Are All .Exe Files Viruses or Malware? How to Check & Prove Yours Isn’t

What do Sys.exe, AnyDesk.exe, and netscan.exe have in common? They were all exploited by cybercriminals to deploy BlackByte ransomware attacks. Explore whether all executables are viruses and discover an easy way to discern the good .exe files from bad ones
For the second consecutive year, SonicWall’s 2023 Cyberthreat report lists .exe as the most common malicious file type. Executable files are so popular among cybercriminals that they’re constantly reported as the top Windows malware file type. This is largely why Microsoft Outlook blocks the sending and receiving of .exe files by default; in April 2023, the company also rolled out a similar block for One Note.
Wait. So, are all .exe files viruses or viruses then? Does this mean that developers and software vendors should stop creating .exe files? Spoiler alert: No, and no. Executables play critical roles in our digital world, so don’t give up on them just yet. In this article, you’ll discover how:
- You (as a user) can check whether that weird .exe process running on your device (and draining your CPU) is safe.
- You (as a developer or vendor) have a way to prove to your customers and users that your .exe files are safe.
Because even if threats are everywhere in the digital world, not all viruses or other types of malware are painted with the same brush.
Are All .Exe Files Viruses or Other Types of Malware?
As a security engineer, I had to teach newbie employees and students to analyze cyber threats and potentially harmful files and codes. Almost all of them, sooner or later, asked me the same question: “Are all .exe files viruses?”
Why? Because among all the malicious scripts and dodgy compiled programs we were analyzing, no matter if they were email attachments or downloadable executables, those with the .exe extension were the most common.
And today, things haven’t changed much. In Q1 2023, malware infections jumped by almost 40% year over year. Cybercriminals are getting creative by exploiting new tools like ChatGPT to generate new malware.
So, what was my answer to my students then? The same one I’m sharing with you today: “Not all executables are viruses. Just like there are bad and good people, there are also bad and good .exe files.”
For example, .exe files could be:
- Legitimate programs running on your device. Think about Windows software installers often named something_setup.exe. Do you want to install Firefox or Chrome on your Windows device? You’ll be prompted to download a .exe file, too.
- Malware. These are the bad .exe files you want to stay away from. If you compare them to people, they’re the criminals. Often disguised using legit-looking names, they lure victims by posing as genuine email attachments or downloadable software applications. When you look behind the masks, you’ll discover that they’re infected with viruses, worms, ransomware, and other types of malware.
- Corrupt files. These are like confused people who might unintentionally cause harm. This type of .exe file isn’t as dangerous as the previous one. It’s genuine code that, due to accidental corruption, won’t work properly once installed.
In short, the answer to the question “Are all .exe files viruses or malware” is “No, but many of them are.” Is there a way to check and prove that yours isn’t? You betcha! And this is what we’re going to explore next.
Users: How Do I Know Whether an .Exe File Is Legit and Safe to Install and Use?
Telling if a .exe file is safe to install and run isn’t complicated, but taking the time to determine this can help protect your devices against malware and attacks. At least, this is the case so long as you know how to do it and what to check. Is it difficult? Not at all. It’s sufficient to follow these three simple tips.
1. Verify the Source of the .Exe File
Do you normally download .exe email attachments without thinking because they seem to come from a person/company you know and trust? Have you habitually gotten your software from dodgy websites or file-sharing sites to save money? Both of these are terrible ideas. Why?
Email addresses can be easily spoofed (i.e., doctored) to trick recipients into opening phishing emails or clicking on malicious attachments. Is it really so dangerous? Judge for yourself. In 2022, 66% of organizations surveyed by Mimecast were victims of at least one email-based ransomware attack that somewhat damaged their business.
Are shady websites and file-sharing sites better? Nope. They both are well-known sources of many types of malware. Therefore, the first rule is to click on or download .exe files from reputable sources only.
Want to know how to recognize a spoofed email? Check out this short video to learn a few tricks:
2. Look Out for Your Operating System Warnings
Are you a Windows user? I’m sure you’ve seen the popup below at least once when you tried to install or run an executable:
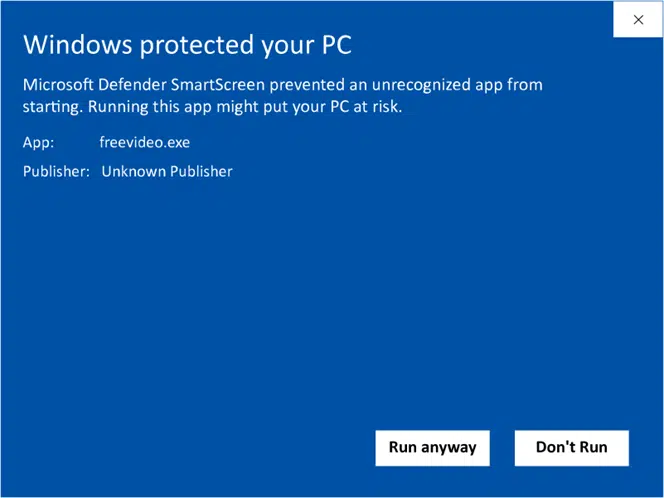
What is it? When you download and/or install software, Windows automatically checks whether the code has been digitally signed using a code signing certificate and looks for the publisher’s verified name. If the software hasn’t been signed, the screenshot above is an example of the warning that Windows Defender SmartScreen will show you.
What does it mean? The file could be dangerous as the operating system couldn’t verify its origin. The solution? Click Don’t run and exit the installer right away.
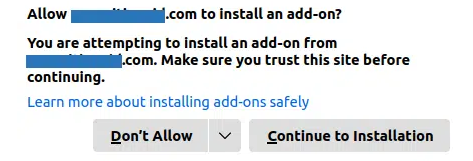
For those who would be tempted to go ahead with it anyway, all major browsers will also show a similar warning, like the example below from Firefox:
What if the .exe file has been signed? If the publisher used an extended validation (EV) code signing certificate, you won’t see a Windows SmartScreen Defender warning at all. Windows operating systems and Microsoft’s Edge browser will automatically trust the software.
Otherwise, if the code has been signed with an organization validation (OV) code signing certificate, Windows Defender SmartScreen and the User Account Control window will show you a pop-up displaying the publisher’s name.
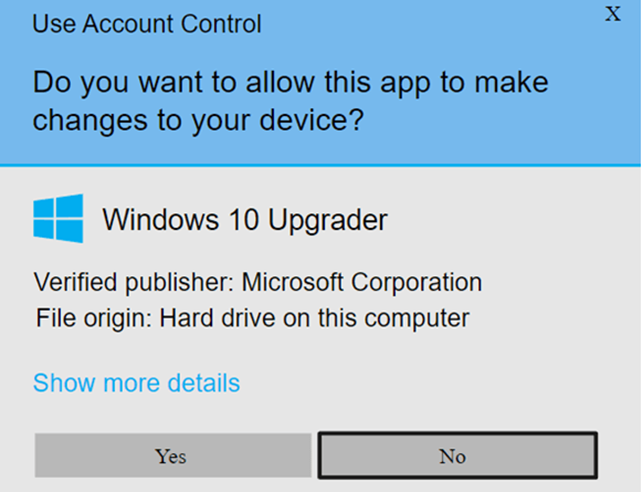
In both cases, the origin of the file has been confirmed and it looks legit. So far. But, as it’s always better safe than sorry, there’s at least one last key tip you may want to follow before finally running or installing the file. Which one? This is what we’re going to discover next.
Before we move on, though, do you want to learn more about how to check the digital signatures of a file signed by a code signing certificate? Discover how to check them in a breeze by following a few simple steps.
3. Scan All .Exe Files Using an Antivirus Program
Hold on, can’t expired or stolen code signing certificates be used for fraudulent activities? Yes, in certain cases (e.g., when signing Windows drivers). It isn’t easy, but that’s what happened in 2022 when attackers stole two Nvidia code signing certificates and used them to sign malware.
Want to avoid falling into such traps? After checking the .exe file’s code signing certificate, scan the file with your antivirus software or an online scanning tool. VirusTotal, for example. It’s free, and you just have to upload the file to know the verdict.

At the end of the day, the devil is always in the details. The more you check the authenticity and integrity of the files you download and install, the safer you are.
OK, all of that is good advice for users, but what if you’re a developer or a vendor?
Developers/Publishers: How Can I Prove My .Exe Files Are Secure?
Let’s say you are the manufacturer of luxury brand of watches. How do you prove to your potential buyers that the designer watches you’re selling are the real deal and not a copycat? By:
- Adding to your product your unique label and trademark.
- Including the watches’ serial numbers and certificates of authenticity to attest that the products are legitimate.
- Knowing key qualities of the watches (design, weight, ticking sounds, backing design, etc.) to assess its integrity so you can feel confident they haven’t been replaced by counterfeits.
- Selling the watches only in select shops that are licensed by you.
Right. But what about digital items? If you’re a developer or software vendor, you don’t sell physical goods, and counterfeiting something in the digital world is dead easy. An attacker just needs to access the file, right?
So, how can you prove the authenticity and integrity of something intangible like software? With code signing. As a matter of fact, using a code signing certificate to digitally sign your .exe files prior to release or distribution will be your best bet to:
Prove That Your Codes Are Safe, Original, and Malware Free
In Q1 2023, Avast blocked a stunning 61 million suspicious files. So, if the answer to the question “Are all .exe files viruses or malware?” is no, what’s the magic behind a digitally signed code that can help you prove it to your potential customers and users?
To sign an .exe file with a code signing certificate, a developer:
- Applies a secure hashing algorithm to the code to generate the hash digest (i.e., the hash value),
- Uses their private key to encrypt the hash value,
- Adds a time stamp (i.e., the exact time and date when the code has been signed), and finally
- Appends the signature block including the digest, code signing certificate, and the hash function to the .exe.
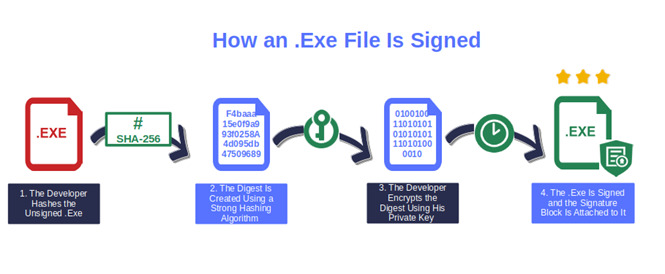
Bibbidi-Bobbidi-Boo! The code is now signed. From now on, the signature will prove that the .exe is:
- Original, and really made by you (i.e., authentic). Every time a user attempts to download the .exe file, your identity will be confirmed by the User Account Control or Windows Defender SmartScreen pop-up displaying your organization’s verified information (if you chose to use an OV certificate). Did you opt for an EV code signing certificate? Even better. The user will be able to immediately run the executable without any warning or annoying popup.
- Safe and malware-free (i.e., your file’s integrity is intact). Has your .exe file been tampered with by a malicious third party or replaced with malware? When the customer downloads the software, their operating system will automatically check if the digest it generates matches the one provided in the digital signature. If it doesn’t, the customer will be alerted.
Protect Your Brand and Organization Against Malware-Based Attacks
In 2022, 66% of organizations were hit by ransomware. 84% of those in the private sector lost customers and revenue due to the attacks. Code signing doesn’t only protect your users; it also shields your organization from malware infections and data breaches.
How? Imagine that you’ve just published a new, unsigned software on your corporate website. As it isn’t protected by a digital code signing certificate, all a cybercriminal has to do is replace the legit file with a malware-infected one. Voila’.
Imagine that one of your employees downloads the malicious file and attempts to run it, assuming it’s safe. They double-click on the .exe icon and ignore the “Unknown Publisher” or and ”Windows has blocked this software because it can’t verify the publisher” warnings. Now, that device and the network it’s connected to are compromised. If an attacker chooses to, they can now move laterally through your network to find other vulnerabilities to exploit and systems to compromise.
Yup, people ignore warnings sometimes, and when they do, boom. The damage is done. And it could spread all over the organization like fire in the wind. The consequences? Locked files due to ransomware, a data breach exposing your customers’ sensitive data, and your reputation going down the drain.
Code signing helps minimize the risk of your .exe files being tampered with or replaced. How? Remember when we briefly explained how code signing works earlier? To change your software, an attacker would need your unique private key and/or code signing certificate to resign it and apply a new hash. Otherwise, Windows Defender SmartScreen will notify a user that the file has been modified since it was signed.
Could a cybercriminal get their hands on your private key? Doing so is easier said than done; nevertheless, never say never. An attacker can get ahold of your code signing certificate’s private key if you don’t properly manage your certificate and key life cycle and securely store your key. Don’t despair, though. Ensure that your precious private key and certificates are stored and managed following a few unbeatable security tips and you’ll be good to go.
Protect Your .Exe Files During Development, Distribution, and Maintenance
Since 2020, software supply chain attacks have increased by an average of a walloping 742% year over year. “Everything’s not lost,” though, as the British band Coldplay sang. And they were right. According to the same report, 3.4 billion vulnerable downloads could be avoided each month. That’s approximately 40.8 billion vulnerable downloads per year!
Implementing code signing in every step of the software development life cycle (SDLC) can help shield your .exe files and software. It’ll also enable you to securely distribute and update all your codes, preventing forgery and tampering throughout your software supply chain.
Why would you want to do so? Because thanks to automation and the adoption of continuous integration/continuous deployment (CI/CD), software development has become faster than ever.
But, as the American frontiersman Wyatt Earp once said, “Fast is fine, but accuracy is everything.” if you aren’t careful (e.g., you don’t implement SSDLC), weaknesses and vulnerabilities can be easily overlooked. This makes any step in the software supply chain a perfect occasion to inject malware or modify code without anyone noticing.
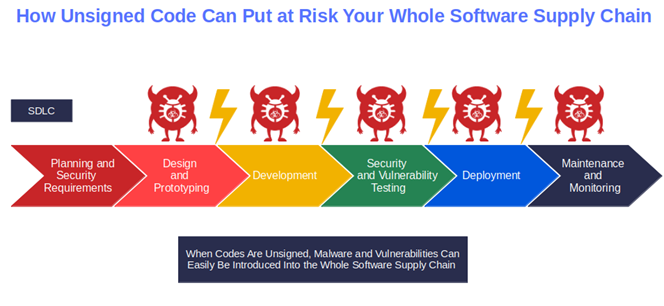
Let me give you an example. Remember the Kaseya ransomware attack? At the time, TrendMicro’s Managed Detection and Response (MDR) team identified two other examples of small businesses developing software for large organizations being attacked by cybercriminals “Kaseya style.”
In both cases, the malicious actors inserted malicious code into legit .exe files (e.g., agent.exe) in their systems. If not stopped, the malware infection could have spread to any organization using the software (cybercriminal’s main targets) and caused substantial losses.
As you can see, code signing matters and can make a difference.
Want to know more about code signing? Check the National Institute of Standards and Technology’s (NIST) white paper.
OK, I’m In. How Can I Start Code Signing My .Exe Files?
So, how do you sign your .exe files and avoid customers asking, “Are all .exe file viruses?” It’s easy — you just need to follow a very straightforward process. Before you do that, ensure you have the following:
- A valid (i.e., not expired or revoked) code signing certificate that was issued by a trusted certificate authority (CA).
- Microsoft SignTool installed on your Windows machine.
- A NIST Federal information Processing Standards (FIPS) 140 Level 2 approved cryptographic module (e.g., Thales SafeNet or Okta Single Sign-On).
Do you use Visual Studio? You can sign your .exe directly in it too! Visual Studio can’t find the certificate? Keep calm and carry on. We have a solution for that.
Last but, not least:
- Don’t use self-signed certificates to sign your .exe in production.
- Don’t forget to keep your keys and certificates safe! Attackers will attempt to steal those, too.
- Create a PFX certificate file to bundle your keys and certificate in a single secure file.
That’s all folks! Next time you have a doubt about the security of a file, or one of your customers asks you, “Are all .exe files viruses or malware?” you should:
- Think about code signing,
- Be aware of warnings,
- Remember to use antivirus and anti-malware software,
and answer with a smile: “Nope, not all .exe files are viruses after all.”
Final Thoughts: Avoid the Effects of .Exe-Based Viruses and Malware with Code Signing
.Exe files are simply program files that can be run as programs on devices; as such, they can be exploited by cybercriminals for malicious purposes. However, as we’ve just learned, there are tools at your disposal that can help users, developers, and software vendors drastically reduce the risks of attacks and infections. One of these is signing your software using a code signing certificate that’s issued by a trusted third party (i.e., a CA like DigiCert).
Therefore, if you’re a user, follow the zero-trust approach (i.e., never trust, always verify). Check the product code signing certificate every time you run a .exe file.
As a developer or a software vendor, you can use code signing to offer assurance about the authenticity and integrity of your codes by adding your cryptographic digital signature. This will protect not only your customers but your organization and brand reputation as well as the long run. Want even more security and privacy? Discover other two ways to use digital signatures to boost the level of security of your digital assets.


