How to Sign an EXE or DLL in Visual Studio 2022 Using SignTool

Code signing is a critical step in releasing secure, trusted software. Here’s a step-by-step guide to signing application executables or DLL files in Visual Studio.
Visual Studio simplifies software development and is essential for creating .NET applications. As developers increasingly distribute executable software, securing the exchange process is crucial. Code signing is vital to this security, protecting end-users and software distributors from malicious software and reputational harm. Code signing your application .exe and .dll files is essential when sending out executable content.
Before discussing how to sign an EXE in Visual Studio 2022, though, let’s briefly review what code signing is and why you should sign executables, DLLs, and other code in Visual Studio.
What Is Code Signing?
Code signing verifies the identity of the entity who released files and scripts and ensures that the code hasn’t been altered or infected with malware since signing. The process involves hashing and encryption and requires a code signing certificate. The sender encrypts the hash using their private key, and the recipient uses their public key to validate the signature. If the hashes match, the data is not tampered with, and if they are different, the file is compromised.
Code signing is a recommended software security practice and protects clients’ security and software creators’ reputations.
Let’s dive into how to sign an EXE using Visual Studio 2022. (Please note: This tutorial only covers how to sign an executable. This tutorial doesn’t cover manifest signing.)
Notice: It’s important to mention that the steps outlined in this article are the same for how to sign a DLL in Visual Studio. So, rather than write a separate article, we’ll address both how to sign an EXE and DLL in Visual Studio in this one.]
How to Sign an Executable or DLL in Visual Studio 2022
Looking for a video to walk you through the process of signing these files in Visual Studio? Look no further:
Of course, not everyone likes watching video tutorials. If you want a step-by-step guide to skim, then keep reading because we’ve got you covered.
Step 1: Purchase and Install a Code Signing Certificate
To sign an executable or DLL file in Visual Studio, the first thing you will need is a built-out executable you would like to sign. Next, you will need to obtain a code signing certificate from a trusted certificate authority (CA). (If your organization does not currently possess an organization validation (OV) code signing certificate or an extended validation (EV) token-based code signing certificate, you can purchase one here at CodeSigningStore.com.)
Once you get a code signing certificate, you’ll need to install the certificate into the Windows Certificate Store before proceeding with this tutorial on how to sign an EXE or DLL in Visual Studio.
Learn How to Install a Certificate in Windows
Please note that starting June 1, 2023, new regulations will become effective that specify new OV code signing certificates and keys must be sent out on a physical token by default. (Storing certificates and keys on a hardware security module, or HSM, will also be an option in specific use cases.)
Step 2: Open Your Project in Visual Studio
Once you open Visual Studio, the next step will be to navigate to your project dashboard and open up the relevant project.
Step 3: Open PowerShell
Go to search bar or hit Ctrl+Q and look up “Developer PowerShell.”
The PowerShell terminal should open with the file pathway to the project you are working on. The executable you’re trying to sign should be in the folder that the pathway points to. If not, use the cd command to switch directories before proceeding.
Once you have PowerShell open, it should look like this:
Step 4: Use SignTool to Sign Your Executable or DLL File
The command line should show the file pathway to the folder of the current project you’re working on. Make sure that the .exe or .dll file you want to sign is in the destination folder — otherwise, this command will not work. (Remember: the directions are the same regardless of whether you’re signing an EXE or DLL file.)
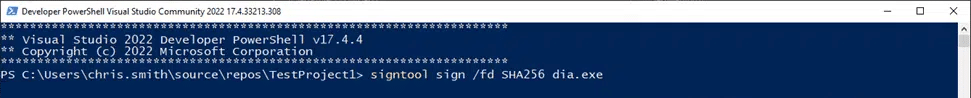
To sign the file, we’ll use a tool called SignTool, which comes preinstalled in the Developer PowerShell of Visual Studio. This first command will automatically sign a file using your store’s best certificate. The command is as follows:
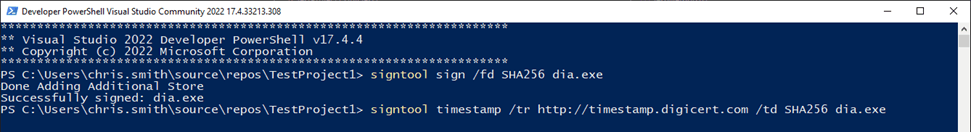
signtool sign /fd SHA256 dia.exe
In this case, our test project is a file named dia.exe. We’ll use this example file throughout this article.
What if you’re signing a DLL file instead of an EXE? No worries, the process will look virtually identical. Simply change the file extension in the command and continue with the process:
signtool sign /fd SHA256 dia.dll
How to Specify Which Certificate to Use in SignTool
What if you have multiple code signing certificates in your certificate store? No worries — there’s an easy way to specify which certificate you want to use. Simply use the following command:
signtool sign /n “My Company Certificate” /fd SHA256 dia.exe
That’s it! This command will enable you to sign your DLL or EXE file in Visual Studio. Now, it’s time to move on to the next step.
Step 5: Add a Timestamp to Your Executable
After the file has been successfully signed, it’s a code signing best practice to timestamp your signed files. This ensures that the digital signature will remain valid even after the certificate expires. For this example, we’ll use a DigiCert timestamp server to complete the following command.
signtool timestamp /tr https://timestamp.digicert.com /td SHA256 dia.exe
If you’re trying to sign a DLL file, the process will look virtually the same. Simply swap out the .exe for a .dll in the following SignTool command:
signtool timestamp /tr https://timestamp.digicert.com /td SHA256 dia.dll
Step 6: Verify the Code Signing and Timestamping Were Successful
Now that we have signed and timestamped our executable, we need to verify that this process was successful. To do that, enter the following command:
signtool verify /pa example.exe
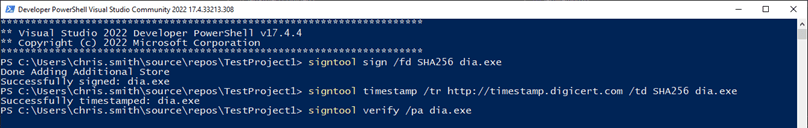
The resulting SignTool response you’ll see in PowerShell should look something like this:
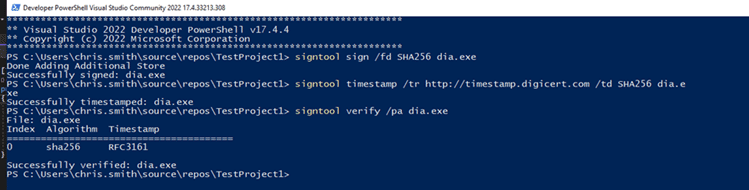
Why Is Code Signing Your EXE or DLL in Visual Studio Important?
Cybercriminals are more savvy and more organized now than they have ever been. In recent years, they have been able to successfully attack companies around the globe at devastating costs. Many of these companies send code to clients in the form of scheduled software updates and patches. This represents a huge opportunity for threat actors to infect many victims’ devices with malware, malicious scripts, and other damaging agents.
A successful attack of this nature could:
- cause significant financial losses,
- lead to potential litigation, and
- result in permanent damage to a company’s reputation.
Code signing your application executables or DLL files from the very beginning in Visual Studio is a great way to help mitigate these risks. This also prevents the “Unknown Publisher” pop-up that displays when trying to install unsigned code in Windows. This warning causes confusion and can result in a loss of trust among users.
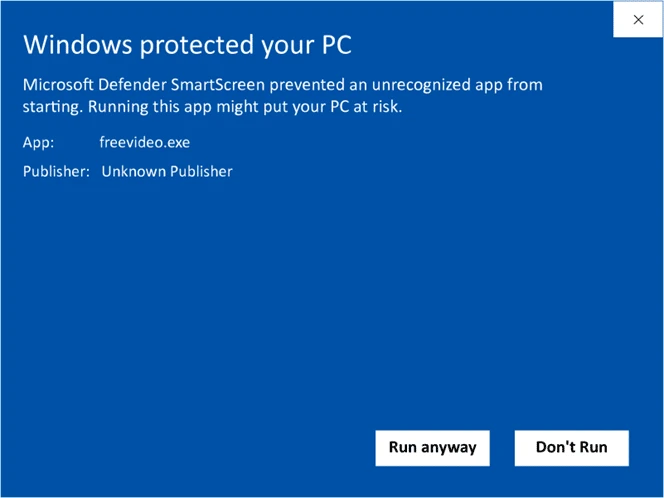
Code signing solves this problem by creating a standardized way of authenticating software releases and protecting clients and customers from the pervasive security threat in cyberspace. It’s a win-win for you and your software users.
Final Takeaways on Code Signing for EXE and DLL Files in Visual Studio
Code signing is an integral part of modern software distribution security. It’s a NIST-recommended security practice that, when implemented securely, ensures data integrity and authentication. This is needed now more than ever as cybercriminals continually seek new exploits in an ever-growing attack surface that includes development pipelines (such as the distribution of software updates).
By integrating code signing into your software security strategy and practices, you now have the tools you need to protect your organization, customers, and reputation.
Please check back on this blog for more useful content. You also can buy a code signing certificate at CodeSigningStore.com and enjoy significant savings on your purchase!
For more information on signing executable files, check out available resources:
- How to Digitally Sign Executable Files and Why It’s Important
- What is Microsoft SignTool and How Can I Use It to Sign Executables?
- How to Sign an EXE or Application in 5 Steps
- How to Sign Executable Files With a Code Signing Certificate
Save 21% – Code Signing Certificates
Protect Software Code & Avoid Pesky Warnings


