How to Use Java Keytool to Create & Manage a Java KeyStore

DigiCert 2024 digital trust survey: 74% of businesses had their private keys or digital certificates stolen, compromised, or misused in 2023. Learn how to create and use a Java Keystore to protect your insecure keys and certificates.
Java Keytool is a Java-specific certificate management tool that allows you to store your cryptographic keys and certificates in a special digital file. Think of Java Keystore as a digital lockbox that helps you easily manage and securely store your cryptographic keys and certificates. It protects those keys from prying eyes, even during development and testing, and enables you to use them for cryptographic functions without requiring direct access.
Since the industry changes to code signing baseline security requirements came into force in June 2023, Java Keystore can only store and manage self-signed certificates. Granted, it still works for SSL/TLS certificates, but that isn’t really the focus of this Java-focused article.
Certificates and key-related incidents continue to be among organizations’ top security concerns. Keyfactor’s 2024 PKI & Digital Trust report indicates that businesses suffered an average of nine certificate-related issues in 2023.
Today, we’ll show you:
- How to generate your very own Java Keystore using Java Keytool,
- Four ways you can use it to enhance the security of your keys, certificates, and Java applications, even during development, and
- An alternative approach you can take for signing your Java apps, if you’re publishing your software externally and need a publicly trusted digital signature.
How to Create a Java Keystore With the Java Keytool
If you used a Java Development Kit (JDK) to build your Java app/applet Java Keytool should be already installed on your device. In fact, the JDK also includes:
- JarSigner.exe. A utility enabling developers and software publishers to digitally sign Java applications with a code signing certificate.
- Java Keytool. A command line tool to generate and manage Keystores, key pairs (i.e., public and private keys), and self-signed certificates.
If you don’t have JDK already installed on your device, follow the same steps to download and install JarSigner described in our previous article. Once done, then keep reading here.
Note: All Keytool command examples in this article contain some options in bold. To use them correctly, replace the marked text with the information about your keystore and files.
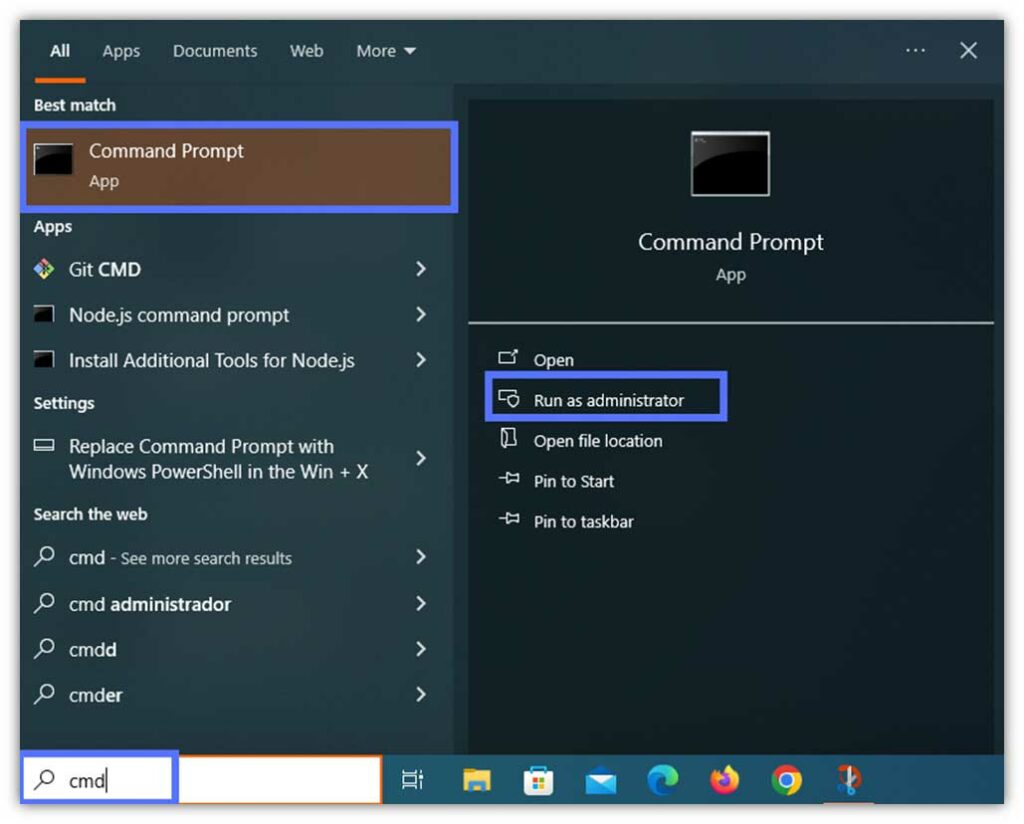
1. Navigate to the Keytool Folder Using the Command Prompt (CMD) as Administrator
- Type cmd in the Windows Search bar, as shown in the screenshot. Hit run as Administrator. The CMD window will pop up.
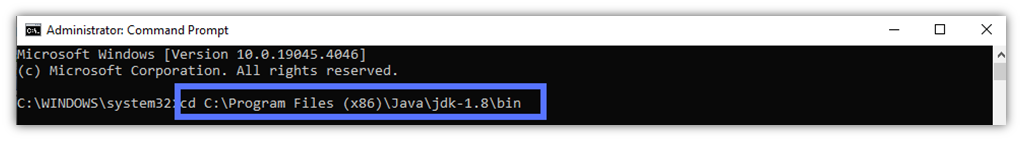
- Use the cd command to go to the directory where Keytool is stored and hit Enter.
cd C:\file_path_to_java_JDK_folder\Java\Your_jdk_version\binHere is what it looks like in our real-life example. Keytool.exe is usually located in the JDK’s bin folder.
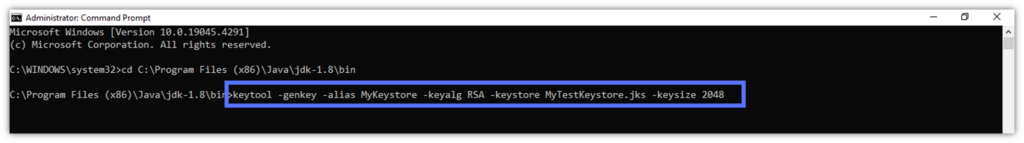
2. Generate a Key Pair, a Keystore, and a Self-Signed Certificate
- Key the script belowandhit Enter. NOTE: “Alias” is the term Java keystore uses to refer to the certificates it generates and stores.
keytool -genkey -alias keystore_alias -keyalg encryption_algorithm -keystore path_to_the_keystore_being_created.jks -keysize 2048 Pro tip: Always use a strong key size when signing executables and other code. In our Java Keystore example, we’ve chosen a 2048-bit key. (NOTE: The minimum key size required for publicly trusted code signing digital signatures is 3072 bits.)
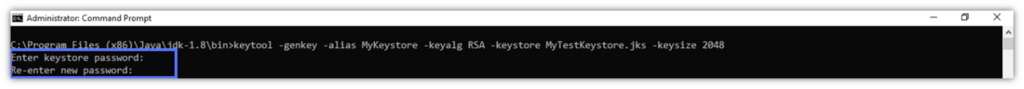
- At the prompt, type a Keystore password and hit Enter. Re-type it to confirm it and click Enter again. As shown in our sample, the password field will remain empty. Don’t worry. The password has been registered.
- Key in your organization information (e.g., name and domain), which is used to issue your self-signed certificate. Click Enter. Once finished, you’ll be required to type your key password twice.
Pro tip: Never share your private key with anyone. If an attacker gets hold of it, your certificate will be compromised.
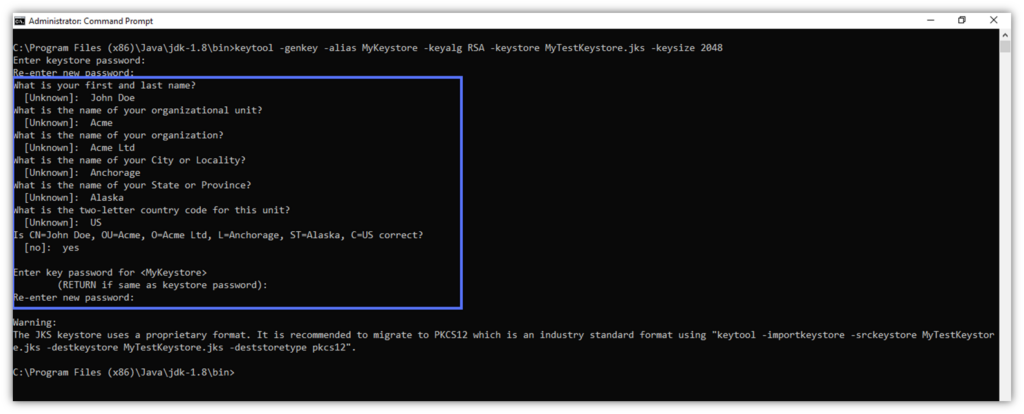
Mission accomplished! Using Java Keytool, you’ve just created a Java Keystore and a self-signed certificate that will be valid for 180 days (Keystore’s default certificate validity period).
Optional: Migrate Your Keystore to the More Secure PCKS12 Format
When you generate a new Keystore or certificate with Java Keytool in the .jks format (i.e., Oracle Java-specific file format), you may see this warning:
The .jks file format will work just fine for Java-based applications. However, there may be situations where you might need a more secure and versatile solution. For instance, .jks files don’t work with OpenSSL, and Java Keystore doesn’t allow you to import or export the private key using Keytool.
Here is where the standardized PKCS#12 format comes in. Oracle recommends using the PKCS#12 for Java Keystore because it’s an industry-standard format that’s cross-platform compatible with most platforms and offers enhanced security that’ll enable you to use your existing private key and certificate.
Want to give it a try?
- Migrate your Keystore to PKCS#12 with the command listed below:
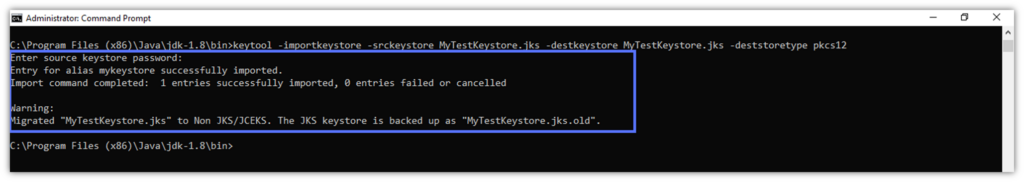
keytool -importkeystore -srckeystore -keystore path_to_the_keystore.jks -destkeystore path_to_the_keystore.jks -deststoretype pkcs12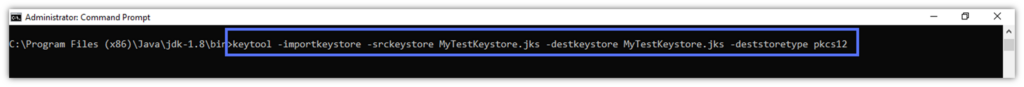
- When prompted, type your Keystore password and hit Enter (not pictured).
And it’s done: Java Keystore has been successfully migrated to PKCS12 format. Keytool has also created a backup copy of the original .jks file (“MyTestKeyStore.jks.old” in our example).
Interested in learning more about PKCS12 keystores? Check out this short video:
4 Ways You Can Use a Java Keystore to Secure Your Java Development Project
Now that you’ve generated your Java Keystore, key pair, and basic self-signed certificate, let’s uncover how you can practically use the Keystore to:
- Enhance the security of your Java application(s) in development
- Fix security issues that might affect the security of your certificates and Keystore
- Confirm the authenticity and integrity of your Java apps
- Boost trust among users and services once published or distributed
Java Keystore Example #1. Create a Self-Signed Java Code Signing Certificate for Testing
Let’s generate a self-signed code signing certificate valid for a whole year.
- In the cmd window, type the following and hit Enter.
keytool -genkey -alias keystore_alias -keystore path_to_the_keystore.jks -storepass your_keystore_password -validity 360 -keyalg encryption_algorithm -keysize 2048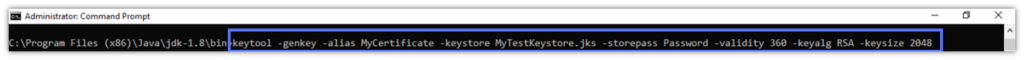
- Fill in your certificate’s information. Click Enter.
- Type your certificate password twice.
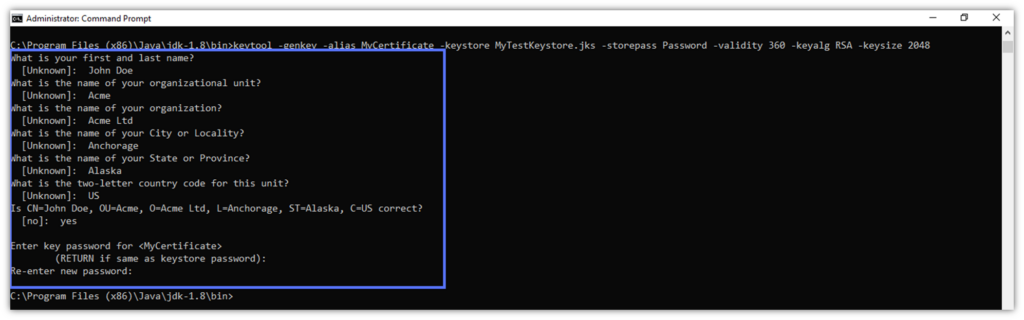
Now, verify that the certificate has been added to your Keystore with:
keytool -v -list -keystore path_to_the_keystore.jks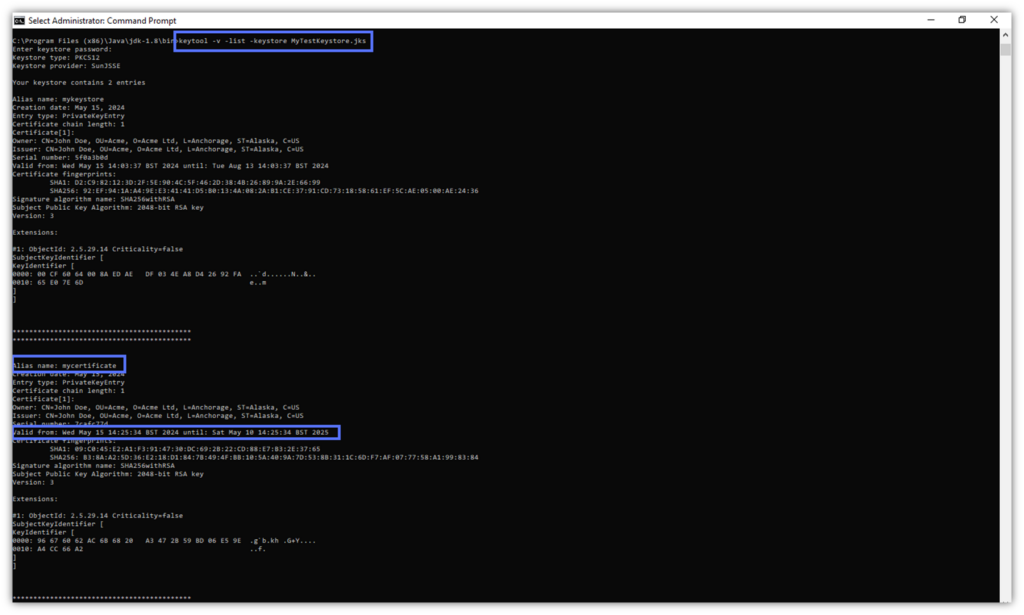
Job done! You can now use your self-signed certificate during development, testing, or in a training environment for up to one year.
Pro Tip: Always sign your published software with a code signing certificate issued by a globally recognized certificate authority (CA). If you use a self-signed certificate, browsers and operating systems will display a warning message whenever a user tries to download or install the app. Code signing should foster trust, not scare your customers away, which is why it’s important to use a publicly trusted certificate.
You don’t have a trusted code signing certificate? We can help.
Save Up to 21% on a Java Code Signing Certificate
Digitally sign unlimited JAR files and applications for as little as $211.46/year.
Jump to “The Alternative: Sign Your Java Apps Without a Keystore” section to learn more about different options for this type of certificate.
Java Keystore Example #2. Export a Self-Signed Certificate From a Java Keystore Into a Truststore
To export your self-signed code signing certificate to save it in a Truststore (a type of Keystore used to store third-party certificates that a device should trust):
- Type the script below in the cmd and click Enter. Provide your password when prompted.
keytool -exportcert -alias mycertificate -keystore path_to_the_keystore.jks -file mycertificate.crt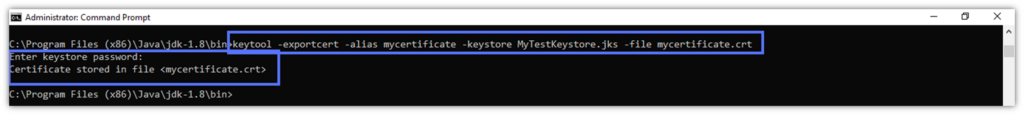
The .crt file has been saved in the same Keytool /bin folder.
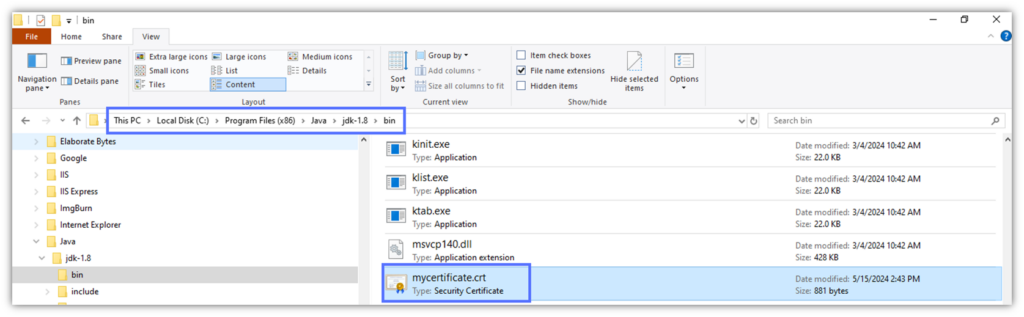
Now, you can send the .crt file to your users. To save the file in a Truststore:
- Modify the following script to include your necessary file path info and post it in CMD to create a Truststore with Java Keytool. Hit Enter.
keytool -importkeystore -srckeystore path_to_the_keystore.jks -destkeystore path_to_the_truststore.jks -deststoretype jks
After you’ve typed your new Truststore password twice and your original keystore password once, as shown in the screenshot below, your Truststore is ready. Good news: like Java Keystore, the Truststore is also available in PKCS12 format. Follow the directions outlined in the screenshot (or on your CMD Prompt screen, if you’re following along on your own system) to migrate to PKCS#12.
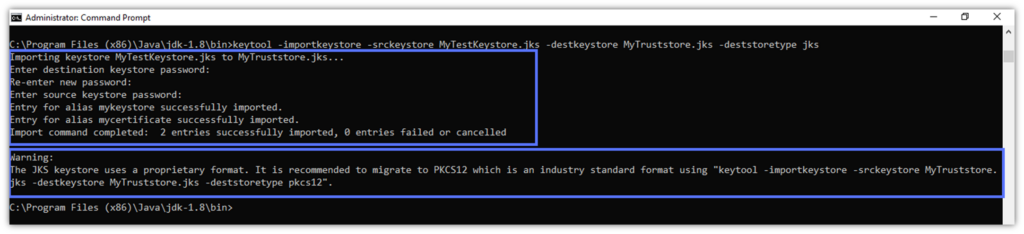
- Let’s import the .crt certificate. Enter the following:
keytool -importcert -alias certificate_alias -file path_to_certificate.crt -keystore path_to_truststore.jks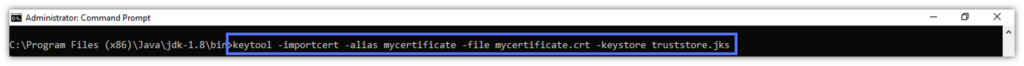
- Hit Enter and provide your password twice. Then, type yes to confirm that the certificate should be trusted, just like we did in the example below.
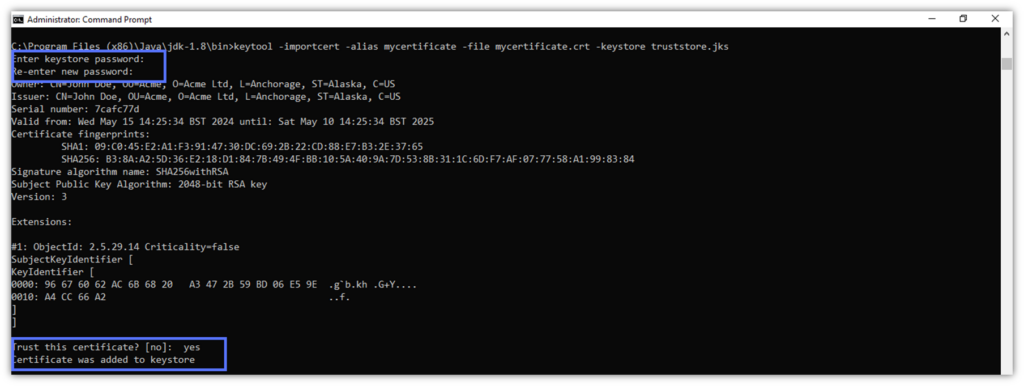
Voila’. The certificate has been added to the Truststore.
Java Keystore Example #3. Use Keytool to Change Your Passwords
35% of a recent Forbes Advisor survey participants confirmed that weak passwords were the primary root cause for their hacked accounts. Weak and insecure passwords are a paramount concern for developers and publishers, as someone using your certificates and private keys can cause irreparable harm to your customers through their supply chains and catastrophic damage to your reputation.
Your Keystore and private key passwords are key barriers against cybercriminals.
Option 1: Change Your Keystore Password
- In the cmd, type the simple command below and hit Enter.
keytool -storepasswd -keystore path_to_the_keystore.jks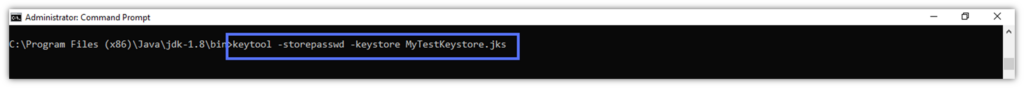
- Enter your actual Keystore password, provide the new password, confirm it, and hitthe Enter key.
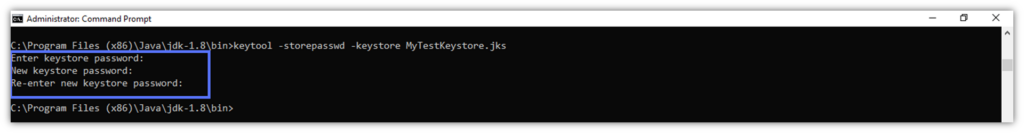
Done and dusted.
Pro Tip: Password security matters. Consider implementing multifactor authentication (MFA) to add another layer of security. It’ll help protect you from breaches by requiring you to provide two or more authenticating factors (e.g., a one-time code and a password).
Option 2: Change Your Private Key Password
Type the script below followed by Enter:
keytool -keypasswd -alias your_key_name -keystore path_to_the_keystore.jksJava Keystore Example #4. Delete a Certificate From Your Java Keystore
Have a problem with a certificate? Get rid of it and create a new one.
- Make sure you know the certificate’s alias. If you forgot it, run the -list -v command option below to get a list of all the files saved in the Java Keystore. Click on Enter.
keytool -v -list -keystore path_to_the_keystore.jks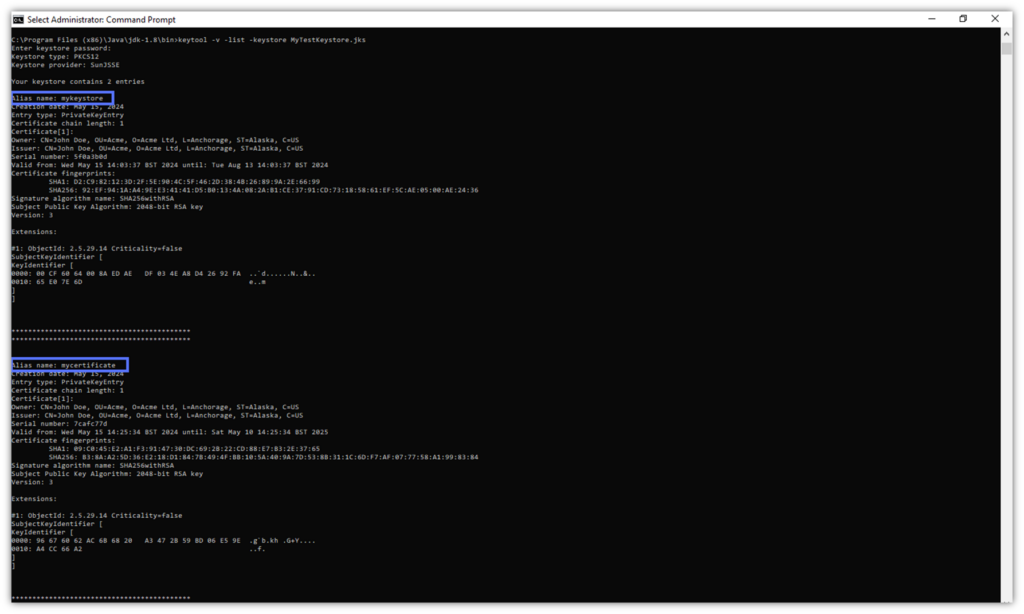
- Delete the certificate with the following command. Click Enter, type your Java Keystore password, and click Enter one more time.
keytool -delete -alias certificate_alias -keystore path_to_the_keystore.jks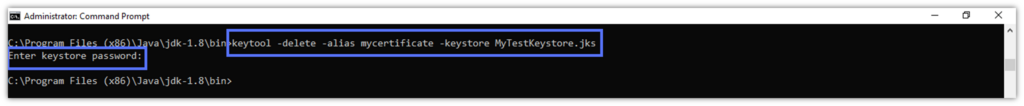
Victory! The certificate is now deleted. But how do we know that it’s gone when it doesn’t display a confirmation message of some kind, verifying that the certificate has been deleted? Using the -list -v command you just learned enables us to verify that it has been deleted. There’s only one entry left in the keystore and no sign of the deleted certificate.
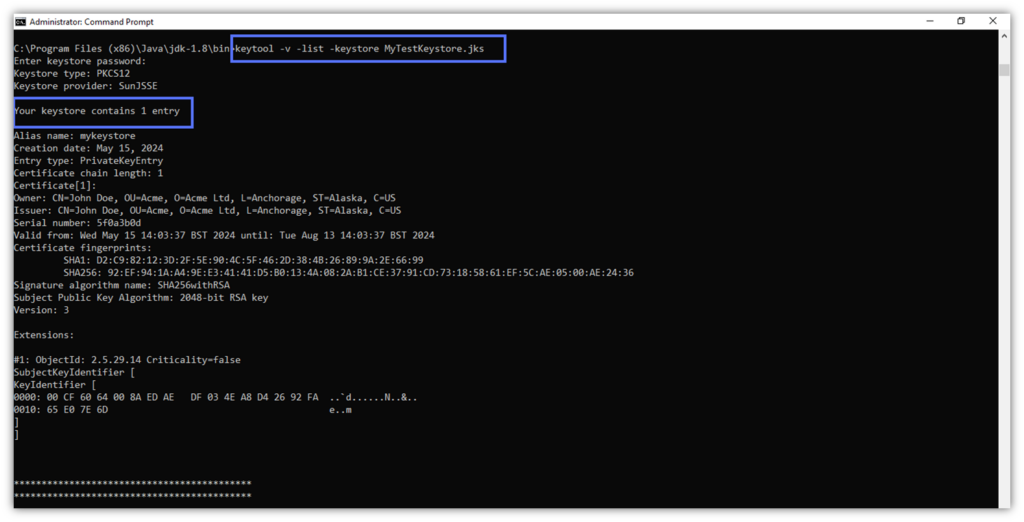
Pro Tip: Regularly back up your Keystore files using the -keyclone option, especially when deleting something or changing passwords. It may be your lifeline in case of wrong deletions or data corruption.
The Alternative: Sign Your Java Apps Without Using Java Keystore
To make your Java app available to the public, you’ll need a widely trusted digital signature. A globally recognized seal of authenticity and integrity that can only be applied to your software using a CA-issued code signing certificate.
As Java Keystore doesn’t work with this type of certificate, CodeSigningStore.com’s GoGetSSL cloud signing solution can be a valid, highly secure alternative. This DigiCert-powered code signing certificate is stored in a cloud hardware security module (HSM) so that users don’t have direct access to the key.
As with Java Keystore, DigiCert’s KeyLocker software license included in the package will let you securely generate and store your private key. However, the GoGetSSL cloud code signing certificate offers far greater versatility. It enables you to sign your Java apps with Jarsigner and a plethora of other software using DigiCert’s Click-to-Sign tool or another third-party tool of your choice (e.g., SignTool, jSign, Sign4j, OpenSSL, etc.).
Save Up to 45% on a GoGetSSL Cloud Code Signing Certificate
Digitally sign up to 1,000 signing without having to manage a physical USB token for as little as $372.69/year.
Looking for more alternative Java Keystore solutions? Check out our quick guide on how to code signing certificate options without a hardware token.
Final Thoughts on Using Java Keytool to Create & Use a Java Keystore
Java Keystore is the digital guardian that’ll keep your Java code, cryptographic keys, and self-signed certificates secure during testing and development. Once you’ve created your Java Keystore, secure it by implementing and adhering to a few industry best practices, including:
- Using strong passwords and multifactor authentication,
- Keeping your private keys private (i.e., don’t hardcode or otherwise share your credentials),
- Backing up your Keystore, and
- Reviewing your certificates regularly.
Last but not least, be sure to sign its .jar files using a CA-issued code signing certificate before moving your Java application to production. This will assert your identity and the integrity of your software. Your app will be trusted by major operating systems and browsers. Moreover, it’ll keep your organization from becoming the next headline about compromised keys and certificates.


