5 Minute Guide: How to Securely Manage Your Code Signing Certificates & Keys
70% of surveyed technology organizations were impacted by a software supply chain attack in 2021. Explore five unbeatable certificates and key management tips that’ll help you protect the integrity of your software and help you secure your digital identity to stay a step ahead of attackers
50,000 This is the average number of digital certificates DigiCert reports organizations having to manage within their IT environments. (Yes, this stat includes code signing certificates.) No wonder 61% of them are concerned about the time required to manage such a massive number of certificates.
And it doesn’t stop here. Public key infrastructure (PKI) and digital certificates such as code signing certificates are quickly becoming critical factors for a more secure software supply chain. Their benefits? They help you add digital identity and data integrity to your software. As a result, finding an effective way to securely manage an ever-growing number of code signing certificates and keys has become paramount.
What about your organization? Is certificate management also causing you headaches? Don’t despair! This quick guide will show you five tips that’ll help you become a pro at securely managing code signing certificates and keys. Today, you’ll learn how visibility, automation, and more can make a real difference to the security of your data and organization. Right here, right now. Five key points in just five minutes — start the clock.
Discover How to Securely Manage Your Code Signing Certificates & Keys
Digital certificates and, specifically, code signing certificates have been used for years by organizations as an effective way to assert their identity as vendors and assure data integrity. Code signing certificates enable organizations to add an extra layer of security by signing everything from PowerShell scripts to executables and files.
However, if poorly managed, code signing certificates and keys can quickly turn into security issues that could impact the security of your whole software supply chain. And if you think about it, it isn’t something that it can be taken lightly — just look at the stats. In 2021, 661% of successful security breaches originated from attacks targeting vulnerabilities in the software supply chain.
So, how can you transform these potential weaknesses into strengths again? Let’s get right to it with these five key certificate management tips. Don’t have five minutes to spare? Then check out our table and get a quick overview of our tips in half the time.
| Certificate and Keys Management Tips | Certificate and Keys Management Tips Examples |
|---|---|
| 1. Ensure 100% Visibility of Your IT Environment |
|
| 2. Implement an Automated PKI Life Cycle Management Solution |
|
| 3. Protect Your Private Keys |
|
| 4. Integrate Code Signing Into Your Software Development Life Cycle (SDLC) |
|
| 5. Monitor Your Code Signing Certificates and Keys and Report Their Vulnerabilities |
|
1. Ensure 100% Visibility of Your IT Environment
How can you protect something that you can’t see? You simply can’t. Therefore:
- Make an inventory of keys and certificates. List all of them and ensure you write down their key information. This includes everything from the expiration date to the actual owner of the certificate and its deployment location. Categorize both keys and certificates based on use cases. Make regular inventories and don’t forget to remove expired and revoked certificates.
- Map and manage your dependencies (e.g., external libraries). Yup, this means all of them. In 2021, 97% of codes contained open-source components. Do your codes include open source materials? I bet they do. Do you have a list of all of them? If you don’t, a software bill of materials (SBOM) is what you need. List the individual components, check them, and update them. You can also use dependency management software like Dependabot, Sonatype, or Snyk (more on that in a minute) to help you carry out this crucial task.
2. Implement an Automated PKI Life Cycle Management Solution
Do you really believe that you’ll be able to secure every single step of your software supply chain manually? Forget it, it’s too complex and the risk is too high. Therefore:
- Use a reliable certificate management tool. Don’t risk the security of your organization’s systems and data on manual tracking methods that are prone to failure. After all, using the average of 50,000 certificates, that’s an average of about 137 certificates (and their keys) to track per day! If even one of them slips through the cracks, it can spell disaster.
- Opt for public key infrastructure as a service (PKIaaS) approach. Simplify and automate your PKI management responsibilities by moving them to the cloud and outsourcing them. This way, you don’t have to worry about managing your public and private PKI needs in house.
- Automate the whole certificate life cycle. Regardless of the type of PKI management solution you opted for (in-house or outsourced like PKIaaS), ensure that it covers the whole certificate life cycle. Right from issuance to deployment, and renewal. This will help you to also reduce the possibility of human errors. Don’t forget to automate key creation for an efficient rotation. And this takes us to the next point.
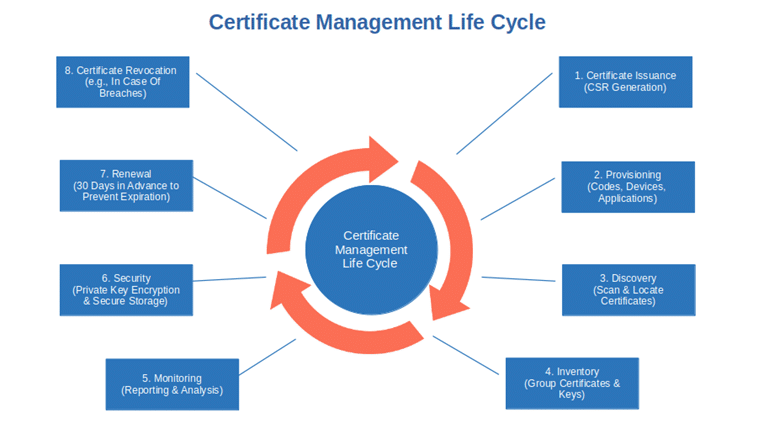
3. Protect Your Private Keys
Your private keys are the gateway to your organization. What are the best ways to protect the keys to your castle?
- Limit access to keys by using a zero-trust baseline. Implement access control policies (e.g., least privilege principle) to code signing keys. Start from the assumption that no one is trusted (i.e., zero-trust, or deny by default) and minimize the number of users who have access to your cryptographic keys.
- Securely store your private keys and certificates. Have you ever heard of hardware security modules (HSMs) and hardware security tokens? They’re physical, tamper-resistant appliances or devices used to generate, protect and manage private keys and certificates. The USB token you receive when you buy an eextended validation (EV) code signing certificate is an example of it. Want to keep your keys and certificates safe? Store them on devices like HSM, hardware security token, or on a FIPS 140 level 2 approved secure hardware device.
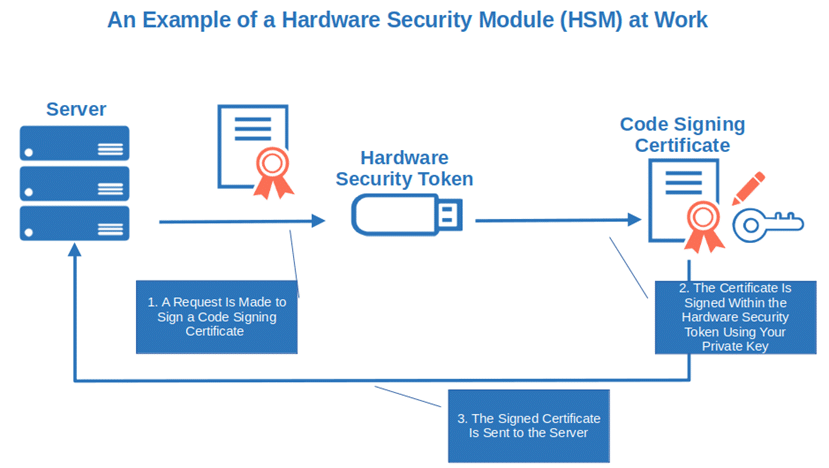
- Use strong passwords. Less than one second. Yup. It’s all it takes to hack any of the 2021 top 13 most common passwords used more than 308 million times in 2020. Do your organization a favor. Ensure your private key passwords are strong enough. Password meters can facilitate this task. Once done, store password hashes based on secure algorithms only instead of plain text.
- Rotate your keys. Enforce automatic rotation and renewal of keys, passwords, and certificates. This will help you minimize data breaches and outages, and limit the damage of security incidents due to expired certificates or stolen keys.
- Use secure algorithms. Even the most bulletproof algorithm will be breached one day, we all know it. Keep your keys up to date by ensuring you’re always using the latest more secure algorithm.
4. Integrate Code Signing Into Your Software Development Life Cycle (SDLC)
Venafi’s new global study found that 85% of CIOs admit that developers and software engineers take shortcuts on security. Why? To release software faster. But haste makes waste. Avoid that by:
- Code signing early and often during the whole SDLC. That’s not going to be easy. I hear you. Moving from the traditional software development life cycle (SDLC) process to the more modern secure SDLC will help your team incorporate security at every stage of the development life cycle. And you know what’s even cooler? There are frameworks ready for you to use, like NIST’s secure software development framework (SSDF).
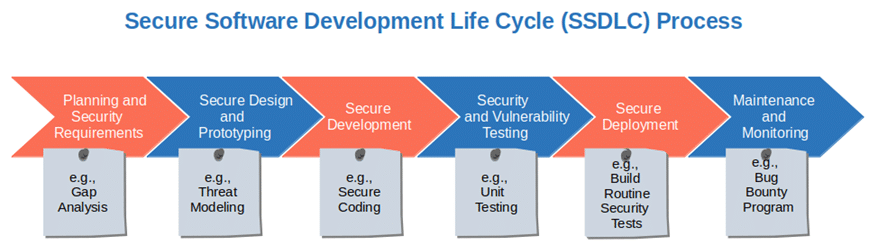
- Use different types of signing certificates. Do you want to make sure you circumscribe the damage in case a code signing certificate gets stolen? See that your developers use self-signed certificates during development and then swap them out for publicly trusted ones when they go to production. By the way, don’t think even for a moment about using a self-signed certificate in production: it’s a no-go!
5. Monitor Your Code Signing Certificates and Keys and Report Their Vulnerabilities
Have you ever tried to organize something without knowing what had to be organized in the first place? It sounds virtually impossible, right? The same goes for certificate management. You can’t effectively manage and protect something if you don’t know who you’re up against, what the issues are, and what you have to protect looks like. The solution?
- Constantly monitor your code signing certificates and keys. This year Keyfactor’s report indicates that 42% of organizations are still tracking their certificate via spreadsheets. In point two, we talked about automation. A PKI certificate management tool platform like DigiCert CertCentral Enterprise or Sectigo Certificate Manager will bring your certificate monitoring into the 21st century. And you’ll never miss a certificate expiration date again.
- Use a reporting tool. Are you sure that your organization isn’t affected by Log4j (Log4Shell) vulnerability? What if your boss comes to your desk and asks you to confirm that all software you’ve developed is compliant with privacy and security regulations like The EU payment service directive (PSD2) and the California Consumer Privacy Act (CCPA)? Run a report with tools like Xray or Sourcegraph and you’ll quickly get an answer to both questions. You still don’t have a reporting tool? Time to find one and impress your boss.
Tick-tock, five minutes are nearly gone. Time to act! Securely manage your code signing certificates and keys before they’re gone.
Final Thoughts on 5-Minute Guide: How to Securely Manage Your Code Signing Certificates and Keys
Is your organization aiming to produce only bulletproof secure software? You can use what you’ve just learned to make this dream become a reality. All you have to do is build a robust certificate management system that focuses on:
- Visibility,
- Automation,
- Keys protection,
- Integration, and
- Reporting.
These five key items will not only give your business an extra security boost to keep pace with today’s cyber threats, but they’ll also:
- Keep your organization, customer’s data, and your software supply chain secure,
- Speed up and simplify certificates procedures for developers during the whole SSDLC,
- Protect you against attacks like SolarWinds, where a single compromised file affected their whole supply chain, and
- Ensure your code signing certificates and keys will be securely managed.
What do you think? Weren’t these five minutes well spent?


