Secure SDLC: A Look at the Secure Software Development Life Cycle
42% of cybersecurity professionals interviewed by Cisco consider the growing number of application vulnerabilities one of their top concerns. Discover how to take your software development life cycle to the next level by joining the secure SDLC revolution
The Cybersecurity and Infrastructure Security Agency (CISA) has warned organizations that Log4Shell will remain a threat for at least the next decade. That’s a very long time in the world of digital security. So how can you deliver more secure applications when:
- The level of global malware attacks reached new highs in the first half of 2022, and
- Only 14% of developers see application security as a chief priority?
Wouldn’t it be amazing if there was a way to make the software development life cycle (SDLC) more secure? Hold on, there is! It’s called secure SDLC.
This article will share how to ramp up the security of your SDLC process to deliver high-quality and highly secure applications without sacrificing speed or agility. Discover the phases of the secure SDLC that’ll help you stand up to attackers who want to tarnish your good name and reputation. It’s payback time.
What Is Secure SDLC?
Welcome to the future of development security: the secure SDLC (or SSLDC as it’s sometimes written). What is it? Secure SDLC is the evolution of the classic software development life cycle process. It integrates security in all steps of the development journey, ensuring that all teams involved take into account the functional requirements of the project and its security aspects.
How Is Secure SDLC Different From the Traditional SDLC?
Fundamentally the difference is made by the level of importance given to security. Let’s have a look at the table below for a quick overview:
| Traditional SDLC | Secure SDLC |
|---|---|
| The focus is on developing efficient, and productive applications at minimum costs and as fast as possible. | The focus is on developing secure applications without having an impact on costs, time of delivery, and efficiency. |
| Security testing and secure coding aren’t included in its process phases. | Security testing and secure coding are fundamental parts of the process. |
| Testing comes toward the end of the process. | Testing starts at early stages and continues throughout the whole process. |
| Security is an afterthought. | Security is incorporated at every stage of the life cycle. |
The Traditional SDLC
In traditional SDLC, security is the Cinderella of the story, considered a nuisance and always left behind. And it doesn’t matter which SDLC model you select (e.g., waterfall, agile or continuous integration and continuous delivery/continuous deployment or CI/CD), often security remains an afterthought
Since most security flaws are identified later in the cycle or at the very end, fixing vulnerabilities is usually expensive and difficult. Often it might even end up delaying the time of delivery of the software. As a result, the code released to the users or customers is generally insecure and still packed with vulnerabilities that are waiting to be addressed. Found a bug in production? With traditional SDLC, the code is sent back to the beginning of the project and you’re back to square one, just after product release. This isn’t good for you or your customers.
The Secure SDLC (SSDLC)
Much like Cinderella again, with secure SDLC, security is the protagonist of the story. It’s embedded into the code’s blueprint and architecture at every single phase of the process. The application is built following a set of structured, secure development best practices. Developers, operations, and security professionals work together through the whole process and are all responsible for delivering secure software. And these are just a few of the characteristics of this secure process.
Isn’t it fascinating how a small change of focus can make security the protagonist of your development process?
What Are the Benefits of Implementing Secure SDLC?
Did you know that in 2021 the number of software supply chain attacks increased 650% over the previous year? This alone should be enough to justify having security as the central figure of your SDLC. But there’s more when you consider that implementing secure SDLC will:
- Reduce your overall software development costs. Isn’t it cheaper to identify and fix vulnerabilities and errors early in the development process instead of patching your application once it’s released? The later you do it, the more costly it becomes. The National Institute for Standards and Technology (NIST) has demonstrated in a study that organizations could have to fork out five times more when a fix is applied after the software has been released.
- Fix issues faster and with fewer errors. As vulnerabilities are identified in the early stages of development, you’ll be able to get them fixed by the same developer writing the software. That’s way better than having a different team (who didn’t participate in the development process) work on it later. This will not only speed up the process, but it’ll also reduce the chance of mistakes.
- Protect your whole organization from cyberattacks. Because once an attacker manages to breach into your application, it’ll easily get access to your whole network. And you may lose a lot more than you think. Valuable customers, sales, reputation, you name it. The damage could be huge and far reaching.
- Supports high development velocity. Including automated security testing at every stage of the SDLC (rather than only at the end) won’t slow down your software development process, it’ll enhance it. Why? Because the time you may lose in constant testing will dramatically reduce the number of last-minute, time-consuming modifications and fixes.
- Help you get compliant with privacy and security regulations. Including security in your planning and design phases ensures you won’t forget to add all the elements required by the previously mentioned security and privacy regulations. You’re not 100% compliant with the EU’s General Data Protection Regulation (GDPR)? Get ready to fork out up to €10 million (or 2% of your global annual revenue, whichever is higher) for the less severe violations. You could pay upwards of €20 million (or up to 4% of annual global revenue, whichever is higher) for bad ones.
- Increase collaboration. With secure SDLC, everyone participating in the project is responsible for the security of the final product. You name it: developers, operation teams, management teams, and other stakeholders. All of these different facets work together toward the same goal: building secure and high-quality software that doesn’t sacrifice usability for security (or vice versa). Security isn’t a burden anymore; it’s become a shared responsibility that many people contribute to achieving.
Interested to know more? Let’s discover what a secure SDLC process looks like in detail.
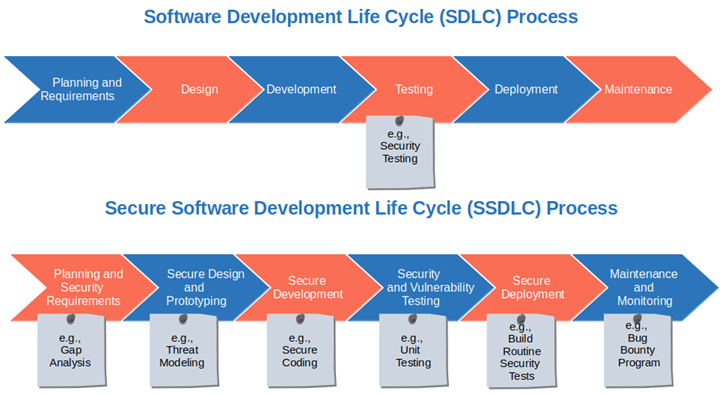
The Six Phases of Secure SDLC
Did you know that according to a report from CircleCI, companies could lose up to $126 million in revenue because of an ineffective software delivery process? Secure SDLC may help you avoid that kind of loss. How? By ensuring that each deployment phase contributes to the security of the application. See it for yourself in our step-by-step look at secure SDLC phases. Ready, steady, go!
| Secure SDLC phases | Examples |
|---|---|
| 1. Planning and Security Requirements. |
Pinpoint all critical security considerations. For example, ask yourself about:
|
| 2. Secure Design and Prototyping |
|
| 3. Secure Development |
|
| 4. Security and Vulnerability Testing |
In addition to the one already mentioned, your tests should include:
|
| 5. Secure Deployment |
|
| 6. Maintenance and Monitoring |
|
1. Planning and Security Requirements
After a lot of thought, brainstorming and meetings, you have a clear idea of the application you want to build. Great! Now it’s time to start laying the foundations of your project. The classic SDLC process would compel you to:
- Identify the project’s objectives and customers’ expectations,
- Gather all requirements from the project’s stakeholders,
- Plan adequate resources and budgets, and
- Work out a timeline and its related milestones for the delivery of the application.
Did you notice that security isn’t mentioned at all on that list? Not even once. Now, let’s spice up this step a bit and transform it into the real planning and requirements stage for a secure SDLC. Understanding exactly what you need to build, also from a security perspective, will help you design your application in the next phase. How? By identifying all critical security considerations related to the above-mentioned points.
Let’s say you’re planning to build a new chat application. You’ll probably need to find a secure way for the users to sign up for it, log in, and be able to send encrypted messages. In this case, you may want to ask yourself about the following questions:
- How are we going to secure the sign-up page for the application? For example, you may decide to secure and encrypt all communications between the server and the client using a secure socket layer/transport layer security (SSL/TLS) certificate.
- Are there any potential vulnerabilities that similar applications are facing? Build on what’s already available. Check the CVE databases (e.g., MITRE’s CVE list) to get a list of the latest known vulnerabilities impacting applications similar to the one you’re planning to build. Learn how they’re handled and ensure that fixes are included in your project plan. This will help you calculate resources and budget, and ensure that the team has enough time to fix those already known vulnerabilities.
- Do we build an in-house authentication system or do we use an external provider? Think about all of the pros and cons and choose wisely. For example, using an external provider (e.g., an OpenID provider of your choice) might save you time and money over managing a traditional in-house authentication system (i.e., storing credentials in an application database), but you may have to pay extra to add specific security features.
- What authentication protocol do we go for? Decide whether it makes more sense to use the lightweight directory access protocol (LDAP), where users’ data are stored within the database, or if it’s better to opt for an SSL/TLS certificate or OpenID where the users are redirected to the OpenID site for login?
- What kind of authentication methods should we choose?
- Single sign-on (SSO) where the user has one credential to access multiple applications or sites,
- Multi-factor authentication (MFA) that requires two or more additional authentication factors on top of a password or,
- A token-based authentication requiring a physical device like a smartphone or a USB stick?
Got it? These are just a few examples of how the classic planning and gathering requirements phase can be radically transformed by taking security into account. You just need to ask the right questions! Ready for the next phase? Let’s go.
2. Secure Design and Prototyping
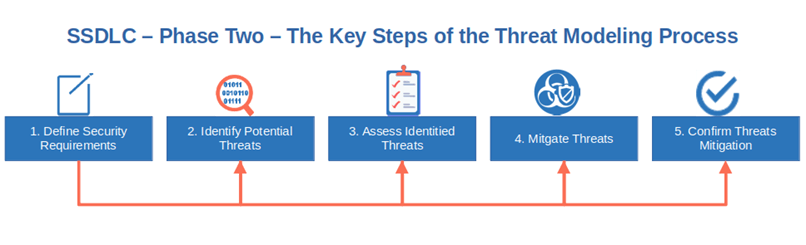
Now that you’ve nailed the requirements, it’s time to put them “on paper” and describe how they should look once included in the application. Don’t forget to specify where and how security issues or concerns are addressed. In this step, you’ll ensure that:
- All security requirements will be implemented and coded following the latest secure coding standards (more on that in a minute). This means that the application will be created using the most up-to-date security architecture to protect it from the latest security threats.
- The application will be built by applying secure design and threat modeling at every step of the secure SDLC. This means that threat modeling (i.e., architectural risk analysis), risks assessments, and security tests will become part of the software development process.
- The application will be fully compliant with data privacy and security regulations. Therefore, you’ll have to list, analyze, and describe how regulations and standards, like the following, will be addressed:
- General Data Protection Regulation (GDPR),
- California Consumer Protection Act (CCPA), and/or
- The Payment Card Industry Data Security Standard (PCI DSS)
Are you struggling to put together a top-notch design? I know it isn’t easy. Get it wrong and the whole process will suffer. Why don’t you work on two or three design alternatives and get them evaluated by the teams? In this scenario, the one that receives the most votes wins. This approach can help increase collaboration, boost motivation, and help you finalize the perfect design.
3. Secure Development
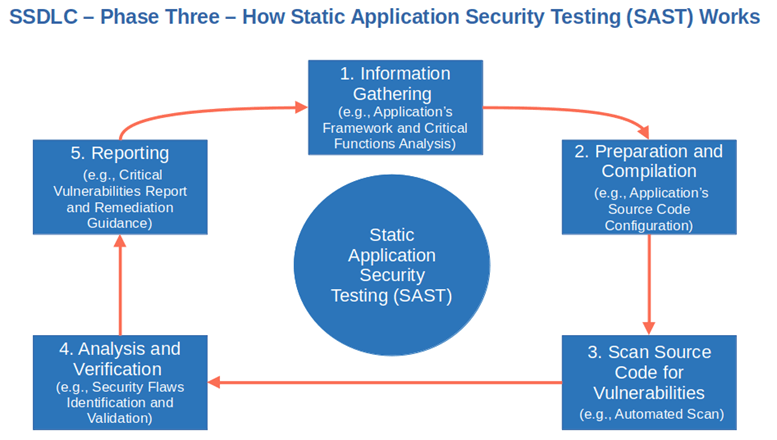
It’s coding time! Until now, the application was just an intangible project, a dream. Now, it’s time to make that dream a reality and start building it with security in mind. How?
- Follow the latest coding standards and guidelines.
- Use a code signing certificate issued by a trusted certificate authority (CA) to add your verifiable identity to your software.
- Use SQL queries parameterization to protect your app against SQL injections,
- Implement input validation and data sanitization to prevent malformed data from being entered into the database and remove unsafe characters. This will protect your components from errors and malicious inputs.
These are only a few examples of secure coding guidelines. If followed correctly, they’ll help you prevent the risk represented by the majority of vulnerabilities, thus decreasing your organization’s overhead and costs (more on that later).
- Ensure your teams are always up to date. To be successful, ensure your developers are familiar with the latest guidelines and standards and are using only the most updated version of the chosen programming language.
- Run code reviews and penetration tests during the whole secure SDLC. It’ll enable you to identify and address vulnerabilities earlier and check that the previously mentioned guidelines have been applied correctly. To do so, you can:
- Check your code manually or automatically by using a static application security testing (SAST) tool,
- Use peer code reviews, and
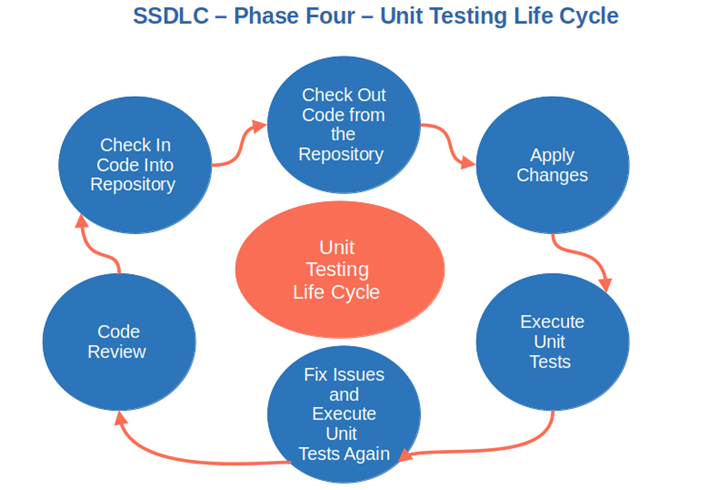
- Implement unit testing (more on that in a minute).
- Check open-source libraries before using them. Did you know that according to a recent study from the Linux Foundation 98% of modern codes include free and open source (FOSS) libraries? Yup! The times when developers were writing their code from scratch are long gone. Today, in a world where codes have to be released as fast as possible, developers often rely on existing open-source libraries to build their applications’ key functionalities and features. This is great because it can save your developers tons of time, however, you should never forget to check whether those libraries are safe to use. How? By scanning them with a software composition analysis (SCA) tool.
4. Security and Vulnerability Testing
Hold on a second. Didn’t we just talk about testing in the previous point? That’s correct. However, as we’re aiming to transform a traditional SDLC into a secure SDLC, testing is one of the activities that you’ll have to perform often, basically throughout the whole life cycle.
This particular phase will enable you to thoroughly test your new application before its final deployment to ensure that you’ll:
- Catch vulnerabilities or bugs that have slipped through previous tests.
- Address new vulnerabilities as they are announced.
- Release a bug-free and secure product.
In addition to the one already mentioned, your tests should include:
- Penetration testing. Have you ever heard of certified ethical hackers (CEHs)? They’re security experts in the latest hacking tools and techniques. Like pen testers, they can act as malicious attackers to hack into your new application to identify potential vulnerabilities. They may attempt to breach firewalls, access sensitive data, or simulate ransomware attacks to poke, prod, and test your defenses.
- Automated unit tests. Unit testing tools like SimpleTest or Junit will allow you to check your application down to the finest details. Do you want to test a single function? No problem, unit testing can do that. As we want to build a secure application, don’t forget to include specific tests on critical application components like:
- User authentication,
- Session management,
- Access control,
- Error handling,
- Data encryption,
- Input validation, and
- Authorization services.
- Dynamic application security testing (DAST). Often used for testing software as a service product (SaaS) using DAST software (or black-box testing) like SOOS or Detectify is another way to test your internet-facing application for security flaws. How does it work? It runs the application in a test environment and tries out possible combinations of inputs to find security weaknesses.
Did your application pass all the tests? Good, you can move on to the next step. If it didn’t, like Gandalf in Tolkien’s Lord of the Rings said, “You shall not pass!” In other words, the application shall not be deployed until all tests are successful and you’re certain your software is as secure as possible.
5. Secure Deployment
A proverb says, “A woman’s work is never done.” The same applies to developers. In fact, once the application is ready for deployment, a developer should:
- Build routine security tests. Do you remember when we talked about static analysis scans? You can adapt them and use them after deployment, too.
- Let your users test your application. Want to know if your application meets your users’ expectations from both usability and security perspectives? Beta testing is a great solution that can help you do precisely that. Just before releasing your product to the world, allow some selected customers, developers, and colleagues to test user acceptance.
- Implement key changes based on user acceptance testing feedback. Did your first users find a bug or a security issue? Make sure you address them before release.
6. Maintenance and Monitoring
No rest for the weary! Even if the application has now been released into the wild, it’ll still need some nurture and care to keep it secure and ensure it works properly. New vulnerabilities are discovered every day. Hackers never sleep and some bugs might be identified only after the product has been used for some time. The following actions will help you keep your precious newly born application in tip-top, secure condition.
- Monitor your application. By keeping an eye on its performance, you’ll be able to immediately spot anomalies and suspicious behaviors that could lead to a breach. There are tons of monitoring tools on the market. Check them out and pick the ones more suitable to your needs.
- Constantly patch vulnerabilities. Did a new vulnerability related to a library or a component you used to build your application come up? Make sure you patch it immediately. Don’t forget to set up a sleek patching and updating process to make things even easier.
- Set up a bug bounty program (optional). Did you know that there was a 63% increase in white hackers reporting vulnerabilities in 2020? Yup, bringing white hackers on board means you can let the others do the work for you. Tap into their skills, and compensate them if they find a bug or a flaw in your application. It’ll save you money and time while helping you keep your application secure.
- Make it easy for your users to report a bug. Your customers and users are your best allies against errors and attackers. They use your application every day, therefore, they’re the most likely ones to find issues or flaws. Add a feedback button to your software like “Found a bug? Let us know!” or set up a feedback page as Duolingo, MadCap Software, or Facebook did.
Now, It’s Time to Rinse and Repeat
All done? Good. Now, back to step one. Why? Because the secure SDLC is an infinite loop, not a line. It goes ‘round and ‘round and never stops. Every new vulnerability, bug, or new feature to implement has its own cycle. And every cycle starts from step one.
With secure SDLC, security doesn’t stop when you finish writing your code. It’s constantly embedded into the whole process from the very beginning.
Do you want to see a few examples of the positive impact secure SDLC could have on your organization? Check out the adventures of the hacker Salta in this short funny video:
Now that you know the difference between the traditional SDLC and secure SDLC, which one do you think is better? Would you rather write software with security in mind from the very beginning or check it for security issues later, just before release? Up to you to judge.
Final Thoughts on Secure SDLC, the Secure Software Development Life Cycle
Doesn’t your organization’s future look brighter and more secure now with secure SDLC? Of course, vulnerabilities and threats will always be there, as they’ll evolve with the software industry. That’s why focusing on security at every single deployment step has become fundamental.
The switch from the traditional software development life cycle approach won’t happen overnight, though. It’ll require your teams to change to a more security-oriented mindset and to adopt (and get used to) new practices. It may be challenging at the beginning, but you’ll get there at the end. And that’s when your teams will realize that everything you’re doing is worth the effort when they’ve made more secure software.
Start shifting your security risks left today. Don’t forget security testing and watch the odds turn in your favor.


