Code Signing Certificate Expired? Here’s What This Means For Your Business
Errare humanum est: To err is human. With organizations managing more than 50,000 certificates, it’s easy for one to slip through the net. And the consequences can be rough. Don’t bury your head in the sand. Learn what happens when a code signing certificate expires so that when and if it happens to you, you’ll know how to overcome the challenge
Has your code signing certificate expired because you forgot to renew it? You’re not alone. In fact, 81% of organizations interviewed by Keyfactor experienced one or more expired certificates within the last 24 months. And with the use of PKI growing dramatically, like in the case of the M&T Bank which went from 2,000 certificates to more than 350,000, businesses are really struggling to keep their cryptographic resources under control.
Software is increasingly becoming the driving engine behind many businesses. As software supply chain attacks skyrocket, the pressure to secure those supply chains is growing by the day.
But what does an expired code signing certificate really mean for an organization? What are the consequences your business may face? And why do code signing certificates expire anyway? Explore the answers to these questions and more. Follow us down the rabbit hole of the expired code signing certificates!
Why Has My Code Signing Certificate Expired?
This is the question a PKI admin asks when something like this suddenly happens. When it does, they instantly know that it’s going to be a bad day. Does it sound familiar?
I remember that Friday pretty well. Of course, these things usually happen on a Friday afternoon when everybody is ready to go home and can’t wait to enjoy the weekend. We were at the end of an important project — a brand new app we’d built was supposed to go live the following week and everything, as far as we know, was ready. The developers just had to sign the app. That’s when disaster struck: the code signing certificate expired the week before and no one noticed.
How could it happen? To cut things short, our PKI admin simply missed the certificate expiring warning emails sent by the issuing certificate authority (CA). When you receive hundreds of emails daily and rely on those to help you manually manage more than 4,000 certificates, missing an email is easy. And if you don’t have a proper certificate management processes, policies, and tools in place, it’s just an accident waiting to happen.
So, why can’t we just have lifelong code signing certificates that never expire? You buy them once and then forget about them. That would make things so much simpler! Yes, it certainly would from a certificate management perspective. But it also makes attacks easier for cybercriminals. Why?
- Trust doesn’t last forever. Code signing certificates are issued only after the CA has verified your identity and ensured that you’re a legitimate business. But these days, things change fast. Organizations take new names, go out of business, or get new owners. Anything can happen. So, how can a CA, after three years (this isn’t an arbitrary number; it’s the actual code signing certificate maximum lifespan period), know that nothing changed and that you’re still trustworthy? Through certificate revalidation. Your customers will be sure that they can still trust you, even after a few years or if your organization’s name has changed.
- Technology and security standards evolve. In the digital world, everything is constantly transforming; this includes attackers and, consequently, cybersecurity itself. Key lengths change, algorithms get deprecated (like in the case of SHA-1), and attacks get more sophisticated. Therefore, when a certificate expires, you’ll be issued a new one that complies with the latest security standards, giving you and your customers additional peace of mind.
- Using the same old key pairs can be dangerous. Renewing a certificate presents a great opportunity to create new key pairs, as suggested by the National Institute of Standards and Technology (NIST). Why should you do that? It’ll help you mitigate the risk of a data breach. Think about it. Let’s say an attacker managed to get hold of one of your keys without you noticing it. By changing them regularly, you’ll automatically reduce the period within which the attacker can use that key for malicious purposes.
What do you think? Aren’t these three very good reasons why code signing certificates should expire? I think so, even if the consequences of an expired signing certificate sometimes can be rough. Let’s go deeper down the rabbit hole and find out what this could mean for your organization.
What Happens When a Code Signing Certificate Expires?
The answer is nothing good. When you open your fridge and find out that the only container of yogurt left expired, it may be disappointing but it isn’t a big deal. If you eat it anyway, it may just upset your tummy. If you throw it away, you’ll just have to spend a couple of dollars to buy a new one.
When a code signing certificate expires, things aren’t so simple; the consequences your organization may suffer could be much more serious. The news is full of examples, like the most recent one, when a group of hackers called Lapsus$, managed to get hold of two Nvidia’s expired certificates and used them to sign malware. Hold on, they shouldn’t be able to sign new codes with an expired certificate, correct? Not quite. In fact, Windows still allows using them to sign some drivers. This creates a good opportunity for attackers to exploit this loophole.
Talking about money, the picture looks even darker. Venafi and Air Worldwide Corporation have estimated the global losses due to poorly protected machine identities (including PKI certificates) range between $51.5 and $71.9 billion. No wonder PKI admins are so stressed out when even one certificate expires!
But is it always so critical when a certificate expires? And how bad can it be if you don’t renew it on time? This is what we’re going to find out next.
What Are the Risks of an Expired Code Signing Certificate?
In addition to the examples we’ve just mentioned, there are many other ways an expired code signing certificate may impact your organization. Among them:
- Lower download numbers. Let’s put yourself in your customer’s shoes. You’re trying to download a new app. You click on the download button and a pop-up comes up warning you that the code’s signature validation failed. What would you do? I guess you’d stop the download and get the app from a more reliable website or vendor. Like 75% of Americans who wouldn’t purchase from a digital brand if they don’t trust it. How can you blame them? And this takes us to the next point.
- Decreased trust. Trust is a very fragile thing. You have to work hard to earn it; trust takes time to build it, but it can be easily broken. And when it breaks, getting it back it’s even harder. The same survey from Okta confirmed that 47% of American respondents would stop using an organization’s service for good after a data breach. Can you imagine losing 47% of your customers only because of a missed email?
- Losses of sales. Lower download numbers, decreasing trust. This downward spiral can only lead to a loss of sales and thus, revenue. Traffic to your website will plummet, and the majority of your customers will take their money elsewhere. This isn’t a good perspective in today’s competitive world.
- Damaged brand and reputation. Recent research from 1440 found that 78% of customers decided against purchasing a product after reading a negative review. This shows the level of impact a single negative review can have on your brand’s reputation. Now, imagine what could happen if your organization would be the victim of a data breach because of an expired certificate. Because bad news travel always fast.
- Security risks due to exploits and infection. That’s exactly what took place during the Nvidia attack mentioned at the beginning of this article. As it’s still possible to sign some Microsoft drivers with an expired certificate, even for the less experienced attacker, signing infected codes and distributing them all over the network would be a piece of cake. And if some of your employees download them, your devices would also be infected.
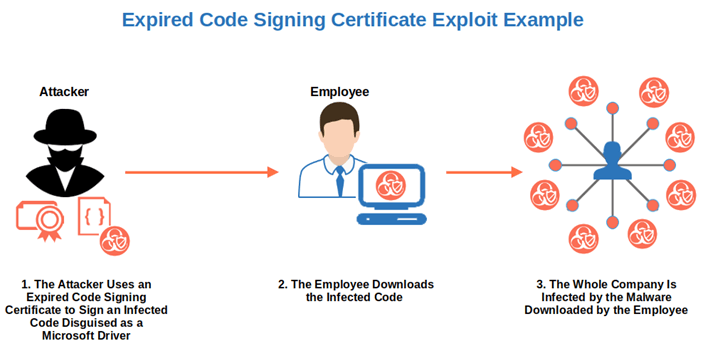
- Higher risk of security incidents. 52% of the IT security experts interviewed by Ponemon for an AppViewX report confirmed that their organizations experienced a security incident or data breach caused by an attack due to a compromised digital certificate. Expired code signing certificates are less secure and, thus, much more prone to being compromised by attackers. How easy would it be for a cybercriminal to get access to your organization by exploiting an old code signing certificate that’s still using a deprecated algorithm? I guess you already know the answer.
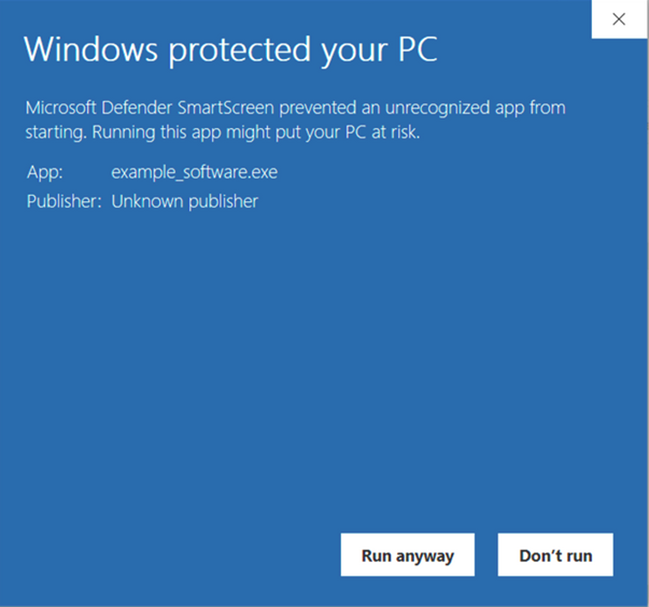
- The Microsoft SmartScreen warning is back. Did you invest some of your hard-earned dough in an extended validation (EV) code signing certificate to get rid of the “Unknown publisher” warning but forgot to renew the certificate? Surprise! The warning is back and it’ll stay with you until the situation is rectified. Why? As you won’t be able to sign new codes, you’ll have to publish them unsigned. As a result, every time one of your customers downloads the new, unsigned code, they’ll be presented with a warning. That isn’t very inviting for customers looking to download your applications.
Does this list answer the question about the risks your organization could face with an expired signing certificate? I hope it does. But, before we move on to discover what you’ll have to do to get out of this mess, I also want to talk briefly about timestamping. Why? Because I know that some of you may ask:
Why Is Timestamping a Solution That Helps When My Certificate Expires?
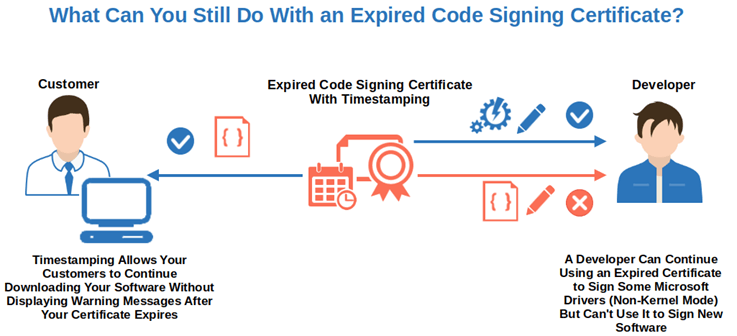
Timestamping is a workaround that benefits you when your code signing certificate expires. ‘Workaround’ pronounced ˈwərk-ə-ˌrau̇nd. A plan or method to circumvent a problem (as in computer software) without eliminating it. Merriam-Webster dictionary. This is because time stamping allows you to attach the exact moment when you digitally signed your code. This enables your software to be trusted by browsers and operating systems well after the certificate has expired.
This is exactly what timestamping is in case of an expired code signing certificate. Don’t get me wrong, timestamping is indeed a vital part of a secure code signing process and it shouldn’t be omitted. However, when a certificate expires, it allows the software you signed while the certificate was still valid to be trusted well beyond the life of the certificate. This means that users won’t see the ugly warning messages they’d otherwise see when your certificate expires.
Time stamping doesn’t change anything regarding signing new software with an expired certificate; it only allows you to prove that your certificate was still valid at the time of signing.
Got it? Timestamping can be a precious ally for a PKI administrator. It can keep you out of trouble until you don’t have to sign new software, or until you have renewed the certificate. Be careful, though, timestamping is a useful tool, but it isn’t the panacea for all expired code signing certificate ills.
As a matter of fact, there isn’t a magic bullet for an expired code signing certificate. Either you renew it before its expiration date or you deal with the repercussions once it’s expired. So, how can you deal with it before it becomes an issue? Let me show you the best ways to do it step by step.
I Have an Expired Code Signing Certificate. What Can I Do?
When your code signing certificate has already expired the only way to fix the issue is to buy a new one. This means that you’ll have to go through the whole process you followed the first time you bought it. And, depending on the certificate, it might take some time. What are the steps to follow?
| Expired Code Signing Certificate – How to Re-Purchase It | Expiring Code Signing Certificate – How to Renew It |
|---|---|
| 1. Purchase a New Code Signing Certificate. | 1. Renew the Code Signing Certificate. |
| 2. Go Through the CA’s Full Validation Process. | 2. Go Through a Quick Verification. |
| 3. Get Your Certificate and Install It. | 3. Get Your Certificate and Install It. |
1. Purchase a New Code Signing Certificate
Select the code signing certificate you need (i.e., extended validation [EV] code signing certificate or organization validation [OV] code signing certificate) and fill in the order form with the information required.
In some cases, after your order has been placed, you may have to generate and send a certificate signing request (CSR) to the CA. There are various methods you can follow to generate it:
- Using OpenSSL.
- Using DigiCert’s certificate utility.
- Using Java KeyStore (for Java code signing certificates only).
- Using a CSR generator.
On top of that, all OV code signing certificates purchased starting in mid-November (2022) will have to comply with the CA/Browser Forum’s (CA/B Forum) new requirements. We’ll speak more on that in a few moments.
2. Go Through the CA’s Full Validation Process
Once your order is completed, the CA issuing the certificate will have to verify that your organization is legitimate and authenticate you. If you’ve chosen an EV certificate, the vetting process will take a bit longer as it involves a more rigorous background check. Curious about the process? Check out the following resources for additional information:
- DigiCert validation process – OV Code signing certificate.
- DigiCert validation process – EV Code signing certificate.
- Comodo validation process – OV Code signing certificate.
- Comodo validation process – EV Code signing certificate.
- Sectigo validation process – OV Code signing certificate.
- Sectigo validation process – EV Code signing certificate.
3. Get Your Certificate and Install It
Validation completed? Great! The CA will send you an email with the installation instructions. Follow them and you’re done. Did you purchase an EV code signing certificate? In that case, you’ll also receive a USB hardware token that you’ll have to insert into your device to sign your software. Starting Nov. 15 (Nov. 14 if you’re located in North America), the OV code signing certificates and their private keys will have to be stored on a hardware security token.
There you have it. This is the re-purchasing process to follow if you find yourself with a code signing certificate that’s expired. Now you’re ready to start signing your codes again.
But what if your certificate is still valid for a few more days? Hurry up and start renewing it now! Why?
- It’ll keep your codes protected. As it always takes a few days to issue the certificate, by renewing it while it’s still valid, you won’t risk being unable to sign and distribute your codes.
- It’ll save you some time as you won’t have to go through the whole validation process all over again.
To start the renewal process:
1. Renew the Code Signing Certificate
Log in to the provider’s website where you bought your code signing certificate the first time. On the page listing the certificates you own, there should be a “Renew now” button (or something similar). Click on it and fill in the order form with the information required.
Do you own an OV code signing certificate and want to upgrade it to an EV? You can do that. Just select the certificate you want. Don’t forget, though:
- EV code signing certificates have more stringent requirements. For example, EV code signing validation requirements state that your organization has to be in good standing and must exist for a specific minimum amount of time.
- The EV code signing certificate will require a more thorough verification. Therefore, it may take longer for you to receive it.
- A physical token (usually a USB) will be sent to you in the mail. This device enables you to securely store your private key and sign your codes. (NOTE: This token requirement will come into play starting in mid-November 2022 for OV code signing certificates as well.)
Is it worth it? Generally, yes. When you re-purchase or renew an OV code signing certificate or an individual validation (IV) one, you’ll always have to spend time establishing or rebuilding its Microsoft SmartScreen reputation. Therefore, when you renew your code signing certificate, you may want to spend some time carefully evaluating your options.
Last but not least, if you’re required to send a CSR, you can use the one you generated to place your first order or create a new one.
2. Go Through a Quick Verification
The CA will perform a quick cross-check verification to confirm that your organization is still legitimate and that the information is still valid. In case anything has changed, you may be requested to provide new documentation.
3. Get Your Certificate and Install It
The CA will issue the new certificate. To continue signing your software, make sure you install it as instructed in the email received from the CA.
That was easy and painless, right? By the way, did you know that even if you start the renewal process 90 days before the expiration date, the remaining time on the old certificate will be added to the new certificate? That’s great, right? So, next time, don’t wait till the last minute to renew your certificate. Because the early bird gets the worm!
Final Thoughts on Code Signing Certificate Expired? Here’s What This Means for Your Business
Code signing certificates don’t last forever. They have a maximum life span of three years; then they expire. And when they do, the consequences can have a heavy toll on your business (and for your customers as well if your certificates’ private keys fall into the wrong hands).
In the best-case scenario:
- Your software won’t be trusted by your customers’ browsers and operating systems anymore, or
- You won’t be able to sign any new code with it.
But it can get worse if attackers manage to replace your executable with malicious software and get it out to the public. This means that customers will no longer trust you and your brand and reputation are likely to take a significant hit.
From now on, make sure you renew your code signing certificates well before their expiry date by following certificate management best practices. It’ll save you a lot of hard work, sleepless nights, and money in the long run. Show your customers you’re serious about security by demonstrating that your codes and organizational identity are valid and protected at all times. What will you get in return? Peace of mind, your customers’ trust, and, perhaps, their returning business.


