What Is a Java Digital Signature?

Is your organization building new full-stack Java applications like 70% of the enterprises interviewed by Vaadin? Then you can’t do without a Java digital signature, a must-have for any software publisher. Discover in less than 5 minutes what it is, what it does, and how to get one
“Write once, run everywhere.” This is how Sun Microsystem defined the Java programming language when it released it. A few decades later, Java really does run everywhere — from mobile phones (e.g., Android operating system) to Wikipedia search, and from cloud-based applications to the fascinating NASA WorldWind. Even Minecraft is written in Java!
This programming language is so popular among developers that, in 2023, the adoption rate of its latest long-term (LTS) support release (Java 17) grew by 430% year over year. Does it mean that applications written in Java are also highly secure? It depends. Java digital signature is the publishers’ secret weapon that keeps Java applets and applications secure against attacks and unauthorized manipulation. But what is a Java signature, exactly? What does it do? And why should you bother adding it to your products? It’s time to find out.
What Is a Java Digital Signature? A Brief Definition
Java is a platform-independent, object-oriented (i.e., focused on data rather than commands) programming language used to develop web and mobile applications. Owned by Oracle, it’s easy to write and read, and runs on virtually any device.
Java is used by nearly every company (e.g., Amazon, Cloudflare, Netflix). If you’re like the 3 billion people in this world who have an Android phone, then you’re using Java. It’s the perfect match for Internet of Things (IoT) devices and cloud applications.
Its versatility is a hit, even among the bad guys who exploit it to perpetrate their crimes. Log4j attacks, malware infections, ransomware, you name it. This is where the Java security signature comes in.
A Java digital signature is a cryptographic signature that cannot be forged. It confirms the authenticity and integrity of a code (more on that in a moment), and it’s used by developers to sign Java applications that run on desktops as well as applets running in browsers.
To create a Java digital signature, publishers must first purchase a Java code signing certificate from a trusted certificate authority (CA); its private key will need to be stored on a secure hardware token (which the CA will issue with it by default) to meet the industry’s new requirements.
Save Up to 21% on a Java Code Signing Certificate
Digitally sign unlimited JAR files and applications for as little as $211.46/year.
What a Java Digital Signature Does
In a nutshell, a Java digital signature gives you a way to assert your digital identity on your Java software applications and show they haven’t been tampered with. This is crucial when you consider that nearly 40% of breaches start with malware.
Here’s a useful description of Java digital signatures from O’Reilly:
“Digital signatures can be used to authenticate Java class files and other types of data sent over the network. The author of an object signs the data with his or her digital signature, and we use the author’s public key to authenticate that signature after we retrieve it. We don’t have to communicate with anyone in order to verify the authenticity of the data. We don’t even have to make sure that the communications by which we received the data are secure. We simply check the signature after the data arrives.”
But the next line of the paragraph is important because it asks a critical question: “If it is valid, we know that we have the authentic data and that it has not been tampered with . . . or do we?”
A Java digital signature uses public key cryptography and PKI digital certificates. This potent combination helps a user’s operating system or client:
- Confirm the identity of the applet/application’s publisher. When you add a Java security signature to your code, every time a user runs the application, they’ll see your organization’s name listed as a “verified publisher” instead of showing the “unknown publisher” or “untrusted app” warnings. This will prove to your customers that the code is really coming from you (i.e., authenticity).
- Prove that the Java/JAR file hasn’t been modified since it was first signed. A Java digital signature works a bit like your iPhone warranty seal: it protects your code from tampering and acts as tangible proof that it hasn’t been modified since it was signed.
- Provide non–repudiation of the signer. This helps prevent someone from signing a piece of software and then later denying they were the source of the file.
Interested in learning more about digital signatures? Don’t miss our deep dive into the three uses of digital signatures that can take your security strategy to the next level.
What Files You Can Use Java to Create and Sign
Java can be used to create and sign many types of files, including:
- .exe and .msi files on Windows operating systems
- .deb and .rpm to run on Linux OSes
How Java Signing Works
Let’s say you’re a developer or publisher who’s looking to sign your latest application. When applying a digital signature, you hash your code using a cryptographic function and sign the outcome (i.e., digest) with your private key. The signed hash is then packaged with your code signing certificate, a timestamp, and your application.
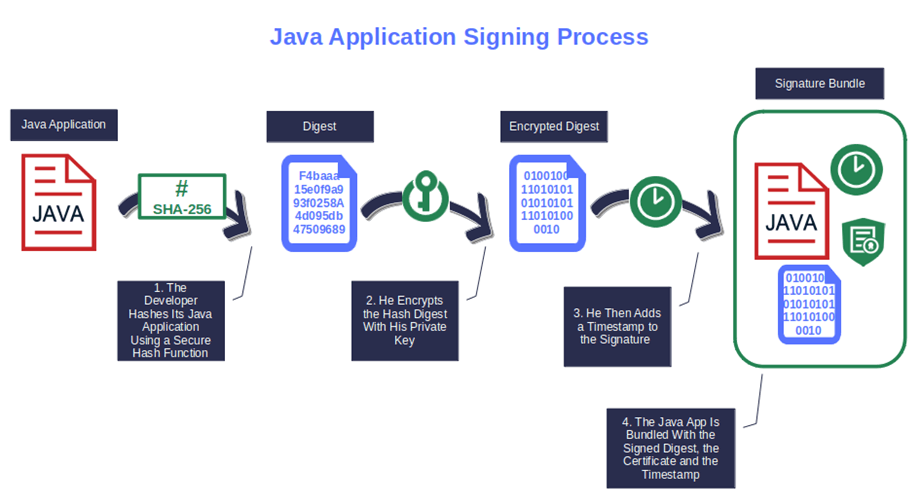
Voila’. This is your digital signature (i.e., signature block).
When a user downloads/installs or runs your signed application, their client will verify the signature’s validity by comparing the hash value generated with the one included in your signature block. If they match, the integrity and authenticity of the file are confirmed, and they’ll be good to go. If they don’t, they’ll be warned that your software can’t be trusted, and the installation or download will stop.
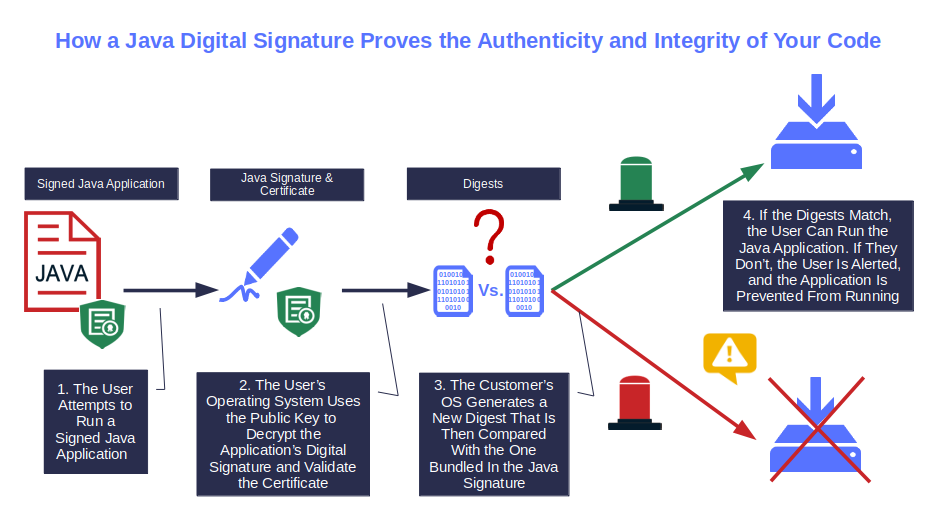
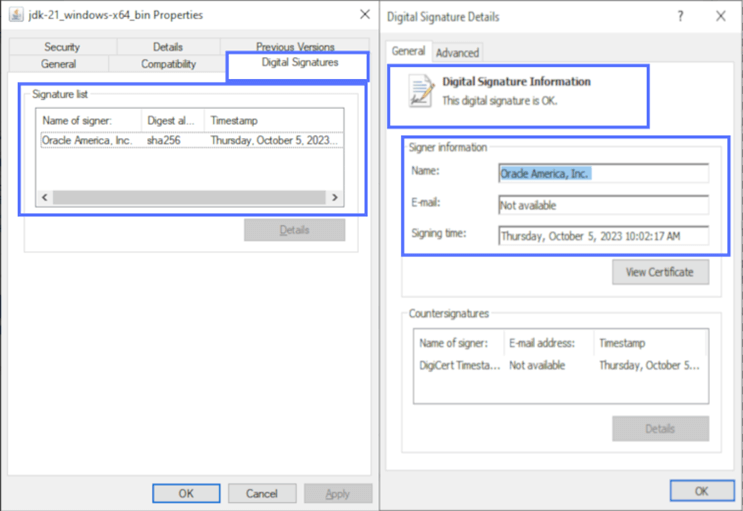
On top of it, users can also view the Java signature details by simply right-clicking on the downloaded code icon, selecting Properties and the Digital Signature tab.
Pro tips:
- When you sign your .jar files and applications, ensure you add a timestamp. It’ll extend the validity of your signature even when your Java code signing certificate is expired.
- If you have several certificates and keys to manage, create a .PFX file to “Rule them all” in a single, secure bundle. (A hat tip to my fellow Tolkien fans out there.)
Discover how code signing works by checking our article that explores the process step by step.
Why Should You Care About Java Security Signatures?
Java security signatures are the magic ingredients that enable software publishers and developers to boost the security of their codes and build digital trust in their products. A Java signature will:
- Secure Java applets and applications from unauthorized manipulation. Applets are small programs used in webpages to generate dynamic and interactive content. An unsigned applet or application could be easily modified by an attacker. All they have to do is to inject malicious code into it. It’s important to note: Most applets have now been replaced by modern alternatives like JavaScript and HTML5. However, Java applications are alive and kicking. Want to maintain their integrity? Apply a Java signature to your codes.
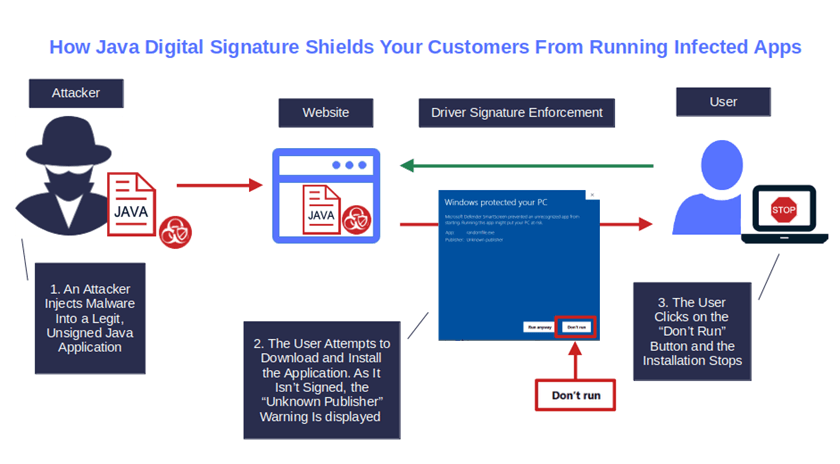
- Avoid pop-up warnings during download and installation. Want to get rid of those alarming “Unknown Publisher” or “file.jar was blocked because this type of file can harm your device” message pop-ups that inform users that your application could harm their devices? Add a Java digital signature to your application to display your organization’s information instead. It’ll reassure your users, boost customer trust, and increase software download, installation, and adoption rates. And this takes us to the next point.
(NOTE: To make the Windows Defender warning window disappear altogether, you’ll need to sign using an extended validation [EV] code signing certificate, which is automatically trusted by Windows operating systems and browsers.)
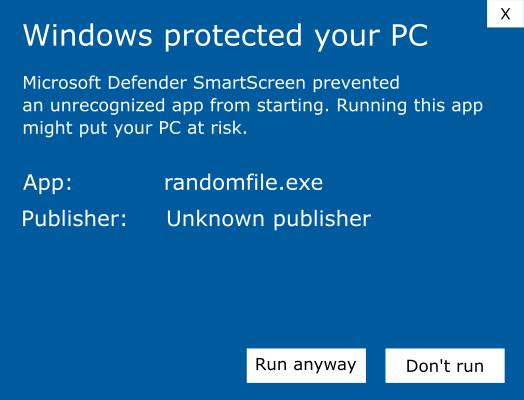
Image caption: Do you really want your customers viewing this alarming “Unknown Publisher” warning every time they download or run your Java-based executables?
- Improve your brand and organization’s reputation. 84% of consumers would stop buying from a brand if they lost trust in it. Compare this to the 37% of customers interviewed by PwC who would stick with a business that blows it once, so long as long as the brand takes the necessary steps to fix the issue at hand. A Java digital signature will add a shining star to your brand by showing your clients you care about the security and reliability of your software. So, give signing your code using a Java digital signature a try — your reputation can only benefit from it.
Want to start signing and time stamping your Java applications and .jar files but you don’t know the process? Once you have purchased your Java certificate, and set up your USB token on your device, follow these five simple steps.
Boost User Trust in Your JAR Files — Save Up to 21% on a Java Code Signing Certificate
Prove your Java apps and JAR files are legitimate by signing them with a Java code signing certificate. You can get one starting at $211.46/year.
Final Thoughts on What a Java Digital Signature Is
Java digital signatures are more than just a signature confirming the authenticity of your products. They safeguard all your Java applications and files from malicious tampering. Adding a Java digital signature using an EV code signing certificate even prevents the display of security alerts during the download and installation processes.
To add a Java signature and timestamp to your applications, .exe, .msi and .jar files, all you need to do is to:
- Get a digital certificate and secure USB token issued by a publicly trusted CA,
- Create a Java digital signature using cryptographic functions and your cryptographic key that’s stored on the token, and
- Add a timestamp.
From now on, your application will be cryptographically bound to your Java digital signature. Every time a user runs or downloads the application, their client will be able to validate its integrity. Remember, though: your Java signature’s security is directly proportionate to how carefully your private keys and certificates are stored and managed. Treat them both with care and be sure to follow other code signing best practices.
Want to see how to digitally sign a Java file using a code signing certificate? Be sure to check back on our blog, as we’ll publish a step-by-step article that will walk you through the process of signing .jar files using Windows Command-Line (CMD) using Jarsigner.


