Why Should I Sign My JAR Files? A Look at Why JAR Signing Is Required

One in five businesses interviewed by Hornetsecurity were victims of a ransomware attack in 2023. Keep the lid of the malware jar sealed with JAR signing. Learn why you need it and uncover its top benefits
With over 91 million new pieces of malware identified in 2023 (as of the writing of this article), the time when users could blindly trust what they downloaded and installed on their devices is long gone.
Organizations looking for digital trust solutions are turning to code signing as a way to prevent tampering and assert that their software products are legitimate and trustworthy. Even Oracle, since the Java 7 Update 51 was released in 2014, has blocked all unsigned applets and Java Web Start (JWS) applications from running.
So, are these the only reasons why .jar signing is required (using the term “required” loosely)? Yes and no:
- Yes, in the sense that cryptographically signing your .jar files will help you safeguard your users and organization from malware and will provide evidence that your software really came from you. It’ll also ensure old Java Rich Internet Applications (RIAs) aren’t blocked by security checks.
- No, in that .jar signing isn’t technically a requirement for most non-client applications. But the issue isn’t black and white; there’s more to .jar signing, and that’s what we’re here to explore.
Intrigued? Here, you’ll get the complete answer to why .jar files signing is something every developer and software publisher can’t forgo.
The Issue With JAR Files
A Java Archive (JAR) file is similar to a ZIP file. It aggregates all the different resources and components needed to build and run one of the following in a single compressed file:
- Executable Java application,
- Applet, or
- Java library
Since everything — from .class files to audio/image files and directories — is stored under one roof (i.e., in a JAR file) and compacted, the distribution and maintenance of JAR-based applications and libraries is child’s play. This is partly why jar files have become a staple in our digital world; they’re found nearly everywhere — from your smartphone to middleware and enterprise servers.
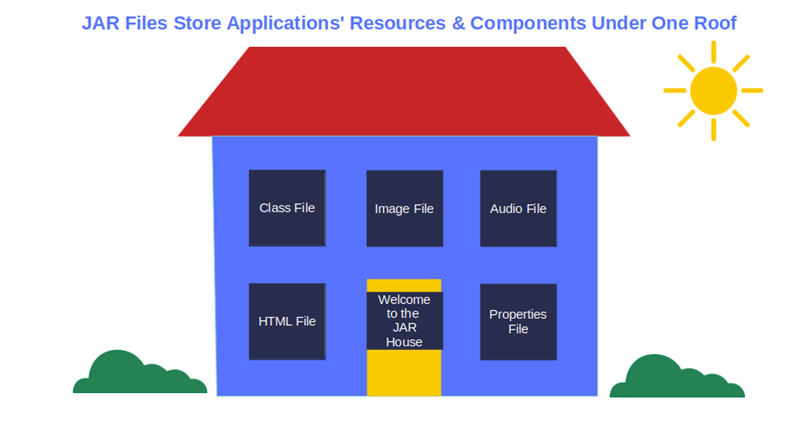
However, just as JAR files are handy for nearly all kinds of applications, the fact that they often incorporate other JAR files (which, in turn, can include more JAR files, and so on) makes them also incredibly useful to cybercriminals.
Let me explain it with an example. Imagine I hide a penny in a Matryoshka (the set of Russian nesting dolls in which one figurine is placed inside another, which is inside of another, etc.). To find it, you’d have to open all of the nesting dolls until you found to the one with the penny.
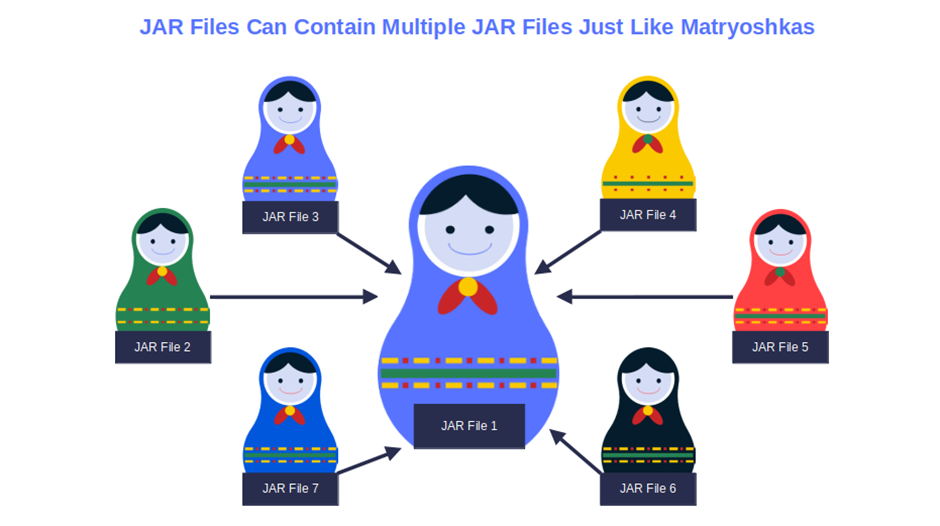
The same goes for security teams and .jar files. To find malware deeply hidden several levels down in a JAR file, they’ll have to go through all levels of JAR files, not just the top-level ones. This can be done manually or by using some vulnerability scanning tools. Either way, it’ll be like looking for a needle in a haystack.
Tricky, right? And with 29% of the 276+ million Log4j Java library downloads in the past two years still including Log4Shell vulnerabilities, it gets even more complicated. Another good reason for attackers to exploit JAR files.
How can you blame them? It’s such an easy job, and bad guys love low-hanging fruit (i.e., achieve the biggest payoff with the least amount of effort). All they have to do is modify an application’s JAR file and hide a single piece of malware in one of its layers. In one go, they’ll be able to infect multiple endpoints and operating systems. It’s far too tempting for cybercriminals to resist.
So, what can organizations do to get out of this impasse and protect their users from malware? Let’s find it out.
The Solution: Sign Your JAR files With a Code Signing Certificate
When asking yourself why jar signing is required, it’s always a good idea to look at it from the perspective of the benefits Java jar signing provides. When you sign a JAR file with a publicly trusted code signing certificate, you won’t have to worry about unauthorized changes any longer. Because the certificate was issued by a trusted certificate authority (CA), you also have a way to prove (through cryptographic means) that your software is authentic and was created by you (not an imposter).
In fact, the digital certificate containing vetted information about your organization, together with the Java digital signature, will alert users every time a JAR file is modified by a malicious third party.
How? In a nutshell, when you create a Java digital signature using your code signing certificate, you also generate a unique string of data (i.e., a hash digest or hash value) that informs whether the Java files have been modified since they were signed. When the user downloads the Java application or library, their client will generate a new hash and compare it with the original one.
But what if the two digests don’t match? A-ha! The file may have been tampered with or corrupted. In any case, it has been modified without authorization, which means it can’t be trusted. As a result, the user will be alerted by a pop-up warning. Yup. Cybercriminals may try to hide the malware in the most secluded JAR file, but with JAR signing, no secret hideaway will keep it from being spotted because of the checksum that offers assurance of the file’s integrity.
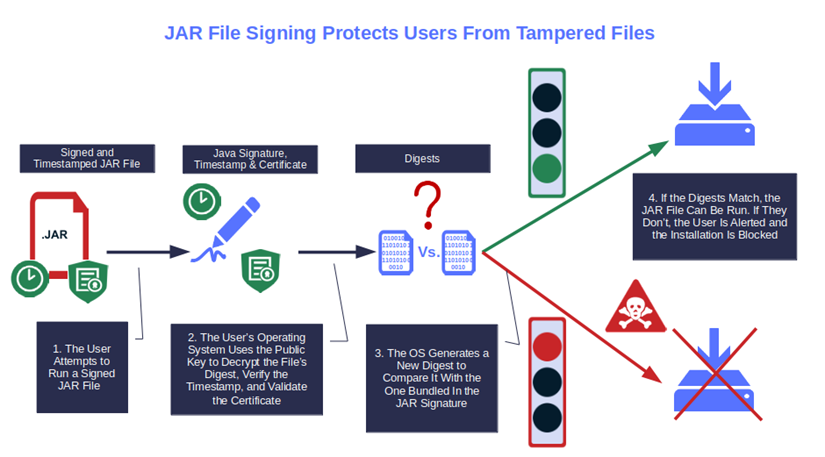
So, isn’t this already a jolly good reason why a JAR signing is required? Of course, there are more reasons why developers and publishers should sign their .jar files. But before we deep dive into them, let’s check out a quick overview of the JAR file signing process.
1. Purchase a Code Signing Certificate From a Trusted Certificate Authority (CA)
If you already have one, you’re in luck, and you can jump to step three. If you don’t:
- Pick your trusted CA and certificate.
- Go through the vetting process.
- Set up your code signing hardware token. Note: This is a one-time operation that everyone who has purchased a code signing certificate (individual, standard, or extended validation) after June 1 2023 must complete. In fact, since that date, all certificates have been issued so they can be stored on secure hardware (e.g., USB token or hardware security module [HSM]). To set up your token for the first time, follow our step-by-step guide.
Save Up to 21% on a Java Code Signing Certificate
Digitally sign unlimited JAR files and applications for as little as $211.46/year.
2. Download and Install the Java Development Kit (JDK)
To sign your JAR file, you’ll need the JarSigner tool embedded into Java JDK install. Grab it and move to the next step.
3. Sign Your JAR File with JarSigner
Now, you have everything you need to use Oracle’s Jarsigner to sign your Java archives. All you have to do is follow a simple process and you’ll be ready to go. (We’ve got an article that will walk you through how to sign a jar file, step by step, using a code signing certificate and secure token.) Once done, you’ll be able to securely distribute your Java-based applications and files.
Be sure to add a timestamp as well. This way, your digital signature will remain valid even after the certificate itself has expired.
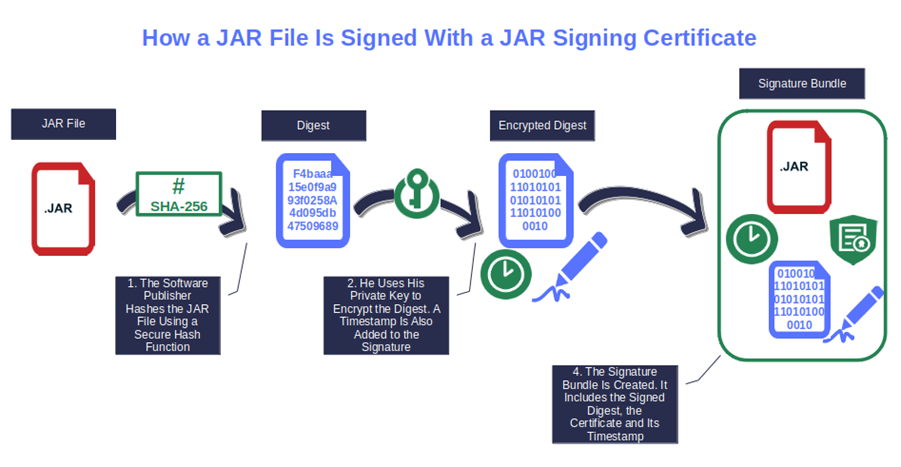
This is how JAR signing works. Easy, right? But there’s still an open question that we’ll answer in the next section: Why should organizations and/or developers go through all this hassle?
Authenticity, Integrity, Trust, and More: 5 Good Reasons Why JAR Signing Is Required
Ta-DA! Here is the part we’ve all been waiting for. Let’s get to the bottom of why JAR signing is required in terms of the benefits it provides.
1. Authenticity
Each Java code signing certificate is issued by the CA only after conducting a thorough vetting process. During the process, the CA verifies key details about your business or organization (e.g., physical address, phone number) to certify that it’s legitimate.
The advantage? This will enable you to confirm to your customers that every JAR file signed by you has really been created by you and nobody else.
Save Up to 21% on a Java Code Signing Certificate
Digitally sign unlimited JAR files and applications for as little as $211.46/year.
2. Data Integrity Protection
According to Verizon’s 2023 Data Breach Investigations Report (DBIR), 49% of data breaches stemmed from stolen credentials. And guess what? Several JAR-based, cross-platform malware such as Java remote access trojan (JRAT), STRRAT, and Adwind RAT are specifically crafted to take control of devices and steal sensitive information, such as login credentials.
Two of the latest .jar-based malware infection victims? BukkitDev and CurseForge, two popular Minecraft modding platforms. In June 2023, attackers injected fractureiser malware into several mods (i.e., plug-ins) usually downloaded by millions of users.
This self-replicating malware, in its final stage, spreads the infection to all JAR files on the system. It steals cookies, credentials, and replaces cryptocurrencies addresses. Imagine the damage it can cause. And it all starts with a user downloading an infected plug-in.
JAR signing (and timestamping) will help safeguard your organization and customers from malware infected code by alerting users when the hashes don’t match.
3. Brand Trust
In the words of writer Maria Snyder: “Trusting is hard. Knowing who to trust, even harder.” This is particularly true in today’s digital world, where fake news, videos, and infected files push people to question everything they see, read, and download.
Signing your JAR files with a standard code signing certificate is a way to prove to customers that they’re coming from a trusted publisher. Your organization’s CA-verified details will be clearly shown at the beginning of the installation, leaving no more doubts.
As a result, the level of trust in your brand will go up. And so will the number of loyal customers on your books.
4. No More Warnings
Would you download an application if your operating system would display an alarming “unsigned app” or “unknown publisher” warning, like the one shown below? I bet you wouldn’t.
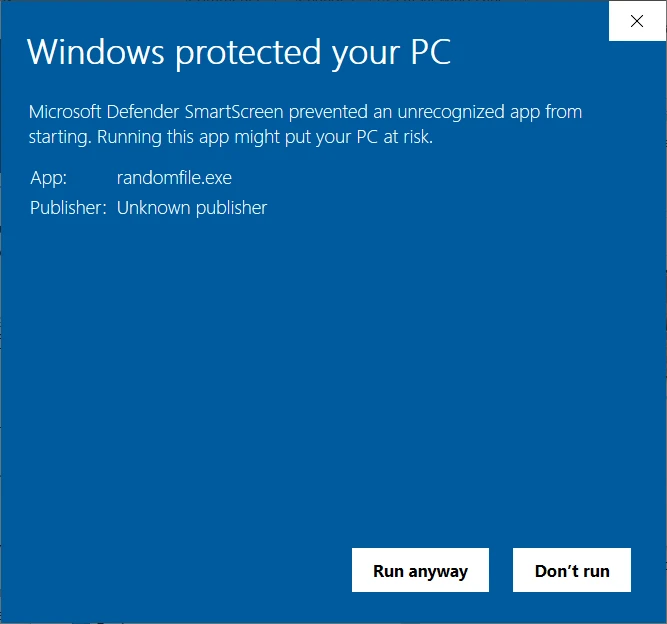
Sign your JAR files, and your users will enjoy a smooth installation instead of running to the competition. Warning messages are always a big turnoff, but code signing can help you hold them to a minimum. When you sign with an EV code signing certificate, you’ll get the advantage of not displaying the Windows Defender SmartScreen warning at all because your software will be automatically trusted. Your customers will be happier, and the number of downloads will increase.
5. Increased Downloads and Revenue
In 2022, 52% of the companies interviewed by Splunk were victims of a data breach. Knowing this, it shouldn’t come as a surprise if software publishers, operating systems, browsers, and even app stores increasingly require software products to be signed with code signing certificates issued by trusted CAs.
Increasing your brand presence within the market and reducing or eliminating annoying warnings can help make the number of downloads of your JAR files skyrocket. And what does more downloads mean? The answer is elementary, my dear Watson: higher revenue!
Ultimately, many have learned the hard way that these days, cybercriminals are picking up one of the illusionists’ most popular tricks: if you want to hide something, hide it in plain sight. That’s what they do with malware. They hide it in inoffensive-looking files, such as JAR files. Unaware users download them, and the damage is done. However, just like with magic tricks, as soon as the method is revealed, the illusion falls apart. This is why JAR signing is required in the sense of being a good practice, even if it’s not a technical requirement in some cases. When you sign your jar files, =users know when a file has been modified because they’ll be alerted by their browser or operating system. As a result, the attackers lose their power and the trick no longer works.
Final Thoughts About Why Should I Sign My JAR Files? A Look at Why JAR Signing Is Required
Next time your boss or developer asks you why JAR signing is required, and why anyone should even bother with it, don’t flip out.
Clarify that signing your .jar files isn’t just a whim of the moment or another way to increase the complexity of software development. As we’ve just discovered, JAR signing has a lot to offer users and software developers and publishers alike:
- Increase users’ trust in your products by confirming that they’re original, made by you, and unmodified.
- Enable you (as a software dev or publisher) to increase your reputation, revenue opportunities, and users‘ trust in your brand.
- Offer a smoother customer experience by removing those alarming operating system warnings and blocks.
Don’t underestimate the importance of secure code signing anymore. Integrate it into your secure software development life cycle (SSDLC), and share why you’re doing it. Your JAVA applications and applets will run smoothly, and you’ll help keep your organization’s name off lists of known malware.


