An Error Occurred While Signing: SignTool.exe Not Found
Are you trying to sign your code in Visual Studio and the message ‘An error occurred while signing: SignTool.exe not found’ keeps popping up? Discover how to fix it in a blink of an eye, without compromising the security of your software
In 2022, SonicWall identified 6.3 trillion intrusion attempts and 112.3 million examples of IoT malware. Respectively, these figures represent 19% and 87% more than in 2021.
In such a dangerous environment, being unable to sign your codes during the software development life cycle (SDLC) or before going into production just because of a SignTool error, would be suicidal for any business, big or small.
Stop gambling with the security of your software and your customers’ trust in your brand. In our previous article, you’ve learned how to fix the cryptic Visual Studio error: ‘‘SignTool error: no certificates were found that met all the given criteria‘ This time, we’ll show you the best solution that’ll save the day when another common Visual Studio error pops up: ‘An error occurred while signing: SignTool.exe not found.’ Ready to crush this? Let’s go!
‘An Error Occurred While Signing: SignTool.exe Not Found’ — How Can I Fix It?
Don’t you just hate it when you start the day all pumped up, ready to finish a project, and then, you get stuck on an error message like ‘An error occurred while signing: SignTool.exe not found’? I sure do, and it’s something that happened to me recently. So, how did I fix it?
I ran a search on the internet and found out that I had two options. Well, one usable option, to be honest — the second was more of a workaround than a safe solution to employ. The second option basically consisted in unchecking the ClickOnce sign manifests, which is something I wasn’t prepared to do (more on why that is in a few minutes).
Anyway, let’s walk through how I fixed the problem once and for all, and finally managed to sign my test project.
The Solution: Manually Install or Update ClickOnce
Before we start, be aware that we’ve used Visual Studio 2022 for this demonstration. If you’re using an older version of VS, you may have to follow different steps (i.e., update your ClickOnce Publishing Tools).
To get rid of the error message ‘An error occurred while signing SignTool.exe not found’:
1. Open the Visual Studio Installer tool.
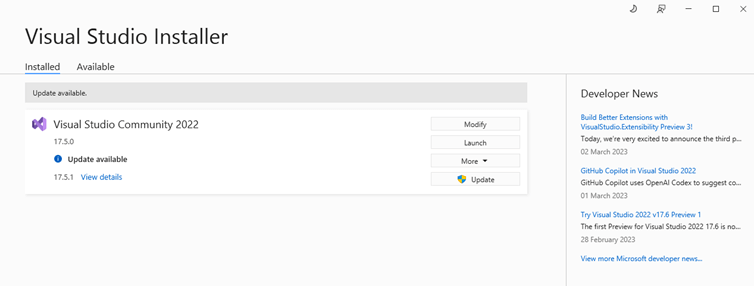
2. Click on the Modify button near the Visual Studio version you’re using to create your codes. Of course, you can always check to see if you’re using the current version or if you need to apply an update first. If you have an update available, apply that first to see if it fixes the issue. If not, use the modify option we mentioned and continue with the process.
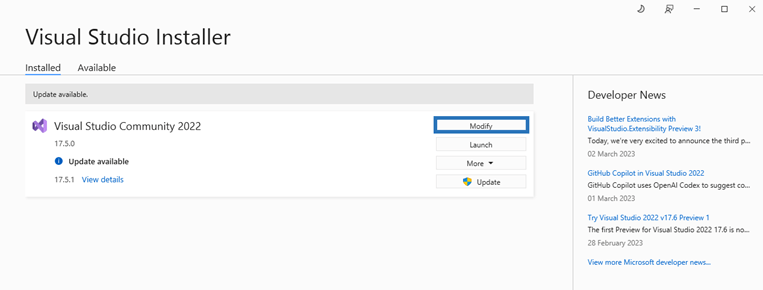
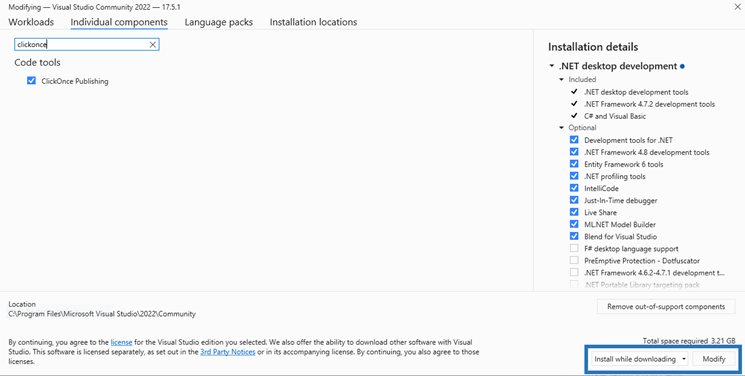
3. A pop-up window will come up. Choose the Individual components tab.
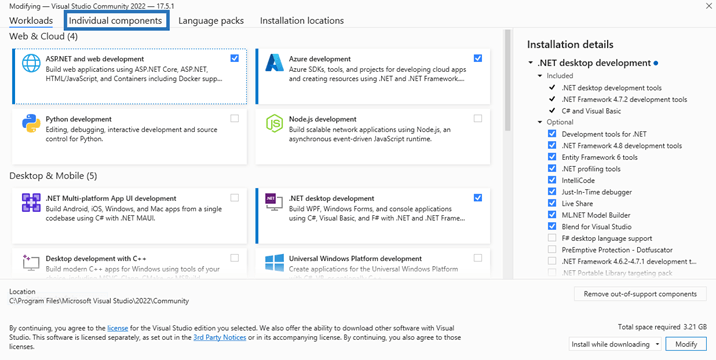
4. Search for ClickOnce Publishing and install it.
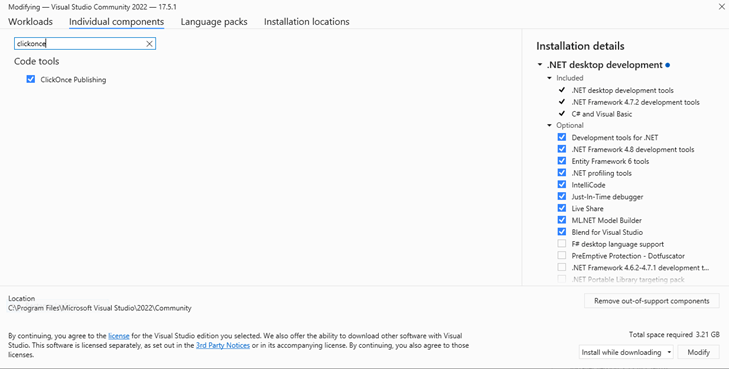
5. Ensure the option Install while downloading is selected in the drop-down menu at the bottom of the screen and select on Modify. The installation of ClickOnce will start.
Mission accomplished! Now you can get the most out of your Visual Studio platform and secure your codes in just a few clicks.
Right, I know that some of you may still be wondering why I didn’t go with the workaround we mentioned at the beginning. It probably would have saved me even more time, but would have been really the right choice to make? In most cases, no — here’s why…
Why You Shouldn’t Uncheck the ‘Sign the ClickOnce Manifests’ Option as a Workaround
If you check a few figures from the Malwarebytes 2023 State of Malware report, you’ll quickly notice how challenging 2022 has been for organizations of all sizes, in terms of cybersecurity.
- 71% of organizations worldwide were victims of ransomware,
- LockBit was responsible for more than three times more attacks than the second most active ransomware.
The highest largest LockBit ransom request reached a jaw-dropping $50 million.
Is 2023 looking any better? No way, Jose’. At least, not so far based on the attacks seen so far… for example:
- The Royal Mail LockBit ransomware attack that completely paralyzed the United Kingdom’s largest mail organization’s international shipping services in January 2023, or
- The six American schools that were recently attacked by another ransomware group called the Vice Society.
What does all this have to do with the workaround that’ll help you get rid of the error ‘An error occurred while signing SignTool.exe not found’? Let’s find it out.
Deselecting ClickOnce Manifest So May Result in Unintended Consequences
When you choose to uncheck the Sign the ClickOnce manifests feature, what you’re really doing is deactivating SignTool.exe. By doing so, Visual Studio won’t check anymore to see if SignTool is available and, as a result, it won’t give you the error message. Fantastic, right? Not really, as it also means you won’t be able to sign your executable manifests anymore.
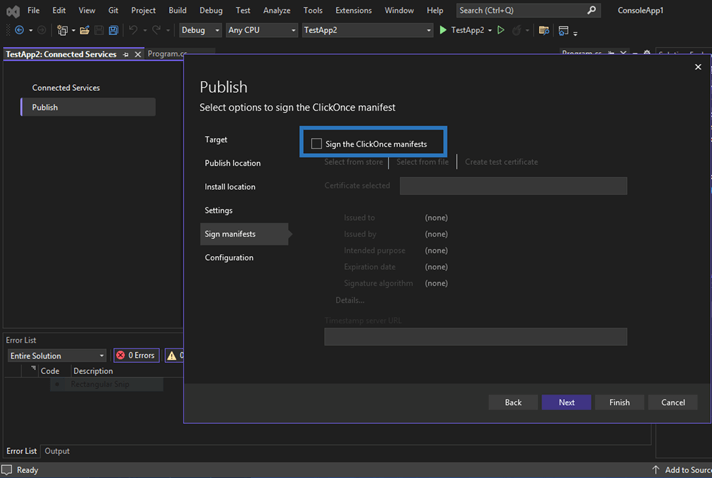
Sure, this workaround is as quick as ripping off a band-aid and faster than installing the missing feature. Some websites are even suggesting it as a good solution. But what does this approach mean for the security of your organization and users? Are you prepared to ignore it and face the potential consequences?
In general, there are a couple of important reasons to digitally sign your executables and manifests. Code signing your apps and other .exe files using SignTool in Visual Studio will enable you to:
- Confirm your users that the software has really been created by you, and
- Guarantee that the code hasn’t been altered since its signature.
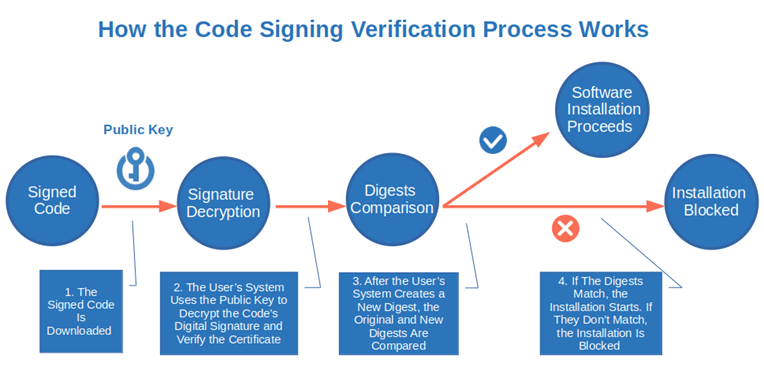
How? In a nutshell, before publishing his application, the developer uses a code-signing certificate issued by a trusted certificate authority (CA) to digitally sign the code with its private key. When a user downloads the code, its operating system will use a public key to decrypt the signature and verify the integrity and authenticity of the code. If something is wrong (e.g., the hash used by the developer to sign the code doesn’t match the hash created by the user’s system), the download/installation will halt and a warning will display.
Do you create ClickOnce applications (i.e., self-contained Windows apps that can be installed by clicking on the .application file) and want to digitally sign them? You can use ClickOnce to digitally sign your deployment files (i.e., .application files) and manifest files. Once signed, your users will be able to verify your identity and the integrity of the application as well.
Want to explore the code signing process in detail? Check our article that explores what code signing is and how it’s beneficial.
Now, let’s say you decided to try your luck, deactivate ClickOnce, and publish your brand-new app without adding its digital signature. This is what could happen.
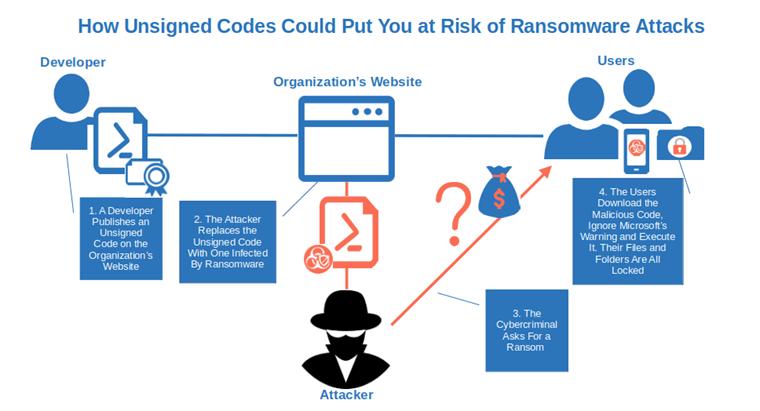
Unsigned Application or Code Can Be Replaced By a Malicious Asset Posing As Yours
23% of threats identified by McAfee in 2022 were malicious applications posing as legit productivity apps. Your users and customers may download one of those apps thinking that it’s coming from you and it’s malware free.
How so? As the app is unsigned the users won’t have any way to verify if what they downloaded has really been published by you. They also won’t be able to check if the code has been modified by an unauthorized third party.
Thus, as they’ll give the app (and the attacker) all sorts of permissions (e.g., contacts, location, microphone, and settings) the hacker will have free access to their devices and to all the information in them.
Attackers Get Access to Easy Pathways to Compromise Systems and Devices
If the infected smartphone or laptop is also used for work, things will get even worse. The cybercriminal will have free access to the organization’s network, systems, and sensitive information, too. This serves as a gold mine for them and a lot of trouble for you.
The infection could spread like wildfire to your customers, partners, and suppliers. Can you imagine the extent of the financial and reputational damage this could cause? Your customers’ stolen passwords could have cost you, in 2022, an average of $4.50 million. in data breach-related costs and take an average of 327 days to identify and contain.
On top of that, you’ll have to add the costs of any potential legal action, privacy, and security regulation fines (e.g., the European Union’s General Data Protection Regulation [GDPR] and the U.S.’s California Consumer Privacy Act [CCPA]).
These insider threats have become increasingly common. A report by Gurucul shows that in 2022 60% of surveyed organizations were victims of such attacks, while 8% suffered more than 20 insider attacks in just one year. You don’t want to be next, right?
Your Organization, Partners, or Customers Could Become the Next LockBit Victim on the Next Ransomware Report
At the beginning of this chapter, we saw how dangerous LockBit and ransomware-related attacks have become. Recovering from a ransomware attack can take an organization lot of time and money.
In fact, in the first five months of 2022, the average ransomware payment seen by Palo Alto Network analysts nearly reached the $1 million mark. Have you been hit by ransomware but managed to fully recover your data without paying the ransom like 78% of organizations surveyed by Cybereason that chose not to pay?
Well done. But just remember that you may not be so lucky next time. Furthermore, you still have to face all of the costs of remediation, downtime, legal expenses — you name it. And, unfortunately, these mounting costs can be more than enough to put companies out of business in some cases.
Want to explore further how you can prepare and recover from malware? The National Institute of Standards and Technology has a plethora of resources for every taste and use case.
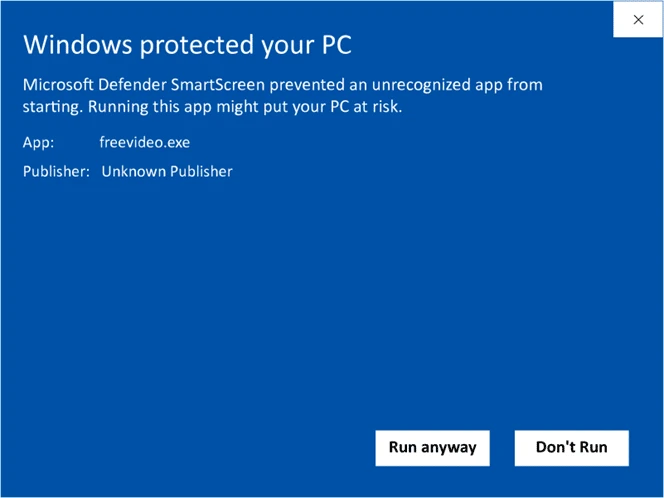
Your Users Will Get Security Warnings When Installing/Downloading Your App
Even if you’re lucky enough to keep your app out there untouched and malware free, your users’ operating systems and browsers won’t trust it. Why? Because it’s unsigned. Thus, the major browser will flag it as dangerous, while operating systems like Microsoft will show a pop-up warning.
Do you really want your users and customers to visualize a big, fat warning message stating that, if installed, your application may damage their computer? I don’t think so. Your reputation may suffer, and the number of downloads (together with revenue) may decrease. It would be a bit like giving away money to your competitors.
Wrapping Up on the Importance of Signing Your Applications
Did you answer no to at least one of the questions above? Welcome to the cybersecurity-conscious developers’ club. And these were just a few examples. Discover other possible dangerous consequences of publishing unsigned software in our article ‘What Happens When You Use Unsigned Code or Software’.
Convinced? From now on refuse to help your users, organization, and customers to become infected with malware. Opt for the real solution we’ve explored in this article and manually install ClickOnce to digitally sign your manifests and use SignTool to digitally sign your executables.
This simple action will:
- Help you increase the number of downloads.
- Prove your customers and users the authenticity and integrity of your code.
- Improve your organization’s reputation and yours, as a developer too.
- Ensure your software and updates are trusted by all major browsers and operating systems.
Aren’t the few minutes spent installing this feature and choosing the right solution well worth it?
Final Thoughts on An Error Occurred While Signing: SignTool.exe Not Found
When you work as a software developer, whether you like it or not, error messages become part of your day-to-day job. And even if it can be frustrating sometimes, it’s something you can’t escape from.
But, when life gives you lemons, you just need to find the right solution to make delicious lemonade. Today, you did just that. You’ve learned:
- How to fix the Visual Studio error ‘An error occurred while signing: SignTool.exe not found’ without putting your development project, customers, and organization at risk of cyber attacks, and
- What not to do to avoid creating big cyber security risks and causing reputational harm to your organization and those around you — from customers to suppliers.
Your customers deserve the most secure products you can provide. Interested in further enhancing the security of your software and web applications? We’ve plenty of tips for you.
- Discover how to create a secure web application.
- Explore and use our web application security checklist.
- Check our ultimate programming best practices guide.
- Familiarize yourself with our developer’s essential software security checklist.


