What’s the Difference Between Signed and Unsigned Drivers?

Signed vs unsigned drivers: the ultimate showdown of secure hardware. Discover their advantages and disadvantages, and which has the numbers to win the jackpot.
Drivers are the muscles of devices and applications. They’re essential pieces of software that allow them to run properly. Not all drivers are created equally, though. Some have direct access to the system’s heart (i.e., kernel-mode drivers) and others don’t (i.e., user-mode drivers). While many are digitally signed, some aren’t. And we’ll be exploring the difference between signed vs unsigned drivers today.
So, what’s the difference between signed and unsigned drivers? In this article, we’ll answer this question and break down the specifics of signed and unsigned drivers.
You’ll learn:
- What signed and unsigned drivers are,
- Their key singularities, and
- The effects signed and unsigned drivers can have on organizations, software publishers/developers, and users.
The battle of signed vs unsigned drivers has begun. Who is going to be the winner? Let’s find it out.
Comparison Table: A Look at Signed vs Unsigned Drivers
What’s the difference between signed and unsigned drivers? In a nutshell, a signed driver is much more secure compared to an unsigned one. As the name implies, a signed driver comes with a digital signature that’s linked to a publicly trusted code signing certificate (more on that in a moment), which is tied to a verified digital identity. Together, they confirm the authenticity of the code.
Thanks to the signature’s cryptographic foundation, users can also verify the integrity of the driver (i.e., it hasn’t been corrupted or modified with malware), confirming that it’s safe to install.
Now, let’s compare this to an unsigned driver.
The unsigned driver is a just code. Pure and simple code. No public key cryptography-based digital signature, no certificate, and also no way to know who created it or if it’s safe to install.
Want to know more? Check out the table below for an overview of signed vs unsigned drivers. Don’t stop there, though! Keep reading through the next sections to discover the nitty-gritty of the similarities, differences, advantages, and disadvantages between the two types of drivers.
| Signed Drivers | Unsigned Drivers | |
| Definition | A signed driver is a driver with the developer/publisher’s digital signature attached to it. The signature, based on public key infrastructure (PKI), uses cryptographic processes to bind the driver to a code signing certificate. This confirms the driver’s authenticity and integrity. | An unsigned driver is a driver without a digital signature. Thus, it’s impossible to know who published it and whether it’s been manipulated by a malicious third-party |
| Security Level | High. This is possible due to the use of hashing and encryption (i.e., cryptographic functions). | Low. The driver can be easily compromised without the user even noticing it. |
| Alignment With Industry Standards | It follows the latest Microsoft driver signing security policies. | It doesn’t follow any standards. |
| Ease of Installation | It’s easy to install as it goes through the Windows installation process. | It can be installed without error messages only by deactivating key security features, going into test mode, or using other hacker tricks. |
| Risk Level in Case of an Unauthorized Modification | Low. If the driver is modified by another party, the signature will be automatically invalidated. Users will be warned before downloading and/or installing it. | High. Users have no way to verify whether the driver has been altered by a malicious third party. |
| Security Warnings | When a signed driver is downloaded, installed, or run, no security warnings are displayed. The driver is signed and safe! | Windows will automatically warn the user every time they attempt to download, install, or run an unsigned driver. |
| Impact on Publisher’s Image | Positive. A digital signature shows customers and software users that your brand cares about their security and user experience. It can help increase revenues and downloads. | Negative. An unsigned driver radiates danger from every pore. Therefore, don’t be surprised if there won’t be many users around willing to download your drivers. |
| Customers’ Trust | It helps boost customers’ trust in your applications by confirming their authenticity and integrity. | Publishing applications with unsigned drivers will trigger security alerts during the installation process. The majority of users don’t trust such applications. |
Signed vs Unsigned Drivers: What Does It Mean If a Driver Is Signed?
In short, if a driver is signed, the software publisher has added a digital signature to prove its authenticity and integrity. But what does this signature really signify for developers and users alike? Is it just an extra tab on the driver’s properties? Nope, it’s much more. Because signed drivers:
1. Are More Secure
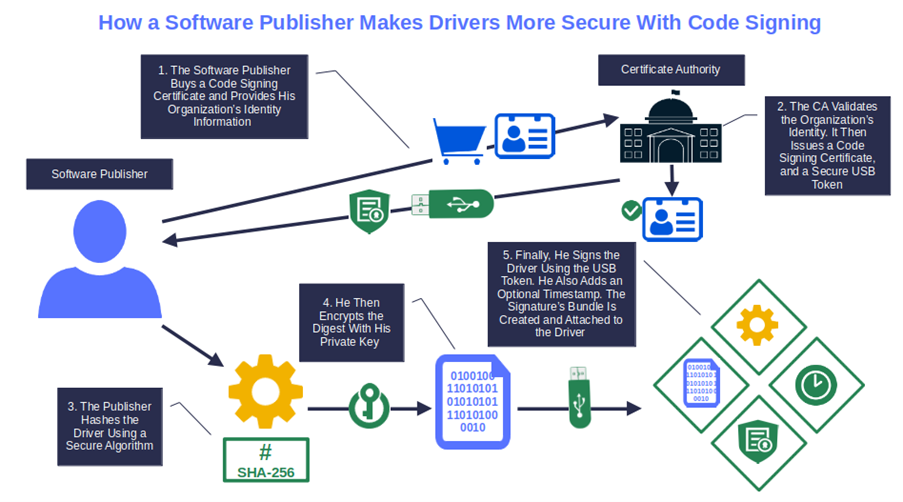
To sign a driver, a developer uses a cryptographic function (i.e., hashing algorithm) to hash it. Afterward, they encrypt the resulting hash value (i.e., hash digest) with their private key. The signed digest is then packaged with the driver and the developer’s digital certificate, attesting that they published and signed the code.
When a user attempts to install the driver, their client uses the public key to decrypt and validate the certificate. It then generates a new digest to compare it with the original one to verify its integrity (more on this in point four).
This combination of hashing and asymmetric encryption, together with the code signing certificate that’ together with the code signing certificate issued by a trusted certificate authority (CA) only after a vetting process, something no one can do without nowadays. Hackers are being as active as ever: Between March 1 and May 31, 2023, BlackBerry identified an average of 11.5 malware attacks per minute.
2. Align With Industry Standards
I get it. All those standards to abide by can be a pain. Sometimes, they’re updated — like it happened recently with the industry’s Code Signing Certificate Baseline Requirements — and organizations have to deal with the changes.
Nevertheless, they’re the digital world’s seatbelt, annoying but necessary for safety and security. Signing your drivers will help you comply with the latest industry standards. It’ll ensure your drivers will be accepted by major distribution platforms and will work smoothly.
For instance, all Windows drivers for the 64-bit version must be signed to be able to run on the operating system. Moreover, since Windows 10, version 1607, all kernel-mode drivers and driver packages (e.g., user-mode printer drivers) must be signed twice. Yup, two separate publicly trusted signatures. The signatures must be applied by:
- The publisher, using an extended validation (EV) code signing certificate, and
- Microsoft, through the Windows Hardware Developer Center Dashboard portal (Dev Portal).
Find it too much? Well, you can skip it, if you wish. However, in the best-case scenario, an alarming warning will be displayed during the download. In the worst case (e.g., kernel-mode drivers), you won’t be able to distribute it through the usual channels (e.g., Windows update), and its installation will be blocked. This takes us to the next point.
3. Guarantee a Smooth and Secure Installation
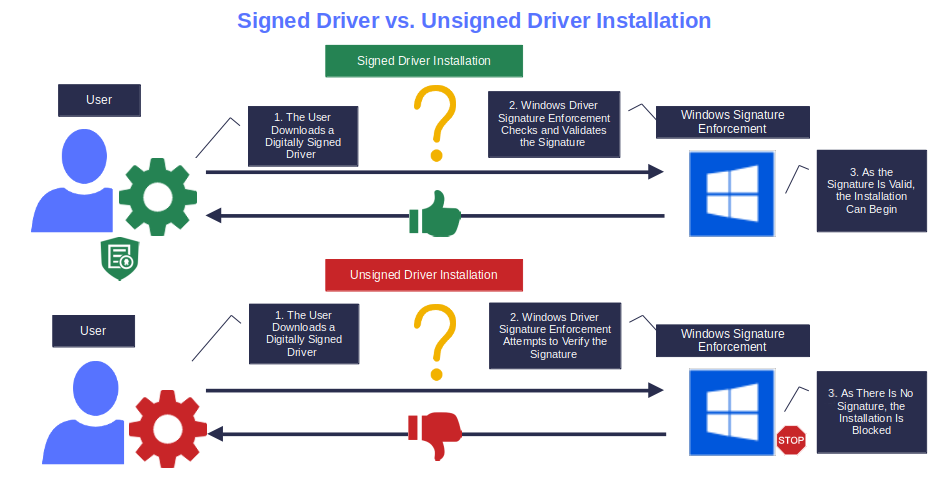
A signed driver is incredibly easy to install. Let’s say you’ve just published a new driver version for your Windows application. If you’ve signed your driver package following Microsoft’s process and published the driver to Windows update, it’ll be automatically pushed for installation in the next scan. The user will then be able to install it quickly and easily.
The same goes for hardware drivers. For example, with plug-and-plug (PnP) hardware, Windows automatically detects, installs, and configures most PnP drivers as soon as the hardware is connected (e.g., printer, USB, mouse, you name it). Cool, huh? And it gets better. The operating system (OS) will only search for drivers that are compliant with the Windows driver security policies mentioned in the previous point.
But what if the driver must be installed manually because, for whatever reason, it isn’t available in the Windows catalog? For example, think about very specific niche drivers. Thanks to the Windows driver signature enforcement, the installation will be a piece of cake, and highly secure as the feature blocks the installation of unsigned drivers.
4. Enable Users to Spot Unauthorized Modifications or Corruptions
Malware has become a big issue for users and organizations alike. In the first half of 2023, TrendMicro identified 14 new ransomware families. According to the latest Verizon Data Breach Investigations Report (DBIR), 74% of data breaches in 2022 were caused by the human element.
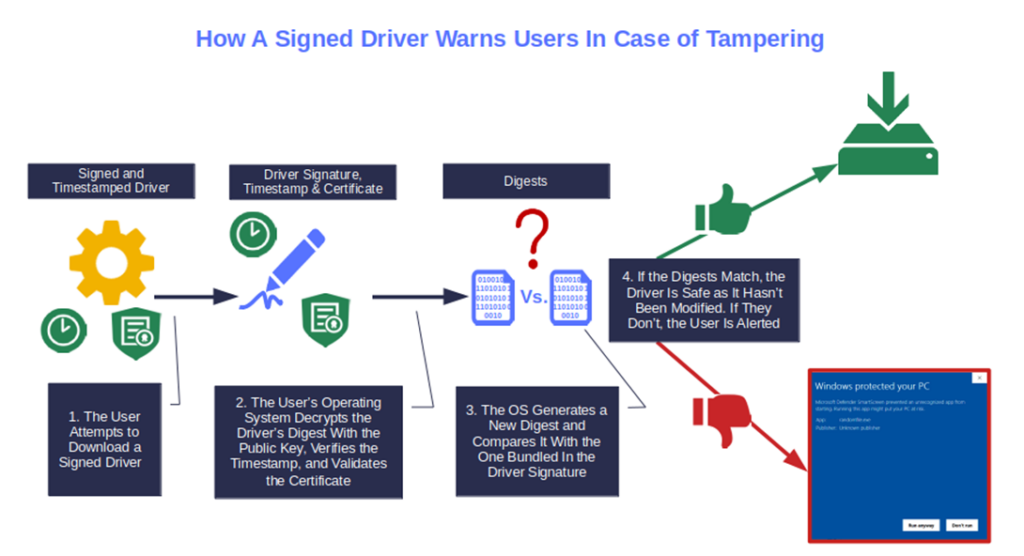
A signed driver allows customers and users to verify its integrity before installing it. How? The developer uses hashing, a one-way cryptographic hash function that generates a unique string of characters (i.e., the hash value or digest) that gets attached to the driver.
Let’s say an attacker alters your original signed driver by inserting malicious code. This modifies the hash value. When a user downloads it, their client automatically tries to verify the driver’s digital signature. It generates a hash digest and compares it with the original one embedded in the signature.
As the driver has been altered, the two digests won’t match. Consequently, the download will be stopped, and the user alerted. Why? Because this is the beauty of hashing algorithms. Every time even a minuscule change is applied to the code, the new digest changes completely:
5. Reduce or Even Eliminate Security Warnings
Have you ever seen the following pop-up warning screen?
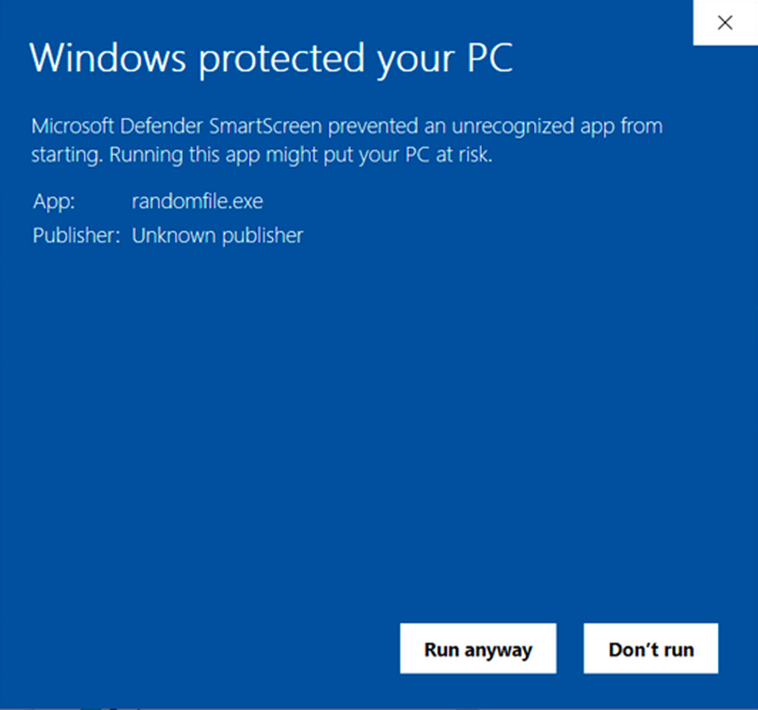
I bet you have. This is the typical warning that Windows OS will display when you attempt to download unsigned software. (It’s the Microsoft Defender SmartScreen) In practice, it’s saying that the software looks dodgy. Not good, right? In the case of the screenshot above, it’s related to an executable, but you’ll get a similar pop-up window for unsigned Windows drivers.
Signing your driers with an EV code signing certificate will eliminate the warning altogether because Windows operating systems will trust it automatically. Alternatively, user-mode drivers signed with a standard certificate (remember, kernel-mode drivers can be signed only with an EV certificate) will show a pop-up displaying the publisher’s details.
6. Bolster a Publishers’ Reputation
What can a signed driver do for your image? It can make it shine by showing the world that you care about security, and that you’re actively doing something about it. The reward can be bombastic. In fact, 73% of consumers surveyed by Edelman in 2023 engage more with brands that provide an increased sense of safety and security.
A good reputation will draw more customers/downloads, which can result in higher revenue. It’s no surprise that according to the “Approaching the Future 2023: Trends in Reputation and Intangible Asset Management” report, corporate reputation is the third strategic priority area for more than 50% of the organizations interviewed by Corporate Excellence — Centre for Reputation Leadership.
So, as Aquarius’s song says: “Let the sunshine, let the sunshine in, the sunshine in…” and watch your organization’s reputation (and earnings) grow.
7. Strengthens Consumer Trust in Your Application(s)
All relationships are built on trust. The relationship users have with the applications installed on their devices is no exception. However, gaining and maintaining customers’ trust isn’t easy, above all when you’re dealing with software, as demonstrated by recent surveys:
- Fewer than 2 in 5 customers interviewed by PWC in 2023 strongly agree that they’d forgive a company that breached their trust.
- 58% of consumers who responded to the Deloitte 2023 connected consumer report, are concerned about security breaches and tracking through their devices.
So, how can a signed driver make the difference and prove that your applications are trustworthy? A signature uses a code signing certificate that’s issued by a publicly trusted CA, which follows the standards set forth by the CA/Browser Forum, in addition to cryptographic functions to create a signature. Together, they create tangible proof that the application’s drivers are generated and signed by an authentic person or entity and are unmodified.
This is what customers are looking for. Show them evidence that your applications are secure, and they’ll trust you blindly.
So far, so good for signed drivers. But what about unsigned drivers? Are they really so bad, or do they also have some advantages? This is what we’re going to find out next.
Signed vs Unsigned Drivers: What Does It Mean When Your Driver Isn’t Signed?
To put it short and sweet, when a driver is unsigned, the user has no way to know who created it in the first place or if it has been compromised. Therefore, it can’t be really trusted.
Think of it like a Tinder profile. The pictures linked to it may be of a gorgeous girl, but who knows who’s really behind it? There’s nothing to certify its originality, right? The same goes for unsigned drivers. And this is only the tip of the iceberg. In fact, an unsigned driver:
1. It’s Highly Unsecure
Unsigned kernel-mode drivers are the ultimate golden tickets for attackers. They’re basically a passe-par-tout —a free-access pass — to the whole OS. Once infected, the bad guys will have access to the entire device. They’ll be able to perform any highly privileged operation they want, no exception made.
User-mode drivers might offer a much more restricted action as they don’t have access to the device’s core (kernel). Yet, if loaded with malware, they can wreak havoc. For instance, attackers could use an unsigned user-mode driver to lock out a user or a whole organization from their files.
Does it sound familiar? Yup, ransomware. This highly dangerous malware, according to Corvus Insurance, hit a record increase of over 95% year over year by September 2023. And a recent Sophos survey showed that a single ransomware attack can cost organizations an average of $1.82 million. Holy moly!
2. Precludes Its Distribution Through Main Channels
In the digital world, an unsigned driver is a dangerous driver. This is why no unsigned driver:
- Can be pushed through Windows Update
- Gets included in the device manager’s search for driver update results
- Is generally published on reputable software and hardware vendors’ websites
So, how are you going to reach your potential customers if you’re locked out from all main distribution channels? OK, you could always publish it on your own website, but do you really think that it’ll go very far? It probably won’t if you consider what we’ve just said about trust.
3. Can’t Be Installed Without Deactivating Standard Security Features
Some time ago, I upgraded the hardware of my old Windows 7 laptop and decided to install Windows 10 OS. I downloaded the ISO and, as my Stone Age printer was still in service, I decided to add to the OS image the related printer drivers.
As soon as I started the installation, the process stopped abruptly, and the “No signed device drivers were found” error message came up. I was stuck. At first, I couldn’t understand the reason behind the error. Then I remembered: The printer drivers were unsigned. They were way too old.
What could I do? Well, the only way out was a dangerous workaround that isn’t really recommended, above all to “standard” users. As I had no choice, I went for it and disabled Windows secure boot.
Careful, though. Disabling Windows Secure Boot should only be used when there are really no other options. This security feature should be re-enabled immediately after installation.
4. Triggers Several Security Alerts and Error Messages
What if, instead of adding the driver to the ISO, a user first makes a clean installation of the OS, and only after, attempts to install the unsigned driver he saved on a USB stick? Would they have the same problem?
Yes and no:
- No, because the user won’t get the same error message. This, time they’ll be warned that “Windows requires a digitally signed driver”, which is basically the same thing.
- Yes, because they’ll still be unable to proceed with the unsigned driver installation.
The solution? There are a few workarounds available. However, it isn’t something you want to try at home or suggest to your users unless you’re willing to take the blame (and bear the costs) if the worst happens. Imagine if the user forgets to remove the workaround and falls victim to a data breach. One incident alone could cost him — and maybe you — an average of $4.45 million.
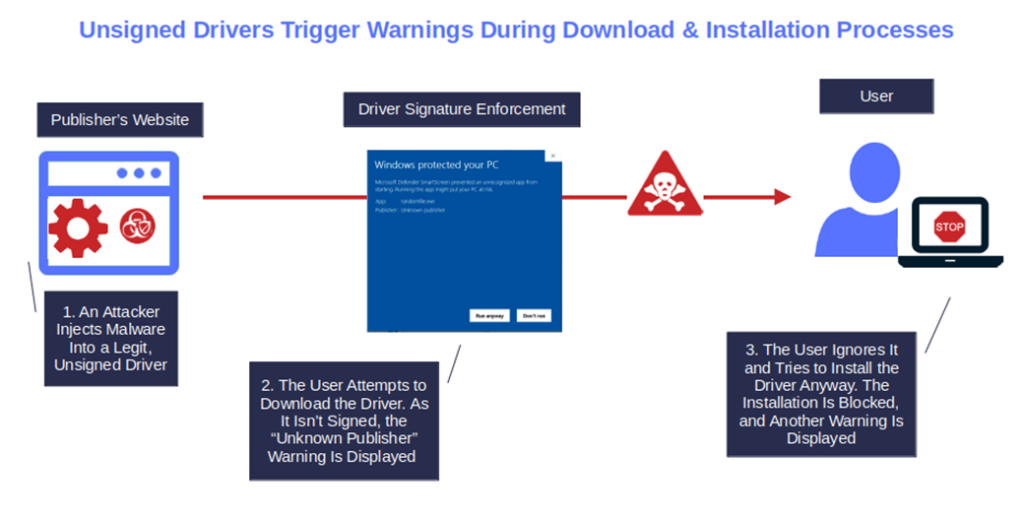
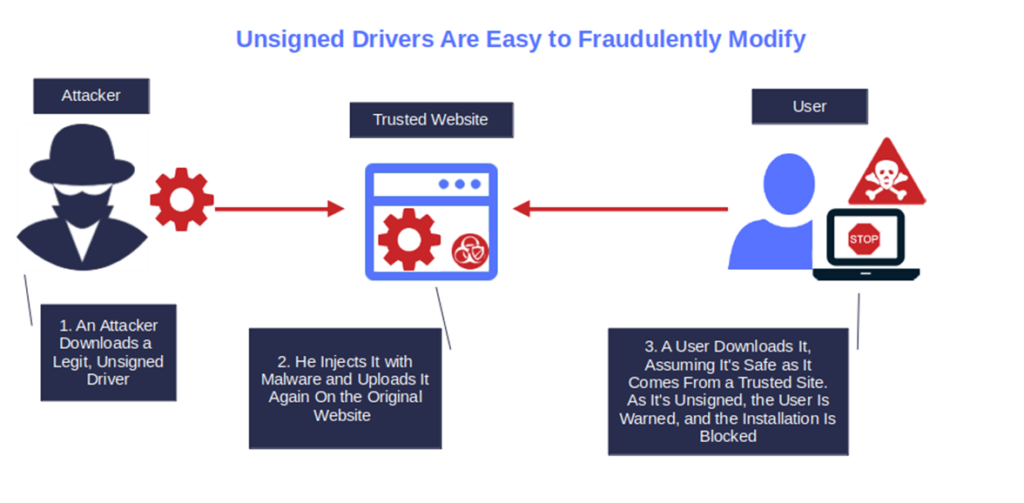
5. It’s Easy to Fraudulently Modify or Infect With Malware
Publishing an unsigned driver on your website is like leaving an opened box of chocolate bonbons in front of a kid and expecting them not to touch it. As soon as you turn your head, the box will be half empty.
Injecting malware into an unsigned driver and tricking users into installing it is a walk in the park, even for the less skilled cybercriminal. The driver has no protection, no indication about the author, nothing. It’s a bottle with a label without ingredients on it.
All the attacker has to do is as follows:
- Get ahold of the driver,
- Inject the malware, and
- Upload it using the same file name on the original website.
Et voila’ les jeux sont fait like the French say, the game is over.
6. Hurts the Publisher’s Reputation
The latest Edelman Special report shows that 59% of consumers are keener to purchase products from brands they trust, no matter the price. Are you really prepared to give up such a large number of potential customers to save the cost of a code signing certificate?
After all, as we’ve learned in this article, it has become clear that publishing unsigned drivers isn’t a good deal for a publisher’s reputation. It will not only cut the organization out from major markets and distribution channels, but it’ll also leave an open door to attackers, negatively impacting its brand.
7. Kills Customer Trust in Your Application(s)
And when the reputation goes down, your customers’ trust falls, too. You don’t think a single, unsigned driver could affect the popularity of your best application? Try to install it on another device you control. You’ll quickly change your mind.
Yes, if you have signed your application, the download won’t be a problem. No warning will be displayed. But what happens when you attempt to install it? Windows Signature Enforcement kicks in and blocks the installation. Bang! Can you see the trust your customer had in your application “fade to gray,” just like the Visage song?
In conclusion, now that you know the answer to the question “What’s the difference between signed and unsigned drivers?” who won the battle of signed vs unsigned drivers for you? The signed drivers? Good. Then it’s time to act. Add your very own digital signature to your Windows drivers now!
Final Thoughts on What’s the Difference Between Signed and Unsigned Drivers?
So, based on what you’ve just learned about signed vs unsigned drivers, which one would you choose?
- A signed driver that’s associated with a publicly trusted digital certificate and that confirms to users that your product is safe to install, showcases your security commitment, and boosts your downloads (therefore sales) or,
- An unsigned driver that triggers unlimited error messages and warnings during installation and, if compromised, may stain your reputation permanently, and can’t be distributed by Windows update?
I guess I know the answer. Now that you know the benefits and advantages of driver signing, take it a step further. Put your investment to work. Use the same code signing certificate to sign your MSI installers, executables, and JAR files.


