7 Software Security Lessons to Avoid Repeating in 2025

Explore seven headline-grabbing cybersecurity incidents from 2024 that you can learn from to prepare for a stronger 2025 and beyond
2024 was another rough ride for organizations of all sizes. Ransomware hit unprecedented new highs, with nearly three-quarters of the businesses polled by OpenText reporting experiencing at least one attack that year.
Supply chain attacks continued to wreak havoc, occurring at a pace of “at least one every two days in 2024.” Credential phishing attacks swept the world and surged by an alarming 703% in the second half of the year.
So, even if the past year was a tough battle in the trenches, it’s time to arm yourself with the knowledge you’ve learned from the frontline. In this article, we’ll look at seven real-world examples of software security-related incidents that made headlines in 2024 and discover how to avoid making the same mistakes in 2025.
Cybersecurity in 2025 TLDR: What to Learn From 7 Real-World Software Security Incidents
Here is a summary table giving you an overview of the lessons to learn and actions you can implement to boost your organization’s security in 2025. Don’t stop reading, though. We’ve included a lot of “juicy bits” (insights) regarding each incident and lessons learned in detail throughout the rest of the article.
| Breach or Incident Information | What Occurred | Lesson(s) Learned |
| 1. Snowflake Credential Breach and Ransomware Attack | Cybercriminals exploited weak credentials to access corporate customers’ data and extort them. | Evaluate your vendors. Enforce multi-factor authentication (MFA). Implement the principle of least privilege. |
| 2. Amazon Web Services (AWS) Attack | The ShinyHunters group leveraged vulnerabilities in cloud apps and endpoints to steal sensitive data, credentials, and secrets from AWS customers. | Invest in a web application firewall (WAF). Rotate your keys and certificates. Securely manage your keys and certificates. Use canary tokens. Scan your website for vulnerabilities. |
| 3. AnyDesk Hack | AnyDesk portal was unavailable for days due to a data breach stemming from a misconfiguration. | Store your code signing certificates on a hardware security module (HSM). Never underestimate anomalies (or your guts). Log network traffic and activities and set up automatic alerts. |
| 4. CrowdStrike Update Incident | A CrowdStrike security platform update caused a global IT meltdown. | Test patches and updates. Go for incremental rollouts. Set up a strong disaster recovery and business continuity plan. |
| 5. Ascension Ransomware Attack | An employee downloading a malware-infected code caused the third-largest healthcare data breach in 2024. | Train your employees Sign your code and executables. Allow only downloads from trusted sources. |
| 6. Ivanti Flaws and CISA Data Exposure | Two Ivanti security tools’ flaws caused breaches for customers and impacted two of CISA’s critical infrastructure applications. | Run static and dynamic tests, and pen test your applications often. Implement a strong patch management process. Embed security into every stage of the software development lifecycle. Adhere to OWASP’s secure coding practice checklist. Hash and salt stored sensitive data. |
| 7. Sisense Breach | Attackers are thought to have exploited a hardcoded token to access one of the company’s Amazon S3 buckets storing unencrypted customer information. | Never hardcode credentials. Monitor your systems, applications, and network for suspicious activities. Create a software as a service bill of materials (SaaSBOM). |
Lesson #1: Assess Your Vendors and Limit Access to Sensitive Systems and Data (Snowflake)
Let’s start with a bang. I’m sure you remember the Snowflake attack. The multi-cloud data hosting company made news in April 2024 when at least 165 of its corporate customers fell victim to devastating data breaches.
How did it happen? It was easier than you think. Cybercriminals accessed and downloaded data using credentials previously stolen through a remote access Trojan (RAT). The operation was further facilitated by three key factors:
- Weak authentication. The sensitive data stored in the cloud was accessible via login with a traditional ID and password.
- Unchanged passwords. The credentials exploited by the bad guys were still valid. Yup, the victims didn’t change their passwords after a previous breach.
- Too broad permissions. Several accounts granted unrestricted permissions and access to sensitive data and databases.
This explains a lot.
Who/What Was Impacted
The impact was so severe that the attack was dubbed by many as the “mother of all data breaches.” Millions of customers’ sensitive data were compromised. Here, are a few examples:
- Ticketmaster. Over 40 million users were affected and 560 million records (e.g., customer names, email addresses, payment data) were leaked.
- AT&T. Hackers stole records relating to nearly all AT&T customers’ phone number, text messages, and phone calls. Some records even include the location of cell towers closest to a “subset” of subscribers. That’s a massive leak of nearly 110 million customers’ data.
- Santander Bank. The records of more than 12,000 Santander U.S. employees were compromised. The leak included names, bank account information, and social security numbers.
What Can You Learn from This Breach?
One of the big mistakes AT&T and other affected organizations made was to unquestioningly trust Snowflake’s security posture. Don’t make the same error.
- Carefully evaluate your software providers and other third-party vendors. Minimize exposures and risks by conducting thorough vendor risk assessments, following the best practices issued by the National Institute of Standards and Technology (NIST).
- Update your account credentials. The cybersecurity firm hired by many organizations targeted in the campaign, Mandiant, reports that many of the impacted accounts used credentials that had been exposed in previous third-party breaches but had never been rotated or updated.
- Enforce multi-factor authentication (MFA). Replace the traditional ID and password with the more secure MFA that requires users to provide two or more verification factors. Even better, opt for passwordless authentication. This way, hackers won’t have anything left to steal.
- Implement the principle of least privilege (PoLP). Regulate permissions by giving vendors and users access to only what they need to do their jobs. Joe from the HR department doesn’t need to access your customers’ sensitive data to carry out his duties, right?
Lesson #2: Scan & Secure Your Websites, Cloud Apps, Software and Other Assets (Amazon Web Services)
Cybercriminals are always hungry for more — more vulnerabilities to exploit, more financial opportunities, and more invaluable customer data. In August 2024, AWS customers were targeted by hackers connected to the cybercriminals involved in the Ticketmaster attack.
The crooks scanned 26+ million AWS IP addresses for vulnerabilities and misconfigurations. They also analyzed secure socket layer/transport layer security (SSL/TLS) certificates and did a reverse IP lookup to extract domain names. Dark Reading reports that they were able to do this by targeting “flaws present on the customer application side of the shared responsibility cloud model and did not reflect any fault of AWS.”
As soon as the operation was completed, the little devils swept the listed vulnerable endpoints and extracted every sensitive data, credentials, and secret they could find.
Who/What Was Impacted
Once again, the spoils were pretty rich. In just a few weeks’ time, the attackers extracted two terabytes of data, including:
- 1,526 unique and valid AWS credentials. The loot included private keys and secrets for GitHub, the communication API Twilio, and cryptocurrency platforms.
- 8,244 accessible private buckets (i.e., the cloud storage version of file folders).
- Over 252,000 exposed GIT repositories.
What Can You Learn from This Breach?
The digital world is a dangerous place, above all “up in the cloud.” Protect your organization, customers, and data:
- Invest in a web application firewall (WAF). A WAF is a cost-effective way to protect your web application from the bad guys. Think of it as an all-seeing eye between your website and the internet that filters, controls, and blocks suspicious traffic.
- Scan your website for vulnerabilities. According to CVEdetails.com, more than 11,000 recent or updated vulnerabilities were detected in 2024 when compared to the previous year (which had a total of 29,066 vulnerabilities). This is a massive increase, considering that fewer than 4,000 common vulnerabilities and exposures (CVEs) were published or updated in 2023. So, pick your favorite free or paid scanning software and automatically scan your websites and applications for vulnerabilities.
- Use canary tokens. Time to start trapping! Prepare your trap line by sprinkling these little nets in critical places across your website. Did you get an alert? It means a canary token has been triggered and you now know that someone is trying to access your secrets. Isn’t it sweet? And you don’t even have to wait for trapping season to place them.
- Shield your keys and certificates. Protect your code signing certificates and keys. If you own several keys and certificates, DigiCert Software Trust Manager provides HSM storage and certificate revocation and rotation to granular permission management and activity logs.
Lesson #3: Safely Store Your Certificates and Keys, and Never Underestimate Anomalies (AnyDesk)
In February 2024, AnyDesk announced that hackers had broken into its production servers. Jackpot. Although the firm didn’t share many details about the incident, it’s thought that the root cause was likely a misconfiguration problem.
Even if AnyDesk identified some evidence of breaches in their production servers in mid-January 2024, bad actors were already freely running all over the platform since December 2023.
Who/What Was Impacted
OK, as far as we know, the aftermath didn’t involve any lawsuit in this case. However, AnyDesk and its clients — the company’s remote desktop software programs used by at least 170,000 organizations worldwide — had to invest a lot of time and effort to get back to normal, as:
- Over 180,000 customer credentials were posted for sale on the dark web.
- Code signing certificates and keys were stolen. AnyDesk had to revoke all code signing certificates and keys used to digitally sign their software. The company reported it also revoked all customer web portal account passwords out of an abundance of caution.
- Customers were unable to access the portal for several days. Fixing a breach takes time, and this incident wasn’t an exception.
What Can You Learn from This Breach?
Incidents do happen. The following measures will help you prevent or at least minimize their impact.
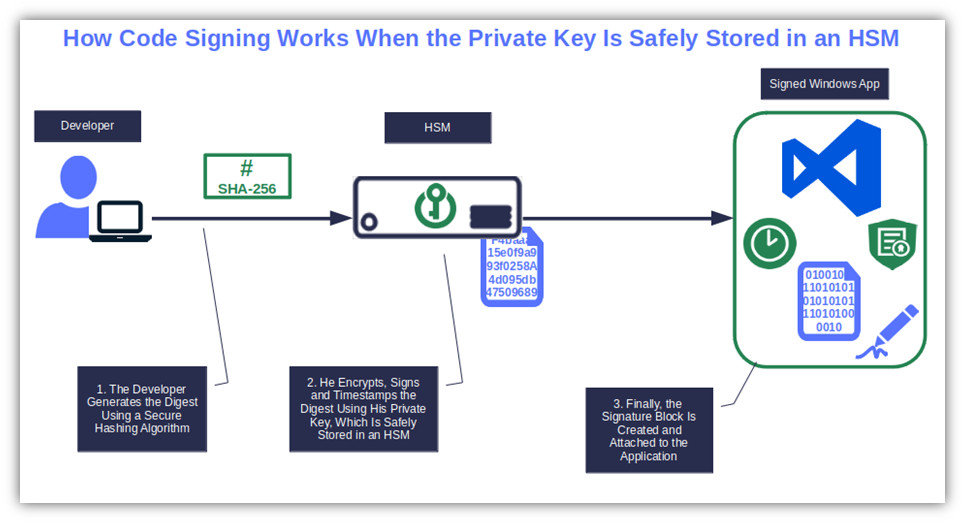
- Store your code signing certificate’s private keys on a hardware security module (HSM). When your cryptographic keys are saved on an HSM, neither users nor applications can see, touch, or alter them. Corporations can opt for a highly secure, self-managed, on-premises FIPS 140-2 Level 2 compliant HSM. Smaller businesses usually go for more affordable managed solutions. Purchase a code signing certificate and store it on a fully managed HSM-backed cloud solution or use a secure key management solution like DigiCert Key Locker and Azure Key Vault.
- Never underestimate anomalies (or your guts). AnyDesk ruled out that the customer credentials listed on the Dark Web were related to the breach. Nevertheless, the company did the right thing by forcing a mass password change and taking additional security measures. So, the next time you notice something suspicious during a routine audit or monitoring, don’t ignore it. Take action right away, as doing so might save your day (and your job).
- Monitor and log network traffic and activities. Keep an eye on your network traffic, analyze logs, and set up automatic alerts for unusual patterns or unauthorized behavior. Don’t stop at traditional website scanning processes; regularly pen test your applications.
Lesson #4: Rigorously Test Updates/Patches and Deploy Them Incrementally (CrowdStrike)
Did you ever imagine that a simple feature update gone wrong would bring half the world to a halt? That’s what happened in July 2024, when CrowdStrike’s Falcon security platform update was rolled out and blue screens of death (BSOD) popped up on millions of Windows systems globally.
According to CrowdStrike’s official statement about the issue, the situation boiled down to a basic input field mismatch within the sensor system. The sensor expected one thing (i.e., 20 input fields) while the update provided another (i.e., 21 input fields). While this error is small, it had a big effect that resulted in system crashes.
The event was so catastrophic that the company won the DEF CON Epic Fail Pwnie Award, a trophy for top failures that is typically awarded at the annual cybersecurity conference in Las Vegas.
Who/What Was Impacted
Yup, it was a real Armageddon that grabbed the attention of the U.S. Cyber Security & Infrastructure Security Agency (CISA) and:
- Affected 8.5 million Windows devices. “Blue screens of death” (BSODs) appeared all over the world and across various private and public sectors. From banks and government agencies to airlines, retailers, and healthcare services — organizations around the world were thrown into a state of chaos.
- Required an extremely time-consuming recovery process. Businesses had to spend weeks to restore normal operations.
- Was immediately exploited by cybercriminals. Attackers targeted CrowdStrike customers with malware and phishing.
What Can You Learn from It?
On top of what we’ve mentioned so far:
- Test patches and updates. Don’t rush into deploying patches and updates. Test them in a sandbox environment first and on a limited set of devices. This approach will help you catch compatibility issues and flaws before deployment.
- Go for incremental rollouts. Implement a patch and update management process that ensures rollout in stages. If something goes wrong, the damage will be limited to a few devices and won’t jeopardize your whole organization.
- Have a plan B. Set up a strong disaster recovery and business continuity plan. Outages happen, but if you have a system redundancy in place and a backup on hand, you can reduce your operations’ downtime and impact on customers and users.
Lesson #5: Sign Your Code & Train Your Employees (Ascension)
In May 2024, bad actors launched what became the third-largest healthcare data breach of the year. An Ascension employee downloaded a legit-looking malware-infected file that spread like wildfire, finally resulting in a ransomware attack.
The investigation was concluded only in December 2024. Apparently, no ransom was paid, but the impact on the company’s reputation, patient relationships, and operations was humongous.
Who/What Was Impacted
As a result of the incident:
- 5.5 million patient records were stolen. The files included medical, insurance, and payment information, and other personal data such as passport numbers, date of birth, and addresses.
- Operations were severely disrupted. Ambulances were diverted, patient appointments, non-urgent operations, and tests were postponed for days.
- Patients’ records were locked. Thus, Ascension employees had to go back to the 90s and note everything on paper, from triages and procedures to prescribing and dealing out medications.
What Can You Learn from It?
- Train your employees. Set up comprehensive cybersecurity training for your whole staff. Include exercises on spotting phishing emails and scanning attachments and codes for malware using a reputable antivirus tool. Show them how easy it is to check the authenticity and integrity of software by verifying its digital signature. When this knowledge is applied to real-world circumstances, this approach will significantly reduce the risk of falling for scams.
- Allow only downloads from trusted sources. Implement security policies so that your employees stick to software vetted by your IT department or coming from trusted app stores (e.g., Microsoft App Store or Google Play for mobile devices). Be sure to enforce an antivirus scan before any download, regardless of where a file or app is coming from.
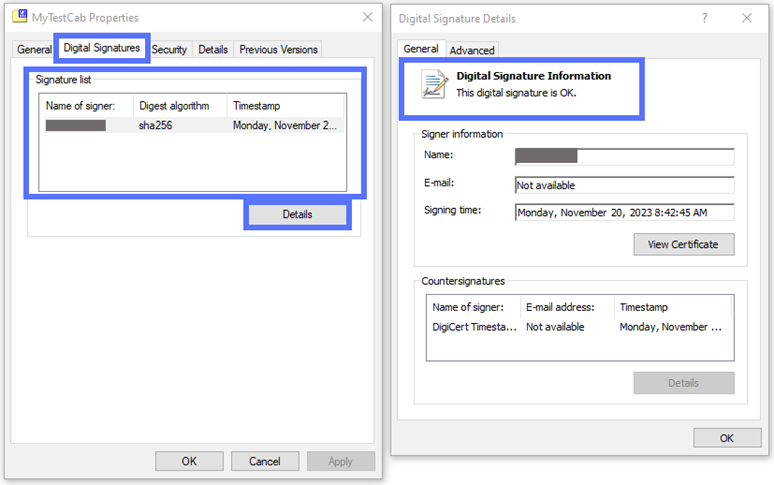
- Sign and timestamp your code and executables with a trusted code signing certificate. A code signing certificate lets you add a digital signature to your software. Thus, when an employee downloads the signed code, the client verifies the signature and alerts him if the software has been modified. The code/ attachment isn’t signed? Then it isn’t safe and shouldn’t be trusted or run — no exceptions.
Lesson #6: Build Your Products Following the Secure-By-Design Approach (Ivanti/CISA)
In today’s digital world, no one is safe, not even the experts. Beginning in 2023, cybercriminals repeatedly exploited flaws in two Ivanti security solutions to breach government agencies and enterprise networks.
If this wasn’t bad enough, even when Ivanti issued a fix for the vulnerabilities and created a tool for its customers to check whether they were compromised, the attackers bypassed both mitigation measures and Ivanti’s integrity checker after a mere few days.
The Ivanti Connect Secure and Ivanti Policy Secure Vulnerabilities became a major incident, and CISA was one of the victims.
Who/What Was Impacted
Obviously, when government agencies are involved, the level of impact is always pretty high. This one, was no exception.
- Potentially, 100,000+ individuals were affected. The breached CISA’s Chemical Security Assessment Tool (CSAT) contained a wealth of screening data screening on people and companies that had access to high-risk chemicals in the U.S, and private sector chemical security plans.
- Two CISA systems had to be taken offline for days. On top of the CSAT application, CISA has to temporarily take offline also its portal used to secure critical infrastructure (CISA Gateway).
- Ivanti had to officially apologize and change their cybersecurity approach. The company’s reputation was badly hit. Ivanti had to invest time, money, and resources to put it right and change the way their cybersecurity strategy.
What Can You Learn from It?
- Run different software tests (and do it often). During development, test your code, often and early. Use static and dynamic software testing to find errors, bugs and evaluate its performance. Assess the security of your application by getting a pentester to simulate cyberattacks. Check all configurations to eliminate weaknesses and potential security issues. You’re not sure where to start? CISA’s recently published Top 10 Cybersecurity Misconfigurations document will help put you on the right path.
- Implement a strong patch management process. Stress-test your patches with different systems in an isolated test environment before rolling them out. Automate the deployment using a critical-updates-first approach so that the most critical patches are installed first.
- Opt for a secure-by-design approach. Strictly speaking, embed security into every stage of the software development lifecycle, starting from the very beginning. Learn more about how to implement it by reading CISA’s whitepaper and following OWASP’s recommended secure coding practice checklist.
- Hash and salt or encrypt your data at rest. Worried one of the bad guys will find a way around your security measures? Make his efforts fruitless by scrambling your sensitive data at rest (e.g., stored credentials, personal information, etc.) to add another layer of protection. For personal info, encrypt the data. For passwords, salt and hash it.
Lesson #7: Monitor Your Systems/Network & Don’t Hardcode Credentials (Sisense)
In April 2024, malicious actors exploited a hardcoded token embedded in one of Sisense’s self-hosted GitLab repositories and gained a free ride into Sisense’s Amazon S3 bucket in the cloud.
To make matters worse, the attackers even didn’t break a sweat as the data stored in the bucket was unencrypted. The situation is akin to Sisense handing the bad guys its data on a silver platter. The event was so extreme that CISA took an active role in the investigation.
Who/What Was Impacted
The volume of stolen data and secrets was just one of the multiple repercussions.
- Attackers exfiltrated several terabytes of data. The leak included access tokens, SSL/TLS certificates, email credentials, and sensitive customer data.
- Third-party services were also affected. The breach put at risk also services connected to the stolen information such asSalesforce, Amazon S3, Amazon RDS, and GitHub.
- Critical infrastructure providers were among the victims. Financial services, telecommunications, healthcare, and education were just a few of the over a thousand organizations compromised.
What Can You Learn from It?
- Never hardcode credentials. Hardcoded cloud credentials are one of the biggest threats to cloud security, as demonstrated by case studies and real-life examples. Be proactive. Invest in secret management tools and use secret detection platforms to detect and eliminate hardcoded credentials. Some can even automatically delete, encrypt, or redact the identified secrets.
- Monitor your systems and network. You don’t need to break the bank to get a unified view of your infrastructure and applications. Open-source software like Nagios or Prometheus gives you real-time visibility of your systems and network for suspicious activities so that nothing can slip through the cracks.
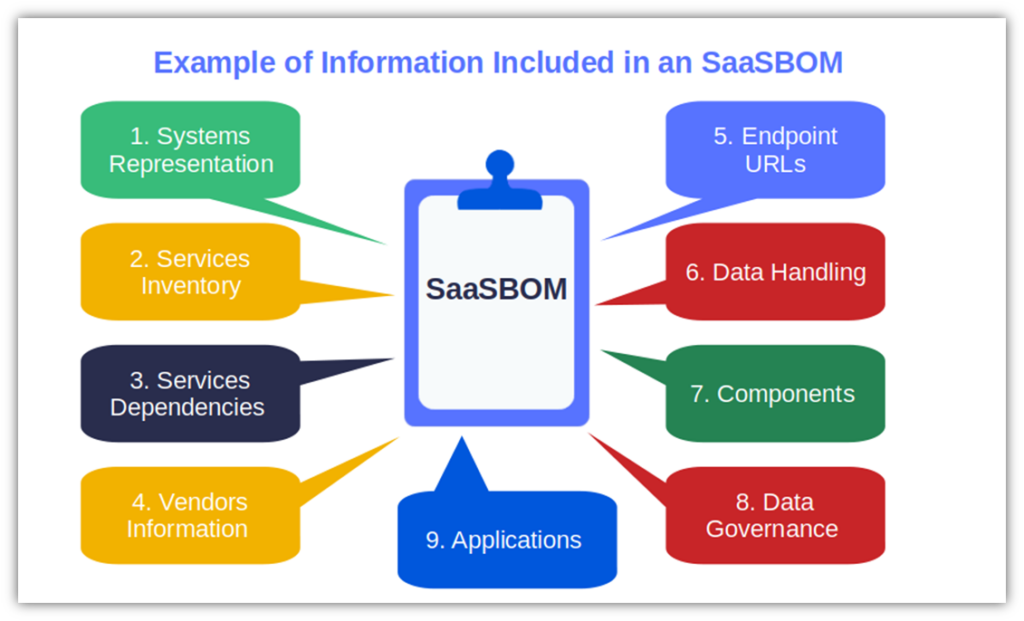
- Generate a software as a service bill of materials (SaaSBOM). Just like the traditional SBOM documents every component of a software app’s code, an SaaSBOM lists all SaaS applications used within an organization. It gives you a clearer picture of your organization’s data flow and overall infrastructure to provide meaningful insights into critical areas such as rogue applications (think shadow IT and unauthorized software usage), data handling and governance, and vendors.
A Quick Look at the Potential Consequences of Unaddressed Software Security Issues
Cybersecurity incidents can happen to any business and the aftermath can have short and long-term effects on the organization as a whole, leading to (among other issues):
- Reputation/Brand harm and damages. Vercara’s latest survey shows that 70% of consumers would stop buying from a company victim of a data breach. Bad news travels fast, but reputational damage can take ages to mend.
- Financial losses. This is probably the first and most immediate impact. Monetary losses go beyond remediation costs. CrowdStrike’s shares went down by nearly 20% when the incident happened. There are also concerns regarding the loss of sales contracts and future business opportunities that directly impact your company’s bottom line.
- Legal or compliance-related issues. Failing to comply with data protection and privacy regulations can cost you big money in fines. Lawsuits followed many of the incidents mentioned in this article. For instance, CrowdStrike’s shareholders filed a class action and Delta Airlines sued the company for the mass flight cancellations.
- Operational disruptions. Incidents can shut down an organization’s operations for hours or days. Downtime may affect customers and third parties. Consider what happened with Ascension and CrowdStrike. In both cases, a snowball effect seriously impacted millions of customers and systems.
Final Thoughts About 7 Software Security Lessons to Avoid Repeating in 2025
OK, we all know that bad guys will never stop looking for ways to sneak into organizations’ systems and that cyber threats are unending. However, you can mitigate the risk of attacks and stay ahead of emerging threats by adopting a multi-layered and proactive defense strategy.
Use the lessons learned from the 2024 battlefield as your cybersecurity blueprint for 2025 to lead your company through the modern minefield.
- Sign your code with a trusted code signing certificate during the whole software development life cycle (SDLC),
- Implement the principle of least privilege,
- Secure your private keys,
- Never hard code credentials/secrets,
- Configure your apps and systems with care, and
- Encrypt your data at rest and in transfer.
Last but not least, create a robust open-source vendor evaluation checklist and supercharge your software supply chain security to prevent potential third-party vulnerabilities. 2025 is here; it’s time to flex your muscles and get ready for the fight.


