A 10-Minute Guide to the Secure Software Development Framework
Welcome to the era of ‘secure everything, everywhere.’ This secure software development framework in our 10-minute guide will show you how to mitigate software vulnerabilities from the beginning to end of your SDLC. Because even in 2022, insecure applications remain the main cause of data breaches
In 2021, the number of identified software vulnerabilities (i.e., holes in your defenses that bad guys can exploit) grew from around 18,000 in 2020 to more than 20,000. In the same year, the number of exploited weaknesses in the wild rose by 24%. Vulnerable points of entry can be found virtually everywhere — in the platform you choose to write your code, the libraries you use, you name it.
Cybercriminals are moving faster than ever while organizations are scrambling to find new ways to prevent the risks of attacks. In such a dangerous environment, secure code and the old good software development life cycle (SDLC) aren’t enough anymore. This is where the secure software development framework (SSDF) can help.
The National Institute of Standards and Technology’s (NIST) Secure Software Development Framework is a comprehensive list of high-level security practices that aims to address virtually all security aspects of your SDLC. This valuable framework can serve as a useful resource for helping you learn how to protect your organization and customers from the most critical SDLC vulnerabilities.
Reading it will only take you the amount of time it takes to drink a cup of coffee. So, fill in your mug and start reading.
What Is a Secure Software Development Framework?
Did you want to implement a secure software development life cycle (SSDLC) but you desisted because it was too complicated and time-consuming? Or did you feel that security in every step of your development process was harming the time taken to release the product? Stop racking your brain about it! Someone else has already put together a set of guidelines and best practices taking into account all the aspects of the software development process: the secure software development framework (SSDF).
The secure software development framework (SSDF) is a collection of high-level, consolidated best practices and recommendations that can be directly integrated throughout the secure SDLC. Created, in part, as a response to Executive Order (EO) 14028, this resource aims to help organizations ensure security is embedded in every step of their life cycles. These practices have been pulled from more than 150 position papers, including some existing NIST guidelines, as well as other secure software development resources like
- Building Security in Maturity Model (BSIMM) framework (more on that later),
- Software Assurance Maturity Model (SAMM),
- Open Web Application Security Project (OWASP), and
- OWASP Application Security Verification Standard (ASVS).
What is it, exactly? It’s a flexible framework that focuses on secure software creation and can be easily adapted to any kind of organization.
Why should you bother with it? Let’s find it out.
Why Should I Use a Framework for Software Development?
Are you aiming to develop applications that are secure against the latest threats and vulnerabilities? Then you do need a software development framework that:
- Helps you reduce the number of vulnerabilities in your released software. Found a vulnerability? The framework’s best practices will guide you on how to find and address the root causes of the identified flaw. This will enable you to mitigate the issue and avoid the same situation happening again in the future.
- Can be used by any organization. Thinking that it won’t fit within your business? Wrong. Thanks to its flexibility, the framework can be integrated into virtually any kind of business software development workflow. Startups, SMBs, big corporations, you name it — the size and complexity don’t matter.
- Works with any SDLC. Are you developing mobile software applications or applications for the internet of things (IoT)? Are you using Java or PHP? Is your SDLC unique and complicated? No problem. The secure software development framework is like a black t-shirt: it goes with virtually anything.
- Helps organizations establish a continuous improvement process. How? By providing you a good reason to document your secure software development best practices, and defining new security guidelines to implement.
- Teaches your teams to manage security checks in a more structured and effective way. SSDLC addresses the basics of security but also takes it a step further. This framework helps guide your teams in creating processes and checklists that’ll help them easily bake security into every step of the cycle. Foolproof. For example, it covers everything from knowing which lists of secure libraries to use to how to handle security flaws and when to reuse code. Because the devil is in the details.
- Facilitates the move from a classic devops process to a more secure (and modern) one. Are you looking to implement devsecops or secdevops within your organization? This framework will be a precious ally in your transition to a more secure software development model.
Among all frameworks available (more on that toward the end of this article), our guide will focus on providing an overview of the one recently published by NIST. Why? Because it’s:
- Clear and concise,
- Focuses on the entire life cycle of software development, and
- Was recently updated (a few months ago at the time this article was written).
Still sipping your coffee? Good. Grab a cookie and let’s start exploring NIST SSDF in more detail.
NIST Secure Software Development Framework
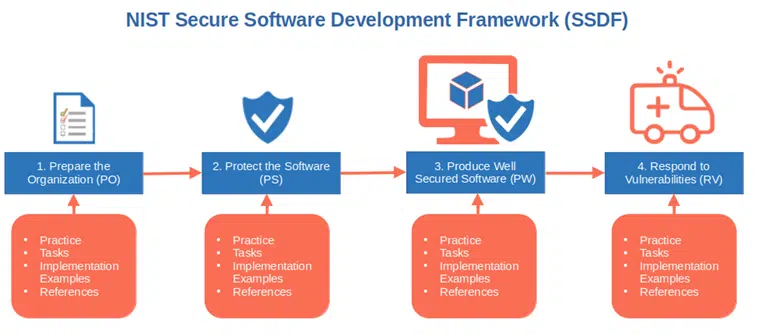
The secure software development framework (SSDF) is organized into four practice groups (more on that in a minute). Each group includes the following four points with ready-made examples and suggestions (told you, you didn’t need to rack your brain!)
1. Practice. These are outcome-based elements that should answer the following questions:
- What are our goals?
- Why are they beneficial?
- How are we going to reach them?
- Who is going to be responsible for what? (For example: ensure the users can verify that the code is original and hasn’t been tampered with.)
2. Tasks. These actions or activities must be done to help you fulfill each practice. If we take the example above, it could be something along the line of making the information needed for the verification available to the users.
3. Implementation Example Notes. This information boils down to answering the question: How can it be carried out? Think in terms of tools, policies, processes, and all that good stuff. Here, you should have multiple answers and describe all implementation options available. For example, code sign all your software, and upload your codes on a website using a secure, encrypted connection (thanks to a website security certificate). Any tool, process, or method should be listed to give you an overview of all feasible options.
4. Reference. Where are the implementation example processes documented? In this section, you’ll add links to where the documents are stored or what the files are called. The key is that everyone on the team is aware of where/how to find them.
Now, let’s have a look at the four groups of the secure software development framework.
| Practice Groups | Implementation Examples |
|---|---|
| 1. Prepare the Organization (PO) |
|
| 2. Protect the Software (PS) |
|
| 3. Produce Well Secured Software (PW) |
|
| 4. Respond to Vulnerabilities (RV) |
|
1. Prepare the Organization (PO)
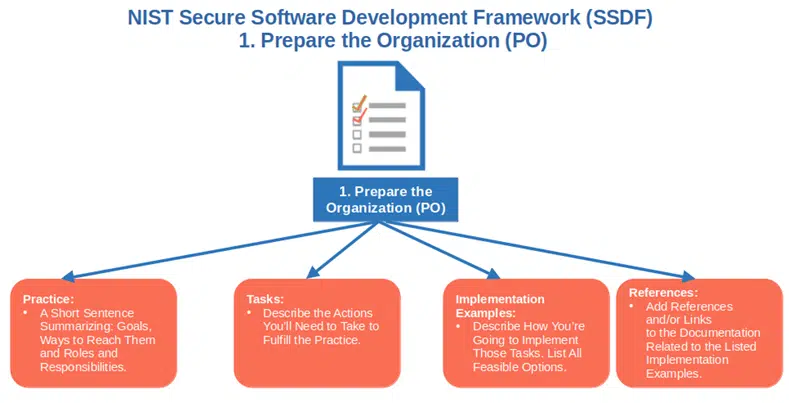
Here is where it all begins with NIST’s secure software development framework. This is the first step that builds the foundation of your organization’s SSDLC. It’s where you ensure that all teams, processes, and technology are ready to include security in every step of your development process by:
1. Defining security requirements for software development. Requirements must be known by everyone involved in your secure SDLC, including third-party vendors. Your requirements list should be updated every time the code is developed and/or new features are added. Here’s a quick example to add to your implementation column: Define policies to secure every single step of the SSDLC and keep it up to date. This will also include open-source and third-party software components used for the development.
2. Delineating roles and responsibilities. Define the people responsible for the security requirements and ensure they’re ready to act upon them. Don’t forget to include third-party vendors participating in the SSDLC. A good implementation example could be to integrate security roles and responsibilities into the development teams.
3. Implementing supporting toolchains. Increase speed and reduce manual effort by introducing automation at every level of the organization. How? Automating your toolchain management and orchestration is one potential idea.
4. Outlining and using criteria for security checks throughout the SSDLC. In other words, find a way to measure if and how secure your code is. For example, you could decide to define and use key performance indicators (KPIs) as metrics.
5. Enforcing and maintaining a secure development environment. All components must be protected from internal and external threats. You could do that by using a strong hashing algorithm and storing only password hashes instead of plain text passwords.
2. Protect the Software (PS)
Now that the basics are down and dusted:
- How are releases going to be managed?
- How are you going to protect the integrity of your code?
With organizations being hit by multiple attackers simultaneously or within a short time, these are some of the key questions that every software development company should ask itself. This section is going to help you find the right answers.
1. Protect all forms of code from unauthorized access and tampering. Prevent unauthorized modifications to your code. This will keep at bay errors caused by unintentional code changes. On top of that, it’ll make things more difficult for a malicious third party trying to add infected code to your software. How can you do that? Signing and time stamping your code is a great way to protect your executables, while using strong cryptographic hashes will guarantee the integrity of your files.
2. Provide a mechanism for verifying software release integrity. How can you make sure that your code hasn’t been modified upon release (e.g., a malicious string has been added)? Using a PKI-based code signing certificate issued by a trusted certificate authority (CA) will ensure that your users’ operating systems and browsers will immediately confirm the validity of the signature. Checksums are also a good solution to enable users to instantly verify the integrity of the software by comparing hashes.
3. Archive and protect each software release. A recent three-year study showed that in 2021, an astonishing 72% of identified vulnerabilities were tied to application code-related flaws. Keeping an archive of all your code releases will facilitate identifying and fixing flaws or bugs even when your code is in production. Protect your archive by signing the data and limiting access with read-only permissions though. Attackers can be little buggers: they’re persistent and are virtually everywhere.
3. Produce Well Secured Software (PW)
This is the largest section of the NIST secure software development framework. It focuses on how to write code securely and includes nine practices. Here are five examples of such practices:
1. Design software to meet security requirements and mitigate risks. In other words, make your code secure by design. Your entire process will become much more efficient and of course, secure. Running security assessments is one way to implement it.
2. Review the software design to ensure it meets security requirements. In the beginning, you made a list of security requirements. Now, it’s time to check that your design is in line with the items on your list. A good example of implementation is to ensure that the software designer immediately fixes any failure.
3. Reuse software instead of duplicating functionalities. Did you write good, high-quality code? Don’t throw it away like an old shoe — reuse it. This approach will help you reduce the risks of introducing new vulnerabilities. Did you know that you can re-use code from third-party software, too? Yup. Store your application’s software bill of materials (SBOM) so that when you reuse one of those components, you can also update it.
4. Follow secure coding practices. Adhering to secure coding practices enables you to minimize the risks of attacks and vulnerabilities. For example, adopting the principle of least privilege and denying access by default are a couple of examples.
5. Review and analyze human readable codes to find security flaws. Isn’t it better to address as many vulnerabilities as possible before releasing your code? Manual code reviews and peer reviews can be great ways to spot backdoors or code errors. Don’t forget to document all discussions and feedback for later references.
Interested in the complete list, including more implementation and task examples? Download the latest version of the NIST Secure Software Development Framework.
4. Respond to Vulnerabilities (RV)
Did you know that following a study made by Cisco, 42% of security experts consider customer-facing web applications the ones with the highest vulnerabilities? How can you deal with those?
1. Look for vulnerabilities on an ongoing basis. The sooner you find them, the less time you give the attackers to find a way to breach your system. Sign up for security mailing lists and newsletters like CISA’s weekly vulnerabilities bulletin, RSS feeds, and catalog updates. It’s an excellent way to stay up to date on the latest vulnerabilities and exploits.
2. Assess, prioritize and remediate vulnerabilities. It’ll enable you to fix them efficiently by first addressing the most critical ones. What if a permanent fix isn’t available yet? Don’t give up. Work on a temporary patch and implement it as soon as possible.
3. Look for the root cause of each identified security flaw. Do you want to avoid a similar issue happening again? Find the vulnerability’s root cause and ensure your automated tests will be able to catch it in the future. Lessons-learned sessions are unbeatable tools to help you find out the exact cause of a vulnerability.
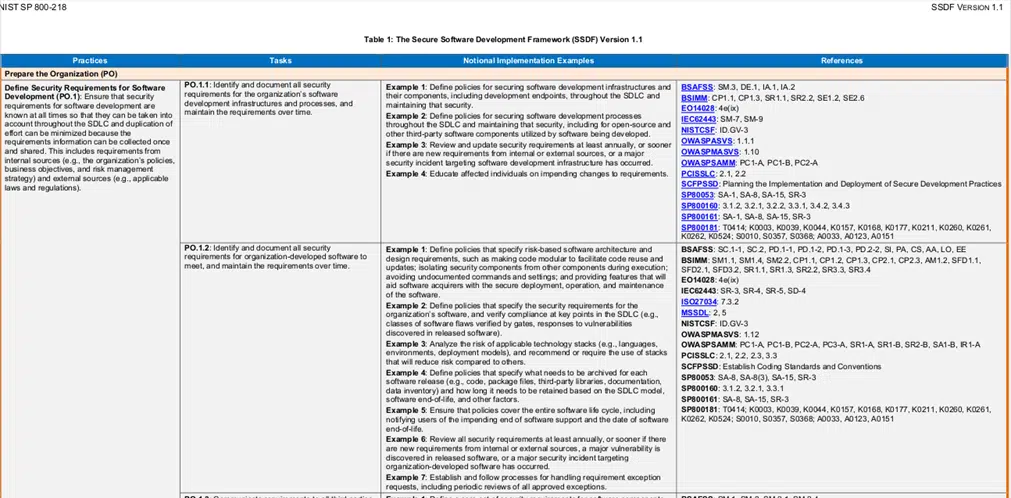
Have you run out of coffee? No worries, we’ve reached the end of our guide to the secure software development framework. Do you think your organization could benefit from implementing this framework? What are you waiting for? Back to work! Download the NIST framework right now. Check the additional practices and examples like the ones in the screenshot below and start implementing them.
Other Secure Software Development Frameworks
Before you go, though, here are a couple of other software development frameworks and resources to check out:
- The BSA Framework for Secure Software. Similar to the NIST framework, it’s developed by BSA | The Software Alliance, and it also focuses on security and threats. It’ll help you bake security into your SDLC process and ensure that your application will include the security features you need.
- The Building Security in Maturity Model (BSIMM). Comprising a total of 12 practices, this framework is divided into four groups (called domains): 1) governance, 2) intelligence, 3) SSDL touchpoints, and 4) deployment. It’s a resource that incorporates data from 122 assessments from nine different industries and it helps you analyze and improve the security of your SDLC. Its purpose is to help you develop an effective software security initiative.
What are the key differences between NIST’s SSDF and these frameworks?
- The SSDF tells you what you should improve and why, while also providing a few examples of how to implement those improvements. The others are more focused on how to apply specific security practices in their SDCL.
- The SSDF applies to any kind of organization and situation, while the others are focusing on specific industries including:
- Financial services,
- Software,
- Healthcare,
- Cloud,
- Internet of things (IoT),
- Fintech,
- Independent software vendors (ISVs),
- Insurance, and
- Retail.
Final Thoughts on a 10 Minute Guide to the Secure Software Development Framework
Modern applications require modern development processes that’ll keep organizations’ SDLCs secure without impacting the speed of their releases. Adopting the secure software development framework will enable you to:
- Securely sign your software,
- Use CA-issued certificates,
- Create a software bill of materials.
These are just a few examples suggested by NIST that you can implement to successfully integrate SSDF practices into your SDLC. Don’t risk losing customers’ trust or jeopardizing your organization’s revenue and reputation. Start producing secure and resilient software by utilizing what you’ve learned today.


