A Guide for Driver Signature Enforcement for Windows 7/10/11
Explore our complete guide to Windows driver signature enforcement. This built-in Windows feature increases the security of your operating system by detecting and blocking the installation of unsigned (and potentially dangerous) drivers.
Have you ever wondered how an operating system takes long streams of binary code and transforms them into graphic images, videos, or sounds? Drivers are the key software ingredient that makes the “magic” happen.
They’re the ones that, behind the scenes, guarantee that the operating system, software applications, and the hardware attached to your device work properly. As such, they’ve become an appealing target for cybercriminals who want to introduce malicious code into a system.
Having Windows driver signature enforcement enabled reduces infection risks by preventing the installation and execution of potentially dangerous unsigned drivers. Keeping the Windows driver signature enablement feature active is a quality that shouldn’t be overlooked, given that the number of newly detected malware families increased by a walloping 135% over the past five years. In this guide, we’ll look under the hood at what driver signature enforcement is, how it operates, how to manage it, and how it can help you prevent cybersecurity attacks.
What We Mean by “Driver Signature Enforcement”
Driver signature enforcement is a security feature enabled by default in all Windows versions, starting from Windows Vista. Every time a new driver installs/runs, this security mechanism checks several key factors:
- Whether the driver has been signed with a valid code signing certificate,
- If it’s been verified and signed by the Windows Hardware Developer Center, and
- Whether it has been signed by Microsoft.
The installation is blocked if any of these security requirements are unmet. Basically, driver signature enforcement shields users, organizations, and devices against installing malicious software.
It’s a considerable step forward in the security of Windows devices. Before its advent, the operating system had no way to automatically validate, authenticate, and block suspicious software installations. It just displayed a pop-up warning “Do you want to run this file?” leaving the final choice to the end users who often had no idea about the risk involved. Leaving this choice up to a potentially unassuming employee isn’t the best solution when you consider that the human element remains the root cause of 74% of data breaches.
Simply put, Windows driver signature enforcement was the breakthrough. Built on top of the groundwork done by code signing certificates, it taps into their capabilities. This takes the security of computers to the next level — no user actions required.
Sign Windows Drivers (and Save Up to 21% While Doing So)
Digitally sign your Windows drivers using an extended validation (EV) code signing certificate for as little as $277.71/year for a 3-year certificate.
How Does Driver Signature Enforcement Work?
In layman’s terms, driver signature enforcement acts much like a border officer checking passports. If everything is fine, you can go on your merry way, but if something is wrong with your papers (e.g., the photo doesn’t match your face or your passport is expired), you won’t be allowed to continue your journey.
Likewise, when a user attempts to install/run an infected, unsigned driver or a driver with an expired digital signature, driver signature enforcement steps in. This security mechanism:
- Checks the driver’s certificate and the digital signature to identify the issue,
- Stops the installation, and
- Warns the user of the security risks.
No more risks of making the wrong decision, and no more installation of infected, suspicious, or incompatible drivers.
So, if code signing certificates alone aren’t the Holy Grail of drivers and device protection, why should you, as a software provider, invest time and money into signing them? There are a few jolly good reasons why you should, and we’re going to explore them now.
Why You as a Software Publisher Should Always Sign Your Drivers
Since the 2016 release of Windows 10 version 1607, before you can publish a new Windows 10 or 11 driver, you first have to:
- Sign it with an extended validation (EV) code signing certificate issued by a trusted certificate authority (CA),
- Successfully complete the Windows Hardware Developer Center verification process, and
- Get it signed by Microsoft.
Yet, code signing certificates are more than just a way to ensure customers can smoothly install your software without being blocked by their operating system’s driver signature enforcement. They also serve several other important functions:
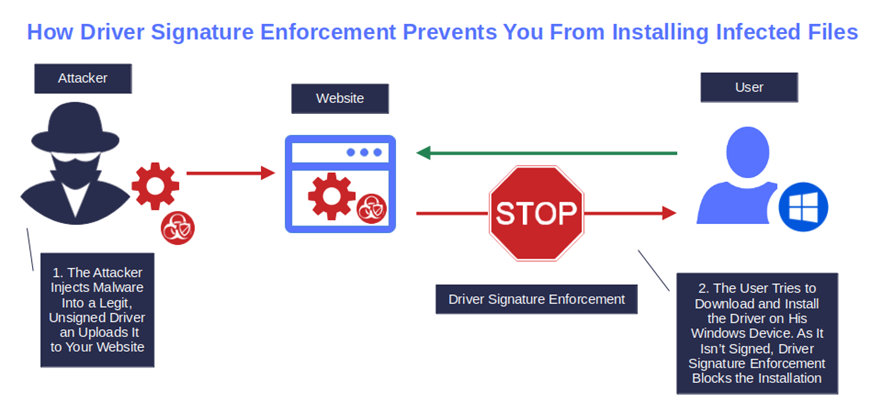
Prevent Users and Customers From Installing Malicious Drivers
According to Trend Micro research, in 2022 the number of kernel-based attacks increased by fivefold compared to 2015. The combination of code signing and driver signature enforcement ensures that, when a user attempts to install an unsigned driver, the installation stops, and an error message “Windows Requires a Digitally Signed Driver” is displayed.
Enhance the Security of Any Device
Kernel-mode drivers have always been among cybercriminals’ favorite entry points. This year, 2023 makes no exceptions. By compromising drivers, attackers are virtually guaranteed high-privileged access to devices’ systems and resources while enabling them to bypass detection.
With code signing verification, installing an unsigned kernel-mode driver bundled into a Windows 10 or 11 ISO isn’t possible. The warning “No signed devices were found” will display when a user tries. Frustrating as it may be from a user perspective, it’ll keep your customers and organization’s devices secure from falling prey to kernel-driver-based malware attacks.
Confirm Driver’s Authenticity and Integrity
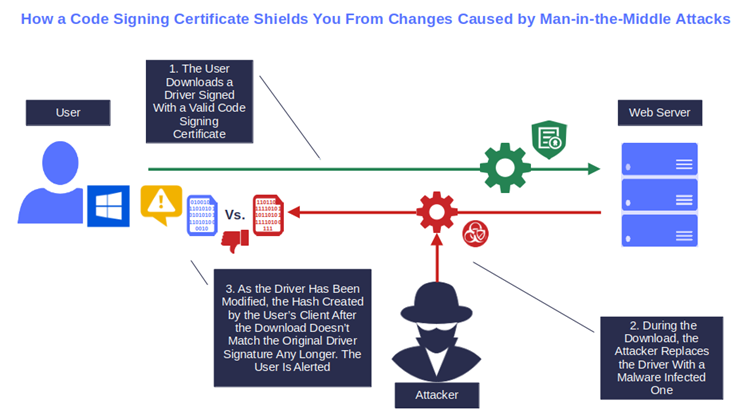
How can your customers trust what they’re downloading from your website and the internet? Authenticity is a big deal for 51% of consumers interviewed by Edelman in 2023. Their research also shows that more than half (59%) of their consumer survey respondents are more likely to purchase products when they trust the brand.
Signing your drivers and software with a code signing certificate enables users to confirm the integrity of your codes. It’ll also guarantee them that the code hasn’t been altered during the download (e.g., man-in-the-middle attacks).
Let the Users Verify Who Signed Them and When
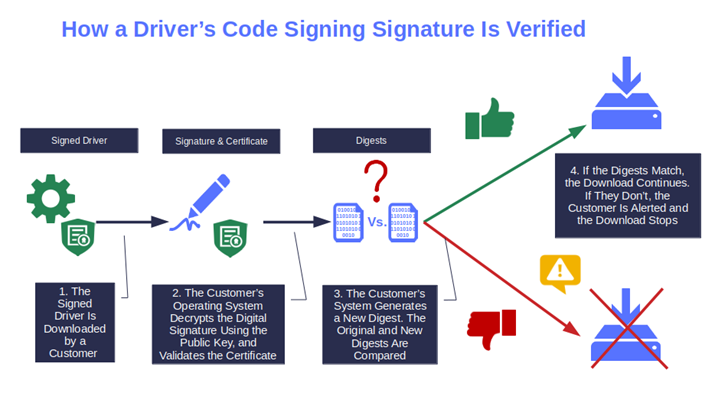
A digital certificate is issued only after the CA has validated your identity as a legitimate software publisher. Validation is a meticulous process that involves using official third-party documentation and government documents to verify your identity. When you sign your drivers using one of these certificates, your customers can check the certificate’s info to view your organization’s details and know exactly when the files were signed.
The same certificate proves that your drivers comply with Microsoft security and compatibility policies, giving additional peace of mind to your clients.
Ramp Up Your Sales and Customers’ Trust
The aforementioned Edelman survey shows that 73% of people consider brands more valuable that are perceived as having strong security. That’s 9% more than in 2022. So, if you’re wondering what’s in it money-wise for you, this is the answer — greater trust that can contribute to greater leads and sales.
Driver signing adds a seal of authenticity, security, and integrity to your software products and drivers. It increases customer trust and subsequently, profitability. Furthermore, as a proud owner of a code signing certificate, you’ll be able to utilize it, not just to secure your drivers but also your software, executables, apps, and scripts.
Aren’t all these very good reasons to sign your drivers?
But what if you need to install an unsigned driver? Is doing so impossible because of Windows driver signature enforcement? Hint: it isn’t. The beauty of driver signature enforcement in Windows 11, 10, and 7 is that it can be configured even to meet this specific requirement. Let’s find out how.
How to Securely Manage Driver Signature Enforcement in Windows 10, 11, and 7
While driver signature enforcement automatically checks the signature of every driver you attempt to run and/or install, and ideally you should never change it, you still have the option to tweak it.
This is a feature that may be useful for developers for example. Do you need to test some unsigned drivers you’ve just created throughout the development process? With all the due precautions, you can still do that, even on the most recent Windows releases.
But that should be it. Disabling driver signature enforcement outside of development or testing purposes merely because you can’t be bothered seeking other comparable drivers, or to save money, isn’t a smart idea.
Why? Because it’ll disable a built-in secure feature in multiple Windows operating systems and can lead to:
- Dangerous malware infections. Malware like rootkits (i.e., backdoor software that grants the attacker full access to an infected machine) execute in kernel mode, allowing bad guys to do basically anything, from stealing sensitive data to changing configurations and spying on the computer’s activity.
- Devastating ransomware attacks. Once they have access to your system, bad guys can use it to evade antivirus tools and even lock you out of your systems and data. Have you ever heard of Mallox? It’s a ransomware type that exploits Windows operating systems and MS-SQL servers. In the first half of 2023, Mallox attacks alone rose by 174% year over year. How much will a small/medium business have to fork out in recovery costs? Based on an independent survey, a minimum of $165,520.
- Costly data breaches. Once an attacker has access to your systems and data, they can hold them ransom. In 2023, a data breach cost to organizations an average of $4.45 million globally. One of the latest victims, Ceasars Entertainment, paid roughly $15 million ransom to the attackers. Yes, if you’re a medium or small business you may get away with less. However, you’ll still have to ramp up your cyber defenses. Businesses with less than 1,000 employees are easier targets thus, are more attractive to attackers than bigger companies.
NOTE: We do not recommend disabling Windows Driver Signature Enforcement because of the potential security risks that are at stake. Instead, we recommend only installing and using the Microsoft Hardware Developer Program dev portal to digitally signed drivers.
After all of this information, are you still willing to take the risk by disabling Windows driver signature enforcement to install one or more unsigned drivers? If so, keep on reading to learn how to do that in all recent Windows releases.
How to Temporarily Disable Driver Signature in Windows 11, 10, and 7 for Testing/Development
There are several techniques you can use to temporarily disable driver signature verification in Windows 7, 10, and 11. Here we’ll show you one of the more straightforward alternatives that’ll work for all releases.
Before we start, though, if you’re a Windows 8, 10, or 11 user, you’ll first have to reactivate the legacy F8 option. This should only take a couple of minutes, and it’s a feature you want to have activated anyway in case of trouble (e.g., you can’t boot your operating system normally).
Are you a Windows 7 user? You can jump to the “Launch the Advanced Boot Option Menu” section.
How to Activate the Legacy F8 Option in Windows 10 and 11
- Open the Command Prompt as administrator. On your desktop select Start, type “Cmd” in the search bar, click on Run as administrator, and enter your administrator password.
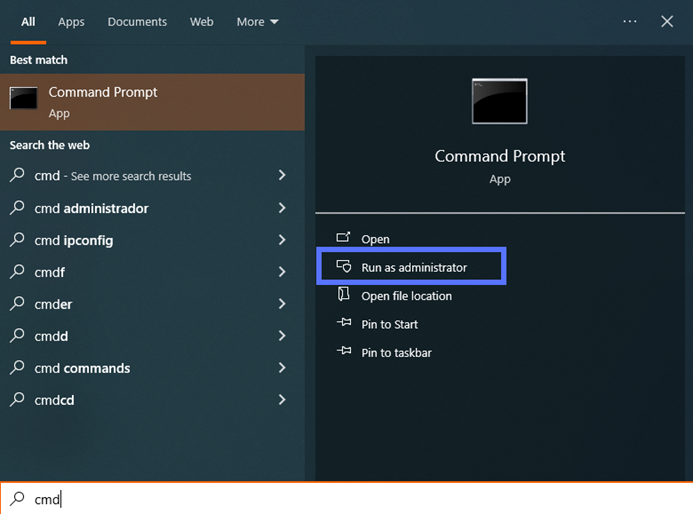
- Type“bcdedit /set {default} bootmenupolicy legacy.”Hit Enter. You can do this by writing in capitalized letters or lowercase, as some users have expressed technical issues writing it one way versus the other.
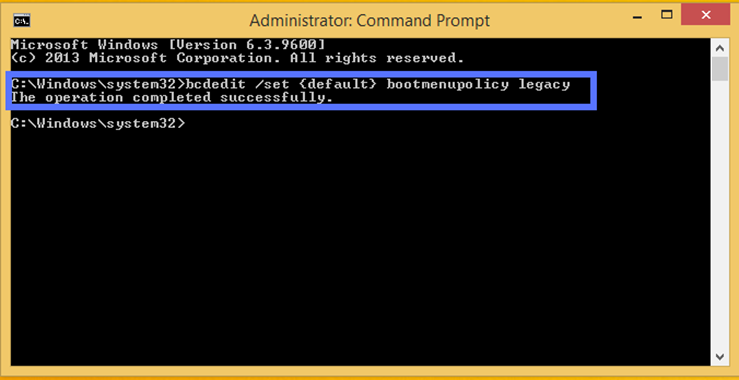
- Close the Command Prompt window. F8 is now enabled, and you can now skip ahead to the “Disable Driver Signature Enforcement” section.
How to Activate the Legacy F8 Option in Windows 8 and 8.1
- Open the Command Prompt as administrator. On your desktop, click Start, enter “Cmd” in the search bar, select Run as administrator, and type your administrator password.
- Type“bcedit /set {bootmgr} displaybootmenu yes.”Hit Enter.

And it’s done! You can now close the Command Prompt window and follow the remaining steps below.
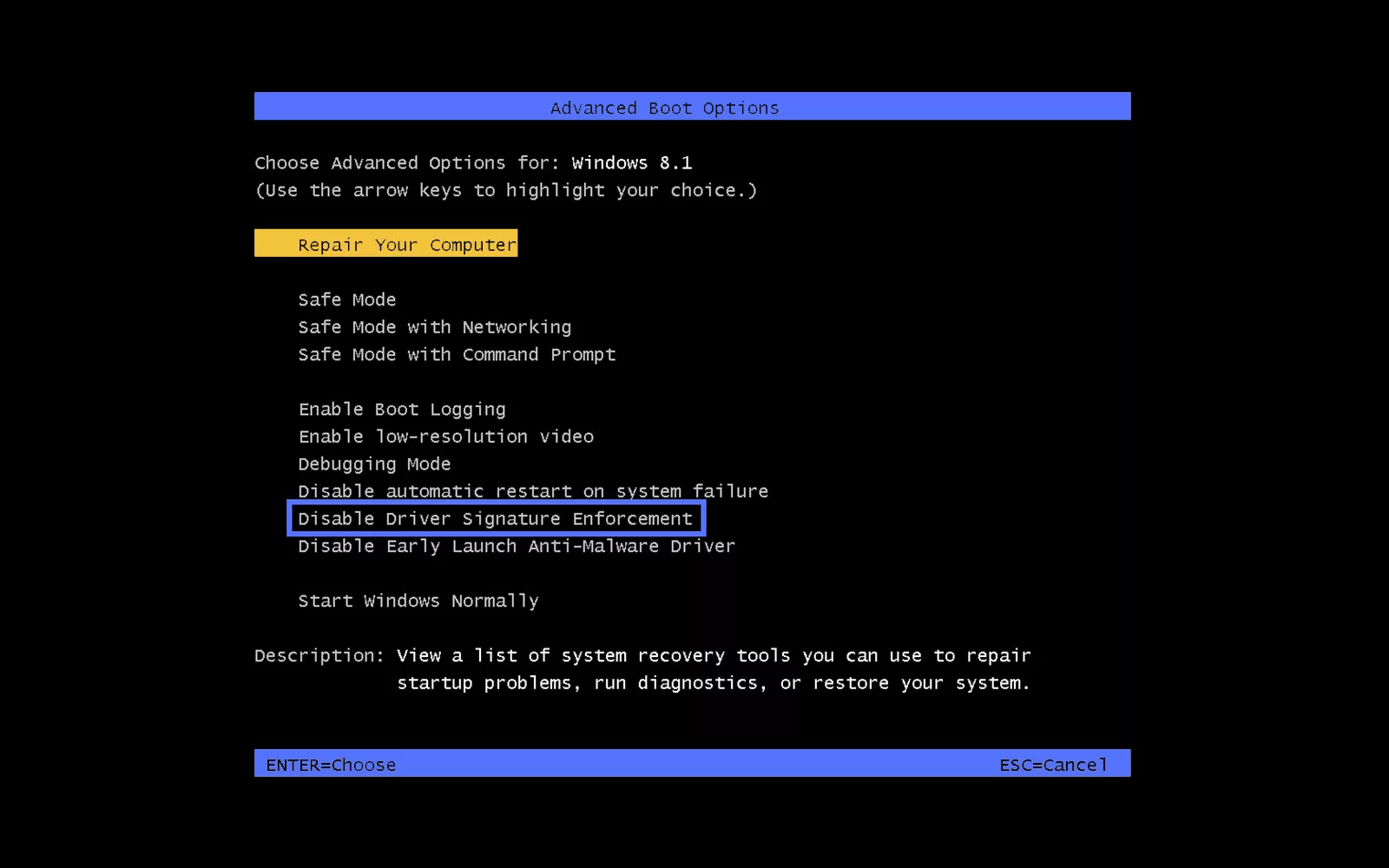
How to Disable Driver Signature Enforcement
- Reboot your device.
- Launch the Advanced Boot Option menu. To do so, hit the F8 button repeatedly as soon as the manufacturer logo appears. Alternatively, you can wait for the Windows Boot Manager screen to display and then press F8.
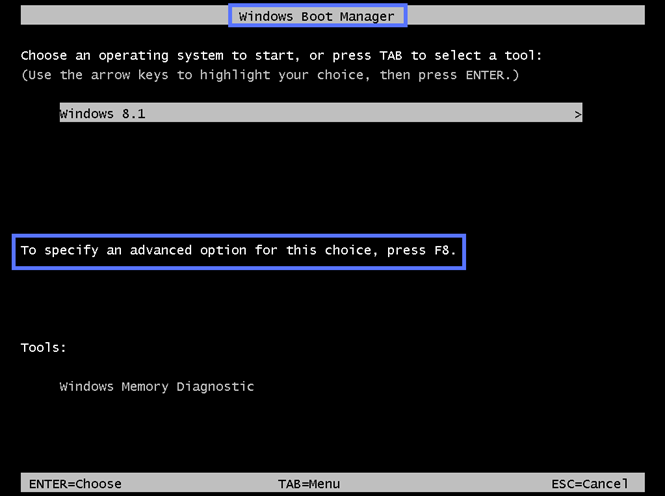
- Select the Disable Driver Signature Enforcement option using the arrow keys, and press Enter.

Done! Your computer will reboot and you’ll be able to install and run unsigned drivers. But remember, from this point on, your machine will be at a greater risk of malware infections. Therefore, disable driver signature enforcement only for testing or development purposes. NOTE: We do not recommend using this approach as a user to install unsigned drivers due to the security risks.
Immediately after installing or testing the unsigned driver, reboot the machine. The driver signature enforcement will be automatically re-enabled.
Final Thoughts on Windows Driver Signature Guide for Driver Enforcement for Windows 7, 10, and 11
Windows driver signature enforcement is a highly effective security tool. It determines whether a driver is safe and can be installed or should be blocked because of security-related concerns.
But Windows Driver Enforcement doesn’t can’t operate alone. This security feature works in tandem with code signing certificates and digital signatures to safeguard your devices, users, and organizations from the severe implications of a security incident caused by a malicious unsigned driver.
Now that you have a better understanding of how driver signature enforcement works, and how to control it, use it wisely. Don’t give the bad guys a chance. As a user, deactivate it only if you have no other options, and then scan your driver for viruses before proceeding with the installation. You’re a software publisher? Unleash the power of code signing certificates. Use them to digitally sign all of your codes and applications. You’ll protect your customers and users and demonstrate your commitment to their safety.


