What Is the Most Secure Hashing Algorithm?
Beef up your data protection security with the most secure hashing algorithm. Learn how a one-way function can unlock your ability to truly excel in cybersecurity, protecting your sensitive data with virtually irreversible and unique hashes
2021 marked one of the most active years for cyberattacks and data breaches with software vendors experiencing the largest year-on-year growth ever (146%). As such, it’s hardly surprising that organizations are implementing smarter measures to tighten up the security of sensitive data and passwords in a more proactive way.
Well-known companies like Microsoft, TrendMicro, and GitHub are now dropping the SHA-1 algorithm because it’s been deprecated as a standard. This algorithm, used for years as an effective way to validate and protect the integrity of files, documents, and other types of data, has been deprecated (i.e., obsoleted) and replaced. But what has it been replaced with? That’s part of what we’ll explore in this article on the most secure hashing algorithm.
In this article, you’ll learn about the power of the most secure hashing algorithm, its key role in data integrity, and how it can help your organization withstand data breaches threats while complying with data security regulations and standards.
What’s the Most Secure Hashing Algorithm? SHA-256
SHA-256 (secure hash algorithm) is an algorithm that takes an input of any length and uses it to create a 256-bit fixed-length hash value. It doesn’t matter whether you hash a single word or the contents of the Library of Congress — the resulting hash digest will always be the same size. The “256” refers to the hash digest length.
SHA-256 is one of the hashing algorithms that’s part of the SHA-2 family (patented under a royalty-free U.S. patent 6829355). It’s the most widely used and best hashing algorithm, often in conjunction with digital signatures, for:
- Authentication and encryption protocols, like TLS, SSL, SSH, and PGP.
- Secure password hashing and verification.
- Cryptocurrency transaction verification (e.g., Bitcoin, 21Coin, Peercoin).
- Tokenization, which replaces sensitive data (e.g., credit card numbers, account IDs, etc.) with an unrecognizable string of random data during data transfers.
- File and software integrity checks (e.g., when a user downloads a signed file or code). The hash included in the code signing certificate will be recalculated and compared to establish the file or code’s integrity.
- Verifying the authenticity of messages or documents.
SHA-256 it’s a NIST’s (National Institute of Standards and Technology) recommended and officially approved standard algorithm. Thanks to the possibility of verifying the content of data without showing it, it’s also used by many governments and public-sector agencies worldwide, including the U.S. and Australia. But, what are the key features making this algorithm so popular among technology leaders, and secure to the point to be considered the most secure hashing algorithm available to date?
1. It’s a one-way algorithm. This means that it’s infeasible (too demanding in terms of time and resources) to reconstruct the original input from the output. Even through a brute force attack, an attacker would have to figure out the right combination of 0s and 1s — out of 2256 different possibilities (i.e., more combinations than the number of atoms in the universe) — to generate the initial data of an SHA-256 hash. To put it another way, it’s the equivalent of 1.158 x 1077, or 115,792,089,237,316,195,433,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936

2. The chances of collision are extremely low. In fact, there is only one in more than
115 quattuorvigintillion (a 78 digit number) chances of collision.
3. Minor change = drastically different output. Even the most insignificant alteration to the original input always produces an entirely different output (i.e., what’s known as the avalanche effect). This resulting change makes it even more difficult for an attacker to use statistical analysis to predict the content of the original data.
4. SHA-256 has not been broken. Seriously. To date, no one managed to crack it even if there is a huge financial incentive to do so. Whoever will succeed in reverse engineering SHA-256 will be able to mine Bitcoin faster than anyone else and will end up making a huge amount of money.
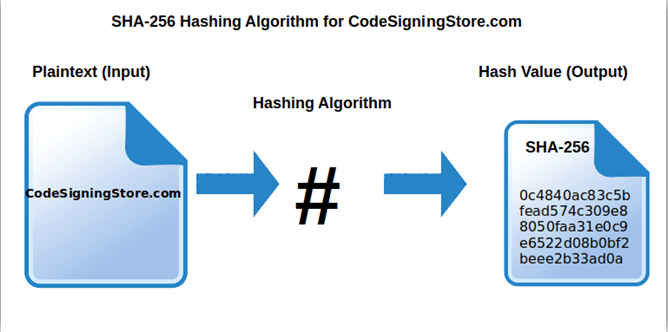
To better understand the true value of SHA-256 and its key features, we must first understand what a hashing algorithm is in general and why it’s important. This is what we’re going to see next.
What’s a Hash Algorithm?
As we touched on earlier, a hash algorithm is a function that takes an input of any length and scrambles it in an output of a fixed length (hash value or digest). If the input is altered, the associated hash value changes as well. This means that with a hash algorithm, you’ll be immediately able to spot if a file or a code has been changed (i.e., has a different hash value) or if two files are identical (your calculated hash value matches the one provided by the file).
In other words, a hash algorithm is a confirmation that the associated file or code is uncompromised — that it is what it says to be and hasn’t been manipulated or altered. In other words,s a hash function protects the integrity of the data or file in question.
To give you a practical example, the hash algorithm follows the same principle of the last digit of a bar code. This number, which is called a check digit, is always determined by the other digits that precede it. If one of the numbers changes, the last digit of the bar code will also change. This means that a computer store may end up with a cupcake in its inventory just because of a single wrong digit.
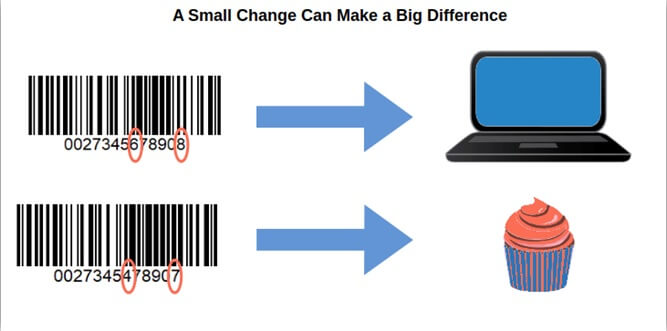
Hash functions operate similarly but on a much larger scale. Instead of changing just the last number (like the bar code), if even one character changes in the original input, the resulting hash digest output will be completely altered.
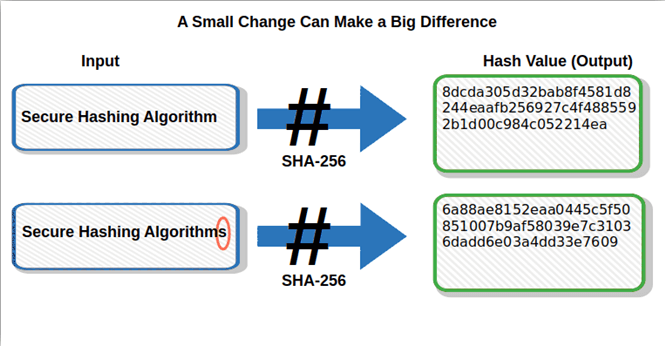
Amazing right? So, how can such an apparently simple thing be so fundamental for data security in today’s digital world?
4 Reasons Why a Hash Algorithm Is Important
Hashing algorithms have come a long way since they were invented in 1941 and, thanks to their key attributes, they’re now an essential part of cybersecurity. Every hash function is:
- Easy to compute in one direction. Generating a hash value from any kind of data is easy, no matter the size of the original file. However, it’s very difficult to calculate back the value of the original input.
- Deterministic and not random. A hash algorithm is like a fingerprint: your thumb will always leave the same fingerprint. The same happens with hashing algorithms. Hashing a distinct input will always deliver the exact same hash value. This means that if two people check the hash value of the same file or code, they’ll be able to determine its authenticity as they should both get the same answer.
- Impossible to modify the input without changing the resulting hash value. Do you remember the avalanche effect we talked about toward the beginning of this article? This is exactly that. If the original file changes, even if the change is small, so does the output. This makes it really easy to verify the integrity of any file or code.
- Resistant to collisions. In other words, it should be difficult to find two different inputs (e.g., files or codes) with the same hash value. This is important if you’re distributing files on the web, for example. Without resistance to collision, an attacker could replace the original file with an infected one using the same hash. The file would appear authentic as it would have the same hash as the real file. As a result, when a user downloads it, its device will be infected.
Do you want to know more about hashing algorithms? Check our previous article and Computerphile’s hashing algorithms and security video:
- SHA-256 takes a plaintext input and returns a unique, fixed length output. A 256-bit output (32 bytes) displays as 64 hexadecimal alphanumeric characters ranging from [0-9] and [A-F].
- Security benefit 1: Ideal for password protection and verification, storing password hashes instead of plaintext passwords is much more secure.
- Security benefit 2: Perfect for code/data integrity checks through code signing certificates, enabling you to verify if the code or file has been tampered with, thus minimizing the risk of malware infections and corruption.
- Its output looks completely random and is unreadable. The resulting hash digest includes no identifying information about the original input.
- Security benefit: This will help your organization to be compliant with data protection regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Protection Act). Both privacy and security regulations require personal data anonymization and protection.
- A hash is a one-way function. Basically, it has only one output for each input. On the other hand, ‘’there’s an infinite number of different combinations to get the same output making it virtually impossible to reverse engineer it, as explained in an excellent video made by Matthew Weathers. This differs from encryption, which is a two-way function (e.g., encryption) that’s intended to allow its original input to be computed from the output by the private key holder.
- Security benefit: Being infeasible to reverse makes it a powerful tool against even more sophisticated attacks.
Cool right? And these are just a few examples of just how useful and crucially important SHA-256 is for cybersecurity.
Surely enough, if used correctly, it can help protect your organization from data breaches. Moreover, with the expansion of cloud services and IoT, a robust algorithm like SHA-256 has become a key player in preserving privacy, integrity, and ensuring secure communication among connected devices on the otherwise insecure internet.
This gets us nearly at the end of our journey into the most secure hashing algorithm world. Before we wrap up though, let’s have a quick look at how SHA-256 — considered the most secure hashing algorithm — differs from the other SHA families.
Not All SHA Families Are the Same: Learn the Differences
As mentioned by the Cybersecurity & Infrastructure Security Agency (CISA) in its hash function definition, SHA is divided into two different families:
- SHA-1 (Secure Hash Algorithm-1), and
- SHA-2 (including SHA-256).
You may have noticed that we didn’t include SHA-3 in the list. As its internal structure is pretty different from the previous two and it’s based on a new approach, SHA-3 has to be kept separate when discussing SHA families. We’ll talk more about it in one of our next articles but won’t get into all of that right now. For now, let’s stick with our topic of SHA-1 and SHA-2.
Published in 1995, SHA-1 is the very first version of the secure algorithm and, even if SHA-2 is in some way its updated version, and they’re both based on MD5 structure, they’re two distinctive families differing from each other in many ways. How? Let’s see.
SHA-1 vs. SHA-256 – Comparison Table
| SHA-1 | SHA-256 | |
|---|---|---|
| Generated Hash value | 160-bit (20 bytes) displayed as a 40-digit hexadecimal string. | 256-bit (32 bytes) displayed as 64 hexadecimal alphanumeric characters. |
| Hash key features | Shorter code, which results in less possibilities for unique combinations (thus a greater probability of collisions). | Extended code with a more complex hash value, thus the possibilities of collisions are nearly null. |
| Applications | Still used to sign some old SSL certificates, even if from 2016 all newly issued SSL/TLS certificates must use SHA-2. | Most used worldwide. From digital signatures to software integrity checks, from blockchain to password hashing. |
| Security Level | Weak and susceptible to attacks (e.g., brute force). In fact, when a 2005 study showed the feasibility of breaking the SHA-1 algorithm, NIST quickly proposed in 2006 that the U.S. federal government move to SHA-2. | High. |
| Has it been broken? | Yes, in 2017 when Google announced the first collision. | Still unbroken. |
| Status | Deprecated. | Widely used and known as the most secure hashing algorithm. |
Even if SHA-1 and SHA-256 are the most popular hashing algorithms, they’re not the only ones available. There are several more, old and new, that are still widely used. Some of them have weaknesses, but some can be good enough for non-critical applications. But this is another story, for another time… stay tuned!
Final Thoughts on What Is the Most Secure Hashing Algorithm
To the time of writing, SHA-256 is still the most secure hashing algorithm out there. It has never been reverse engineered and is used by many software organizations and institutions, including the U.S. government, to protect sensitive information. It’s so secure that it’s even a central part of Bitcoin’s cryptographic protocol.
Now that you know what the most secure hashing algorithm is, don’t leave your data integrity at risk by relying on old and vulnerable cryptographic systems. There’s a much more powerful and secure hash mechanism available at your fingertips! Move to SHA-256 today and enhance your data security protection now.
Remember: Although it took years to build your organization’s reputation, it only takes a few minutes of a cybersecurity incident to destroy it.


