How to Create a Secure Web App (A Look at How to Secure Web Applications)
In July 2022, ethical hackers identified 648 vulnerabilities in the U.S. Department of Defense’s (DoD) systems during a 7-day bug bounty challenge. Would your web app pass the test? Discover 8 cutting-edge best practices that’ll help you develop secure web apps, minimizing the risk of vulnerabilities and data breaches
The 2022 Verizon Data Breach Investigation Report confirmed web applications as the top attack vector among more than 18,000 security incidents analyzed. Fast forward to mid-2022, and cyber attacks on applications keep growing. In Australia, for example, attacks increased a whopping 81% in just 12 months.
Is securing web applications one of your primary concerns, just like it is for 70% of organizations interviewed by Enso security? Are you building a new web app and want to ensure it’ll be as secure as a fortress, but you need to know where to start? Did you try to implement some secure web app development best practices, but you weren’t happy with the results?
Look no further. Discover how to secure your web applications from all angles. Learn top-notch best practices that’ll help you:
- Reduce the risks of attacks, and
- Ensure that you’re always prepared for the next threats.
Because even if 100%-secure web apps don’t exist, there’s always something you can do to make your web application security game as good as it can be.
What Is Web Application Security? An Overview of Secure Web App Development
Have you ever heard about the Open web application security project (OWASP) Top 10? It’s a list of the 10 most critical web application risk categories and defense techniques suggestions. It’s based on feedback from security experts around the globe, analytics, and data from real-life applications.
Web application security (i.e., web appsec) includes all the processes, strategies, and practices that can help you protect your websites, applications, and APIs from those threats and all other attacks exploiting code’s vulnerabilities. Its goal?
- Ensure your application runs smoothly, even when under attack.
- Protect it from threats.
- Safeguard your organization from data breaches and minimize losses.
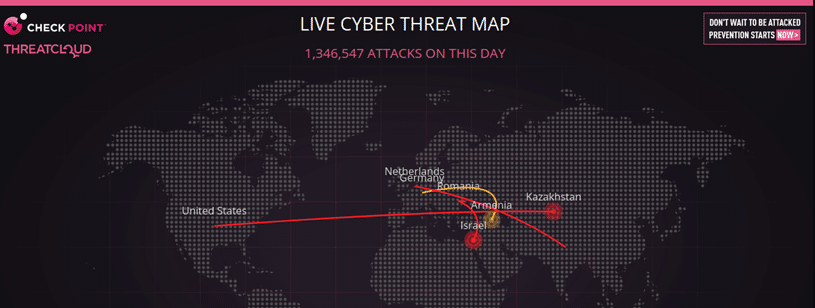
With more than 1.3 million attacks registered by Check Point in the first few hours of the day I’m writing this article, web application security has become a must for all organizations. (The link to the source of this data is in the caption below the following image.) Here’s a quick screenshot of the map when I took a look at it. Simply said, a real-time look at the live map is amazing and disturbing.
Why Is Securing Web Applications Important?
During my career, I have worked for many years as a web application security professional. Every time one of our applications was attacked, the same scene from the Matrix movie “The Matrix Revolutions” came to mind:
Just like in the movie, in the beginning, everything was quiet. Then, we usually started noticing the first small anomalies. A few suspicious logins here, and more failed accesses than normal there; you could feel that something wasn’t right. Then came the breach. After a few moments, all the hell came loose, much like in the movie when thousands of sentinels flooded into Zion.
As you can imagine, attacks on web applications can be devastating. In our case, if their efforts had succeeded, the attackers could have stolen users’ credentials, email content, and customers’ sensitive data. Or, they could have accessed the hacked inboxes and sent spam. Who would you think the customers would have blamed? They would have blamed our company, not the cybercriminals.
Imagine the impact this could have on an organization and the time it would take to recover from it:
- Damaged reputation and broken trust. Did you know that 53% of consumers would only buy from companies with a reputation for protecting customers’ data? Did you suffer a data breach? You might lose more than half of your potential consumers.
- Sensitive data loss. In January 2023, UK sports fashion retailer JD Sports admitted to being the victim of a data breach. The incident exposed 10 million customers’ personal information. The leaked data included billing details, and the last four digits of the customers’ credit cards used in the transactions that occurred November 2018-October 2020. It goes without saying that customers weren’t impressed and, boy, did they let the world know it through social media.
- Higher costs and fewer sales. According to Nationwide, the average cost of a cyber attack for a small business in 2022 was between $15,000 and $25,000. Stolen or compromised credentials could cost an average of $4.50 million, depending on the size of the business. If you add this to a decrease in sales, as a natural consequence of the breach being all over the news, there’s enough to put most companies out of business. But that isn’t all.
- Legal fees and fines. In January 2023, T-Mobile announced being a victim of a massive data breach that affected 37 million customers. After a few days, two class actions were filed in California and Florida. To give you an idea, the last lawsuit (from 2021) cost the telecom giant $350 million in settlement claims. Add to this the possible fines because of breaching security and privacy regulations like the EU General Data Protection (GDPR), and you got the picture.
I bet you understand now why 73% of the organizations interviewed by Invicti in fall 2022 confirmed that they plan to increase their investments in securing web applications in 2023.
Want to do that, too? Read on to discover how to secure your web applications without breaking the bank.
How to Secure Web Applications
“An ounce of prevention is worth a pound of cure.” —Benjamin Franklin
When I joined one of the companies I worked for as a web application security professional, the security team spent a lot of time on the cure and nearly none on prevention. As a result, successful cyber attacks were frequent, we had countless hours of overtime, and the level of customer satisfaction with our products was pretty low. Even other departments were complaining and seeing us as a bit of an incompetent team. We were in trouble.
We knew the situation had to change, so we made it so. We started putting security and prevention at the core of our activities. After a few months, we saw the first results:
- The rate of successful malicious attacks dropped dramatically,
- Breaches were identified and fixed sooner, before they could spread like the sentinels invading Zion,
- Forced overtime became a thing of the past,
- Customer satisfaction skyrocketed, and finally
- We gained the respect of other teams within our organization.
How did we do it? By putting in place the actions summarized in the table below. Want to know more? Keep reading!
| How to Secure Web Applications | Methods to Secure a Web App |
|---|---|
| 1. Put security at the heart of your software development life cycle. |
|
| 2. Audit and test frequently. |
|
| 3. Protect data in transit and at rest. |
|
| 4. Use secure authentication and access control. |
|
| 5. Use data to fix potential security holes with analytics. |
|
| 6. Validate inputs and encode outputs. |
|
| 7. Are you using containers? Manage them carefully. |
|
| 8. Keep it simple and protect your APIs. |
|
Did this list pique your curiosity? Then keep on reading and find out more about each of these SaaS marketing tactics.
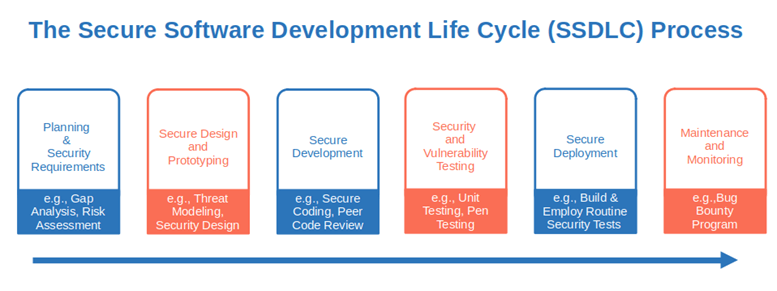
1. Put Security at the Heart of Your Software Development Life Cycle
Well begun is half done. Want to ensure the web application you’re building is secure? Start thinking about security from the very beginning (i.e., at the requirements stage). Don’t stop until the app is released.
Run a Risk Assessment
During your requirement collection activities, run a risk assessment to identify and add potential security needs to your preliminary list. Ask yourself key questions like, “How am I going to protect my web application’s secrets?” or “Where is the application going to be hosted?”
Use Threat Modeling
Integrate threat modeling in all phases of your software development process. The earlier in the process you start, the better it is. It’ll ensure that all vulnerabilities and potential threats will be identified and addressed most effectively and more timely.
Test your Code for Security and Vulnerability Issues
Run regular security testing throughout your software development life cycle. It’ll help you identify issues faster, thus fixing them before it becomes too complicated and costly.
How can you do that without impacting your time to delivery? By adopting the secure software development life cycle (SSDLC) process and putting security first (i.e., secdevops). It’ll make your web app secure and avoid you from being among the 74% of organizations often releasing software with known vulnerabilities.
2. Audit and Test Frequently
How do you know that the code you just wrote and the security fixes you’ve applied to the application you’re developing will work? How can you be sure that the best practices you’ve followed will guarantee you a secure web app development through the whole cycle?
Test Your Web Application
Keep on doing it until all vulnerabilities and potential exploitation points have been fixed. Hire an external skilled penetration tester (pentester) to hack your app just like a cybercriminal would do. Did they fail? Congratulation! You’ve done a good job. Did the pentester manage to breach your application? Now you know what you’ve done wrong.
Don’t forget to use a dynamic application security testing (DAST) tool, too. It’ll automatically test your app for everything from vulnerabilities to classic malicious inputs (e.g., SQL injections, cross-site scripting [XSS], etc.). Learn more about the dangers of XSS in this compelling Computerphile video:
Audit Your Code
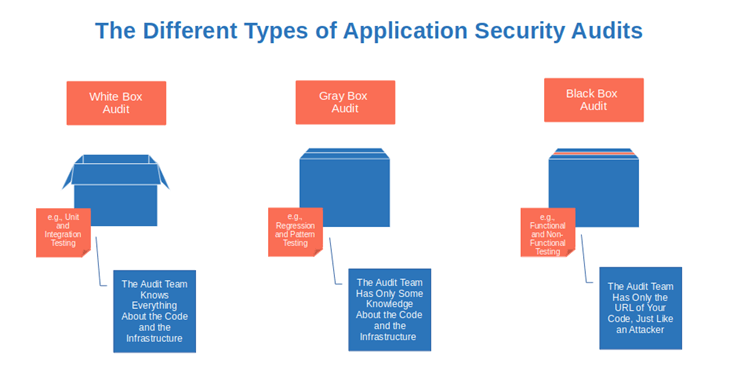
Want to check if you’ve followed all secure coding best practices and if the correct configurations have been applied? Get an audit team to do a white box audit.
Want something more similar to a pen test? Opt for a black box audit, wherein the audit team gets only the web application URL. Worried about login credentials? Go for a gray box audit.
And once you’ve got the results, you just have to analyze them and prioritize what has to be fixed first.
3. Protect Data in Transit and at Rest
Did you know that 94% of organizations surveyed by CISCO admitted that their customers wouldn’t buy a thing from them if their data wasn’t adequately protected? If you want to keep your customers coming back, then encryption is your best friend.
Use HTTPS For Everything
The hypertext transfer protocol secure (HTTPS) will keep your web application traffic safe from eavesdropping and tampering. How? By using a website security certificate (i.e., an SSL/TLS certificate). This will enable to use of the secure TLS protocol and secure hashing algorithms that’ll encrypt all data in transit between the client and the server.
Don’t Leak Sensitive Data
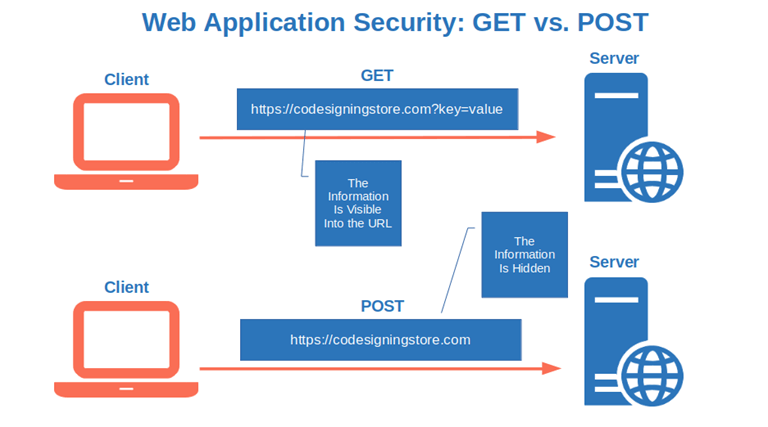
Check if your web app HTTP requests contain sensitive information such as passwords, usernames, or credit card numbers. Let’s consider a quick example.
Say, you book a train ticket you receive a confirmation email with a link to manage your booking. In some cases, that link may include a token or sensitive information directly embedded into the URL. If the email is intercepted during transmission by a malicious third party (e.g., a man-in-the-middle attack), the attacker could click on the link and use your train ticket. They could also modify it or steal your sensitive information stored on the application.
The solution? Transform your GET requests into POST requests (i.e., HTTP/HTTPS methods for sending data from a frontend to the server) if you can, and et voila’! The information won’t be visible in the URL anymore.
Verify Your Server Configurations Regularly
Keep an eye on your server and ensure that it’s always configured as it should be. For example, ensure that no old SSL protocols are allowed anymore. Tools like SSL Labs’ SSL server test will check your server configuration in a matter of minutes. Just enter your hostname and click on submit.
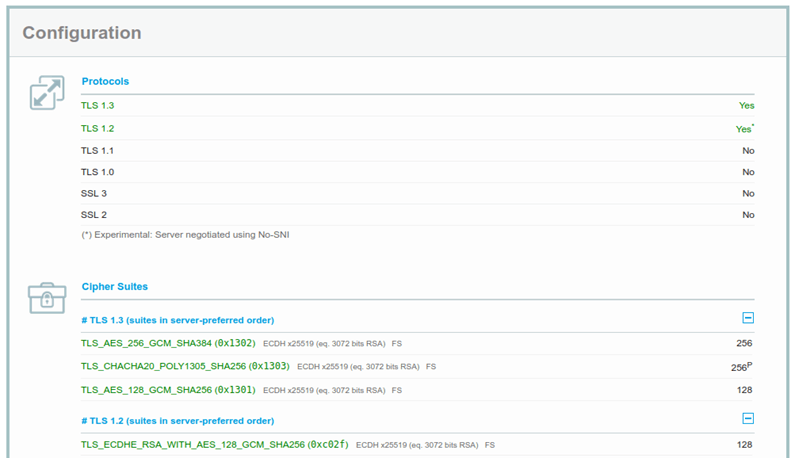
Want more tips on securing your data in transit? Check out OWASP’s TLS protection cheatsheet.
Hash and Salt Your Passwords
Storing passwords as plain text is a no-go. Use a cryptographic hashing algorithm to transform your passwords into a gibberish alphanumeric string (i.e., hash value or digest) and save only the hash value in your database.
For additional security, salt the password (i.e., add some extra data to the front of the password), add a dash of pepper (i.e., another extra bit of data at the end of the password), and then hash the whole lot. Life ain’t going to be as easy as before for those attackers looking for an easy way to steal your passwords, believe me.
4. Use Secure Authentication and Access Control
According to Surfshark, from 2004 to the beginning of 2023, globally were breached more than 16 billion accounts (16,215,269,336 as of Feb. 22, 2023). This makes an average of more than 853 million accounts hacked every year. Want to create a secure web app? Follow the National Institute of Standards and Technology (NIST) password guidelines, and:
Avoid Using Default Credentials
Last year, I changed my internet provider. When the technician came to install my new Wi-Fi router, I asked him how I could change the default router’s admin password. He looked at me puzzled and told me I was the first person in months that asked him such a question.
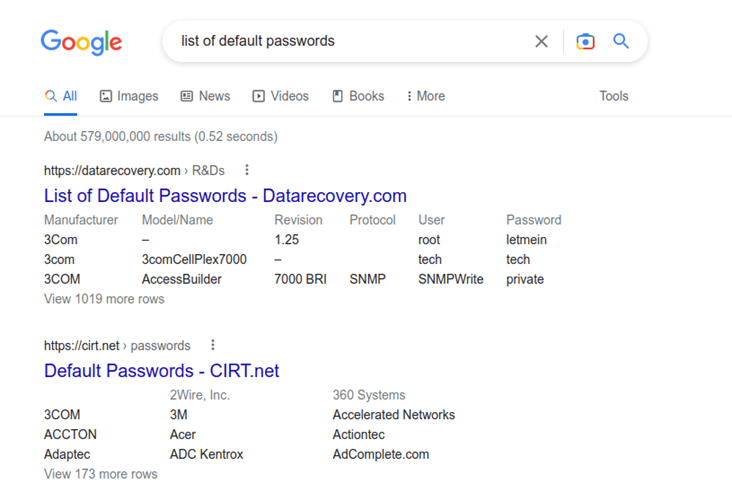
People find default passwords convenient, without realizing the enormous security risks they represent. Is it really so dangerous? Absolutely. Finding a default password is pretty easy. I just did a search on Google for “List of default passwords” and I had a staggering 579 million web page search results. And there’s no telling how many of those pages each contains thousands or potentially millions of passwords!
Don’t Hard-Code Usernames and Passwords
Do you usually embed credentials or SSH keys in your source code? I know that it’s convenient and that you usually remove them before releasing the code, however, it’s a dangerous practice.
What if you forget to remove those hard-coded credentials, or somebody else publishes the code for you without checking first? All an attacker needs to find the accidentally published sensitive information is a simple scanning tool, and the damage is done.
Still not convinced? OWASP put together a few interesting examples that might make you change your mind.
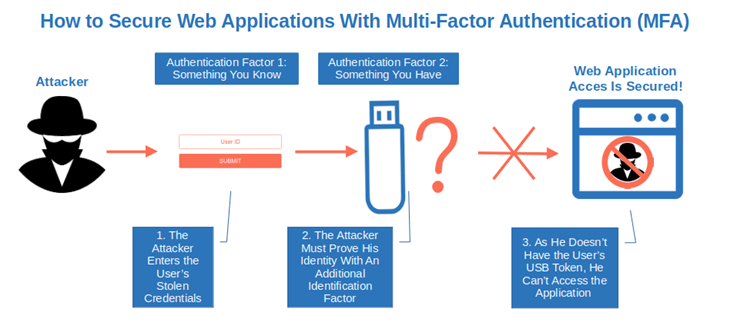
Confirm That Users Are Who They Claim To Be
How? Use multi-factor authentication (MFA) where two or more authentication factors (e.g., a password and a digital certificate stored on a hardware device) are requested to be able to get access to the application.
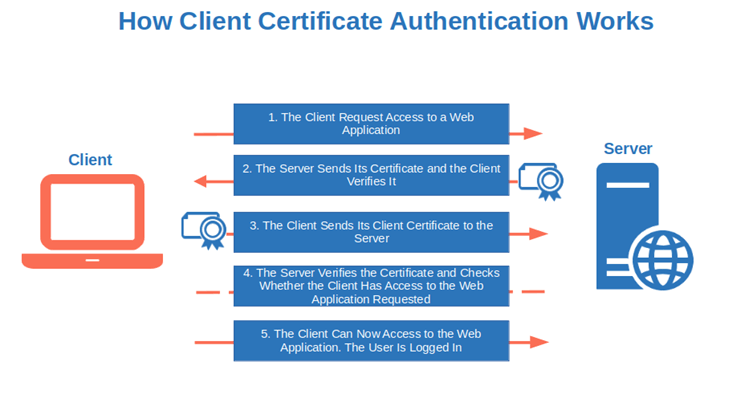
Want to make life easy for your users so that they won’t need to remember yet another password to access your web app? Implement client certificate authentication to enable users to assert their validated digital identities. This will enable them to confirm their digital identities without the need for passwords.
How does it work? The user’s client authenticates itself to the server using a public key infrastructure (PKI) client certificate, much like the server does to the client using an SSL/TLS certificate during a traditional TLS handshake.
Once the server has validated the client’s digital identity and checked that the user has the authorization to access the resource, an encrypted connection is established. Now, the user has access to the web application.
Beware, though! This method is secure only as long as the private keys used in the PKI process are kept away from malicious actors. Therefore, ensure that they’re stored in a safe location (e.g., on a hardware security module) and that only those users who need them can access them.
Define What Each User Is Allowed to Do
Not everyone needs access to everything. Tools like single sign-on (SSO) will enable you to configure user access permissions by roles, responsibilities, and department (i.e., role-based access control [RBAC]). A few popular single sign-on tools include Okta, Duo, and Microsoft Azure Active Directory (AD).
To define these roles, ensure you adopt the principle of least privilege all the time: each user gets only access to what they need to do their job and nothing else. Why? If a user account gets hacked, the attacker will be severely limited in their actions. This limits the scope of the potential damage that an attacker can cause by compromising a privileged account.
Re-Authenticate Your Users When Necessary
When you use an ATM to do more than one operation (e.g., get some cash and pay a bill), for every new procedure, you’re usually requested to enter your PIN. It may sound annoying at first, but this is another way to secure your web app further.
Many websites use the same process, too. For example, they request you to re-enter your password before updating your personal information or transferring money from your account.
5. Use Data to Fix Potential Security Holes With Analytics
Did you know that you’re sitting on a gold mine? Yup. Data is the new gold of our time, and you as an organization, have tons of it. In fact, the data analytics market size is projected to grow by $21.436 billion between 2022 and 2027. Start using the data you have to add another layer of security to your web apps.
Invest in Security Monitoring and Logging Tools
In November 2021, 61% of the organizations interviewed by Imperva said they use a web application firewall (WAF) to protect their applications and data.
A WAF will monitor your web app activities 24/7 and block real-time attacks like SQL injections (i.e., attackers inserting malicious statements enabling them to hijack your back-end database). Add to it a log and monitoring platform and you won’t miss any suspicious activities anymore.
Embed an Application Security Management Platform (ASMP) Into Your App
An ASMP is a program that’ll protect your web applications and APIs from attacks and suspicious behavior by monitoring different protocols (e.g., FTP, ICMP, and TCP) in real time. It’ll also simplify the management and configuration of your organization’s security policies so that they’re consistently implemented and configured across the whole network.
Use an Extended Detection and Response (XDR) Solution
One interface to rule them all. An XDR platform will enable you to use just one centralized interface to efficiently monitor, detect and respond to threats in your whole IT environment.
On top of that, these types of platforms use the most advanced analytics and automation methods to analyze and detect any kind of threats. It’ll help you fix vulnerabilities much faster, before the damage is done.
6. Validate Inputs, and Encode Outputs
Do you always check what comes in and goes out from your application? If you don’t, it’s time to start doing it. How?
Validate Inputs Against an Allowlist (Whitelist, Safelist)
Think about input validation as a contract between the application and the user, regulating the way inputs are entered into your system.
Every time the user types something into the form that violates the contract, it’s rejected. For example, you can use whitelisting to limit the input length as well as to regulate in which form calendar dates can be entered.
Handle Errors With Care
Image that a user tries to log in to your app but types the wrong password. Which one of the following two error messages — “Invalid username or password” or “Wrong password” — would you choose to display?
“Invalid username or password” is the answer. Why? Because this way, if an attacker tries to guess your user’s credentials, they won’t be able to know which of the two bits of info they entered was correct. If you’d used “Wrong password,” they’d immediately guess that the username entered was correct. Want to learn more? Check the related OWASP Cheat Sheet.
Encode Output
Protect your web app from cross-scripting attacks by properly encoding all outputs. How? By replacing specific HTML special characters (e.g., < and >) with other alternatives (e.g., < and %gt;).
This will prevent the automatic execution of malicious scripts that attackers might inject into your app.
7. Are You Using Containers? Manage Them Carefully
44% of businesses interviewed by the Cloud Native Computing Foundation in 2022 use containers to develop most or all their secure web apps. Do you do that, too? No matter whether you use Kubernetes or Docker, you must always manage containers correctly to avoid security issues.
Use Trusted Images and Secrets
When you create a container, always use trusted images (yours or from a trusted third party), and scan them for vulnerabilities. Never store credentials or sensitive information in the image itself.
Avoid Giving Root Access
What if your container or image is hacked and you granted either asset root access to your system? The attacker will have it, too. Are you using Kubernetes? Don’t use the “privileged container option” or the attacker will get all your host machine’s permissions.
Apply the Least Privilege Concept to Containers
Yup. It works with containers, too. Containers should get access to other systems only if they need it to function. The same goes for the internet connection. Always run your containers in a protected subnet whenever possible.
8. Keep It Simple and Protect Your APIs
Have you heard of the recent Optus Telecom cyber attack that impacted 10 million customers (roughly 40% of the Australian population)? What was the root cause? A vulnerable REST API. Want to avoid your organization making history as the next victim of a huge data breach? Then here are a few important steps to implement right away:
Encrypt Traffic Using a TLS Certificate
Do you remember when we advised you to use HTTPS everywhere? It includes your APIs as well, above all if they’re used to exchange sensitive data like user credentials or credit card information.
Implement a Rate Limit
Establish a threshold of the number of requests your API can handle per day per account (e.g., 10,000 per day per account). This is one of our recommended API security best practices. Doing this will help protect it from DDoS attacks, or what are known as distributed denial of service attacks.
Use IP Address Filtering
Restrict which IP addresses that can access your API and ensure the check is done for every single incoming request. Your IP address isn’t on the “allowed” list? You’re out, mate. By the way, the fewer entry points you have, the better it is.
Reduce the Attack Surface as Much as You Can
How? By using only the components you really need, reducing to the minimum the number of entry points to your app, and closing all unnecessary ports are all good ways to keep your attack surface as tiny as possible.
Bonus tips:
- Stay up to date on the latest vulnerabilities,
- Install patches and updates for your components, libraries, and third-party plugins as soon as you can, and
- Secure your databases.
Final Thoughts on How to Create a Secure Web Application
With more and more people connecting to the internet, shopping online, and working remotely, securing web applications is something that organizations and developers alike can’t ignore anymore.
Next time you develop a new application, use a secure web app development approach. Follow the suggestions we’ve listed in this article. It’ll help you ensure you build your application with safety in mind. From the very beginning to the end.
Remember! Securing applications and, thus, protecting your customers and your organization from malicious attacks and data breaches is a never-ending journey. Don’t stop now. Keep on discovering new application security tips by exploring our other resources:


