A Developer’s Essential Software Security Checklist
Local file inclusion (LFI), structured query language injection (SQLi), and cross-site scripting (XSS) — these three attack vectors were used in the majority of the 9+ billion web applications and API attacks in the first half of 2022. Prevent cybersecurity incidents with our one-stop software security checklist to help keep your data and apps safe
Following the Chinese calendar, 2021 was the Year of the Ox. From a cybersecurity perspective, it’ll be remembered as the year of web application attacks, as they increased by 88% compared to 2020.
Does 2022’s threat landscape look any better? With 2.8 billion malware attacks recorded within the first six months, it doesn’t seem like it. Organizations are trying to “shift left” (i.e., putting security first) as fast as they can. But security remains a second thought for 86% of developers, who are already overwhelmed by tasks and tight deadlines. As a result, 48% of them knowingly release vulnerable codes.
What’s the solution? Working harder? Nope. Working smarter. Discover how our five-point essential software security checklist can help you enhance the security of the software you’re developing without increasing your work time or workload.
Why You Need a Software Security Checklist
Software development can be an exciting job. It enables you to create awesome applications with brilliant features that millions of people or companies worldwide will use. However, building secure applications is another matter. It’s a complex process that can quickly become overwhelming due to the many steps involved, dependencies, and vulnerabilities.
Right, a checklist can’t make miracles. But covering the most critical steps can make your life much easier and help you:
- Save time and money. Mistakes happen and software vulnerabilities are growing by the day. A checklist will reduce the potential for errors and ensure known vulnerabilities will be addressed before release. It’ll prevent you from spending time fixing bugs in production or at the last minute. Thus, it’ll minimize the risk of security incidents and related costs. Prevention is always better than a cure.
- Protect your reputation and enhance customers’ trust. Protect your customers and organization from attacks, and you’ll gain in reputation and customers’ trust. Data breaches are a big deal and consumers are fighting back against companies that don’t protect their data with their wallets. 89% of Americans over age 55 wouldn’t buy a thing from a brand they don’t trust (nor should they).
- Ensure security and privacy regulations compliance. The European Union’s (EU) General Data Protection Regulation (GDPR), the U.S.’s California Consumer Privacy Act (CCPA), the Payment Industry Card Data Security Standard (PCI DSS), you name it. There are so many regulations that it’s easier to forget one than remember them all. A checklist will ensure that nothing is forgotten and everything necessary is completed before release.
- Increase productivity by guaranteeing a smooth and secure development process. Software development is a team effort. A checklist will ensure project consistency by explicitly reminding the whole team of the minimum necessary steps to follow to produce a secure, high-quality application.
In a few words, a software security checklist can help development teams get done what they need to get done with minimal effort and without slowing down. Are you ready to free up your memory and stop having to remember every little thing? Let’s go!
5 Essential Software Security Boxes to Check Off to Build Secure Software
Yes, I admit it; I’m a checklist freak. I use them everywhere. When I sit at my desk in the morning, my checklist of the day is the first thing I look at. Eight hours later, I wrap up for the evening, and it’s the last thing I check.
Why? Checklists are practical, straight to the point, and easy to use. You have no idea how many times they saved my neck, above all when I was working on complex projects as an application security engineer.
The list below is based on that experience. It addresses some of the most critical issues I’ve encountered because, as I’ve learned, experience is the best teacher. (Hint: We’ve summarized the checklist in the table below so that you can print it out and have it at hand when building your next app.)
| Developer’s Essential Software Security Checklist | |
|---|---|
| 1. Check Your Code For Vulnerabilities |
|
| 2. Implement Encryption to Secure Data In Transit and At Rest |
|
| 3. Implement Strong Access Management Through Authentication and Authorization |
|
| 4. Log Relevant Data, But Don’t Store Sensitive Data In Your Code |
|
| 5. Secure Web Apps and Software Applications With Digital Certificates |
|
1. Check Your Code For Vulnerabilities
This is probably the most fundamental part of secure software development. Skip it and you’re done. Between open-source software, third-party components, and libraries, it’s easier to introduce even more vulnerabilities than fix those already identified. That’s also the reason why in 2021, 30% of organizations were struggling to keep pace with the volume of new vulnerabilities announced.
Nevertheless, no application should be released without checking and addressing its flaws. Not sure how can you do that?
- Check your code against the latest OWASP top 10 web application vulnerabilities list. This should be done regularly throughout the whole secure software development life cycle. Are you using Microsoft’s .NET development platform? Don’t miss the OWASP .NET security cheat sheet.
- Use static code analysis tools (SCA). Tools like SonarQube or Snyk Open Source will check your code and all your dependencies.
- Don’t forget to subscribe to vulnerability bulletins. This will help you always be up-to-date and know what to look for. There are many around, like MITRE’s CVE newsletter and the National Vulnerability Database’s (NVD) feeds.
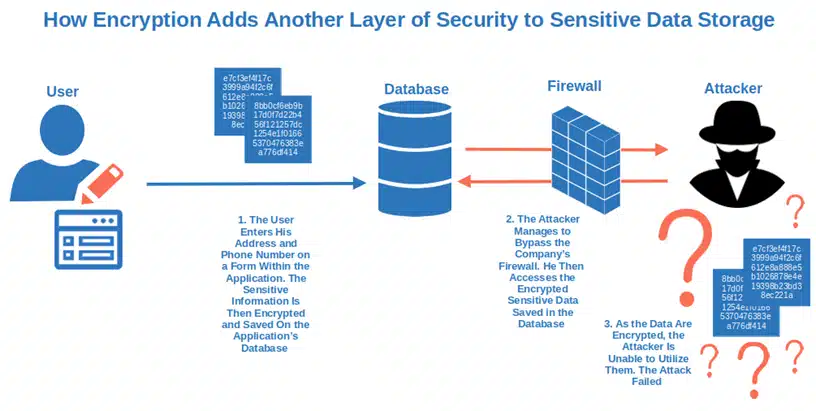
2. Implement Encryption to Secure Data In Transit and At Rest
44% of participants in a study held by Cybersecurity Insiders and Beyond Security by HelpSystems consider data protection one of their bigger application security concerns. And rightly so if you consider that IBM reports the average cost of a data breach reached $4.35 million in 2022.
Encryption implemented at all levels will guarantee you optimal protection:
- Use HTTPS, and website security certificates to encrypt internet communication and transactions. They’ll shield your application data in transit from attacks like man-in-the-middle and ensure safe communication. How? Using the secure sockets layer/ transport layer security (SSL/TLS) protocol 1.2 or 1.3, both based on:
- Symmetric (i.e., the same key is used for encryption and decryption), and
- Asymmetric encryption (i.e., the public key is used for encryption and the private key for decryption).
- Utilize strong encryption as much as you can. It’ll help you secure sensitive data (including access tokens, and email addresses) by scrambling them into a gibberish alphanumeric string, no matter where they’re stored (e.g., databases or files). Ensure your backups are also encrypted (or, at least, password protected).
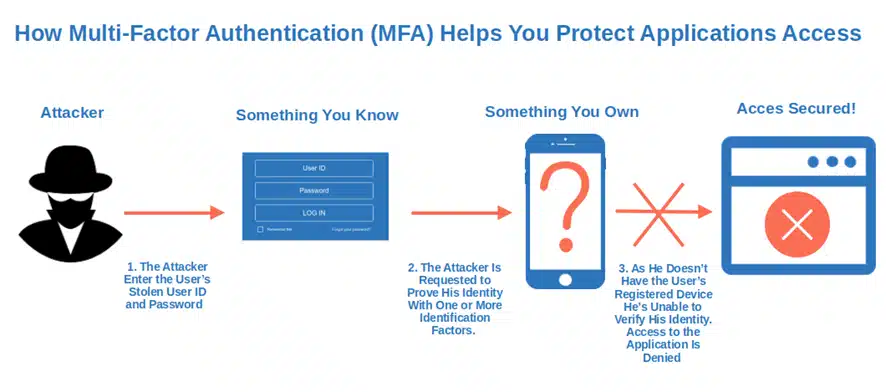
3. Implement Strong Access Management Through Authentication and Authorization
In 2021, more than 80% of login attempts related to industries like e-commerce, finance, and entertainment Auth0 registered were credential-stuffing attacks. In this type of attack, the cybercriminal attempts to access a service or application by leveraging lists of stolen or leaked credentials.
What can you do? As an old saying goes, you can’t control the wind, but you can adjust your sails:
- Enforce multi-factor authentication (MFA). The time you could rely on usernames and passwords alone is long gone. Add another layer of security by requesting two or more sets of identification factors to make your application login hacker resistant. You can even opt for location-based MFA using geolocation data to allow access only from specific locations/IPs or, adaptive MFA where MFA is triggered only when there is a risk.
- Use passwordless authentication as an alternative. Instead of having users rely on traditional passwords, you can bypass them altogether using PKI-based client authentication certificates. This entails authenticating by using a digital certificate installed on your device rather than typing in a password that could be stolen or receiving an SMS-based text message that could be intercepted.
- Strictly regulate access authorization. In other words, use OAuth 2 or the OpenID Connect protocol to give users access to necessary functions and resources (i.e., the principle of least privilege).
4. Log Relevant Data, But Don’t Store Sensitive Data in Your Code
In the first half of 2022, Trend Micro blocked 63 billion threats. With malware on the rise, event logging is another key item that should be included in every application.
- Log errors, suspicious activities, and code changes. ScienceLogic, Site24x7. There are enough tools available on the market that’ll help you log everything you need to monitor your application and manage security events. Want to make sure you’ll know when an app has been modified? Use tamper detection tools as another layer of security. Check out those available on GitHub.
- Don’t save sensitive data or personal information in your code. I know, hardcoding passwords and usernames during development can be handy. Sometimes, there are so many credentials to remember that it becomes overwhelming. But embedding or storing credentials in your code is a no-go. They’re easy to hack and easy to forget to delete before release.
5. Secure Web Apps & Software Applications With Digital Certificates
As we mentioned earlier, you can use an SSL/TSL certificate to secure website connections. But did you know that this works for web apps as well? Yes, SSL/TLS certificates also secure the connections between your customers and your web app(s) that they’re connecting to using an SSL/TLS certificate.
This approach allows you to insert your digital identity and helps to protect your data so no one can mess with its integrity in transit.
Securing Software Applications
For software apps, code signing it’s easy and can make a big difference in your battle against malware. All you need is a code signing certificate (a standard or an extended validation one) issued by a trusted certificate authority (CA).
Code-signed software will:
- Assert your identity,
- Enable your customers to verify the integrity of the application before installing it, and as a result
- Protect your users and your organization from malware.
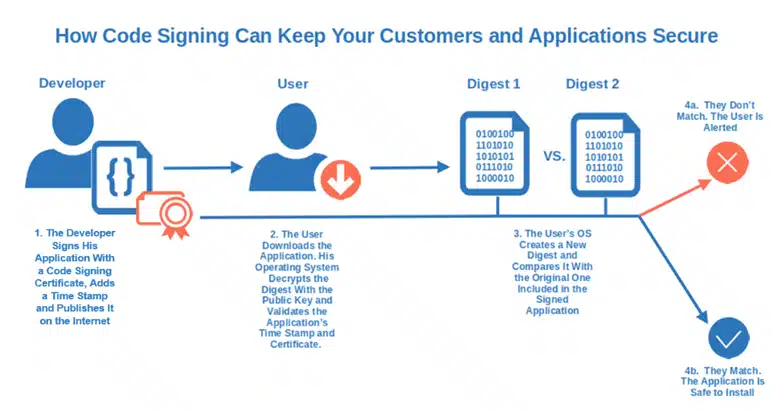
Thinking of using a self-signed certificate? Dangerous idea. While it can be used for internal testing, it’s an absolute no-go for public applications. Why don’t you add a time stamp to your code signing? It’ll ensure your signature will remain valid and your code secure, even after your code signing certificate is expired.
That’s it! Our five points, essential software security checklist. Why don’t you give it a try next time you develop your new application? Be sure to also check out our Ultimate Programming Best Practices Guide and our list of the 10 Application Security Best Practices You Should Have Under Your Belt.
Final Thoughts on A Developer’s Essential Software Security Checklist
Software security is a journey. This checklist marks the beginning of your adventure. It won’t fix all your security issues at once, but it’s a good base to start with. It includes all the essential boxes you’ll have to tick to create reasonably secure software and keep the bad guys away.
Use code signing certificates, encrypt data and communications, implement secure authentication, and stay up to date with vulnerabilities. There you go. You’re already heading in the right direction.
Are you ready to start your odyssey and create safer applications? Grab your checklist and start your new, more secure development journey!


