How to Generate a Self Signed Code Signing Certificate (And Why You Shouldn’t)
While it’s possible to generate and use a self signed code signing certificate, this is a practice you should avoid doing for uses outside your organization’s internal testing environment
Technically speaking, it’s possible to use self signed code signing certificates. However, doing so in public-facing applications means that the certificate won’t work for its intended purpose, which is to prove the legitimacy of your software.
Nowadays, malware attacks are common. Publicly trusted code signing certificates play an essential role in helping users know whether the software applications they download or install come from trusted sources. When these certificates are issued by trusted third parties known as certificate authorities (CAs), they contain verified organization information to let users know whether a legitimate entity published it. However, a program that isn’t signed by one of these digital certificates — such as a self signed certificate that the software’s creator generates — will prompt operating systems and browsers to warn users that the executables are is from an unverified or unknown publisher.
But what is a self signed code signing certificate? How do you create one? And why is it a good idea to only use publicly trusted code signing certificates?
What’s a Self-Signed Code Signing Certificate?
Unlike publicly trusted code signing certificates, which come from third-party certificate authorities (CAs) like Sectigo, DigiCert or Comodo, self signed code signing certificates are developed and issued by the software developers who use them. Self signed certificates have their own policies defined by software developers. Therefore, they’re not universally accepted or recognized by operating systems or major web browsers like Google Chrome or Mozilla Firefox.
In other words, self signed code signing certificates are the code signing certificates signed and vouched by you and not by any third party globally trusted certificate authority. The main issue of having a self signed code signing certificate is that browsers and machines will not have your public key within their trust store as you aren’t popular or a well-known CA, and subsequently, they may not have a reason to trust you.
But let’s say you still want to create self signed certificates for use within your organization’s internal environment. How would you go about doing so?
How to Generate a Self Signed Code Signing Certificate
The way you can generate a self signed code signing certificate is to use OpenSSL. You have a few options as to how to go about doing this, such as using Linux or PowerShell. In this case, we’ll use PowerShell’s New-SelfSignedCertificate cmdlet, which allows you to create different types of certificates for different purposes. Note: you’ll need to have administrator access.
Use the following command to generate a self signed code signing certificate using this PowerShell script:
$cert = New-SelfSignedCertificate -DNSName "www.yourdomain.com" -CertStoreLocation Cert:\CurrentUser\My -Type CodeSigningCert -Subject “Example of Your Code Signing Certificate”
Likewise, you can also add your generated self signed certificate as a trusted certificate authority for the network by using Microsoft Management Console (type mmc.exe in RUN to open). And, after that, you’ll need to copy your generated self signed code signing certificate from the Personal folder and paste it into the folder named Certificates which is under the Trusted Root Certificate Authority.
Here’s what it looks like while stored in the Personal folder:
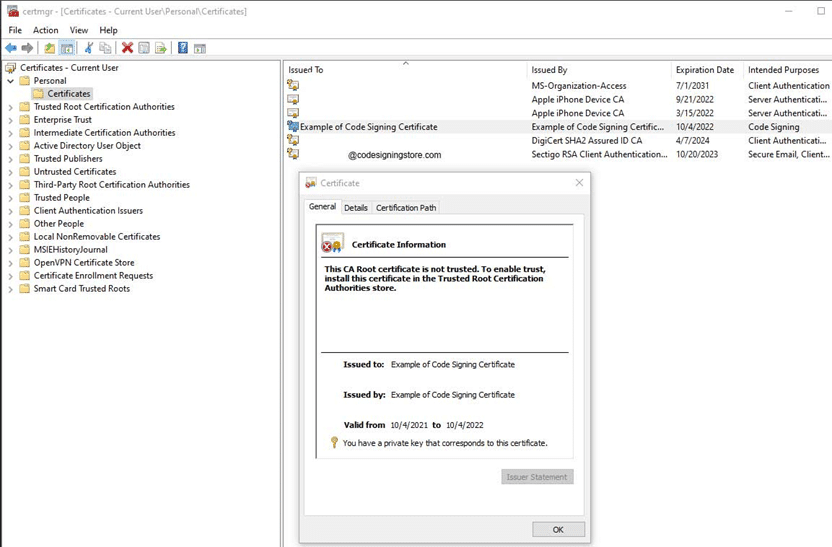
However, it’s important to note that self signed code signing certificates can be misused. For this reason, as a software developer, you should only sign your executables using publicly trusted certificates.
Here’s How It Could Go Wrong If You Use Self Signed Code Signing Certificate
Although a self signed certificate is acceptable for internal purposes (such as testing), it’ll generate issues and warning messages if you try to use it to sign software, scripts or other executables that you publish online. For instance, your users will start receiving different warning messages (like the one below) whenever they try downloading or installing the software:
No one want to see the word “unknown” associated with the publisher. Users want to know that their certificate is from a verified developer or publisher that they can trust.
Of course, if you want to get rid of these types of Windows Defender SmartScreen warnings altogether, you’d need to sign your code using an extended validation code signing certificate.
Not Signing Your Code Makes Your Software Look Dangerous
Whether you use a self signed code signing certificate or don’t sign your software or code at all, the results will be similar. When someone tries to download your software through a web browser like Google Chrome or Mozilla Firefox, it will verify that a trusted source hasn’t issued the code signing certificate. Because of that, it’ll issue a browser warning message to the user.
Such warning messages will make it appear like your software is malicious, and your users will most likely not be bothered to click and download it. As a result, your conversion will fail, and the user will leave your site.
What About Free Code Signing Certificates — Are They Available?
No, free publicly trusted code signing certificates aren’t something you can get. You must purchase them from third-party certificate authorities — like some of the ones we mentioned earlier (Sectigo and DigiCert). If you’re wondering why there’s a cost associated with these certificates, the answer is simple: code signing certificates aren’t free because they require CAs to go through a verification process before issuing them. CAs vouch for the organization’s or any individual software developer’s integrity, which is time-consuming and cannot be done free of cost.
However, it doesn’t mean that you’ll be required to pay a hefty amount. Code signing certificates from respected CAs will fit in the budget of any organization or individual. We are sure you can afford it and get your code signed without breaking the bank.
Buying a Code Signing Certificate From a Respected CA Is the Solution
Code signing certificates aren’t as costly as you may think. For instance, a Comodo code signing certificate is offered for as low as $211.46 per year if you choose to go for a valid certificate for three years. Furthermore, you can also avail yourself of additional discounts by applying coupon codes on the very same product.
Our Final Verdict on Using Self Signed Code Signing Certificates (Don’t In Most Cases)
As mentioned above, self signed certificates are useful in certain scenarios like testing purposes. In other words, you can use it if you’re using it to make them appear trusted on any targeted particular machine by deploying it to the certificate store of Windows before installing the software.
But those who’re looking to use a self signed certificate to sign a software they wish others to download onto their computers on which they don’t have any control must avoid using it. That is because, in such cases, self signed certificates are completely useless. Unlike code signing certificates from public CAs that require their users to go through a vetting process, a self signed code signing certificate doesn’t have any such process. That’s why it’s not recognized or trusted by browsers and operating systems.
All of this is to say that self signed code signing certificates aren’t going to do you any good if you’re looking to sign executables and software that you distribute to customers. Therefore, it’s wise to avoid using a self signed certificate in many cases. However, if you want to use these digital certificates, you need to ensure that their usage remains limited to testing purposes within your internal environments only.


