How to Check an MD5 Checksum
Discover one of the most effective ways to check the integrity of signed executables downloaded from the internet. Learn how to check MD5 checksums and protect your device from harmful downloads
Infected executables are one of the most common malware file types chosen by attackers. These malicious files are often disguised as genuine software updates to trick you into downloading and running their harmful applications to wreak havoc on your device and cost a great deal to your organization. To give you a better idea, Sophos’ State of Ransomware 2021 report revealed that the average total cost of recovery from a ransomware attack went up from $761,106 in 2020 to $1.85 million in 2021.
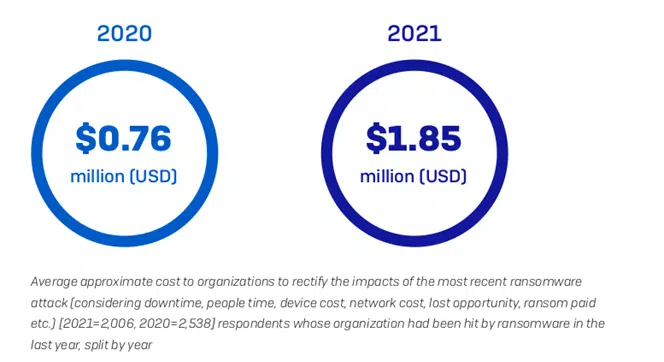
In such a dangerous environment, checking that a downloaded file is authentic and hasn’t been modified has become crucial to the safety and security of your organization and its data.
In our first article of this series, you learned that checksums are special strings of data that can help you to truly accomplish this comparison and validation. You then learned how to check a file checksum to verify the integrity of a file. In this last article of the series, we’ll walk you through the process of generating an MD5 checksum to check the veracity of a signed executable’ signature.
Why Checking an Exe’s MD5 Checksum Matters, Even if the File Is Signed
Executables signed with a code signing certificate are already more secure than unsigned ones. However, in cybersecurity, you can never be too cautious. This is why, in addition to checking the code signing certificate, if a checksum is displayed alongside the .exe file, you should also compare it with the one you’ll generate after the download to check if they match.
How to Check MD5 Checksum of a Signed Executable in 5 Easy Steps
Even if you can always use a third-party software to generate MD5 checksums, using Window’s command prompt will avoid you the hassle of installing yet another specific tool. This process is easy, fast, and works like a charm.
1. Download the Signed Executable
To show you how to check the MD5 of a signed downloaded executable file, we’ll download the last version of KeePass installer for Windows. KeePass is a well-known free and open source password manager.
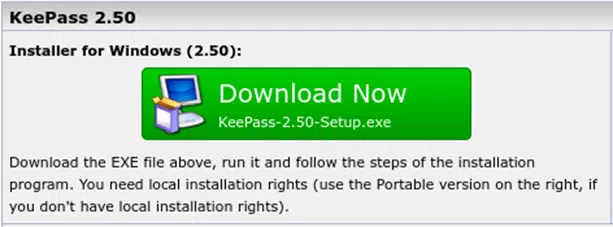
At the bottom of the download page, there’s a link that takes you to the signature and checksum details info that you’ll need in order to verify the executable’s integrity.
2. Open the Windows Command Prompt Tool
- Now that you have all the information, open the Window’s command prompt by clicking the Start button.
- Type cmd in the run bar.
- Select the Run as Administrator
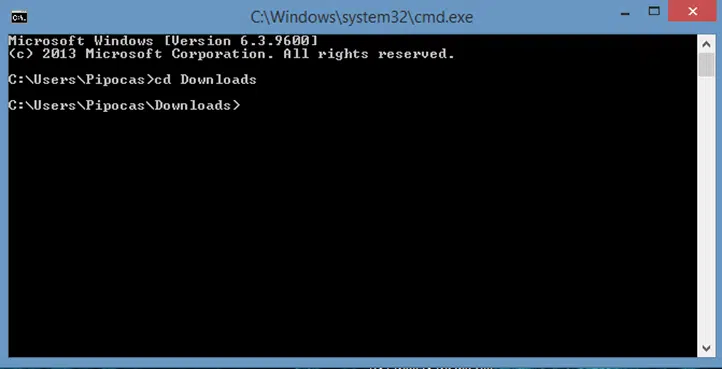
3. Navigate to the Directory Where You Saved the .Exe
- Use the cd (change directory) command to go to the folder where the downloaded KeePass-2.50-Setup.exe is saved.
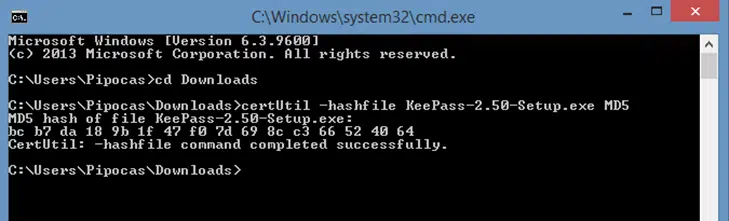
4. Generate the MD5 Checksum Using the CertUtil Command
- Type certUtil -hashfile followed by the filename (in this case, KeePass-2.50-Setup.exe) and MD5. It would look like this: certUtil -hashfile KeePass-2.50-Stepup.exe MD5.
- Press Enter.
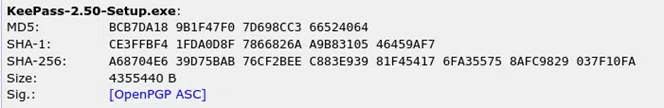
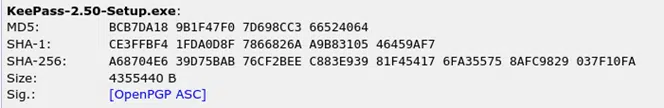
This will generate the following checksum:
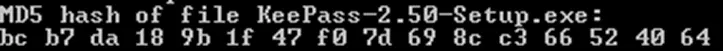
5. Compare the Two Checksums
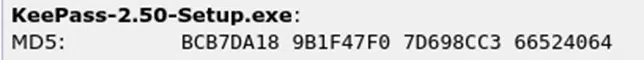
Check that the returned value of the checksum you generated matches with the original MD5 checksum displayed on the download webpage. If they match, the .exe has not been modified and you can install your KeePass without issues. If they don’t, there’s something wrong and you should be careful. The file may be infected, or something may have downloaded incorrectly. Regardless of the reason, you shouldn’t trust the file.
Let’s take a quick look at the two checksums for comparison:
How to Generate an MD5 Checksum Using Windows PowerShell
To make it even easier, if you have Windows 8.1 or Windows 10, you can also use PowerShell to generate your checksum as described below:
1. Download the Signed Executable
Let’s take the same .exe file as an example.
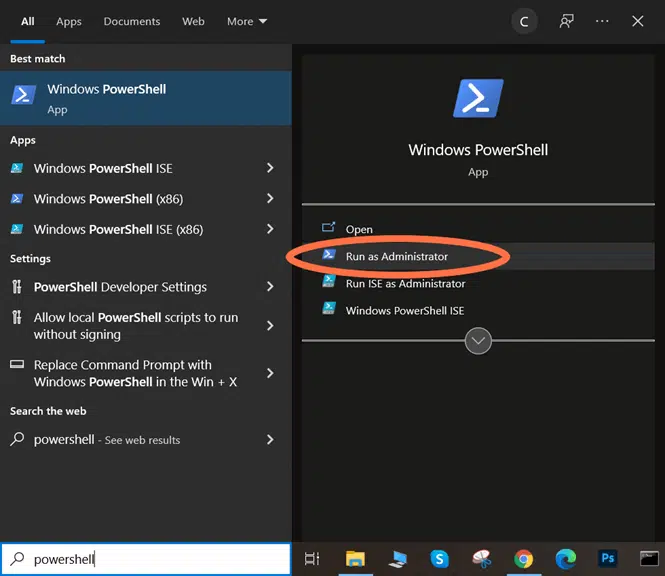
2. Open a PowerShell Window
- In Windows 10, click on the search icon near the Start
- Type powershell.
- Select Run as Administrator.
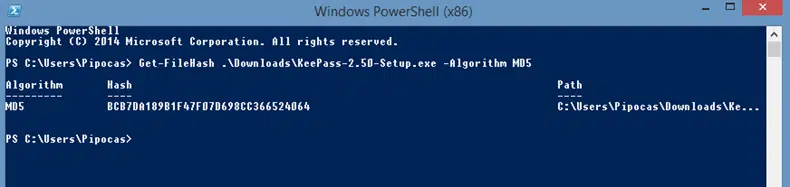
3. Generate the MD5 Checksum Using the Get-FileHash Command
- Type Get-FileHash followed by the path where the downloaded .exe is located (which should start with a period) and –Algorithm MD5. The command will look like this: Get-FileHash .\Downloads\KeePass-2.50-Setup.exe –Algorithm MD5.
- Press Enter.
This will generate the checksum.
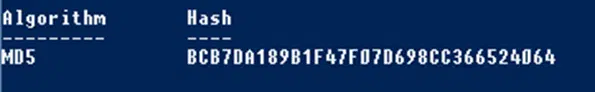
4. Compare the Two Checksums
Now you’re ready to compare the generated MD5 checksum with the original one to ensure they match:
There we go — no sweat! You’ve learned two easy ways to generate an MD5 checksum of an executable with minimal effort.
Final Thoughts on How to Check an MD5 Checksum
I hope these three articles on checksums helped you to learn a new method to protect you and your organization from malware and installation errors. While organizations have already implemented good security practices, attackers continuously develop new ways to infiltrate genuine files with malicious codes.
Even if there’s no silver bullet in IT security, understanding how to protect your devices and data at the fullest extent and with the right tools can make a difference. Including checksums in your security best practices is a way to perform a more in-depth security check, helping you and your organization to mitigate risks and stay ahead of downloading threats.
Don’t take unnecessary risks — leverage the power of checksums to keep your organization and its data secure!


