6 Must-Haves for Your Open-Source Software Security Evaluation Checklist

Is finding the most secure open-source packages akin to finding a needle in a haystack. Add these six essentials to your open-source security vetting list
Open source software (OSS) components empower organizations to deliver high-quality products quickly and efficiently — and at a fraction of the cost when compared to proprietary ones. These publicly accessible software elements are the backbone of innovation and digital transformation.
However, selecting high-quality and safe open-source projects without compromising end-user experience can be challenging. This is particularly true in a world where developers can choose between 7+ million open-source components, and traditional scanning tools often fail to detect new-generation malware.
Fear not. We’ll explore the six most critical factors you should add to your third-party open source software security evaluation checklist to help you sift only the best (and most secure) packages for your application development project.
OSS Security: 6 Items to Include on Your Open-Source Security Evaluation Checklist
Open source components are any software, programs, applications, tools, or libraries anyone can use, view, build on, modify, and share. Usually stored on software repositories such as GitHub or Python Package Index (PyPI), these components have become very popular among companies of every size.
In 2023, over 67% of survey respondent organizations indicated they had increased or “significantly” increased their use of open-source software, fostering a culture of collaboration while enjoying faster time to market. Nevertheless, open-source components, if not carefully evaluated, can introduce unwanted vulnerabilities and put your business at risk of attacks.
These six open-source security essentials will keep the bad guys at bay by helping you select only the best-of-breed OSS.
1. Investigate the Vendor/Developer’s Commitment and Trust Level
Have you ever heard the quote: “If you lie down with dogs, you’ll get up with fleas”? The meaning is simple, and it goes well with this first key point: be careful which vendor you select, or you may end up inheriting their flaws and risks.
So, to stay clear from any compliance, operational, or reputation-related issues that could cost you dearly, ask yourself:
- Who is behind the component (e.g., an independent developer or a company)? How committed are they to the OSS’s security posture? With around 1 billion contributions to open source and public projects registered by GitHub in 2024, spotting good creators isn’t always a walk in the park. Opt for OSS elements that come from well-known organizations that won’t kill the project after a few months. For instance, companies like Red Hat or Oracle have a long history of developing components featuring a high level of open-source security.
- How secure is their software development process? Pick only vendors who follow secure coding best practices and have implemented a secure software development life cycle process (SSDLC) or a security software development framework (SSDF).
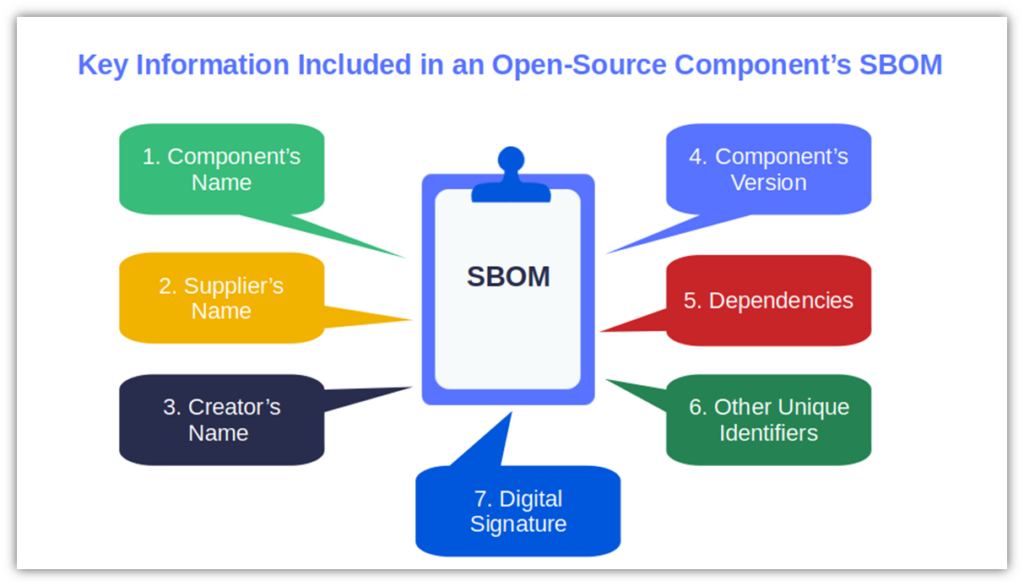
- Does their OSS offering include a software bill of materials (SBOM)? An SBOM will tell you everything you need to know about the component (e.g., version and dependencies). It’ll enable you to check and maintain its level of OSS security. By the way, the use of SBOMs is also part of the White House’s Open Source-Software Security Initiative 2024-25. So, yeah, A creator who publishes components with a digitally signed SBOM is more likely to about open-source security practices than others.
2. Evaluate the Component’s Popularity
Popularity matters — even after high school. Why should you prefer a prominent component over an unknown one? Because the more people use it, the more likely it is that’s going to be analyzed, maintained, updated, and patched.
The U.S. Cyber Defense Agency’s (CISA) Open Source Software Security Roadmap aims to reduce cyber threats by helping federal and critical infrastructure organizations create secure open source ecosystems. If you’re on the same line, these are other questions you should look to answer:
- How many times has the OSS been downloaded? If your answer is “not a lot,” then that’s not good. It’s true that codes with a large user base are often attractive targets for cybercriminals. However, Sonatype demonstrated that the OSS security vulnerabilities detected in the most downloaded open source codes are fixed an average of 50 days faster than others. That’s a huge difference, as a lot can happen in a little more than seven weeks’ time!
- Is it supported by recognized foundations? A code flaunting a badge issued by organizations such as the Apache Software Foundation, Eclipse, and the Cloud Native Computing Foundation is like a restaurant with a Michelin star. Don’t underestimate it. It’s another hint that the creator strives for the highest level of open-source security.
- What’s the level of engagement of the community around it? Generally speaking, an OSS with a large, engaged community (e.g., KDE) translates into more secure code because bugs are likely found quickly.
3. Verify How Often the Project Is Updated
According to Sonatype’s 9th Annual State of the Software Supply Chain report, an alarming rate of just 11% of , Java, JavaScript, .NET (NuGet), and Python OSSs received updates or bug fixes. To ensure you pick only properly maintained OSS projects, check the following:
- How often are the repositories updated and bugs addressed? While there isn’t a standard in terms of time frames to update repositories, it’s a good open-source security practice to promptly update components whenever a bug or vulnerability is found, even for older versions. Has the OSS not had any commits for over a year, or there are tons of open issues in GitHub? I can hear alarm bells ringing.
- Is the code you’ve selected new? Immature projects (i.e., code starting with “0” or “alpha” or “beta”) are usually less stable and have a poor open-source security posture. Trying something new, just out of the factory can be fun, but official, long-term support (LTS) versions are safer.
- Are the maintainers engaged? Maintainers are the beating heart of the codes they safeguard. If they stop working on it, the code dies, just like a body dies when the heart stops pumping blood. Are there no recent announcements about the OSS, and the maintainers are nowhere to be found? Look for another component.
4. Assess the Codebase’s Security and Trustworthiness
The SolarWinds supply chain attack, the Codecov breach, and the Log4Shell attack are just a few examples of the horrific, extensive consequences that a single flaw in the OSS’s security can lead to.
Before sinking your teeth in a new open-source component, pause and reflect on the following questions:
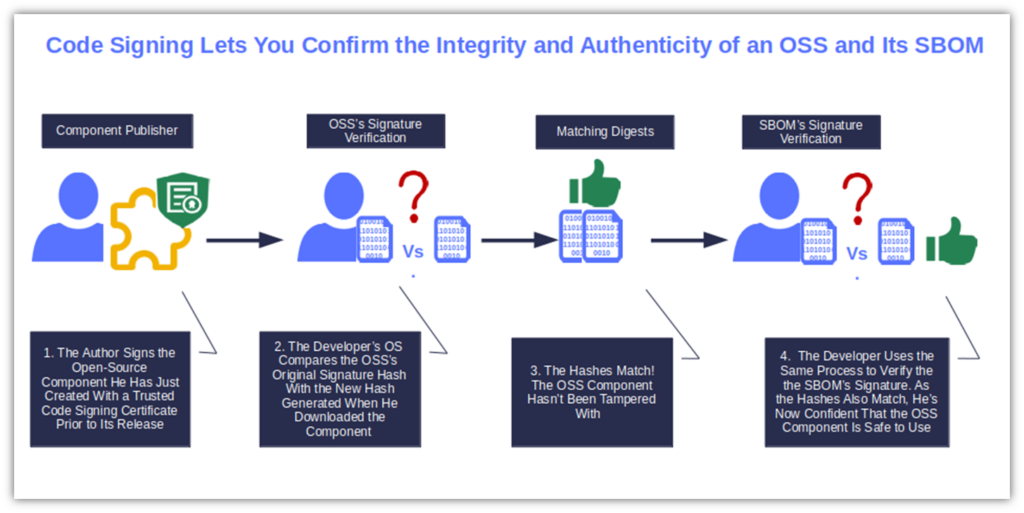
- Is the code authentic and its integrity protected? Software and commits signed with a trusted digital certificate will let you confirm their authenticity and integrity. Verifying the OSS’s digital signature will help you maintain open-source security through the pipeline and prevent you from adding infected/tampered code to your application.
- Does the OSS contain known vulnerabilities and dependencies? Validate their security, open-source initiative (OSI) licensing, and compliance status using open-source-specific security scanning programs such as software composition analysis (SCA) tools.
- Has the component been designed in accordance with secure coding best practices? To find out, download it and play with it in a sandbox. Examine the most recent commits following the Backstabber’s Knife Collection tips.Doing so might save you from disaster. In 2024, millions of Linux systems worldwide escaped malware infection by a whisker thanks to a volunteer testing a recent OSS release.
- Does the project comply with industry standards? Yup. Even the tiniest open-source component must comply with industry and regional law and regulations, such as the European Union’s General Data Protection Regulation (GDPR) and the revised Network and Information Systems Directive (NIS 2).
5. Trust, But Do Your Research to Verify
In other words, never trust anyone or anything by default. Add this zero-trust IT security model to your open-source software security evaluation checklist by pondering the following:
- What’s the OSS’s security history? Remember, you’re adding to your application something you didn’t build yourself. It’s important to do a background check, much like employers do before hiring a new employee. Scan the industry news and blogs to learn if the project was ever involved in any known security incidents. Search the U.S. National Vulnerability Database (NVD) and MITRE’s CVE database for potential vulnerabilities.
- What do other people think about the OSS? Read reviews and check the number of stars given to the repository. Determine whether the project has earned any industry recognition, such as the Open Source Security Foundation (OpenSSF) best practices badge.
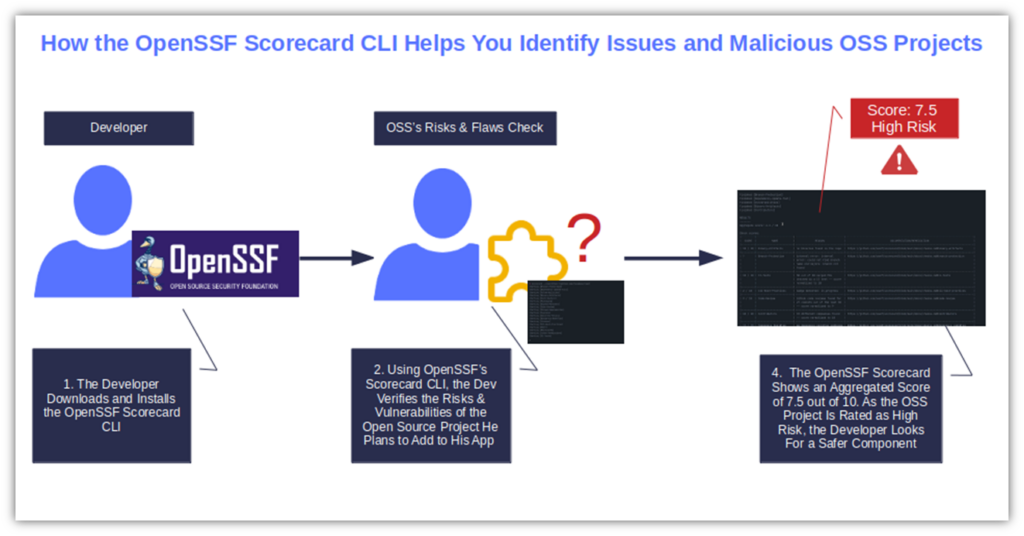
- What’s the component’s OpenSSF Scorecard score? The OpenSSF Scorecard is a static application security testing (SAST) tool that automatically scans and evaluates the security of OSS. Use it to compare different projects and select the most secure option.
6. Look for Proper Documentation
A developer could have built the best and safest component of all time, but if nobody understands what it’s for and how to use it, that OSS is worth nothing. Here are a few questions you should pose when evaluating a project’s documentation:
- Has the documentation been written with the user in mind? Developers come and go, and not everyone has the same level of knowledge. Clear documentation that’s understandable, even to a rookie, often complements well-maintained projects.
- Are all the most important documents included in the OSS? Learning how to install and use open-source libraries and code should be as painless (and as quick) as possible. Good documentation should include at least a well-written readme, an open-source license, a set of contributing guidelines, a code of conduct, and a guide file.
- Does the documentation address how to report open-source security issues? Any reliable product or service provides contact information in case of problems. Respectable component creators do the same through library websites, standard GitHub guides, or automated tools. Think about it: If the documentation doesn’t describe the process of reporting bugs and vulnerabilities, what will you do when you have an issue?
Reduce OSS Security Risks and Boost Your Open Source Security Practices
Last but not least, once you’ve picked the best and most secure OSS, leverage the power of the Open Source Maturity Model (OSMM) framework to assess how you use open-source software and detect improvement areas.
Evaluate your company’s OSS maturity by establishing if you’re only an occasional open source “consumer” or already have some established OSS security policies and rules. Then, set the level of maturity you aim to achieve that’ll enable you to use the selected open-source components to their fullest.
That’s it. You’re now on the right path to take your open-source security posture to the next level.
Final Thoughts About These Open-Source Software Security Evaluation Checklist Essentials
Open-source software can be incredibly beneficial to any organization. Its transparency and flexibility let you tap into the expertise of a huge development community while cutting costs and increasing productivity and velocity.
But as we’ve learned, all these benefits come at a cost in terms of OSS security.
By adding these six best practices to your OSS security evaluation checklist, you’ll limit your risks of exposure. This approach can help you identify the most secure components for your development projects. In turn, this will help you build stronger, more secure applications that foster trust and resilience, and boost innovation.


