What Happens When You Use or Release Unsigned Code or Software?
Have you published or downloaded code today? Did you know that 79.1% of the malware samples reported to Spamhaus in October 2022 were infected .exe files? Discover the potential consequences of releasing or downloading unsigned codes. Find out if, in the digital “wild west,” there’s still a place for unsigned software. Because what you don’t know can hurt you…
In 3Q 2022, cyber attacks increased by 28% compared to 3Q 2021, bringing the average number of attacks per organization worldwide to over 1,130 per week. In the first half of 2022 (January-June), SonicWall identified 2.8 billion malware attacks, totaling an average of 8,240 malware infection attempts per customer in that period. This is an increase of 11% compared to the same period in 2021.
Discover how publishing or downloading unsigned software can put you as a developer, organization, or user one malware infection away from becoming the next cyber attack victim statistic. Learn everything about the risks associated with releasing or using unsigned code or software. Because once you know the risks, then better equipped you are to prevent them.
What Is Code Signing?
Code signing is a process that enables a developer to add their digital signature to a software, code, executable, or program update so that its authenticity and integrity can be verified before installation. Thus, a user downloading the code can be confident that:
- It’s coming from a legitimate author, and
- It hasn’t been modified by a malicious third-party (i.e., it’s safe to install).
On top of that, if the developer used an extended validation (EV) code signing certificate, the user’s operating system and browser will automatically trust it.
Think of it like the wax seal on an addressed envelope: it tells you who sent it and if it has been tampered with. Cool, safe and convenient, eh? But what about unsigned software? What happens when you publish it or download it? Let’s find it out!
| Dangers of Releasing Unsigned Code |
|
| Dangers of Using Unsigned Software |
|
What Are the Dangers of Releasing Unsigned Code as a Software Developer or Publisher?
Every time I talk about code signing certificates, I always remember the conversation I had about it a few years ago with a friend I met at a cybersecurity convention. At the time, he was working as a software developer for a start-up.
I always perceived him as a very security-conscious guy; therefore, when he told me that his company typically unsigned software, it struck me. I asked him why he would do that. He replied that the costs — in terms of time and money involved in signing the software and managing code signing certificates and keys — were too high for a start-up.
That’s understandable, I thought, but still not good enough to justify it. Why? Releasing even a single unsigned code or script could cause a data breach if it were to become altered by a cybercriminal. Do you know how much such a data breach could cost? According to IBM’s 2022 report, the global average data breach cost in 2021 was $4.35 million. That’s an arm and a leg for a start-up and many organizations. Therefore, as stubborn as I am when it comes to cybersecurity (I know, I can be worse than a mule sometimes), I started to rattle off a few examples.
You Leave Your Software Supply Chain Open to Attacks
As a software provider, you need to know that your software supply chain is as secure as possible. Otherwise, you risk malware and other threats infiltrating your software supply chain that can lead to a host of other security issues for your vendors, operators, and consumers.
With a 742% average annual increase in software supply chain attacks over the past three years, and 62% of surveyed organizations impacted in 2021, software supply chain attacks are becoming a serious issue. And guess what? To carry out these attacks, cybercriminals rely on the possibility of being able to edit the code, disguising it as safe, and then exploiting the trust the users have in the code’s publisher.
Using this approach, attackers can infect entire organizations with malware or access their sensitive data, servers and other IT environment resources.
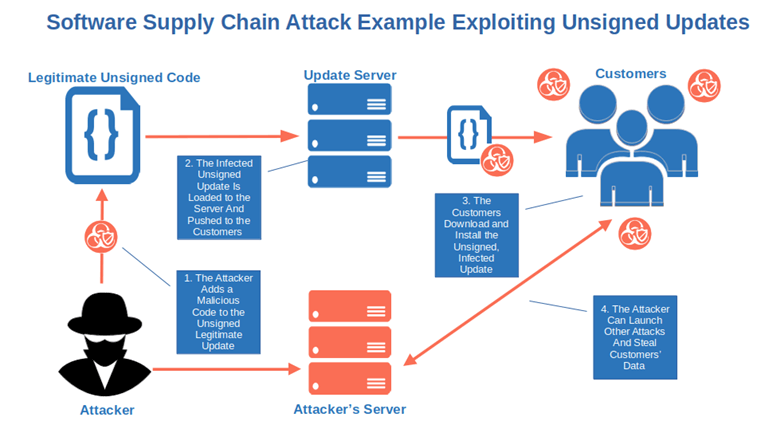
Want to know more? Check out this video talking about three case studies of software supply chain attacks.
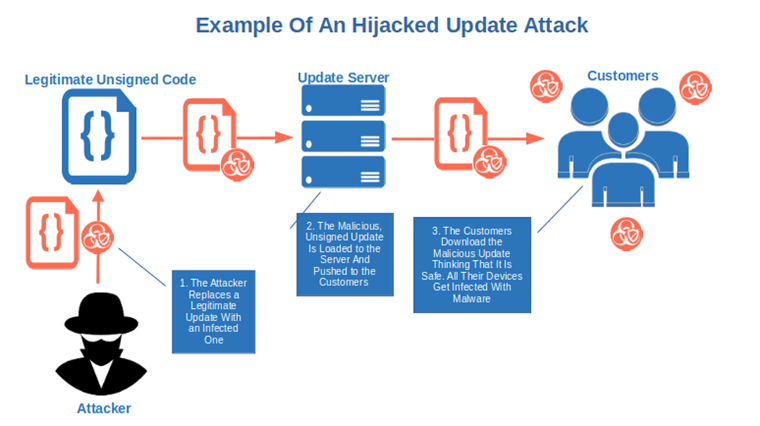
Someone Could Hijack Your Software Updates and Patches
What if you release a software update for your most used app and, as the update isn’t signed, an attacker replaces it with an infected code? All your users will install it thinking that it’s genuine and malware-free. Thus, their devices will be infected with malware unleashing cybersecurity mayhem.
The same can happen with any firmware and, according to Eclypsium’s 2000 research, the consequences can be humongous.
Vulnerabilities Could Lead to Data Breaches For Your Consumers (or Your Customers’ Customers)
We’ve already said that a data breach can cost many a pretty penny. In addition to containment and recovery measures, you’ll also have to add the cost of potential legal fines due to security and privacy legislation (e.g., the European Union’s General Data Protection Regulation [GDPR] and the U.S.’s California Consumer Privacy Act [CCPA]). And who is going to pay for that in the end? According to IBM, your customers — or, at least, those who are left (more on that in a moment).
In fact, 60% of businesses that suffered a data breach had to raise their prices. How do you think your customers would react? If you’re lucky, many will “just” moan and groan; some will take their money elsewhere. But in some situations, you could lose a big chunk (21% according to Thales’ survey) of your revenue and customers.
Do you think it won’t happen to you? Maybe, but in the first three quarters of 2022, the Identity Theft Resource Center (ITRC) recorded more than 166 million victims and AT&T customers were among them. If it happens to big companies, why couldn’t it happen to your organization?
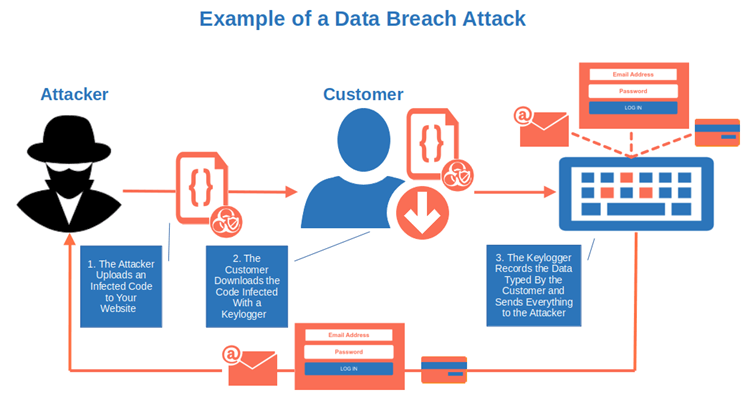
Your Users and Customers Could Get Infected By Malware
In the first half of 2022, Trend Micro identified over 22 billion malicious files, nearly four times more than in the same period in 2021. If your code isn’t protected by code signing, bad guys can easily inject malware into it or exploit it to their advantage by enabling their inserted code to download and run unsigned payloads once installed.
A similar situation was identified by Trend Micro in a Zoom installer bundle. Want another real-life example? Check out Charlie Miller’s test he did with Apple’s AppStore:
Among all malware types, ransomware has become a huge concern for organizations worldwide with an average ransom payment of $1 million. The same report shows that, despite having spent an average of $6 million in 2021 alone on ransomware mitigation resources to combat these attacks, 80% of companies have been hit by ransomware. Do you really want to risk becoming one of those statistics?
Find out how ransomware works in this entertaining short video published by the Federal Trade Commission:
Cybersecurity Incidents Could Impact Your Revenue and Damage Your Reputation
From software supply chain attacks to malware infection, every point enumerated until now has its consequences. Loss of revenue and reputation are two of them. A new study from ISACA showed that nearly one out of three customers stopped buying from businesses that were targets of data breaches.
What about reputation? Varonis analyzed the consumers’ perception of two big companies (Target and Uber) after each separately suffered data breaches and found out that the pain lasted for years.
Security Warnings Could Negatively Affect Your Customers’ Trust and Result in Poor Experiences
When you sign a piece of software or executable with an EV code signing certificate, it’ll be automatically trusted. Thus, the users won’t see any security warning before installation. On the other hand, if they try to download and install unsigned software, Windows will automatically show the dreaded “unknown publisher” warning pop-up. This will affect their experience as users and their trust in the publisher or developer.
Did you know that according to a study we did, only 5% of interviewed users said they’d still install software if they’d see that warning? That’s a major drop in installations, right?
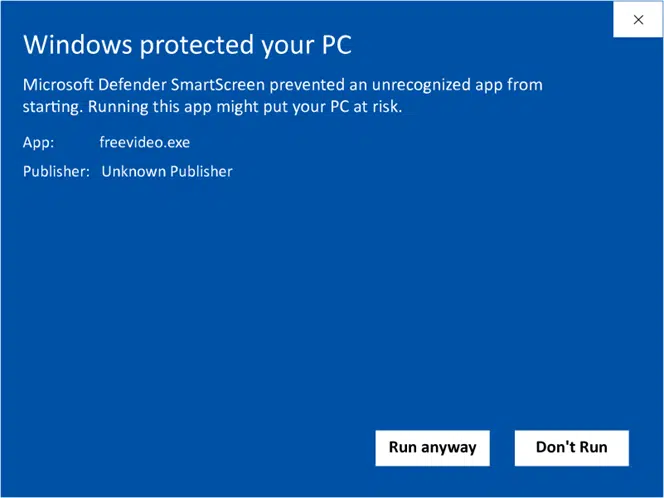
This is the pop-up warning that your customers and users will see every time they download and install unsigned code, software, drivers, or executables.
The list could go on, but it goes without saying that, by the time I was done with my examples, my friend decided to have a chat with his boss. After a few months, I met up with him again. He proudly told me that all of their software was signed and they’d even added a software bill of materials (SBOM) to avoid issues with third-party components.
But what about the users? What are the dangers somebody like you, me, or your mom could face when downloading unsigned software? This is what we’re going to discover next!
How Does Unsigned Software Put Users at Risk?
Once upon a time, end users could trust the software they downloaded. Today, things are very different. Cybercriminals have become incredibly skilled at the art of spreading malware. They’re so clever that, sometimes, even techies find it hard to determine whether code has been manipulated. And it gets even worse with automatic software updates…
When downloading unsigned code, end users could find themselves one or all of the following scenarios:
They Could Download and Install Infected Software/Code (i.e., Suffer a Malware Infection)
As if getting a malware infection wasn’t bad enough, in some cases, you’ll get a horrible “deal” that you never asked for: Two for the price of one! In this case, a two-for-one isn’t a good bargain, though, as the second item might be a virus that could transform your device into a bot and become part of that 63% of bad bots‘ internet traffic. You don’t know what a botnet is and how it works? This entertaining short cartoon explains it.
The unsigned code you’ve just downloaded could also contain spyware or another nasty piece of software — malicious code, basically. Malicious code is considered the top cause of data breaches and security incidents by 31% of chief information security officers (CISOs) interviewed by Deloitte and NASCIO.
They Could Suffer a Data Breach and Get Their Credentials Stolen
Cybercriminals simply love credentials, as confirmed by Verizon’s Data Breach Investigation report 2022. They’re their favorite attack vector to get access to sensitive information and devices. How much of a risk is it for you? Judge it for yourself.
In 2021, SpyCloud recovered 13.8 billion stolen personally identifiable information (PII) data records, which is 200% more than the previous year. In the same year, the Federal Trade Commission (FTC) recorded 1,434,676 identity theft reports. By the way, credential theft is one of the costliest attacks to remediate for organizations, costing an average of $804,997, according to Ponemon Institute’s research. As a single user, it won’t cost you as much, but don’t underestimate it.
Imagine what could happen if an attacker got hold of your online banking ID and password. You’d join those 42 million American consumers who fell victim to identity fraud and lost $52 billion in total losses in 2021 alone.
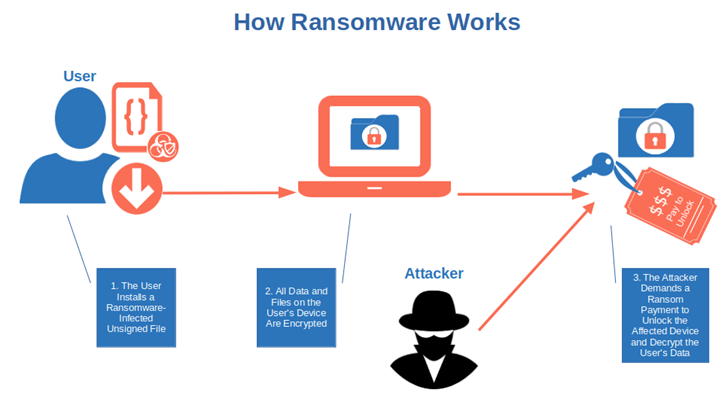
They Could End Up Being Victims of Ransomware Attacks
How would you feel if you’d be literally blocked from accessing all your files on your device forever, or until you pay a hefty ransom? In the first half of 2022, one out of 40 organizations worldwide had that experience. As an individual, you probably won’t have to pay as much in ransom (the same can’t be said for businesses and organizations, each of which could face thousands or millions of dollars in ransomware demands), but it isn’t going to be a picnic, either.
How can it happen? Unfortunately, it’s pretty easy, and downloading unsigned codes can only increase the chance of being infected with some kind of ransomware malware (e.g., LockBit, BlackCat, or Black Basta). If this wasn’t enough, attackers nowadays have it even easier than ever with the proliferation of ransomware as a service (RaaS) offerings. A business model based on software as a service (SaaS) where even the less skilled hacker can rent ransomware software for a small sum.
Despite all the precautions, you’ve been hit by ransomware? Fear not — you might still have a chance to recover your files without paying a dime. EUROPOL put together a collection of 136 free tools to help you recover your files. Give it a try — it might be your lucky day.
Final Thoughts on What Happens When You Use or Release Unsigned Code or Software
Malware, ransomware, decreased customers’ trust, and reputational harm — these are just a few of the real dangers that organizations and users face every time they release or use unsigned code or software.
OK, code signing won’t guarantee you 100% hacker protection, but the truth is that nothing can do that in the digital world. Code signing can be a valuable ally in the war against cyber attackers so long as you:
- Use code signing and manage your certificate(s) correctly (e.g., don’t forget to add timestamping to it),
- Don’t assume that it’s foolproof,
- Don’t use a self-signed code signing certificate in production, and
- Follow code signing best practices and the National Institute for Standards and Technology’s (NIST) recommendations.
So, what do you think? Are you still prepared to gamble it all to publish or download unsigned software just to save a few bucks? The choice is yours!


