11 Database Security Best Practices You Should Know
Are you ready for a year when multifactor authentication may become ineffective and attackers will adopt new hacking vectors like cloud-aware ransomware to get to your data? Learn how to enhance your database security now to stay ahead of cyber threats
January isn’t just the first month of the year. It’s the time when organizations start planning their security strategy for the months ahead, and the cybersecurity sector’s news fills in with predictions about the top threats for 2023. Acronis forecasts that the average cost of a data breach will reach $5 million in 2023. That’s 13% more than the average cost reported by IBM in 2022.
How are you going to protect your organization from data breaches, in a world where even poorly protected databases are easily compromised by bored students? We’re coming to your rescue! This article will cover 11 of the top database security best practices. Learn how to improve your database security to protect your most valuable assets: sensitive data.
Top 11 Database Security Best Practices
Do you remember Davy Jones, the cursed and ruthless captain of the Flying Dutchman in the Pirates of the Caribbean movie franchise? In the second movie in the series (one of my favorites, I must admit), Jones keeps his most precious thing, his own heart, locked away in a chest hidden in a secret, guarded location. But the security of the chest quickly becomes compromised by Jack Sparrow, marking the inevitable end of Davy Jones.
Want to avoid your organization’s treasure chests (databases) becoming the next victims of today’s cyber pirates? Check our summary table or read on for more details!
| Database Security Best Practices | Examples | Why You Should Do It |
|---|---|---|
| 1. Segregate Your Database Servers |
|
|
| 2. Use Firewalls and Inspection Mechanisms |
|
|
| 3. Add a Proxy Server |
|
|
| 4. Update All Software and Applications Regularly |
|
|
| 5. Be Proactive and Use Real-Time (or Nearly Real-Time) Database Monitoring |
|
|
| 6. Back Up Your Data and Test Your Backups |
|
|
| 7. Use Encryption to Protect Data at Rest and in Transit |
|
|
| 8. Say No to Default Ports (and Monitor Them) |
|
|
| 9. Secure User Access |
|
|
| 10. Don’t Forget About Physical Database Security |
|
|
| 11. Hire Someone to “Attack” Your Databases |
|
|
1. Segregate Your Database Servers
Is your organization still keeping databases on the same server that hosts your website? It’s time to put a dedicated database server on your 2023 shopping list. Why? Let me give you a few hints in this first item on our list of database security best practices:
- The same key can open more than one door. If your web server’s admin account is hacked, the attacker will have free access to your databases, too.
- One size doesn’t fit all. In other words, the defense measures you take to protect your web server might not work equally well for your databases.
- Not all databases need to communicate. Your web server will probably need to communicate with different resources for specific tasks. Your databases might not need that at all (e.g., local database) or, if they do, they might just need it for one specific task. Keep the two separate and you’ll be able to limit your database permissions to the minimum (i.e., the principle of the least privilege — more on that later), thus, dramatically reducing the risk of exploits by attackers. All of this can be done without affecting your website performance and operations.
- Keep test, development and production environments separated. Set up a separate database for development and one for testing. It’ll let you play with new ideas and features without the risk of messing up your production database by introducing new bugs or vulnerabilities.
2. Use Firewalls
With a firewall, you’ll be able to deny any traffic to unwanted or suspicious IPs and filter out all unused ports. That’s already good news, but just one firewall isn’t going to be enough to protect your database from all attacks. Don’t be stingy! Add more firewalls to your database. Make sure you install and configure a:
- Packet filtering firewall. Also called static filtering, it sits at the network layer. It checks and filters all incoming and outgoing packets based on pre-set rules and policies protecting your database against malware and malicious traffic.
- Stateful packet inspection (i.e., dynamic packet filtering). It continuously monitors active connections and establishes which packets of data are allowed to go through the firewall. It’s faster than a proxy server firewall (more on that in a minute) as it memorizes the characteristics of each connection.
- Proxy server firewall. It’ll check your network traffic in a much more detailed manner to protect your databases from malware and malicious traffic. It uses deep packet inspection techniques (DPI). It’s considered one of the most secure types of firewalls. It has its own IP address that avoids internal networks making direct connections with the internet.
Why? Because they’ll:
- Keep your database safe from SQL injections. If a compromised web application has direct access to your database, so will the attacker. He could inject a malicious SQL query directly into the application, access your database and help himself with all the data in it. This can’t happen if you have additional firewalls and filters installed.
- Protect your database from malware. With so many inspections, checkpoints, and layers of security, it’ll be very difficult for malware or any suspicious activity to bypass such a granular control.
3. Add an HTTPS Proxy Server
In the Middle Ages, many cities were surrounded by high walls to protect them from the attacks of enemies. (Think of this like the firewall we just discussed). Each entrance was guarded by a gatekeeper, who was in charge of vetting and prohibiting access to any unwelcome person. That’s, essentially, what a hypertext transfer protocol secure (HTTPS) proxy server does.
An HTTPS proxy server acts as a mediator and prevents unauthorized user access to a database by:
- Authenticating the users, and
- Connecting to the database on the users’ behalf by creating an encrypted connection using a secure socket layer/transport layer security (SSL/TLS) certificate.
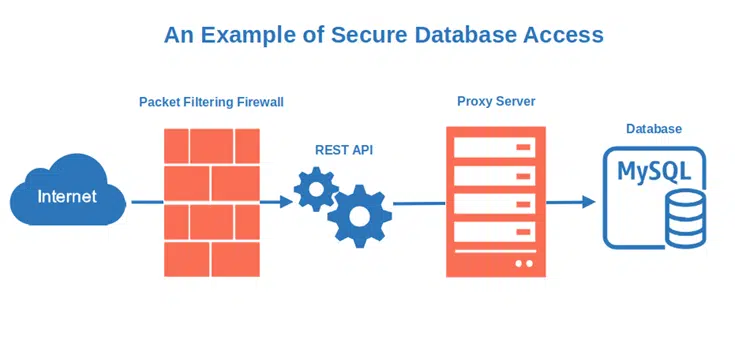
Why is it important? It:
- Adds another layer of security between the client and the database. This means that if the attacker wants to get to your database, he’ll have to carve his way through the proxy server first.
- Protects your database against DDoS and man-in-the-middle attacks. In case of a distributed denial of service (DDoS) attack, your proxy server will act as a sponge. It’ll absorb some of the connection attempts, preventing your database server from being overloaded. In the case of a man-in-the-middle attack, the encrypted connection will make communication interceptions by a cybercriminal nearly impossible. No more snooping!
- Shields your customers’ sensitive information. Does your organization handle sensitive data like credit card numbers, payment details, or personal information? By using a proxy server, you’ll ensure that the data traveling through the network to and from your database will be secure thanks to encryption.
4. Update All Software and Applications Regularly
Could you swear that all your organization’s websites, applications, software, and components are up to date? Taking into account the humongous number of dependencies (e.g., third-party libraries, open-source components) and vulnerabilities, I think not many organizations can. But you can do your best by:
- Regularly updating everything. This includes plug-ins, widgets, and third-party apps and components. Ideally, you’ll want to use software that’s digitally signed by the developer or publisher using a code signing certificate. This way, you can know with certainty that the software is authentic and hasn’t been altered by a malicious party since it was signed.
- Using a patch management tool while also manually checking for vulnerabilities. Creating a software bill of materials (SBOM – an inventory of your software components) will also help you avoid relying on automatic tools only.
- Keeping yourself informed about the latest vulnerabilities and patches. You can do this through newsletters and feeders.
- Staying away from software or plug-ins that aren’t regularly updated by the developer (i.e., abandoned software). Why? According to the 2022 Open Source Security and Risk (OSSRA) report, 81% of codebases that had security operational risk assessments contained at least one vulnerability. To make things even more alarming, 85% of the same codebases include open-source components that haven’t been updated for more than four years. Do you use WordPress? To date, WPScan has recorded more than 38,000 vulnerabilities. 92% of them are related to plugins and 52 of those vulnerabilities have been identified in the first 10 days of January 2023. Crazy, right?
I get it — keeping everything up to date isn’t easy at all though, so with so many vulnerabilities around, why should you bother? There are several critical reasons:
- Avoid leaving open doors to attackers. A vulnerable or unpatched application is a wonderful opportunity for an attacker to easily get into your network and other IT systems. It doesn’t even have to be related to your database. Once the attacker gets into your network, he’ll quickly find his way to it.
- Protect your organization from data breaches. With 47% of small businesses in the U.S. being the targets of at least one cyberattack in 2022, keeping your software and application updated will help you reduce the risk of data breaches. Don’t forget that attackers actively look for vulnerabilities, even old ones.
- Shield your organization from malware. Much like how viruses in nature are more successful at overtaking the weakest organisms, the same can be said about malware in the digital world. Keep your software and applications up to date and it’ll be much more difficult for your internal systems and network to catch a virus.
So, from now on, don’t be shy. Patch early and patch as often as you can!
5. Be Proactive and Use Real-Time (Or Nearly Real-Time) Database Monitoring
The more you monitor, the less you miss (and risk). Some may think that real-time (or nearly real time) monitoring costs a lot of money, but bear with me because that isn’t always the case.
When I started my career as a security application engineer, the department I was working for was monitoring the organization’s systems manually. This means that we were spending most of our days sitting in front of monitors, scanning thousands of graphics (e.g., login attempts, network activities), and hunting for anomalies. As you can imagine, that wasn’t fun. It was often chaotic and unproductive, and it certainly wasn’t real-time. As a result, security incidents were frequent and discovered too late.
One day, a new boss came and brought with him a more than welcomed wind of change. A few months later, we built the first automatic alerts in our systems based on simple rules were built using free monitoring software. We then:
- Kept on building other rules and algorithms that were increasingly sophisticated. This helped us to dramatically reduce our anomalies detection and response time
- Started using the support of machine learning to reduce the number of false positives.
- Set up escalation processes and periodic log reviews to respond more quickly and keep a closer eye on things.
In a few months, the number of security incidents went down, while our level of satisfaction and the amount of time dedicated to projects skyrocketed. See? When there’s a will, there’s a way. You don’t need to break the bank to set up a nearly real-time database monitoring. The benefits?
- Reduce the number of security incidents. Extending the monitoring surface (thanks to automation) and shifting from a reactive to a proactive approach can dramatically decrease the number of security incidents you experience.
- Increased productivity. Your teams will have more time to dedicate to important tasks, projects, and (why not?) training, instead of spending their days staring at monitors. Thus, their mood will also improve.
- Faster response time to potential attacks. The sooner you notice anomalies, the sooner you’ll be able to implement remediation measures to close the breach or potential vulnerability.
6. Back Up Your Data and Test It
I don’t know you, but I’m a backup freak. I always back up my key data once a day and keep several backup copies in different places, just in case. To play safe:
- Back up your database regularly. Don’t forget to encrypt it, store it on a dedicated server, and keep the decryption key separately.
- Create a copy of your backup on the cloud and encrypt it. Why? Because if your server backup is compromised or damaged, you’ll still be able to count on your cloud backup. It’ll be like a second insurance. 50% of organizations interviewed by Electric already do it.
- Test your backup restoring procedures. Back-ups can get corrupted, and the restoration process may fail. Make sure you test it regularly to avoid bad surprises.
Incidents happen all the time. Having a backup will ensure that you’ll still be able to recover your sensitive data even if your database server fails, data are deleted by mistake (yes, it can happen, too), or it gets compromised by an attacker. It’s important, and that’s why we’ve included data backups and testing on our list of database security best practices.
7. Use Data Encryption at Rest and In Transit
Data encryption isn’t only good for backups. It’s also a great way to keep your data safe while in transit. Imagine, for a moment, an attacker has managed to get through all the layers of security that we’ve mentioned up until now. All sensitive data stored in your database are in their hands. What can you do? This is where data encryption comes to your rescue:
- Require SSL/TLS encryption for all database connections. Your data in transit will be encrypted, thus safer. Check out this interesting AWS example on how to use SSL/TLS to encrypt a connection to a database instance, and learn how to correctly manage your TLS certificates.
- Encrypt any disk containing sensitive data. It’ll protect your data in case the disk is lost, stolen, or damaged. As with backup, make sure the decryption key is stored separately.
- Use column-level encryption. This method of encryption is commonly used for databases as it gives you great flexibility. You can define different encryption keys for each column to further limit access to certain data. SQL servers, Microsoft Azure, and Amazon RDS support it too.
What are the benefits of encrypting your data at rest (i.e., stored) and in transit (i.e., transmitted on the network from point A to point B)?
- Your data will be safe even if your database is hacked. Yup! If encrypted, even if your database is hacked and the attacker gets hold of your data, they’ll still have to find the decryption key (that, ideally, you’ve stored elsewhere as previously suggested) to use them.
- SSL/TLS encryption will keep you safe from snooping. By installing an SSL/TLS certificate, HTTPS will be enabled and the communication between the database server and the client will be encrypted. How? Through asymmetric encryption. A public key is used to encrypt the information and a private key is used to decrypt it. During transmission, the cybercriminal will only see a sequence of gibberish nonsense, and your data will be safe.
- It’ll help you comply with privacy and security regulations. Are you storing in your database (even temporarily) customers’ payment data? The Payment Card Industry Data Security Standard (PCI DSS) requires you to encrypt those data in transfer and at rest. Do you store or handle sensitive personal information? Encryption and SSL/TLS certificates are among the requirement of the EU General Data Protection Regulation (GDPR).
8. Say No to Default Ports (and Monitor Them)
Let’s say you’re a hacker and you want to hack my database server. What would be one of the first things you’d check? I bet you’d go for the default ports. Why? Because they’re often overlooked, used as standard ports, and easy to exploit with brute force attacks. There are even tables available on the internet listing the most common database platform ports.
To avoid these risks:
- Don’t use default ports. Configure your database server to use specific ports instead than the default ones. Is your SQL server using port 1433? That’s the default port! Time to change it with another one. To play safe, check IANA’s list to avoid assigning the wrong port number.
- Ensure all unused ports are closed. Why should you keep ports open if you don’t use them? Shut the door in the face of attackers to keep your database more secure.
- Monitor port activities. Monitor all your ports for unusual traffic or suspicious activities. Tools like Nagios, PRTG, and many others can automate this task and provide alerts. Don’t forget to include in your monitoring also closed ports. What if they open unexpectedly without you noticing?
Why should you do it?
- Protect your database from brute-force attacks. Ransomware malware often leverages this type of attack, as observed recently in a PonyFinal ransomware campaign.
- Default ports are easier to find and exploit. Standard ports are public and listed everywhere on the internet. How easy do you think it’ll be for a hacker to find the right one?
- Monitoring will help you detect intrusions faster. With more than 65,000 ports available, no network administrator can do without a monitoring tool. Want to be able to detect suspicious port scanning activities? A monitoring tool can do that. Need to investigate an incident? The logs of your monitoring tool can help you identify the entry point exploited by the little buggers.
9. Secure User Access
Did you know that according to the latest Verizon Data Breaches Investigations Report (DBIR), the human element (e.g., error, misuse, and social attacks) is involved in 82% of data breaches? How do you protect your databases from that?
- Enforce the principle of the least privilege. Users (and admins) should get access to only what they need, when they need it, nothing more. Snowden succeeded in breaching the National Security Agency (NSA) by using digital certificates and keys generated by himself. How? It was easy — his admin permissions allowed him to do so. OK, he also had access to the network and super-secret files, but see what can happen by giving too much trust?
- Use a client authentication certificate. This is a digital certificate that’s issued by a trusted certification authority (CA) and includes a digital signature. It’s used to authenticate the client during an SSL/TLS handshake to ensure that the connecting party is who they claim to be.
- Utilize strong passwords (and change them often). Password123 isn’t good enough, even if it has more than eight characters. Want a strong password? Follow the National Institute of Standards and Technology’s (NIST) password guidelines and apply them to all your passwords. Remember that attackers can get to your database from anywhere and passwords are like yogurt: they’ve got a short shelf-life.
- Store only the hashes of your passwords. Are you storing your passwords on a database as plaintext or encrypted? Wrong either way. Hash your passwords (don’t forget to add some salt and pepper) and use a strong hashing algorithm. Once done, then you’ll only want to save and store the resulting salted password hashes. If you really want to up your security game, then you’ll want to pepper your passwords as well before hashing and storing the hash values.
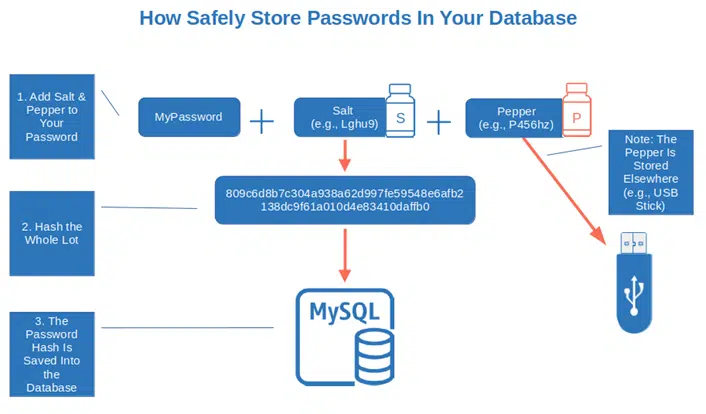
- Review all accesses regularly and deactivate unused accounts. Nowadays people come and go. They change roles, responsibilities, and organizations. Set up an access review process and ensure all unused accounts are immediately deactivated.
- Avoid shared passwords. When I was very young and living abroad, I worked as a cashier in a shop. Many of my colleagues were also my friends. We often hung out together and we trusted each other. Maybe too much, as we often shared our passwords. We did this until, one day, I found out that one of them used my passcode to access my till and steal money from the shop under my name. Luckily for me, he was caught. It was a shock, but I’ve never shared passwords (or used others’ shared passwords) again since then.
- Automatically lock accounts after too many failed login attempts. This is a classic, easy to implement (you just need a simple rule), and very effective. Do you remember when we talked about my experience with real-time database monitoring? This is one of the first rules we built and it did work very well.
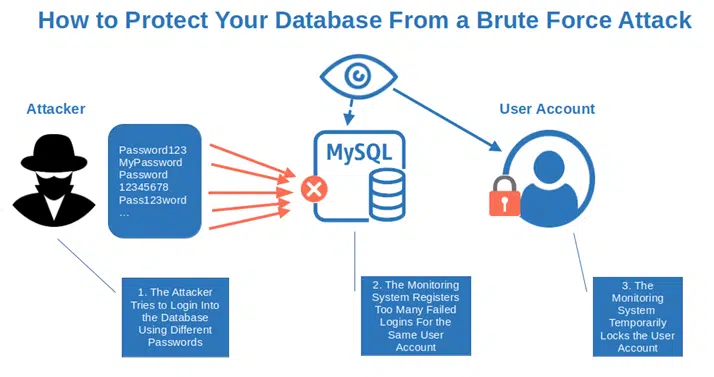
Wondering why you should do all this?
- Protect your database from insider threats. Mistakes happen all the time. Implementing the solutions suggested above will protect your data (and your users, too) from involuntary mistakes and malicious abuse of database privileges.
- A digital certificate can save your bacon. Let’s say that a highly skilled cybercriminal worked out your database administrator’s user ID and password. The attacker tries to access the database by typing the stolen credentials. However, as they don’t have the client certificate associated to that particular user ID, the connection to the database will be refused. How cool is that?
- In case of a breach, you’ll limit the resulting damage. Remember Edward Snowden’s example. Things could have gone differently and the damage could have been contained if he wouldn’t have access to all those systems, files, and permissions. No matter how much you trust your colleague and/or employees, the more boundaries and checks you set up, the smaller will be the damage in case of a breach.
10. Don’t Forget About Physical Database Security
Even if 58% of organizations interviewed by Fortinet in March 2022 are forecasted to run more than 50% of their workload in the cloud, many databases are still stored on physical servers. How do you protect them physically?
- Install locks, security cameras, and hire security guards. Just like in the 1980s, but with today’s technology. If not properly protected, your servers and data centers are vulnerable to external and internal attacks in the same way as your software and cloud-based resources.
- Keep your database server physically separated from others. We’ve already talked about digital separation. The same principle applies to physical servers.
- Record and monitor all accesses. When I was working as a cash supervisor, I had to note down and sign a paper every time I needed to get access to the cash locked up in the shop safe. Do something similar with your data center accesses to minimize the chances of breaches.
Is physical security so important? Well, yes. It helps you:
- Protect your organization and database from malware. If a cybercriminal gets physical access to your server, they can inject malware to get remote access to it, steal data or corrupt them. All they need is a USB stick with a virus on it.
- Keep your database safe in case your web server is compromised. If your database and your web server are running on the same machine, once one is compromised, the other will be, too. Shared servers can be cheaper, but they’re not the safest solution for critical data.
- Reduce the likelihood of cybersecurity threats. Monitoring and restricting physical access will make it more difficult for a malicious third party to enter the premises. In one of the companies I worked for, they were even used to record and compare the registered weight of the employee who wanted to enter the data center before granting access. Personally, I think it was a bit too much, but it was pretty efficient.
11. Hire Someone to “Attack” Your Database
Until now, we’ve populated our list by trying to think like a hacker. To complete our collection of the most effective database security best practices, it’s time to act as a hacker — or, at least, get someone to act like one. Therefore:
- Run regular pen tests. The best way to do it is by hiring somebody outside your organization. A white hat (i.e., ethical hacker) will attempt to hack your database and help you identify vulnerabilities and flaws before a real hacker exploits them.
- Use vulnerability scanning tools. These tools, also recommended by NIST, can be really helpful to find database weaknesses. There are many available on the internet and some of them, like Scuba and Nmap, are free to use.
- Regularly audit your database. Ensure your data are adequately protected by auditing your database activities (e.g., modifications to roles, permissions, and data, login attempts). If you’ve followed one of our database security best practices suggestions and installed some monitoring tools, auditing your database will be even easier.
Why should you invest some time in auditing and pen-testing your database?
- Get ready for official audits. Frequently auditing all databases storing sensitive information will help you verify and prove to external auditors that you comply with regulations like the Health Insurance and Portability and Accountability Act (HIPAA). and the Payment Card Industry Data Security Standards (PCI DSS).
- Fulfill one of the most important requirements of the PCI DSS. Did you know that the latest version of the Payment Card Industry Data Security Standards (PCI DSS v4.0 – requirement 11.4) provides detailed information about when and how often an organization should perform pen-tests to be PCI DSS compliant? It even offers guidance on how to choose a third party to run those tests.
- Fix and patch vulnerabilities before the worst happens. How do you know that the last security measures you put in place on your database are strong enough to protect your database from attacks and that are addressing all the new vulnerabilities announced? If you don’t audit and pen-test your databases regularly you can’t.
This brings us to the end of our list of 11 database security best practices. Are you still wondering why you should follow them? Let me briefly answer the question.
Database Security: Why Should You Do It?
In addition to the reasons we’ve already listed, you should also consider that these database security best practices will also:
- Help you avoid fines for privacy and security legislation non-compliance,
- Avoid you losing money, and reputation by protecting you from potential downtime caused by a ransomware attack, breach, or other security incidents,
- Shield you from potential lawsuits caused by data breaches.
So, what do you think? Are you going to be the next digital Davy Jones and let cyber pirates steal your most precious assets, or are you going to properly protect them?
Final Thoughts On 11 Database Security Best Practices
To quote Tim Berners-Lee, the inventor of the World Wide Web: “Data is a precious thing and will last longer than the systems themselves.” Cybercriminals know this truth very well and that’s why databases are a prime target for them. From customers’ data to intellectual property, they’re all invaluable treasures.
Encrypting your data, monitoring your database(s), and securing access are just a few of the database security best practices that’ll help you protect your digital assets against cyber attacks and data breaches. And three of the primary reasons we must up our database security game is to:
- Protect our organizations’ reputations and nurture customer trust
- Reduce the risks of cyber attacks and data breaches, and
- Comply with privacy and security regulations.
By the way, once implemented, don’t forget to train your employees about database security. You’ll keep your customers happy and your data safe.


