How to Digitally Sign Executable Files and Why It’s Important
AV-TEST reports registering 450,000+ new malware programs and potentially unwanted applications (PUAs) every day. Digitally signing executable files helps you protect your application’s integrity and establish trust
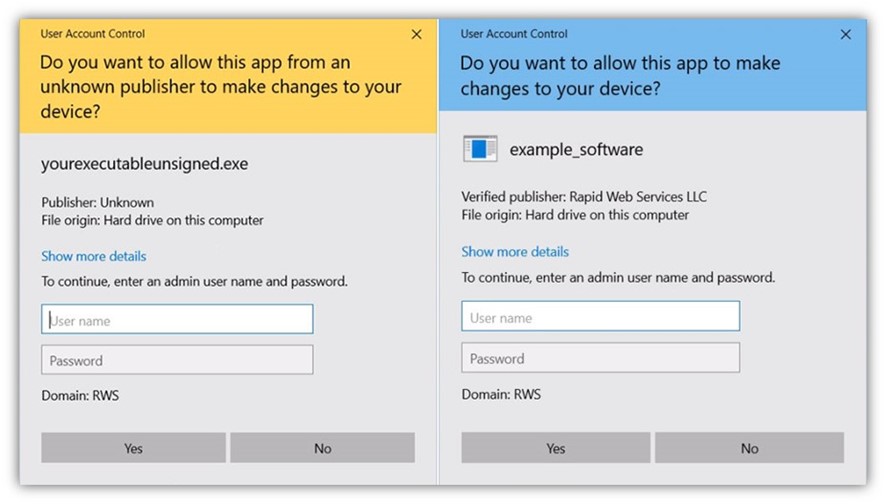
According to 2020 data from Statista, one of the most common ways people receive malware is through executable files. So, it’s reasonable to ask questions like: ‘Are .exe files safe to install?’ For instance, a user may receive a Windows User Account Control (UAC) warning message if they run an unsigned executable file because the file isn’t trusted by Windows operating systems (OSes).
Usually, users face these warning messages if someone tries installing an unsigned (i.e., untrusted) software or application. Why? Windows operating systems regard unsigned executables and scripts as unsafe and potentially malicious files because, well, they could be. (Better safe than sorry, right?)
So, how can you ensure your executables can start building trust with Windows operating systems over time? You’ll need to digitally sign your executable files using a standard or extended validation (EV) code signing certificate.
What Is an Executable Signing Certificate?
Executable signing certificates, commonly referred to as code signing certificates, are digital files you can use to digitally sign executable files (.exe files). The code signing certificate uses a cryptographic hash that validates the executable file’s integrity and authenticity.
Executable code signing certificates are issued by reputable certificate authorities (CAs) like Sectigo and DigiCert. These certificates allow you to apply a digital signature that verifies the author’s identity and helps to confirm that the digitally signed executables are from a legitimate organization — not any malicious cybercrooks.
Executable signing certificates identify the software publisher to the user and their device’s operating system. A trusted publisher is one whose certificate is installed in the certificate store of trusted publishers. You can’t be a trusted publisher without a certificate!
Here is a side-by-side comparison of two software examples:
Save Up to 21% on a Windows Code Signing Certificate
Give users a reason to trust your Windows apps by preventing “Unknown Publisher” warnings. You can digitally sign unlimited apps for as little as $211.46/year.
Standard vs EV Executable Code Signing Certificates
Executable signing certificates are available with standard validation (sometimes called organization validation, or OV) and extended validation (EV). Both types of code signing certificates require you to store your cryptographic key and certificate on secure hardware, As such, they’re typically issued with a secure USB device by default from the certification authority (CA). This serves as a form of two-factor authentication (2FA).
So, what’s the difference between standard and EV code signing certificates?
- A standard code signing certificate will display your verified individual or organizational information in Windows User Account Control (UAC) pop-ups. This certificate has less stringent validation requirements than its EV counterpart and costs less as well.
- An EV code signing certificate requires a higher level of validation than a standard certificate. Up until early 2024, it was automatically trusted by Window operating systems and browsers and would eliminate the Microsoft SmartScreen warning altogether. However, this is no longer the case, as Microsoft now treats OV and EV certificates virtually the same.
Both types of certificates will display your verified organizational identity information and help build trust over time with Windows operating systems.
Benefits of Signing Executable Files With a Publicly Trusted Code Signing Certificate
It’s challenging to get users to trust any newly created executable file. A code signing certificate that’s signed by a trusted public certificate authority (CA) is more trustworthy than one you’ve signed yourself. This helps improve your reputation as the executable creator. Some of the benefits of signing executable files using EV code signing certificates are:
- Promotes trust and identity. Using a code signing certificate verifies and asserts your identity as the creator of the executable file. This is particularly beneficial when distributing and sharing signed software applications on multiple platforms like third-party software publishing websites.
- Ensures file integrity. Digitally signing your software offers proof that the executable file hasn’t been meddled or tampered with since you signed it.
Save Up to 27% on a Standard Code Signing Certificate
Assert your organization’s verified digital identity to increase trust in your software and updates. Boost your sales and download rates for as little as $195.00/year (with a 3-year certificate).
How to Sign Executable Files Using a Code Signing Certificate
Before you can digitally sign your executable file using either a standard or EV code signing certificate, you’ll first need to install your client authentication software onto the device that you plan to sign software on. For DigiCert code signing certificate users, that software is called SafeNet.
SafeNet Authentication Client is desktop software that allows you to access and manage your code signing certificates and change the password for your tokens.
Below are the steps to digitally sign executables. But, before you start digitally signing executable files, you should:
- Set up SafeNet and configure your hardware security token (for DigiCert users). NOTE: The setup of your token is handled for you for Sectigo code signing certificates.
- Use a computer that has Microsoft Windows OS installed.
- Install SignTool as part of your Windows Development Kit on your computer.
Check out our other article for more information about how to set up your code signing certificate secure USB token. This provides step-by-step directions on how to set up the token and how to generate and store your keys.
Steps to Sign Executable Files
Once you complete the above steps, follow these instructions to digitally sign your executable files:
- Insert the USB token that you got from your CA into your system.
- Open the SafeNet Client software that you installed in your system. (NOTE: You can use this tool to change the default password that was assigned for the secure hardware token that was issued with your code signing certificate.)
- Open the command-line tool Windows Command Prompt (CMD) to access SignTool.
- Use the following command to digitally sign and timestamp your executable using SHA-256.
signtool sign /tr http://<timestamp-certificate-authority-server>.com /td sha256 /fd sha256 /a "c:\path\file_you_wish_to_sign.exe"Note: Be sure to change the information to match your CA’s timestamp server address (e.g., http://timestamp.digicert.com for DigiCert certificates) and the file path to your executable file.
- You’ll be asked to enter the certificate token’s password once you enter the above command.
- Once you enter the token password, the executable file will be signed.
Related Resources:
Verify Your Executable Is Properly Signed
Once you’ve signed your executable, you should verify the signature before making it available to end-users:
- Open the folder where you’ve saved your signed executable file.
- Select and right-click that executable file and click on Properties.
- If your executable file is signed correctly, you’ll see the code signing certificate details on the Digital Signatures tab.
Closing Thoughts
Dangerous malware infects many executable files. Microsoft’s operating system takes every possible step to make users aware of its dangers, for instance, by displaying Microsoft warning messages if anyone tries to install unsigned or suspicious executables.
If you want users to trust your executable files, you should sign them using a publicly trusted code signing certificate from a respected CA like Sectigo or DigiCert. This way:


