6 Reasons You Should Release Signed Code and Software

Four and a half minutes: This is the amount of time it takes to make a real Italian espresso and how long it takes the newly discovered Rorschach malware to lock customers out of their files & devices. Explore how releasing signed code can help protect your customers and reputation from these types of attacks.
In 2022, 5.5 billion malware attacks rattled the world. Nearly 321 million of these attacks focused on California targets. IoT malware also played its part, reaching a new record of more than 112 million attacks; that’s an astonishing increase of 87% year over year.
Nowadays, connected devices have become an integral part of our lives, from cars to smartphones and household appliances like your TV. And they all rely on code to function. But code, like all software, must be constantly updated to try to stay a step ahead of attackers.
This brings up an important question: how can software companies prove to their customers that their software and updates are really coming from them, that they’re authentic and malware-free? Signed code can help organizations and developers alike do exactly that.
Do you really need to release signed software? Find it out by checking out our six reasons why you should distribute only signed code and software as a developer or software company.
6 Jolly Good Reasons Why You Should Sign Your Code and Software
When you go to a supermarket and look for a package of your preferred coffee beans, how do you spot it? By looking for the brand’s logo, right? That’s how companies in the real world can ensure that customers immediately know that they’re looking at an original product (i.e., authenticity). As long as the package is sealed, consumers can feel confident that the product hasn’t been tampered with (i.e., integrity). Easy as pie.
Code signing is like the virtual equivalent of physical tamper-resistant packaging. Compatible with all major platforms (e.g., Java, Windows) and browsers, it enables developers to add a digital signature to several file formats, such as .exe, .dll, and .msi, to
- confirm their authenticity and integrity, and
- validate the publisher’s identity.
I know what you’re thinking. “Why would I need virtual packaging with all the bells and whistles in the digital world? I’m not even selling physical and tangible goods!” Good question. And we have six equally good answers for you. Let’s check them out one by one.
1. Signed Code Is Protected Against Tampering and Unauthorized Modifications
According to Unit42’s research run between February and August 2022, 31% of Raspberry Robin malware attacks utilized unsigned dynamic link libraries (.dll) loading. This highly sophisticated worm was the seventh most prevalent threat observed by Red Canary Intelligence in 2022.
Once you publish your software on the internet, everyone has access to it, including malicious actors. And if the code isn’t adequately protected, cybercriminals can easily modify it or replace it with malware. How? With a man-in-the-middle attack, for example.
Let’s say you’ve just finished developing a brand-new application. You upload the file to your website but a cybercriminal manages to intercept the transmission because you forgot to renew to install an SSL/TLS certificate (oops). As the code itself isn’t digitally signed, the bad guys replace it with a re-packed infected software saved with the same name.
Then, a customer browsing your website spots the application. The customer downloads and installs it onto their device. How can they know that they’re not downloading the original file if all they can see is the file name (looking legit) and size? They can’t; however, since they’re on your official website, the customer assumes that it’s safe. Oops again, but now the damage is done.
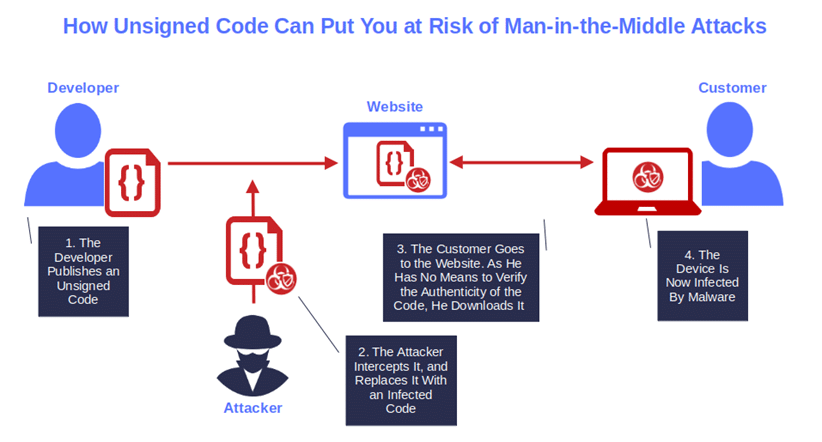
Image caption: Unsigned code can be exploited by cybercriminals to infect devices through man-in-the-middle attacks.
Distributing signed code will reduce the risk of a file being tampered with or counterfeited, re-packed, and distributed under your name. In fact, to be able to modify your code, a bad guy would need to access your private key and/or your code signing certificate (more on that later on in this article). And even if they succeed, the chances that a user downloads it will be very limited. Why? Because of what code signing is and the cryptographic functions behind it.
Let me explain in layman’s terms how signed software works. When you sign your code with your private key, a hash function is added to the signature. If the hash function matches the one created by the customer’s operating system at the time of download, it means that the code hasn’t been modified. The user will be able to download and install the software without issue. However, if the hashes don’t match, the user will get a security warning and the download will be stopped.
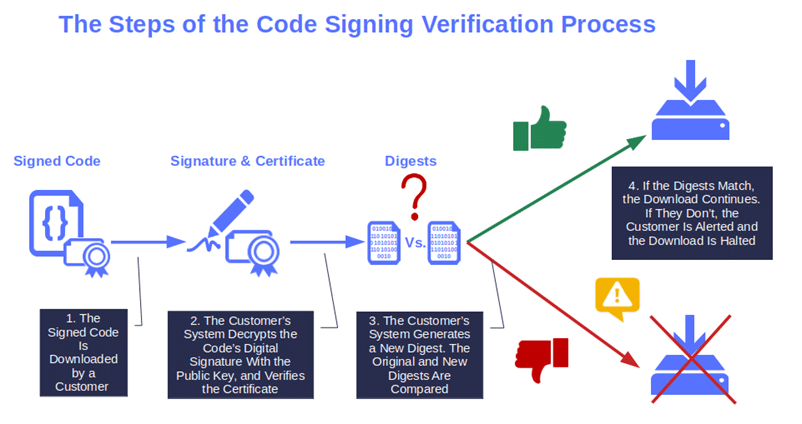
Image caption: The graphic shows how a signed code is verified. Further down in the article, we’ll explore in more detail how software is signed.
What do you think? Isn’t this already a great reason for a start? Fasten your seatbelt because the best has still to come!
2. Signing Your Code Helps You Ensure a Safe Distribution of Software Updates
From 2020 to 2023, malicious codes added to repositories and driving supply chain attacks affecting PyPi repositories went up by a stunning 18,000%. In March 2023, Mandiant identified the first software supply chain attack that set the stage for a second software supply chain attack. What started it? An infected software.
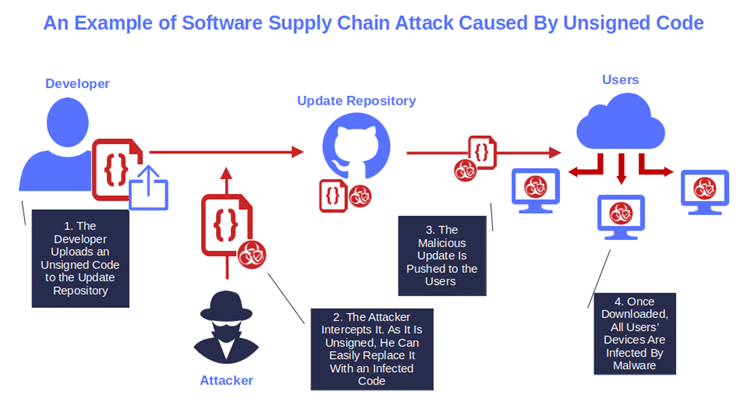
Image caption: If you don’t publish signed software updates, you’ll put your organization and users at risk of software supply chain attacks.
Distributing only signed software has become a critical security asset for the software supply chain as it helps developers and software publishers to:
- Protect the distribution of updates from malicious alterations, and
- Prove to customers that the update they’re installing is safe, authentic, and comes from a legitimate author.
I get it. With 9,497 new vulnerabilities published by CVE within the first four months of 2023, keeping software secure and flaw-free isn’t an easy task. But, choosing to send out unsigned updates can make all the effort and time you put into it meaningless. Why? The patch you release may fix the flaw but, given that it’s unsigned, it won’t free your software from the danger of malware infection and data breaches. Is releasing unsigned software really worth the risk then, when a leak of sensitive data costs more than $5 million, on average? Therefore, It shouldn’t be surprising that signed code was mentioned in the Office of Management and Budget’s (OMB) September 2022 memorandum. Among other requirements, the paper mandates all federal agencies comply with the National Institute of Standards and Technology (NIST) guidance (drawn from Special Publication [SP] 800-218, its Secure Software Development Framework [SSDF], and its Software Supply Chain Security Guidance) which includes, among other things, the recommended practice of releasing and distributing signed software.
3. Signed Software Protects Your Products From Being Used to Distribute Malware
For a developer and his organization, it’s bad enough when one of their codes gets infected by malware. But things go from bad to worse when that infected software is distributed inadvertently on the network and infects other devices with malware.
Among all the malware types, ransomware is the top 2023 concern for 48% of businesses interviewed by Arctic Wolf. In 2022, 73% of organizations surveyed by Barracuda have been victims of one or more successful ransomware attacks. A walloping 38% of organizations were hit at least twice within that same period.
How can releasing and distributing signed software facilitate reducing the chances that your code inadvertently becomes a vector of such vicious attacks?
- A code signing certificate protects the code. The certificate is issued by a trusted Certificate Authority (CA) following a vetting protocol to ensure the buyer is legitimate. This reduces the chances of counterfeiting. And using the certificate entails applying a hashing function that secures the code against unauthorized modifications.
- The software is signed by the developer using a private key. During the signing process, the code is hashed (i.e., transformed into a gibberish text) and the output (i.e., digest) is encrypted with the private key. As long as the private key is kept secure (e.g., stored in a hardware security module), the attackers have no chance to modify or add malware to your code.
But bad guys are wicked and are always up to something new. From malware-as-a-service (MaaS) based on the software-as-a-service (SaaS) model to other pay-per-use services, they surely don’t lack imagination and ingenuity. So, does signed code offer any protection against other types of attacks? This is what we’re going to find out next.
4. Code Signing Certificates Secure Your Codes and Customers Against Attacks
In the software development life cycle (SDLC), to build your application, you rely on several tools, components, third-party resources (e.g., libraries, plugins tools), and processes. What if an attacker manages to find a vulnerability in one of those elements? He doesn’t think twice, he goes for it and exploits it to his advantage.
Signing your codes, keeping every component up to date, and patching vulnerabilities will harden the security of your whole software supply chain, thus minimizing the chances of an attack. On top of that, code signing will also help you ensure that your entire code is unaltered and malware free. Why is it important? Let’s see a real-life example.
Have you ever thought that an IT outsourcer would have ended up locked out of its own IT systems because of a cyber attack? Yup, believe it or not, that’s what happened in April 2023 to Capita, one of the biggest UK-based outsourcing and business services organizations.
The impact on their customers? Pretty impressive. Capita is one of the biggest UK public sector contractors supplying services to, among others, the UK National Health System (NHS), the Ministry of Defense, and the BBC. It’s also in charge of processing disability payments for the British Department for Work and Pensions. Anyway, I guess you got the picture. And who got the worst of it? The citizens who depend on those services. Like those pensioners for example that, according to The Times, couldn’t cash their monthly retirement allowance.
OK, releasing only signed code and software won’t enable you to guarantee your customers 100% protection against every single attack, in the digital world nothing can. However, it can be an effective way to protect them from:
- Downloading and installing malware. Remember? If a customer downloads a signed software app that’s been maliciously modified, they’re alerted by an automatic warning message.
- Paying the consequences of a vendor’s cyber attack. Consider what happened to Capita’s clients, and the members of the public who depend on those services. Or, think of the customers of the organizations targeted in successful data breaches who were hit by price increases to cover the costs of those incidents.
- Being a direct victim of a data breach. Imagine if a client had his sensitive data stolen (e.g., credit card numbers, online banking username, and password) because he downloaded and installed the unsigned, infected software you published. Who do you think the customer is going to blame? You. And who is the customer going to take to court to get compensated for the damages? You, again.
Want to avert all this? Include code signing in the secure software development life cycle (SSDLC) process, and avoid downloading and including third-party, unsigned software into your code, to:
- Significantly reduce the surface of attack,
- Minimize the risk of data breaches, and
- Avoid introducing new vulnerabilities.
Believe me, your customers (and checkbook) will thank you for that.
5. Signed Software Reduce Security Warnings and Provide a Smooth User Experience
A few weeks ago, my friend bought a new laptop. It’s a top-of-the-line unit that must have cost a small fortune. As he isn’t a tech geek, my friend asked me to help set it up, and so I did. But as soon as I started downloading software, though, I quickly noticed the incredible number of warnings and alerts popping up all over the screen. Windows Defender, browser alerts — you name it. Don’t get me wrong, these warnings are good from a security perspective but, boy if they’re extremely annoying for users.
When my friend saw all those alerts, he immediately told me that they were the main reason why he often halted the installation of software and looked for something else that, ideally, wouldn’t display one of these messages. But this experience made me wonder: How many other customers do the same when they see a bunch of scary warning messages? Quite a few, I suppose.
And if they do, I can’t blame them. Sometimes, those warnings can be unnerving and scary, but they serve an important purpose. And, in many cases, running away is the best choice for the safety of your device. Like when you see the Windows Defender SmartScreen Unknown publisher alert warning you that “Running this app might put your PC at risk.”
This type of warning displays when a user tries to download unsigned software or code:
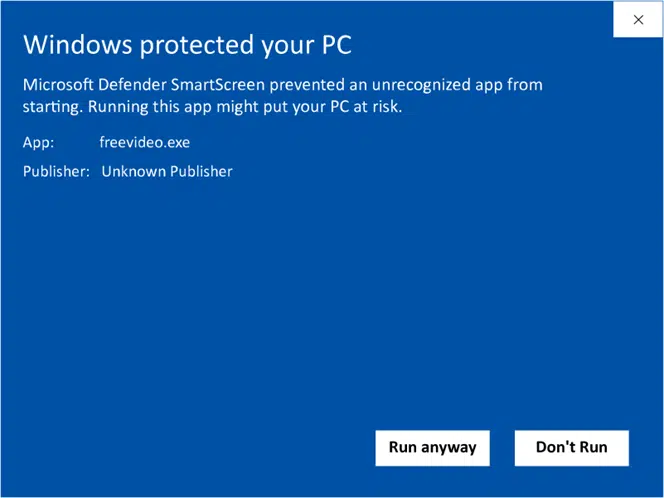
Image caption: A signed code will never trigger the unknown publisher warning.
Want to say goodbye to those pesky unknown publisher warnings when your customers install or download your software? Publish only signed code using an organization validated (OV) or an extended validation (EV) code signing certificate and the magic is done.
With the OV certificate, the details of your organization will replace the unknown publisher warning on the Windows Defender SmartScreen. Those details will also be displayed in the User Access Control (UAC) installation pop-up.
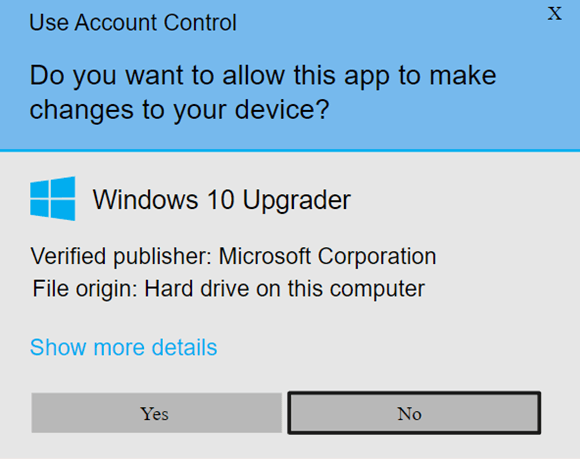
Image caption: This is what your customers will see when installing signed software.
If you go for the EV certificate, your signed software will be immediately trusted by the system and no Windows Defender SmartScreen warning will display Either way, your customers will:
- Immediately know that the code they’re downloading is authentic and safe, and
- Have no reason to spend their money elsewhere because the alternative shows no worrying security warnings and looks more ‘user friendly’ like my friend often did.
6. Releasing Signed Code Increases Brand Reputation, Downloads, and Revenue
It seems like most consumers have taken to heart the old proverb. “Fool me once, shame on you; fool me twice, shame on me.” 84% of consumers surveyed by Digital Trust stated that they’d consider buying somewhere else in case of personal data breaches or any other security-related incident. Knowing this, how do you think they’d feel if they knew that your company released software that could be tampered with?
In today’s dangerous digital world, customers prefer doing business with organizations that put security first. As a consequence, trust and reputation have become everything. Get those right, and your downloads and revenue will multiply. If you tarnish either, you’ll quickly feel the pain in the form of damaged reputation and lost business.
Want an example? A few months ago, I bought the last earbuds model from my favorite brand. They were light, guaranteed to resist dust and water, and they fit nicely around my ears. I thought they were the best earbuds I ever bought. I was happy, but that feeling didn’t last long. Within three months, they’d stopped working.
After weeks of struggles and frustration, the company’s customer service department finally offered me a replacement, which I politely declined. Why? Because I didn’t want anything to do with that company anymore and wanted my money back. See how quickly the trust in a brand can be lost forever?
Distributing and releasing signed software creates a better user experience by avoiding scary security warnings and can help build your reputation as a trusted brand. This can contribute to boosting the number of downloads because your customers will have a guarantee that the code is safe and hasn’t been tampered with.
The result? “I’m talkin’ about money, money” like Simply Red sang. Aww, yeah! Used in the right way, signed code can give a good kick to your revenue growth.
So, there you have it. What do you think? Are our six foremost reasons why you should distribute/release signed code and software good enough to convince you to invest your valuable time and money in a code signing certificate?
If the answer is yes, let’s have a quick look at how you can do that.
Want to Start Releasing and Distributing Signed Software and Code? This Is How It Works
Did you decide to start signing your codes and applications? Good choice! To do so, you’ll need:
- A code signing certificate of your choice issued by a trusted CA. You can purchase an OV or EV code signing certificate, depending on your security goals and needs. Don’t be stingy! Never use a self-signed code signing certificate for software or code that will be published online, as they’re not secure enough and don’t provide verifiable digital identity.
- Your public-private key pair (which should be stored securely). Code signing is based on public key infrastructure (PKI) and authentication therefore, you’ll need a unique public and private key to complete the signature process.
Got them? OK, time to use them to sign your first code.
- Use the private key to encrypt your code’s hash digest. The code goes through a mathematical one-way hash function. You then use your private key to encrypt the resulting digest (i.e., hash value).
- Create the signature. As a last step, the hash function, the digest (i.e., hash file), and the code signing certificate are bundled into a signature block that you can attach to your code.
Done! You can now release and distribute your first signed code.
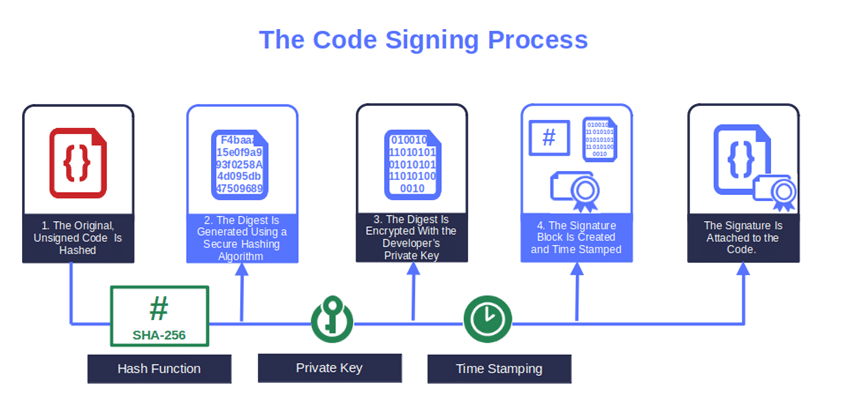
Image caption: The graphic shows how software or code is signed.
Interested in learning more about code signing and hashing? Explore its nitty-gritty:
- Check out our PowerShell code signing best practices,
- Discover the best hashing algorithm to use for encryption,
- Learn about their differences,
- Uncover how to hash a file in 60 seconds, and
- Find out how to sign an .exe or application in five simple steps.
Final Thoughts on 6 Reasons You Should Release Signed Code and Software
As a software developer or software company, providing secure and malware-free code is your responsibility. By releasing only signed code and software you’ll:
- Prove your customers that you’re a trustworthy brand,
- Make your software distribution and supply chain more secure against tampering and dangerous malware attacks, and
- Get rid of — or, at least, reduce — irritating security warnings. Thus, your users will be able to enjoy a smoother user experience and be more inclined to become loyal customers.
Want to code-sign your software like a pro? We’ve three top tips for you. Don’t forget to:
- Add a timestamp to your code signing digital signature.
- Follow best practices for code signing certificate management and keys.
- Regularly scan your codes and components for vulnerabilities.
Last but not least, don’t miss our next article to uncover how to take the security of your private keys and certificates to the next level. How? By integrating them into a single .pfx file.


