26 Ways to Improve Your Web Application Security
53% of consumers say they’ll only buy from companies that are known for protecting customers’ data. Discover how to develop, maintain and operate trustworthy web applications. Toughen up your internal and external apps against attacks while balancing innovation and security
In 2021, 95% of web applications subjected to commercial software security tests by Synopsys Cybersecurity Research Center (CyRC) had vulnerabilities. 25% of them were ranked high or critical. And things didn’t improve much this year as Gartner is already forecasting application security spending to reach $7.5 billion in 2023 alone.
Do you want to be ahead of the pack and maybe save a few dollars? Start securing your applications right now by following our simple but effective tips for any organization, big or small. Discover how to address seven common web application security issues — from data breaches to security misconfiguration issues and weak authentication.
Act now before it’s too late. Learn what you can do to protect your web applications and stop being a prime target for cybercriminals.
What Is Web Application Security and Why Is It Important?
Web application security enables organizations to secure and protect web apps and services from cyber threats, often caused by software vulnerabilities. Why is it important?
- Organizations and customers are going digital. 72% of organizations’ interactions with customers are now digital.
- Vulnerabilities are rising. In October 2022, the National Institute of Standards and Technology’s (NIST) National Vulnerability Database (NVD) listed 1,919 new vulnerabilities. That’s nearly 200 more than those identified in October 2021.
- Cybercrime is growing. Costs associated with the damages stemming from cybercrimes are projected to reach $10.5 trillion by 2025.
- Customer-facing web applications are the number one security worry for security professionals. Cisco’s survey confirms that customer-facing apps are introducing the highest security risks.
Want to boost your web application security strategy in preparation for the year ahead? Keep on reading!
7 Web Application Security Issues (And How to Fix Them)
Data breaches, code injections, malware. Welcome to every organization’s nightmare. In this article, we’ve put together seven of the most common web app security issues and the best solutions to help you keep your organization, customers, and sensitive data safe. Seven days, seven web application security problems, 26 solutions — because every day is a challenge in the digital world.
| Web Application Security Problem | Solutions |
|---|---|
| 1. Security Often Comes Last |
|
| 2. Data Breaches Are on the Rise |
|
| 3. Password and Authentication Issues |
|
| 4. Injection and Cross Scripting (XSS) Attacks |
|
| 5. Security Misconfiguration and Negligence Issues |
|
| 6. Malware and Virus Infection Risks |
|
| 7. Insecure Third-Party Components and Vulnerabilities |
|
Web App Security Issue #1: Security Often Comes Last
It’s Monday. A new week is starting and your development team is nearly ready to release a new web app after months of hard work. Everybody is nervous, though, because they — like 70% of organizations did in 2021 — skipped some security steps to ensure they could deploy the app on time. And the app still has to go through the vigil eye of the security team. What if they find something wrong? The whole project will be delayed.
The solution? There are many. These are our top three selections. Pick one or, for a more secure application, go with all of them. It’s up to you to choose how much further you want to go.
1. Implement Secdevops
This is an evolution of devsecops where security is put at the heart of the development process. With secdevops security is baked into the process right from the start. Every person involved in the development process — from QA engineers to developers to the project management team — shares responsibility for the security of the application.
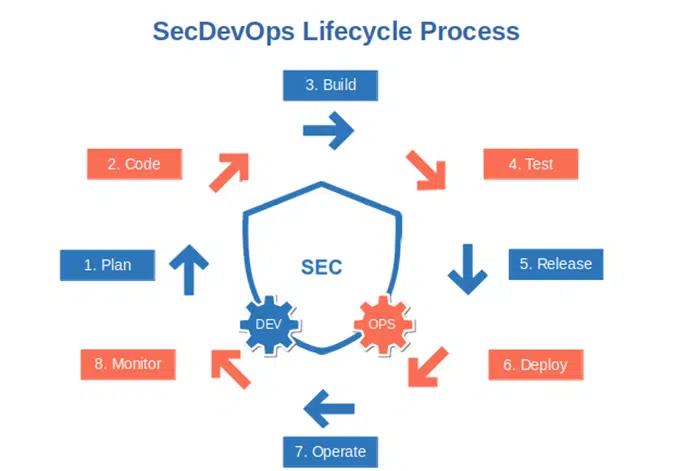
2. Follow the Secure Software Development Life Cycle (SSDLC) Process
Implementing an SSDLC process will help you ensure that security becomes the protagonist of your web application development story. It’ll also enable you to reduce costs, fix security issues faster and reduce the number of last-minute changes. Are you worried about the implementation of such a process? Don’t. Use a ready-made, secure software development framework (SSDF) of your choice and let it work its magic. You’ll be surprised how easy it is.
3. Choose a Secure Host
You can follow all the security processes you want, but if you don’t use a secure host, cybercriminals will still be able to sneak into your systems. Opt for well-known, trusted companies that don’t have a record of long downtimes. Check that they offer security features like secure file transfer protocol (SFTP), rootkit scanners, and that they provide a data backup service. Sure, it might cost you more at the beginning, but it certainly won’t cost you $4.35 million, which is the average actual cost of a single data breach.
Web App Security Issue #2: Data Breaches Are on the Rise
It’s now Tuesday, the second day of the week. Before going to work, you’re flipping through the latest security news and find out that Q3 2022 had 43,5% more breaches than the yearly average. What if such a situation happened to your organization? That’s when you start thinking about possible solutions. But what can you do to prevent data breaches from occurring?
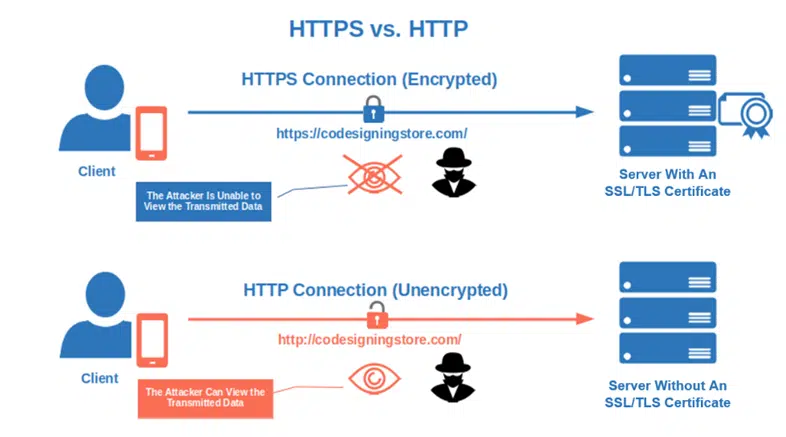
4. Use Secure URLs Only to Secure Data in Motion
In other words, use a secure sockets layer/transport layer security (SSL/TLS) certificate to encrypt communications between the client and the server. It’ll prevent unauthorized third parties from reading the information in transit (man-in-the-middle attacks). And there are bonuses, too! When you add an SSL/TLS certificate to your website, major browsers won’t flag it as being insecure anymore and your Google ranking will improve.
5. Limit Access to Only What Is Necessary
I remember a manager I was working for who always insisted they get administrator privileges for all web apps. Was it a good idea from a security perspective? Definitely not. Research shows that managers constitute 10% of the users in an organization but represent 50% of the most dangerous data breach risks.
But let’s go back for a moment to my story. The manager obtained his administrator privileges as he wished. One day, however, he inadvertently clicked on the wrong button. All users’ passwords for a key application were reset. It resulted in chaos but, thankfully, didn’t cause a security incident beyond that. From that day onward, we always applied the principle of least privilege (PoLP).
It doesn’t matter who you are — you should only get access to what you need to do your work. Will view and/or edit access do? Good, then no admin access for you. Try this conservative approach to handing out access — it may save your bacon one day.
6. Revoke Credentials When Employees Leave Your Company
In September 2022, 5,688 Americans left their jobs. In fact, the labor market has become much more dynamic over the past few years as employees come and go more often than before. Make sure that when someone leaves, their access to systems and data is immediately revoked, and their IDs are deleted or deactivated. Recording users’ access and privileges will make this task even simpler.
7. Secure Your Data at Rest
OK, so using the hypertext transfer protocol secure (HTTPS) and SSL/TLS certificates will keep your data secure during transmission, but what about data at rest? How do you protect the sensitive information (e.g., customers’ addresses, credit card numbers, tax numbers) saved on your databases? Secure them using strong encryption algorithms. What about passwords? That’s what we’re going to see next.
Web App Security Issue #3: Password and Authentication Issues
It’s Wednesday, and you’ve just received a reminder that your intranet password will expire in a few days. Time to think about a new, safe one to use. Again. But with more than 24 billion stolen credentials circulating in the dark web, it’s easier said than done. Which makes you think: “Aren’t there any other possible solutions?” Of course, there are:
8. Implement Strong Password Policies
Bad guys use credential stuffing to access applications using stolen password-username combinations or brute force attacks to guess weak credentials (e.g., default credentials or the same passwords used for different accounts). To make cybercriminals’ jobs harder, create a set of rules that will force legitimate users to create secure passwords.
Want an example? Don’t accept passwords shorter than eight characters and that don’t include several different types of characters and numbers. Do you want more tips? Follow NIST’s Special Publication 800-63B Digital Identity Guidelines.
9. Never Save Passwords as Plain Text
Do you remember when, in section two (#7 on the list), we talked about the importance of protecting data at rest? Passwords are part of it, too. So, what’s the best way to protect them? Store only password hashes in your databases using a hashing algorithm (i.e., a secure hashing algorithm) and add some salt and pepper. These are strings of randomized characters that are added before hashing the password. By the way, the pepper bit is stored separately from your password hashes to make potential attackers’ lives even more difficult.
10. Use Multi-Factor Authentication (MFA)
Do you know the Cybersecurity & Infrastructure Security Agency (CISA)’s #MoreThanAPassword campaign? If you don’t, we suggest you check it out because a good password isn’t enough in today’s digital world. With MFA, a user must prove their identity in two or more ways besides entering their credentials.
Do you use Tableau Cloud? If so, you should already be familiar with MFA then as it’s their chosen method of authentication since February 2022. There are many MFA software on the market offering different features and levels of security. Why don’t you compare them and select the one you prefer?
Psst! I know that many organizations still use SMS text messages as an authentication factor, which isn’t good, but it’s still a tad better than using traditional credentials alone, as Microsoft explains. Be bold! Choose something more secure, such as certificate-based authentication.
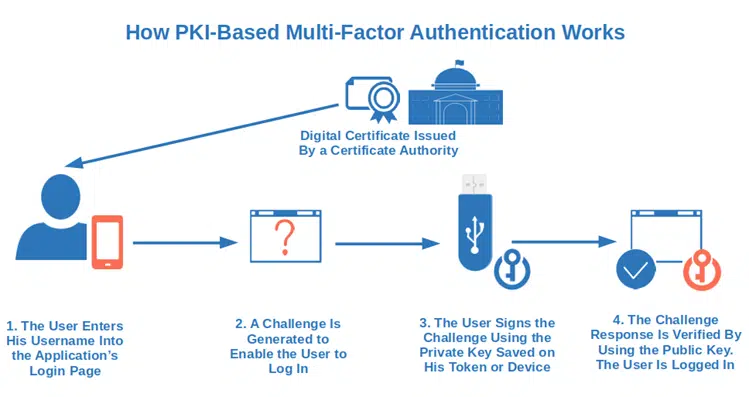
11. Go Passwordless
No matter what you do, traditional passwords will always be vulnerable to attacks. In fact, a recent study demonstrated that 41% of stolen passwords were 12 or more characters long. You can reduce the risks, but the only way to avoid stolen credential issues is to take a step toward the future and eliminate them entirely. How? By harnessing the power of public key infrastructure (PKI).
This process involves the use of a digital certificate, a public key, and a private key. The private key is stored on the user’s device and can be accessed only after providing an additional authentication factor (e.g., biometric or a hardware token). Want to see it in action? Microsoft Azure Active Directory is already offering this option.
Just be sure to securely storage and manage your cryptographic certificates and keys with the utmost care. If you don’t, then you’ll be in for a world of pain.
12. Limit Login Attempts
This is one of the techniques the company I was working for was using. It’s quick and easy to set up and doesn’t cost much. You basically implement a rule that if a user tries to log in too many times with the same account within a given time, the access to the application is automatically locked for a set time. You have no idea how many brute force and credential-stuffing attempts we managed to stop with this simple approach.
Web App Security Issue #4: Injection and Cross Scripting (XSS) Attacks
Thursday is here, and after reading the latest Breachlock Penetration Testing Intelligence Report, you’ve just realized that cross-scripting (i.e., when an attacker injects malicious code into an application or website) and other types of injection attacks are more common than you thought.
Imagine if one of your employees visited a website where an attacker injected a redirection to a malicious site. How could you avoid a similar situation happening on your site to keep your customers (and their data) safe? You’ll want to implement solutions like the following:
13. Sanitize and Validate User Inputs
Clean up your users’ inputs by removing, replacing, or escaping all unwanted characters (i.e., data sanitization). Ensure that all users’ inputs follow the rules you’ve created (e.g., characters whitelisting) so that only the approved characters and formats will be accepted (i.e., data validation). For example, do you want to validate phone number inputs on a web form? Create a whitelist including only numbers from zero to nine. This way, all other characters will be rejected. These methods will help you avoid cybercriminals adding malicious scripts to your forms.
14. Use Web Application Firewalls (WAF)
A WAF will help you monitor your web application traffic closely, identify anomalous commands, and block suspicious activities. You can set custom rules adapted to your application’s patterns and use pre-set vendor rules to identify common attack patterns.
15. Implement Strong Content Security Policies (CSP)
Mitigate the risk of XSS attacks by restricting what a web page can load (e.g., scripts and images) or if other pages can frame the page. Want more examples? Check OWASP’s content security policy cheat sheet.

16. Hire an Ethical Hacker’s Services for Pentesting
Do you know that there are bad hackers and good hackers? The good ones (or white hats) help organizations to find potentially vulnerable entry points and understand the techniques the bad guys could use to attack your website or apps. Get a white hat or a pentester to attack your application. If there’s a security hole, they’ll find it. Want to find an ethical hacker? If you do a search on the internet, you’ll find that several companies are offering ethical hackers for hire.
17. Use Scanning and Detection Technologies
Here, the operative word is automation. Several automated tools exist that can scan your source codes, websites, and apps to detect anomalies and vulnerabilities. From static application security testing (SAST) used to identify vulnerabilities to dynamic application security testing (DAST), which analyzes application responses to malformed or malicious commands. Do you want something that’ll enable you to monitor all your networks, clouds, endpoints, and applications leveraging artificial intelligence (AI)? An extended detection and response platform (XDR) is what you’re looking for. It’ll help you identify zero-day attacks, sophisticated threats, and application layer vulnerabilities.
Web App Security Issue #5: Security Misconfiguration and Negligence Issues
And it’s Friday! You’re nearly ready to go home when your boss calls you into his office. Unfortunately, it isn’t to wish you a nice weekend. While playing with an application your team has just released, he noticed that anyone can assign themselves admin privileges. This kind of mistake can put your organization in real trouble if you consider that Verizon reports 82% of breaches are caused by human elements like configuration errors.
Once you’ve spent a couple of extra hours fixing the problem, you can finally go home. But there’s the nagging thought in the back of your head: How can you avoid starting another weekend with some Friday overtime due to security misconfiguration or negligence?
18. Run Regular Security Vulnerability Testing.
In the previous point, we talked about SAST, DAST, and how using pen testers or white hats to attack your apps can improve the security of your apps. Ensure you embed regular security tests into your secdevops process and you’ll dramatically reduce the risks of misconfigurations and errors.
19. Avoid Using Default Settings
Usually, software like content management systems (CMS) and others, come pre-configurated with default credentials, security settings, and user permissions. Attackers are clever little buggers who use automated scans to identify those kinds of pre-configurations. Once they find one, they have no mercy. I have a WordPress-based website, and the first thing I did when I set it up was to change the default admin credentials, set a limit for login attempts, and specify file permissions.
20. Train Developers and Users in Cyber-Secure Practices
Show your developers and users the danger of negligence (e.g., using a common password or saving credentials within the code during development) and misconfigurations. Create and share security training documentation to raise awareness. Tools like Atlassian Confluence or short videos can be of great help.
Web App Security Issue #6: Malware and Virus Infection Risks
Don’t you just love starting your Saturday morning with a nice cup of coffee while checking the news on your favorite app? What? Wait! Your tablet is running slower than usual, and every time you open a web page, dozens of pop-ups appear. What happened? You pause for a moment and remember that you downloaded a new app yesterday. Could it be that you also installed a virus with the software package? The tablet is now unusable and you end up spending the whole morning to fix it.
How can you avoid something similar happening to your customers? And how can you protect your organization’s reputation as a trusted software vendor when, from January to November 2022, AV-Test identified more than 89 million new pieces of malware? You need to take steps to protect the security of your app.
21. Digitally Sign Your Codes (and teach your users to stay away from unsigned software)
When you use code signing to apply your digital signature to updates with a code signing certificate that’s issued by a trusted certificate authority (CA), you’ll help protect your users against downloading infected codes. How? By validating your identity with your code signing certificate and confirming that your code hasn’t been modified (i.e., it’s malware-free).
Use videos or newsletters to teach your users how it works and show them the benefits. They’ll see that you care and they’ll likely trust you more. You don’t have a lot of money and you’re thinking to use a self-signed certificate created by you? Bad idea. It’s like creating and printing your own passport. Anyone could do that and use your name, including cybercriminals, but it won’t be a trusted document (for obvious reasons).
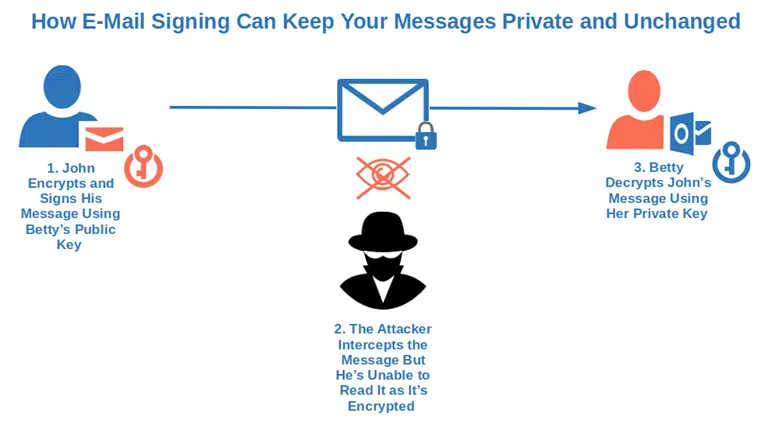
22. Sign Your Emails (and Teach Users the Benefits of Digitally Signing Outbound Emails).
Email-signing certificates follow the same logic as code-signing certificates. In addition to confirming to the user that the email is coming from you and that it hasn’t been altered, it’ll also allows you to encrypt it using the recipient’s public key. (Note: both the recipient and the sender must be using email signing certificates for the encryption process to work.)
The recipient’s operating system will then automatically decrypt the message using their corresponding private key. The process is easy as a pie and it’ll help keep your users safe from phishing and malware.
23. Use Malware and Antivirus Scans (and Keep Them Up to Date)
Scan your apps and website regularly using top-notch malware and antivirus scans. Sure, freeware antivirus software can be cheap, but it usually gets the latest identified malware and virus signatures much later compared to paid software (leaving your systems at risk in the meantime). Online scanners like VirusTotal are good options when you need to check a file or URL on the fly.
Web App Security Issue #7: Insecure Third-Party Components and Vulnerabilities
Sunday. This is normally a day to spend with your family and enjoy some well-deserved rest. But as soon as you fire up your barbecue, your phone rings. Your colleague on duty informs you that they’ve detected huge login spikes on one of your top-selling web apps. Looks like the barbecue will have to wait.
A few days and a lot of exhausting working hours later, you find out that the attackers managed to steal usernames and passwords by exploiting a two-year-old unpatched vulnerability. What can you add to your list of potential solutions for tomorrow’s lesson-learned meeting?
24. Know Your Software and Vendors
List the “ingredients” of your software. In other words, fill in a software bill of materials (SBOM) and make sure you include also third-party components and libraries. It’ll make vulnerability management much easier and ensure that you’ll never forget a path or an update.
The U.S. National Telecommunication and Information Administration (NTIA) put together a very informative page full of SBOM resources, examples, and use cases. Don’t forget to keep an eye on your software vendors to ensure their security policies and procedures are up to date.
25. Prioritize Zero-Day Vulnerability Patching
Keeping up to date with the latest vulnerabilities through feeders and newsletters is important, however, you’ll also need to prioritize your vulnerabilities patches. Why? Nowadays, according to Microsoft’s 2022 Digital Defense Report, vulnerabilities are exploited just 14 days after they’ve been identified. This means that waiting to include a new vulnerability patch that has just been announced in your next month’s patch day isn’t an option anymore. Want to be the best? Join the 29% of organizations that are deploying patches within three days of their availability.
26. Limit the Number of Third-Party Components (and Regularly Scan and Update Them)
I know, in today’s digital world when 70-90% of software products include open-source components or libraries, finding a developer that creates an application from scratch is like finding a white deer. However, you can limit the number of third-party components you use, and regularly scan them using software composition analysis (SCA) tools. They’ll help you keep on top of vulnerabilities, version updates, and more.
Sunday is nearly gone, and our seven application security issues and solutions list is complete. Next time you go to work, why don’t you start the day under the sign of web application security by testing one or more solutions proposed in this article?
And don’t forget to back up your data and systems regularly!
Final Thoughts on 26 Ways to Improve Your Web Application Security
2023 is poised to be another tough year for organizations, particularly from a web application security perspective. There have been plenty of sophisticated hacking attacks, new malware, and new vulnerabilities that have come to light in 2022. But as the saying goes: when the going gets tough, the tough get going. This is the perfect time to start preparing for the challenges ahead and go into the new year with:
- More secure web applications, and
- Lower chances of crippling security incidents.
Among all the options out there, we’ve provided you some of the more effective measures to implement. They surely won’t avert all the issues and attacks; however, they’ll help you build a powerful defense against cybercriminals.
But remember, the threat landscape is continuously evolving. Even if creating a web application comes easy to you, keeping it secure is another story. Keep your eyes open at all times and start tackling your web application security issues now.


