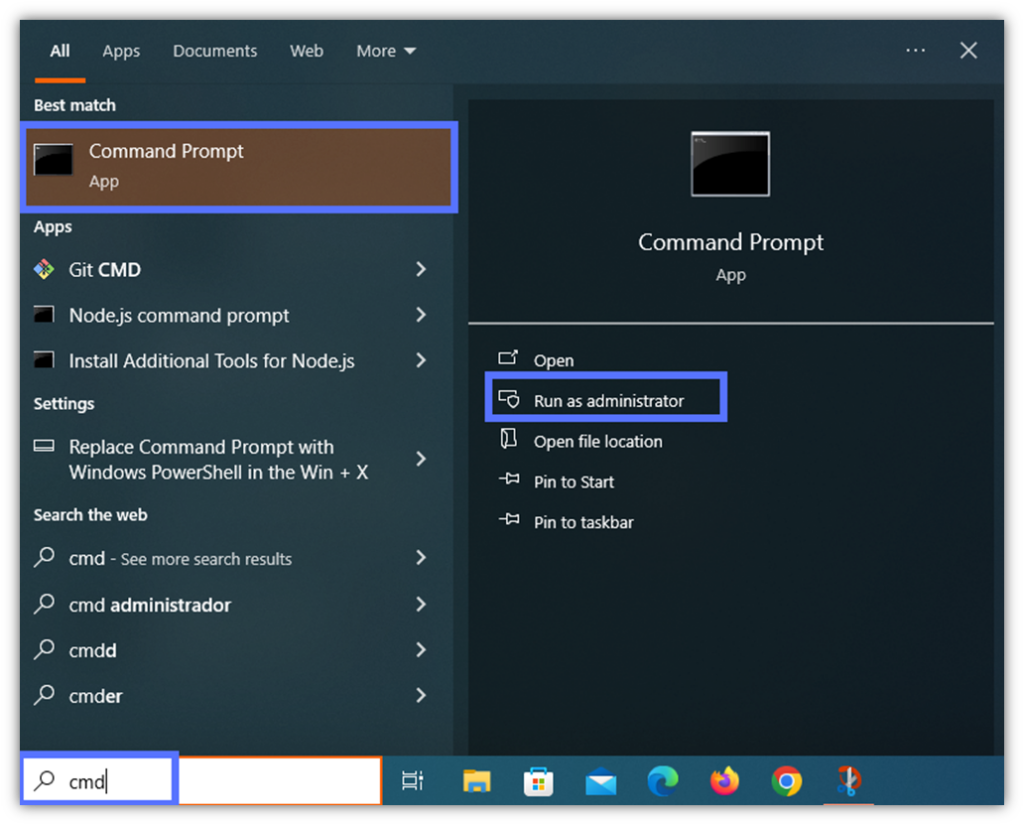
- Navigate to the JDK’s bin folder using the cd command and hit Enter.
cd C:\file_path_to_java_JDK_folder\Java\jdk-[version]\binHere is an example of the cd command in action:
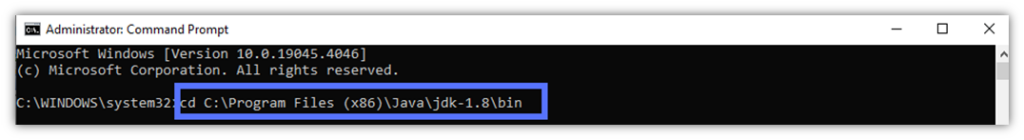
- Type the script below to view your private key’s alias:
keytool -list -keystore NONE -storetype PKCS11 -providerclass sun.security.pkcs11.SunPKCS11 -providerArg eToken.cfg- Input your token password as shown in the example field below and click Enter.
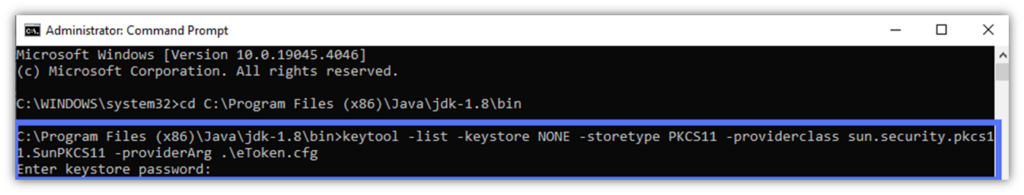
Are you typing your password, but nothing is displaying on the screen? Don’t worry, this is normal; it’s just a security measure to prevent someone from reading and stealing your password.
Pro Tip: Are you getting an error starting with: “jarsigner error: java.lang.ClassNotFoundException” or “jarsigner error: java.lang.RuntimeException“? Download and use a 32-bit (i.e., x86) version of the JDK. You won’t even need to uninstall a more recent JDK version that you may have on your device.
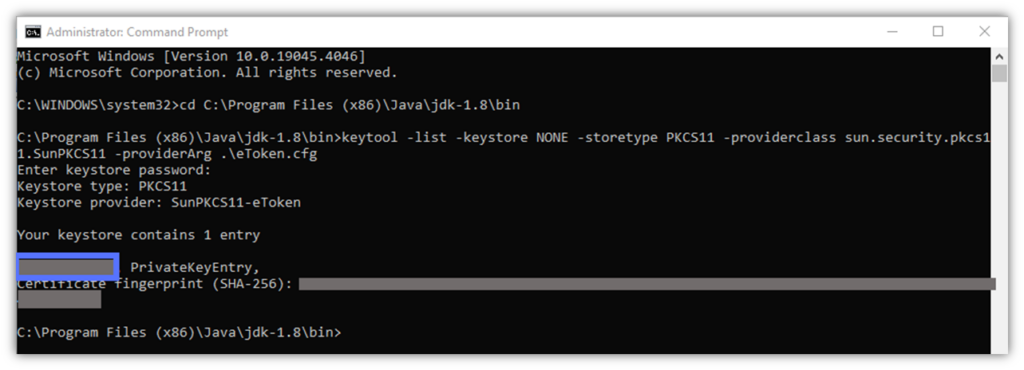
Bingo. The Jarsigner’s one-time setting operations are done and dusted. Keep the command prompt open, though. You’ll need it for the next, final step.
4. Sign and Timestamp Your .Jar File With Java Jarsigner Like a Pro
The hour has come to add a digital signature and timestamp to the app. And guess what? All you need is a single command.
- In the cmd prompt window, key in the following:
jarsigner -verbose -keystore NONE -storetype PKCS11 -tsa http://timestamp.digicert.com -providerClass sun.security.pkcs11.SunPKCS11 -providerArg ./eToken.cfg C:\Users\file_path_to_your_jar_file\YourFile.jar "Private Key Alias Name"Here is a quick look at what it looks like for us when using a DigiCert code signing certificate and timestamp. The last grayed-out bit is where your private key alias name goes.
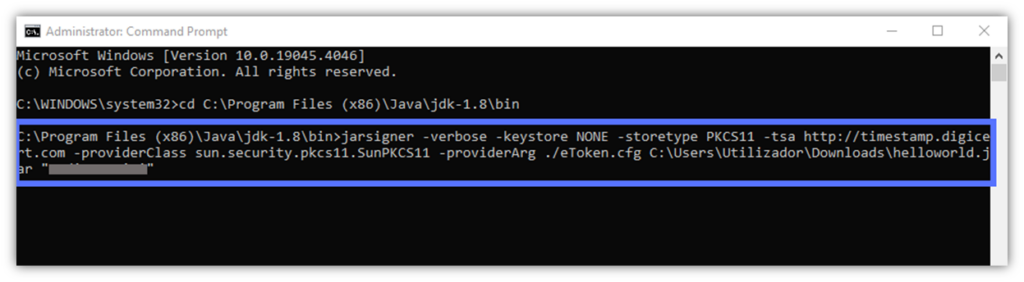
- Click Enter. At the prompt, input your password and hit Enter again.
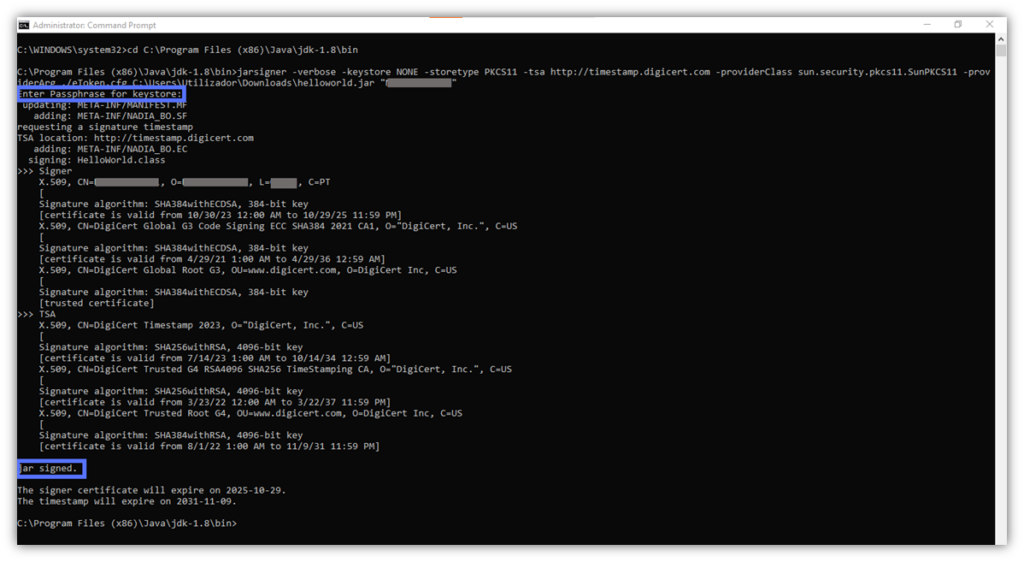
Boom! Done. You’ve now signed your .jar file with Java Jarsigner.
How to Verify a Java Jarsigner Signature in Less Than 15 Seconds
You’re a Jarsigner grandmaster now, and like all real pros, you always double-check everything you do, right? Jarsigner.exe lets you, with a simple script:
- Check the validity of a Java file signature,
- Display the algorithms used for the signature, the timestamp, and
- Confirm that the code hasn’t been tampered with.
In the same command prompt window, type the following and hit Enter:
jarsigner -verify -verbose -certs <File_Path>This will display the following information:
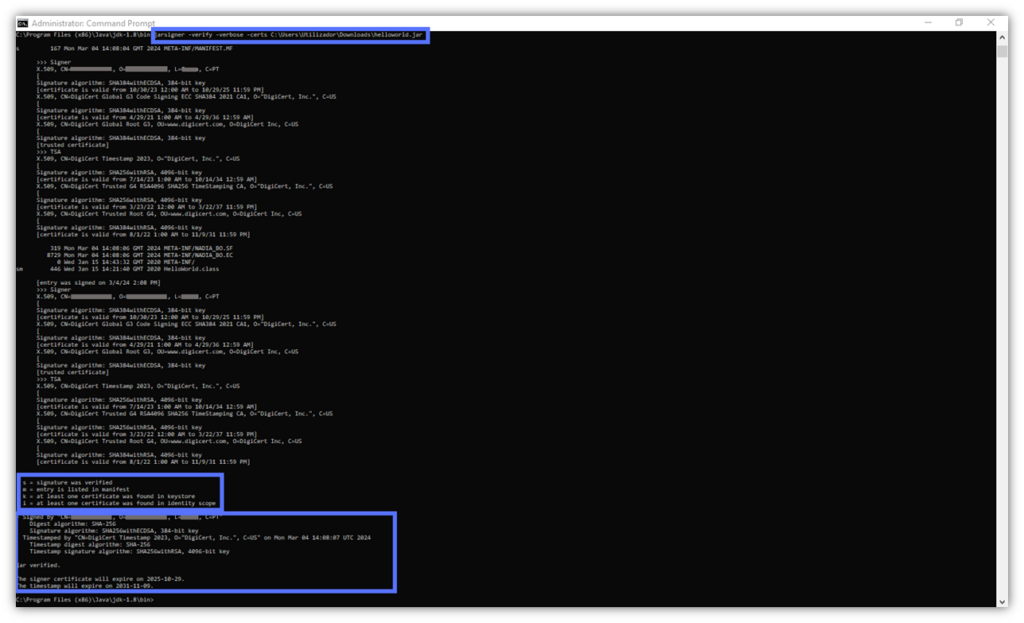
3 Benefits of Using the Java Jarsigner “-Verbose” Command
Hey, you made it! You’ve learned to sign Java files like a real sensei. That was a piece of cake. But are you left wondering what all that gibberish was that displayed when you hit Enter? That data is what you get when you use JarSigner.exe like a pro. And it’ll help you ensure that everything went exactly as planned.
Executing the signing command we’ve just shown gives you a detailed view of your Java Jarsigner code signing into three distinct blocks. Let’s have a quick look at the information displayed in each block.
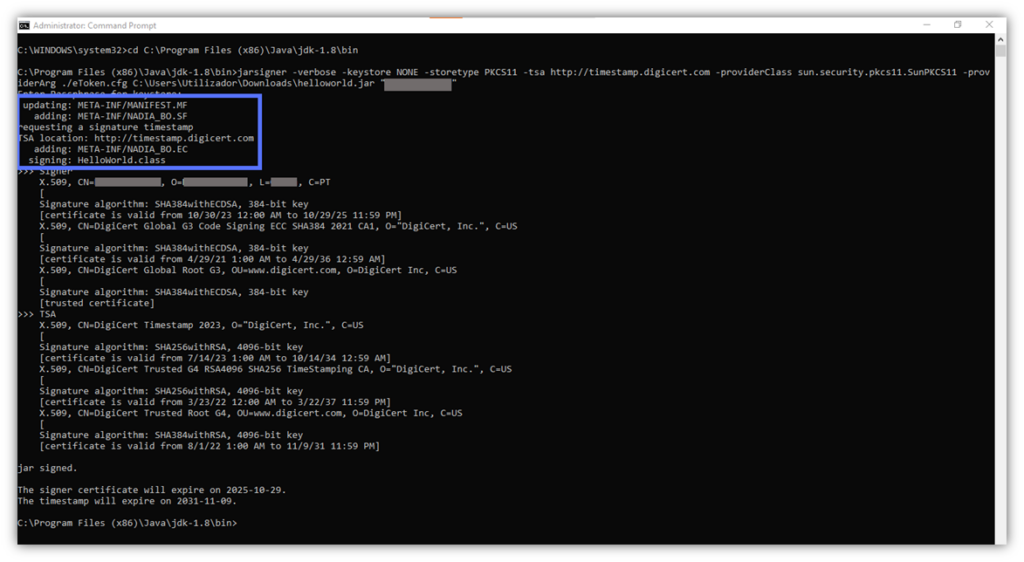
Section 1 – Lists and Confirms the Actions Taken During the Jarsigner Process
When you use Jarsigner to sign a .jar file, its META-INF/MANIFEST.MF is updated. Then, the tool adds two additional files to the .jar’s META-INF directory:
- A signature file (i.e., .SF). Including, among others, a header with the manifest’s hash, the file name, and the algorithm used (SHA).
- A signature block file (e.g., .RSA, .EC, .DSA). Here is where the signature is saved with the encoded code signing certificate and the timestamp.
Section 2 – Lets You Double-Check Whether Jarsigner Used an Authentic Code Signing Certificate
Want to verify that Jarsigner has used the correct code signing certificate and check the certificate’s validity? You’re in the right place. This block will display the certificate owner’s name (CN=), location (L=), country (C=), and chain of trust.
The latter is the information checked by the client during the download and installation of the app. It confirms the authenticity and integrity of the code signing certificate itself.
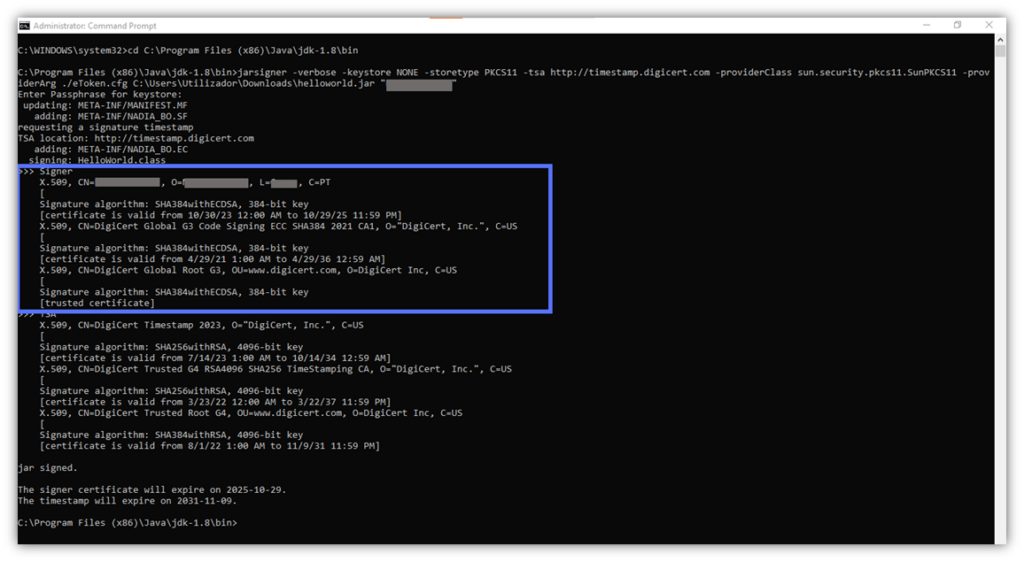
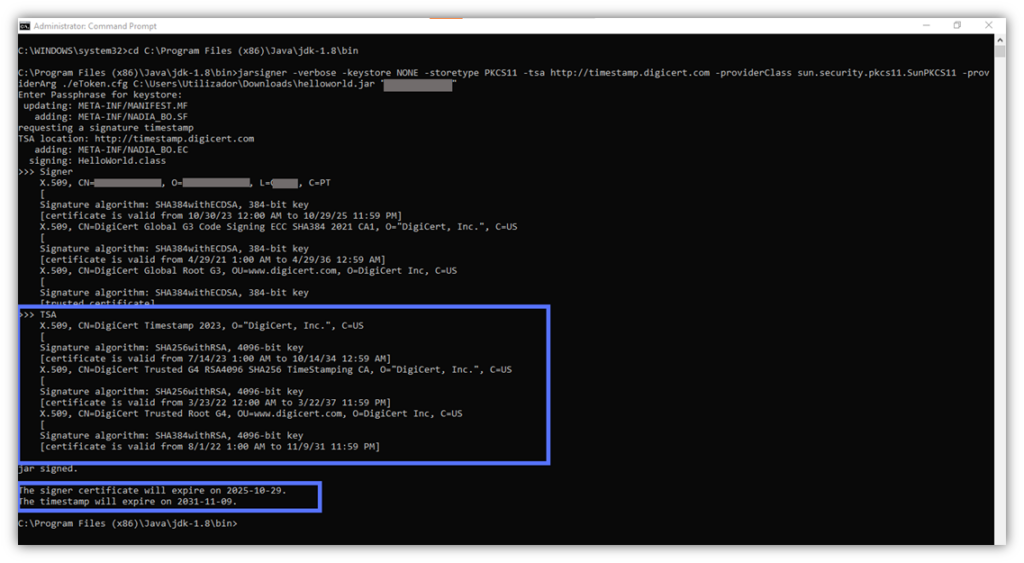
Section 3 – Allows You to Verify the Timestamp Authority (TSA) Information and the Code’s Signature Date
Do you remember when we talked about the importance of timestamping? This block shows you which TSA has been used (e.g., DigiCert) and at what time and date your code was signed. It’ll ensure that the client considers the signature valid even if the certificate used to sign has expired.
You don’t care about all this information and would rather just sign your code quickly and run home to enjoy your night? Fair enough. Explore two other Jarsigner code signing methods you can choose to employ.
The Top 3 Reasons Why You Should Always Sign (and Timestamp) Your Java Apps in 2024
In the 2024 ThreatDown State of Malware report, researchers shared that, ransomware attacks increased by 68% in 2023. This alone would already be a good enough reason to start signing and timestamping your Java code. But the “fun” doesn’t stop there; we have more in store for you…
Let’s explore three key reasons why you, as a software publisher/developer, should include code signing in your 2024 cybersecurity strategy. Signing your code will:
1. Preserve the Integrity of Your Applications Undermined by the Latest Emerging Threats
In 2023, ransomware and generative artificial intelligence attacks (GenAI) were among the top threats plaguing the digital world. For instance, Splunk revealed that 52% of organizations were severely impacted by a ransomware attack.
GenAI numbers aren’t far behind. The seventh annual Hacker Power Security Report, issued in September 2023, showed that 53% of ethical hackers employed GenAI to develop hacking tools and find vulnerabilities. Imagine how many bad guys are doing the same.
Signing your Java files with Jarsigner and a trusted code signing certificate won’t give you total immunity from software-based cyber attacks. However, it will add an extra layer of protection against your malware being tampered with, and it being used to spread malware infections.
Boost User Trust in Your JAR Files — Save Up to 21% on a Java Code Signing Certificate
Prove your Java apps and JAR files are legitimate by signing them with a Java code signing certificate. You can get one starting at $211.46/year.
Every bit of protection and security helps, right? This is especially true when leading tech giants see 2024 as the year that’ll put:
- GenAI-based attacks,
- Opportunistic ransomware (i.e., non-targeted ransomware), and
- Code injection attacks
at center stage.
2. Help Organizations to Comply With More Stringent Industry Regulations
Data protection regulations like the EU General Data Protection Regulation (GDPR) and other data privacy laws require businesses to implement adequate security protections and processes to secure sensitive data.
We’re already seeing an increase of new security-related directives worldwide so far in 2024. The European Union’s Network and Information Security Directive 2 (NIS2) is one of them, and covered entities must implement the directive’s specifications by October 2024. It explicitly requires companies to take certain protective measures to minimize the impact of potential incidents on users.
Adding a digital signature to your applications and files will help keep your customers’ data safe and sound. It’ll protect your organization (and users) from dangerous malware infections that could lead to disastrous (and costly) data breaches.
3. Increase Trust (and Revenue) For Your Organization
Did you know that “Authentic” is the word of the year 2023? Code signing certificates and Jarsigner will enable you to prove your users the authenticity of your signed apps.
Enhancing the security of your products with code signing will elevate your chances of growing your revenue and customer base. Furthermore, it’ll provide a smooth user experience by minimizing security warnings and the risk of installation failures. As a result, it’ll boost your brand reputation and increase adoption.
Statistics prove it:
- 59% of consumers recently interviewed by Edelman are more likely to purchase a product from a brand they trust.
- 67% of surveyed consumers said they’d even advocate for it.
These didn’t win you over? Discover why Jarsigner matters to organizations and users alike.
So, now that you know how Jarsigner works and how you can use Jarsigner code signing to make a difference in the security of your organization and products, it’s time to make 2024 count. Start signing your Java files and give attackers a run for their money.
Final Thoughts About the Ultimate Jarsigner Guide: How Does It Work and How Can I Use It?
We hope that this Java Jarsigner tutorial provided vital insights and techniques that’ll help you improve the way you protect your code, organization, and customers.
Threat actors are increasing the sophistication and speed of their attacks. This often involves piggybacking on the reputation of legitimate, unsigned software to insert unauthorized, malicious code.
Shift your software security strategy from reactive to proactive to stop this from happening by adding a digital signature and timestamp to your Java files. Doing so will:
- Reduce the potential effectiveness of their attacks.
- Prove to customers that your Java files and applets are secure and safe to install.
- Increase trust and earnings.
Interested in reading other smart, ultimate guides? Discover our Code Signing in Visual Studio Tutorial and ClickOnce Manifest Signing How-to. You won’t regret it.


