How to Become a Verified Publisher with Microsoft to Sign Apps & Drivers
Not sure how to become a verified publisher with Microsoft? No worries — we’ll break down what a Microsoft-verified publisher is and how you can start publishing Windows-trusted desktop applications and drivers in no time.
Are you looking to publish Windows-trusted desktop software, kernel-mode updates, or driver packages? If so, it’s essential to know that it requires you to be a verified publisher with Microsoft.
Contrary to what you may think, becoming a Microsoft-verified publisher isn’t a mystical process shrouded in mystery. But to make things easy, we’ll walk you through how to become a verified publisher with Microsoft so you can start signing these assets right away.
With that in mind, this article will cover:
- What a verified publisher is,
- How to become a verified publisher with Microsoft so you can start signing Windows apps and drivers, and
- Why becoming a verified publisher matters to your organization, customers, and digital products.
What It Means to Be a Microsoft-Verified Publisher
If you’re searching for a topic like “how to become a verified publisher with Microsoft,” it’s likely that you already know what a verified publisher is and just want to get the ball rolling on becoming one. (If so, just skip to the next section on signing Windows apps and signing Windows drivers.) But just in case this is a new topic for you, we thought it would be helpful to quickly cover what it entails.
A Microsoft-verified publisher is someone whose software products and code are trusted by Microsoft operating systems and browsers. To achieve this trust:
- The software publisher must undergo a digital identity verification process called code signing validation. This process involves a publicly trusted certification authority (CA) checking your official identifying records and performing other validation checks (phone calls, video calls, etc.).
- The software or code must be digitally signed using a publicly trusted code signing certificate.
But not all code signing certificates are equal. Some have different verification requirements based on their validation level. For example:
- Individual validation or standard validation code signing certificates require verifying specific personal and organizational information.
- Extended validation (EV) code signing certificates have more stringent requirements.
How to Become a Verified Publisher With Microsoft to Sign Windows Applications
Knowing how to become a verified publisher with Microsoft so you can digitally sign desktop software is a pretty straightforward process. Essentially, it entails getting a publicly trusted code signing certificate and rolling with it. (You can use either a standard or EV code signing certificate for this task.) But let’s look at this process a little more closely:
- Get a code signing certificate. You’ll need to purchase one of these digital certificates from a publicly trusted certificate provider (such as DigiCert or Sectigo).
- Complete the validation process. This process allows the CA to verify you’re you (and not an imposter) and/or that your organization is legitimate.
- Wait for your code signing secure USB token to arrive in the mail. We get it — waiting is rarely fun. But be patient, padawan; your time will come. Soon, you’ll be able to start digitally signing Windows apps to your heart’s content.
- Set up your secure hardware. This process entails installing client authentication software and setting up a token password. Check out our other resource to learn more about how to set up a code signing hardware token.
- Start signing! You’re set to digitally sign your Windows application(s) before deployment using the code signing certificate. Learn how to digitally sign executable files using SignTool.
What It Takes to Become a Microsoft-Verified Publisher to Sign Windows Drivers
Technically, signing Windows drivers can be done with virtually any valid and publicly trusted code signing certificate. However, there are steps you’ll need to take in order to be eligible to digitally sign kernel-mode drivers.
As a verified publisher for Windows kernel-mode drivers, you must digitally sign your driver using a publicly trusted digital certificate and achieve Windows’ compatibility certification. However, not just any publicly trusted code signing certificate will do for this task; you must have an EV code signing certificate.
Save Up to 27% on an Extended Validation Code Signing Certificate
Bolster trust in your brand and meet the Windows Hardware Developer Center requirement of having an EV code signing certificate. Certificates start at $250.00/year with a 3-year purchase.
Get Verified by Microsoft
If you’re a developer who wants to create trusted Windows kernel-mode drivers, you must go above and beyond the security requirements for code signing Windows desktop apps. Why? Because Windows kernels are the small but critical software components at the core of your device. They’re what allow different hardware components to communicate.
Ensuring that drivers are as secure and authentic as possible by meeting Windows’ driver code signing requirements is vital to device and data security. This is why Microsoft created the vulnerable driver blocklist in Windows Defender to prevent drivers with known vulnerabilities from running.
To be able to meet driving signing requirements, you’ll need to do the following:
- Create accounts for the Microsoft Partner Center and Windows Hardware Developer Program to create and manage submissions for Windows Update.
- Upload at least one EV code signing certificate to the Microsoft Partner Center dashboard.
- Digitally sign a verification file using your code signing certificate and these directions from Microsoft and upload the signed file to the Partner Center for review.
Otherwise, what a user will see is an ugly warning message like this:

Image caption: A screenshot of the Windows Security warning that displays when a user attempts to install a Windows driver from an unverified publisher. Image source: Microsoft.com.
Sign Your Driver
Once that process is complete, you can start digitally signing and testing your drivers using a command line tool like SignTool, developer tool like Visual Studio, etc., and your code signing certificate.
Test Your Signed Driver’s Compatibility
Next, test the digitally signed driver. This will involve creating files for testing using one of Microsoft’s hardware compatibility certification toolkits:
- For Windows 10 drivers, you must use the Windows Hardware Lab Kit (HLK) as a test framework.
- For hardware devices and drivers for earlier device and server operating systems, you’d instead use one of the following:
- Windows Hardware Certification Kit (HCK) or, in rare cases,
- Winqual Submission Tool (WST) to create a Windows Logo Kit (WLK) hardware submission package.
Submit Your Signed and Tested Driver to Windows
Now, it’s time to send everything to the Windows Partner Center for review. Once you’ve logged into your Partner Center dashboard, you can upload the digitally signed driver package and create a new hardware submission for review. There, you also can view your hardware submissions and update them.
Why Verification Matters: Windows Will Recognize You as Known Publisher
When a user tries to install Windows software that’s been digitally signed using one of these digital certificates, one of the two following things will occur:
- They’ll see your verified digital identity information instead of a worrisome Windows Defender SmartScreen “unknown publisher” warning (as shown below).
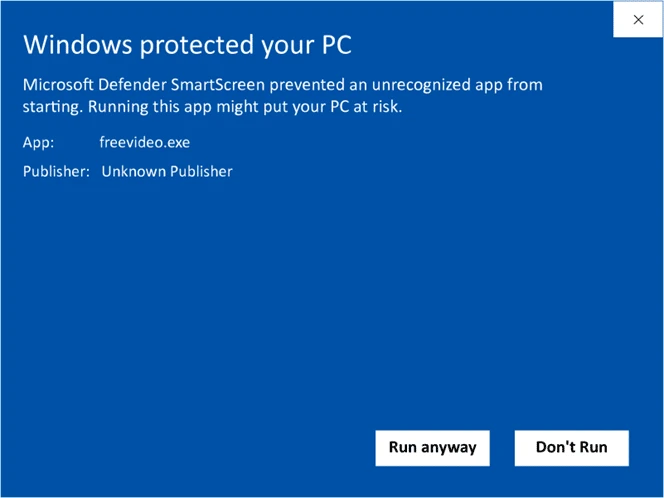
Image caption: A screenshot example of the type of warning message that displays when unsigned software triggers Windows Defender SmartScreen’s defenses.
- The SmartScreen window won’t appear at all because the software will be trusted automatically.
So, what happens if you don’t bother to sign your software? In a nutshell, the app won’t be trusted because Windows Defender doesn’t know whether you can be trusted yourself. (No one has authenticated you as a publisher.)
Whenever a Windows operating system and browser encounters an unsigned app or code, it’s set to warn users that the asset comes from an unknown source (i.e., a questionable and potentially dangerous publisher). This helps to prevent the user from facing the issues that stem from installing fraudulent and malicious programs.
So, by signing all of your Windows apps and drivers, you’re preventing these unknown publisher issues from impacting users’ ability to download and install your digital assets.
We hope you found this article informative and helpful. Need help with getting a code signing certificate so you can become a verified publisher for Microsoft Windows apps and drivers? Reach out to our Support team for assistance 24/7.


