How to Harden Your Software Supply Chain Security

SolarWinds, Kaseya, Codecov. What do they have in common? They’ve all suffered software supply chain attacks. Explore how to beef up your secure software supply chain with 9 killer strategies
Meet Jai Tan, the mysterious hacker who gained the trust of fellow developers in the open-source community and nearly managed to strike the king of all attacks. One so deadly that, if successful, it would have made the SolarWinds incident look like a mere trifle.
After contributing to open-source projects and getting release manager rights, (s)he introduced a sophisticated backdoor into a new version of XZ Utils, an open-source software included in many Linux distributions. Thankfully, the backdoor was discovered before disaster struck.
Dubious open-source packages are more common than we think. The number of those detected by ReversingLabs increased by a whopping 1300% in just three years (2020-23). Furthermore, 54% of global organizations polled by Synopsis were victims of a software supply chain attack in 2023.
However, open-source vulnerabilities are just one of many software supply chain security threats that developers and software publishers must be aware of. So, what can you do to secure your software supply chain? Here we’ve summarized nine strategies that’ll harden your software supply chain security. But first, let’s quickly cover our bases with a quick review of what a software supply chain entails…
A Quick Review of Software Supply Chain Components
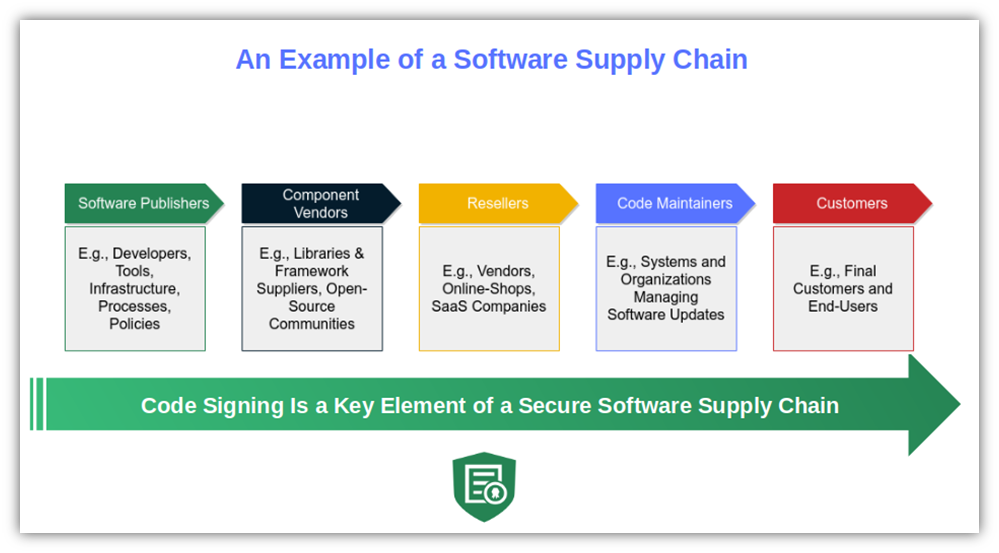
Generally speaking, the software supply chain consists of everything and anyone contributing, directly and indirectly, to
- building,
- delivering/deploying, or
- modifying/updating a software product.
Examples of these different players include:
- The software publishers. Including developers, tools, processes, policies, infrastructure, and all systems used to create and release the product.
- The third-party component vendors. Examples include external suppliers (e.g., libraries and frameworks producers), open-source communities, and service providers.
- The resellers. This group encompasses the whole distribution channel, including vendors who can modify the software before it’s delivered to customers and software as a service (SAAS) companies.
- The parties in charge of maintaining the code. These are the systems or organizations dealing with updates once the customers and end users have installed the software.
- The customers. Customers and end users. They can be severely affected even by a “minor” infection or glitch.
What Happens When Your Software Supply Chain Security Is Lacking
Imagine what would happen if your clients were to become victims of a software supply chain attack caused by unsigned software you released. It would be a logistical and PR nightmare for your company. Here are a few examples of what could occur:
- Option #1: A cybercriminal injects malware into your code during the development process, in production, after the code has been uploaded to your site, distributed, or
- Option #2: He infects the application and then uploads it to a third-party app platform/site, or
- Option #3: The attacker hacks your website or email, injects malware into your file and then re-uploads it to your official site or shares it through official channels.
All the above will lead to the same outcome: The software supply chain of every individual and company that sees you as a trustworthy publisher and downloads your unsigned (and compromised) software will be infected, creating a domino effect. The damage could be devastating.
For instance, your customers and other end users will be at risk of data breaches and other security issues. On top of it, you and all other parties in the supply chain may face data leaks or breaches, financial losses, or reputation damages.
How to Make Your Software Supply Chain Security as Strong as Steel
With so many parties involved, there are tons of elements that can become appealing attack opportunities for a threat actor, right? Luckily enough, there are many preventive measures you can implement to toughen up your software supply chain security.
We’ve chosen nine that’ll ensure you won’t leave your customers’ software supply chains (and organizations as a whole) at risk of ransomware and other cyber attacks exploiting the same vulnerabilities.
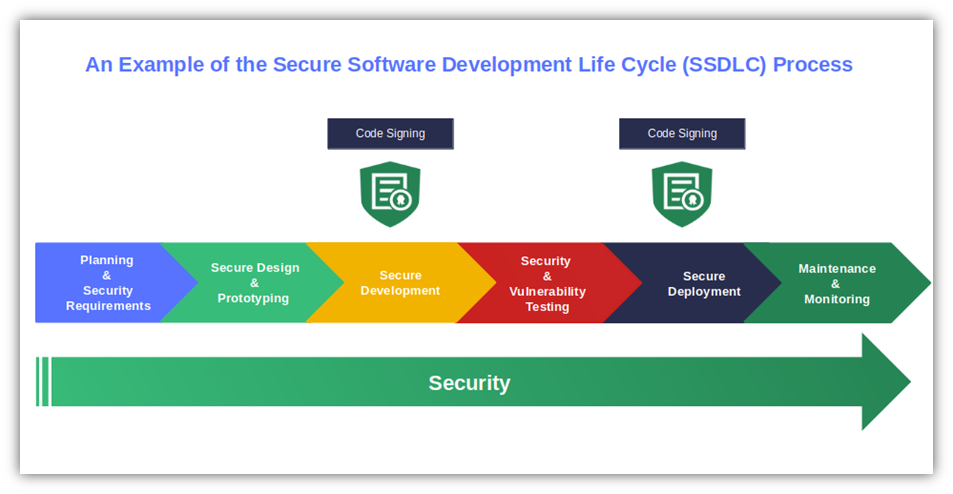
1. Embed Security Into Your Software Development Life Cycle
Checkmarx’s 2024 report shares that 91% of organizations knowingly release vulnerable code. This is one of the key points addressed by the Secure by Design initiative launched in April 2023 by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and other international organizations.
The program aims to reduce the number of flaws that make it into released software apps and shift the responsibility of security from consumers to software publishers.
The goal is to secure the software supply chain from the beginning to minimize the chances of attacks — from the design phase of the product throughout the whole software development life cycle (SDLC).
There are many ways you can achieve it. Here, we’ve listed three.
- Implement the secure software development lifecycle (SSDLC). Focus on embedding secure software development security best practices into every step of the development process. Integrate it into your SDLC in a flash using the National Institute of Standards and Technology (NIST)’s ready-to-use security software development framework (SSDF).
- Take your development process to the next level. With DevSecOps, security is at the heart of the development process. However, secure DevOps (SecDevOps) takes this concept even further, leveraging the power of automation to integrate security in each stage of the development process.
- Make secure coding a pillar of your software generation. Follow secure coding best practices to find and fix vulnerabilities right up to the end of the development process. It’ll enable you to ship highly secure products, reduce technical debt, and minimize the risk of common vulnerability exploits such as malicious code injection attacks.
2. Choose Trusted Repositories and Vendors
Open source’s popularity has reached new heights. The Synopsis Black Duck Audit Service team shows that 96% of the total codebases scanned in 2023 contained open-source components.
But when 91% of those codebases include one or more outdated elements, and 84% contain at least one known vulnerability, the convenience of using unchecked open-source software can quickly become risky business.
The time to ramp up your software supply chain security is now. Know what you’re putting into your software by:
- Assessing your vendors. Scrutinize your vendors by asking the right questions, like those suggested by NIST. Implementing a vendor risk management program and policies will also help you boost your software supply chain security and ensure all components are safe to use.
- Carefully selecting dependencies’ repositories. Not all external repositories are created equally. Utilize only those published by trusted sources that have a track record of updates and patches and digitally sign their software for added security.
- Scanning it before using it. Harden your software supply chain by scanning every open-source component using open-source scanning software. It’ll check your package dependencies for known flaws.
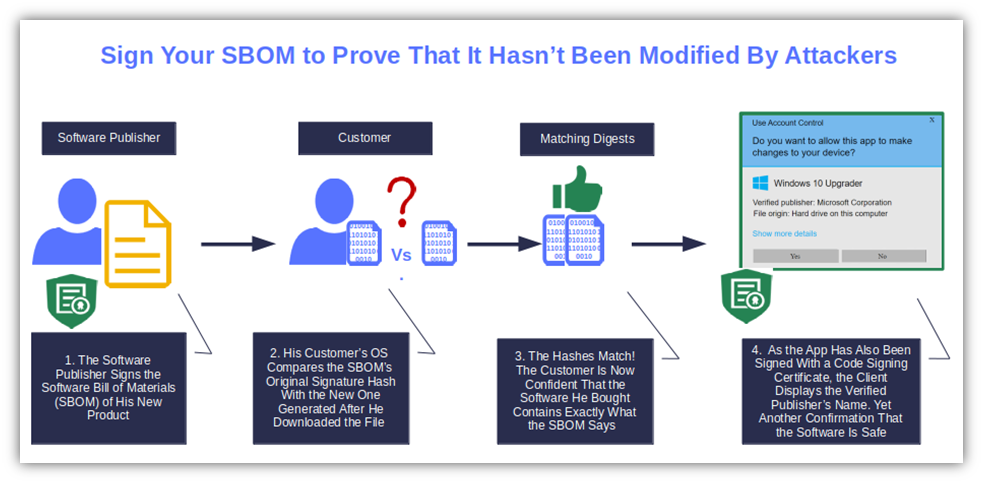
3. Create a Software Bill of Materials (SBOM) and Sign It
With the dramatic increase in supply chain attacks, SBOMs were included in the 2021 U.S. Cybersecurity Executive Order 14028. Since then, the idea of using an SBOM is no longer just a “nice to have” option for businesses looking to expand organizations’ software supply chain security. In fact, Gartner predicts that 60% of critical software publishers will make SBOM compulsory in their license and support agreements by 2026.
As a software developer or publisher, some good practices to implement include the following:
- Generate an SBOM for every software app (and keep it up to date). Doing so will enable you to quickly identify nested outdated, end-of-life, or vulnerable components, proactively address issues, and increase transparency. Your secure software supply chain will benefit from it, as they’ll know what robust (or potentially vulnerable) components went into making your product.
- Require your vendors to provide an SBOM. No matter if you’re using open-source or paid components, always ask for an SBOM and verify it. You don’t want to add something to your code without knowing what’s inside it and how secure it is, right?
- Sign Your SBOMs. SBOMS are digital files and, as such, can be modified by threat actors. Add a digital signature to your SBOMs before releasing the application. It isn’t mandatory. However, if the bad guys change it, your customers will be able to tell that it’s been altered since it was signed.
4. Sign Your Code & Images with a Trusted Code Signing Certificate
In May 2024, Justice AV Solutions (JAVS) courtroom software was compromised by a software supply chain attack. A malicious .exe file signed with a dodgy code signing certificate in the name of a phony company executed malware that gave attackers full control of any infected system.
Signing your code, images, and SBOMs with a code signing certificate issued by a trusted certificate authority will:
- Supersize your (and your customers’) software supply chain security. Tampering can occur at any point in the SDLC. Make a habit of signing your code at the development stage, too. A token-based or cloud-based code signing certificate will protect your company and your software supply chain during the whole SDLC and beyond.
- Confirm the authenticity and integrity of your code. Attaching a cryptographic signature to your containers, images, or code proves that you made and signed those digital assets and helps users immediately spot unauthorized modifications.
- Enable you to track images and code modification history. Using a cloud-based code signing certificate with a tamper-resistant solution like DigiCert KeyLocker will let you monitor and analyze who signed what, with which code signing certificate, and when. Kiss JAVS-style software supply chain attacks goodbye!
Save Up to 27% on a Standard Code Signing Certificate
Assert your organization’s verified digital identity to increase trust in your software and updates. Boost your sales and download rates for as little as $195.00/year (with a 3-year certificate).
5. Protect Your Private Keys and Secrets
DigiCert discovered that 92% of enterprises with poor digital trust practices had their private keys or certificates stolen in 2023. In the same year, GitGuardian detected a record number of 12.8 million new secrets (e.g., credentials) leaked on GitHub.
When secrets or private keys are stolen, bad guys can use them to gain access to systems and infrastructure. Reinforce your software supply chain security strategy with these three safety measures:
- Never hardcode secrets. Saving credentials or any key into an application or repository can be a convenient but dangerous practice. Did you forget to delete them before deploying the software? If so, then anyone who finds them will have privileged access to your code.
- Save your keys and secrets on industry-standard compliant secure hardware. Since June 2023, all certificates’ private keys must be stored on hardware security modules (HSMs) or tokens compliant with FIPS 140 Level 2, Common Criteria EAL 4+ equivalent or higher.
- Use secret detection tools. These scanners will enhance your software supply chain security by effectively inspecting your code, git-based repositories, and files. It’ll spot and eliminate secrets that could be potentially leaked or exploited by cybercriminals.

6. Keep Your Components Malware & Vulnerabilities Free
Software supply chain security is a worrisome blind spot for 77% of chief information security officers (CISOs) interviewed by Cycode. Bring light into your SDLC and strengthen your software supply chain security by proactively detecting software vulnerabilities.
- Install only approved (and safe) updates. Keep your components up to date, but with criteria. Lockfiles will ensure that potentially vulnerable or malicious dependencies’ updates don’t get installed without your permission, reducing the risk of backdoors and infections.
- Use automatic security testing tools. Scan your open-source components with a software composition analysis (SCA) tool every time a new build is committed. Use a static application security testing (SAST) solution to do the same for your proprietary code.
- Patch your components regularly. Monitor vulnerability databases such as the NIST National Vulnerability Database (NVD) and MITRE’s CVE. Install patches only after they’ve been thoroughly tested.
7. Test, Monitor, and Review Your Code Often
Sonatype reports in its ninth Annual State of Software Supply Chain report that for 96% of vulnerable components in Maven Central (a Java open-source component repository), a fixed version was already available.
The same report shows that the number of malicious packages identified tripled in just one year. Keep your code under strict surveillance, like the all-seeing Eye of Sauron in The Lord of the Rings. Add the following actions to your software supply chain security strategy.
- Test and scan your existing applications. Run comprehensive deep penetration tests for desktop applications. Ensure they also include a client-side network traffic scan and backend tests. They should help you identify security issues and fix them before the worst happens.
- Review code written with artificial intelligence (AI). Snyk revealed that in 2023, 96% of development teams included AI coding tools in their software supply chain security strategy. Pay specific attention to code written with AI, as this can put you and your customers’ software supply chains at risk. Follow the suggestions in the U.S. Executive Order about the safe and secure development and use of AI. Don’t miss OWASP’s first Top 10 risk list for large language mode (LLM) applications.
- Remove unused or legacy components. When checking your code, did you find unused, outdated, or unnecessary libraries or components? Get rid of them. It’ll reduce the attack surface and maximize your software supply chain security level.
8. Apply a Zero Trust Policy
In layman’s terms, trust no one. Let’s take the Codecov supply chain attack. Attackers exploited a flawed Codecov docker image creation process that allowed them to access all customers’ credentials.
A zero trust architecture (ZTA) will secure your software supply chain by:
- Ensuring that no one is trusted inside or outside your organization’s network. Everyone (and everything) is thoroughly verified before access to systems and networks is granted. This is true of your developers and other privileged users. Check the National Security Agency (NSA) paper issued in May 2024 for ZTA recommendations and guidance. Remember: never trust, always verify.
- Applying the principle of least privilege and segregating environments. Across a secure software supply chain, users should get access only to what they need to do their work. No more than that. For example, people in your production environment don’t necessarily need access to your development environment and vice versa.
- Reviewing components’ updates approvals. Do you remember when we talked about Lockfiles? A ZTA strategy means that even approved updates aren’t trusted. Automatically review them to ensure no risky third-party components are introduced into your secure software supply chain.
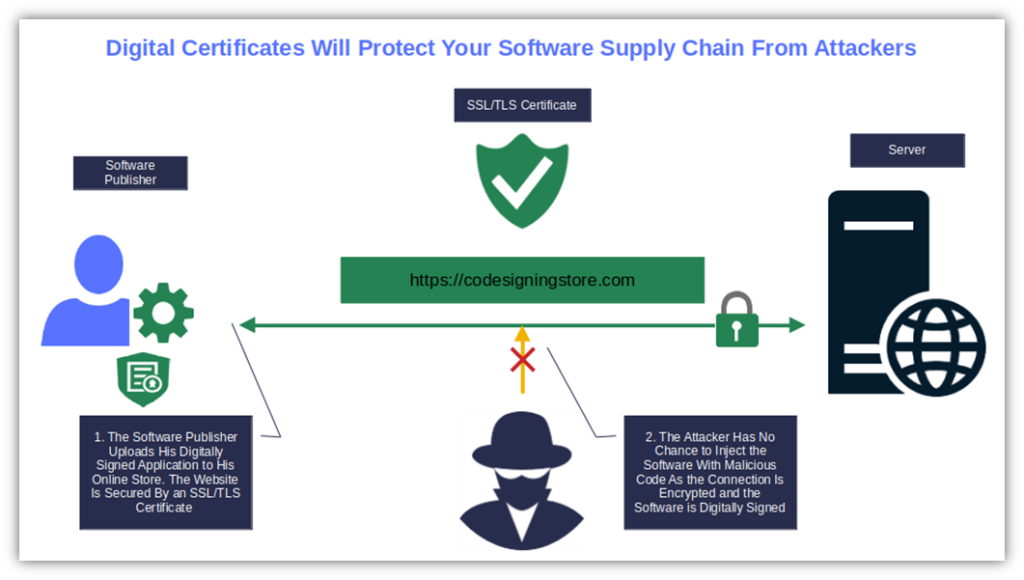
9. Use Encryption and Secure Communication
Verizon’s 2024 Data Breaches Investigation Report (DBIR) shows that 15% of the breaches investigated were the consequences of a software supply chain attack. Secure network communications are fundamental to hardened software supply chain security. Therefore:
- Encrypt your server and client communications. Installing a secure socket layer/transport layer security (SSL/TLS) certificate on your servers will create a secure distribution channel with an encrypted secure connection. It’ll prevent malicious modifications during data transmission and software download/upload processes (e.g., man-in-the-middle attacks).
- Secure your software distribution. Offer your customers a secure application download experience. Add a digital signature to your code. The client or device’s software will automatically warn the user if the software has been altered and stop the installation.
- Digitally sign emails and macros. Written communications and documentation (e.g., Excel and Word files) exchanged with third parties can also be potential attack vectors. Digitally signing emails and macros will contribute to increasing your software supply chain security.
Save Up to 27% on a Standard Code Signing Certificate
Assert your organization’s verified digital identity to increase trust in your software and updates. Boost your sales and download rates for as little as $195.00/year (with a 3-year certificate).
Why You Should Secure Your Software Supply Chain Now
A shaky software supply chain security impacts everyone. Any weak spot can become an attack vector in an instant. And when it happens, it takes a toll on everyone, from software publishers to suppliers and customers, as a ripple effect.
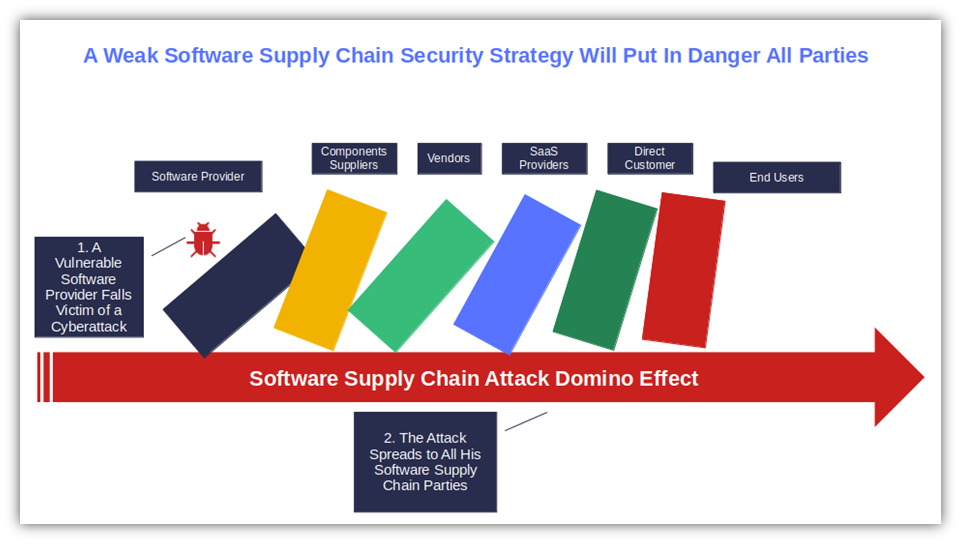
We’ve listed three key reasons why developers and software publishers should harden their software supply chain security end-to-end.
- A “weatherproof” software supply chain security prevents financial losses. Juniper Research’s latest data reveals that the global annual costs caused by software supply chain attacks will surpass $80.6 million by 2026. That marks a whopping 76% increase compared to 2023. From downtime and revenue loss to legal fees, fines, and data breach expenses, the final bill for a single business can be astronomical.
- Keeps your reputation clean. Trust matters — always. And once it’s broken, getting it back ain’t easy. 60% of consumers confirmed to Cyberint that they’d stop buying from a business that’s been hit with a data breach. Even worse, your reputation could go down the drain if your customers were the victims of the leak caused by a flaw in your software supply chain security.
- Helps you ensure compliance with regulations and laws. Do you remember the 2017 Equifax data breach? In December 2023, the company’s subsidiary (Equifax Ltd) added another fine of over £11 million to its collection because it didn’t fulfill three mandatory UK Financial Conduct Authority (FCA) Principles for Businesses. And this is just one example — there are many others you can read about in headlines over the past several years. Boost your software supply chain security to reach regulatory compliance and avoid hefty fines.
Final Thoughts About How to Harden Your Software Supply Chain Security
At the end of the day, you’re a trustworthy developer and software publisher who is responsible for the security of your products. Prove to your customers that security is at the forefront of your software development lifecycle and that you are worthy of their trust and business. Secure your software supply chain from “head to toe” by:
- Signing your code and images,
- Protecting your private keys and secrets, and
- Implementing the software security best practices you’ve learned today throughout your SDLC.
Remember: One single weakness can provide attackers with virtually endless opportunities. Enhancing your whole software supply chain security will protect your organization, code, and customers against potentially destructive attacks and will save you a lot of headaches and money down the road. Fast software deployment is good only if it’s “bomb-proof” against attackers.


