Importance of an EV Code Signing Certificate
An extended validation code signing certificate is a Windows Hardware Developer Center requirement and helps build trust in your software over time
In early 2024, Microsoft changed how its Microsoft SmartScreen security feature interacts with extended validation code signing certificates. Although they’re still the highest-trusted certificates available, extended validation (EV) code signing certificates are no longer instantly trusted or able to remove SmartScreen warnings.
These certificates are still useful for boosting users’ confidence that they’re installing genuine software applications from trusted sources. Signing your software apps using these certificates still helps your apps build trust with Windows operating systems over time.
However, the biggest difference between standard and EV code signing certificates now is that EV certificates are still a requirement for registering for a Windows Hardware Developer Center account.
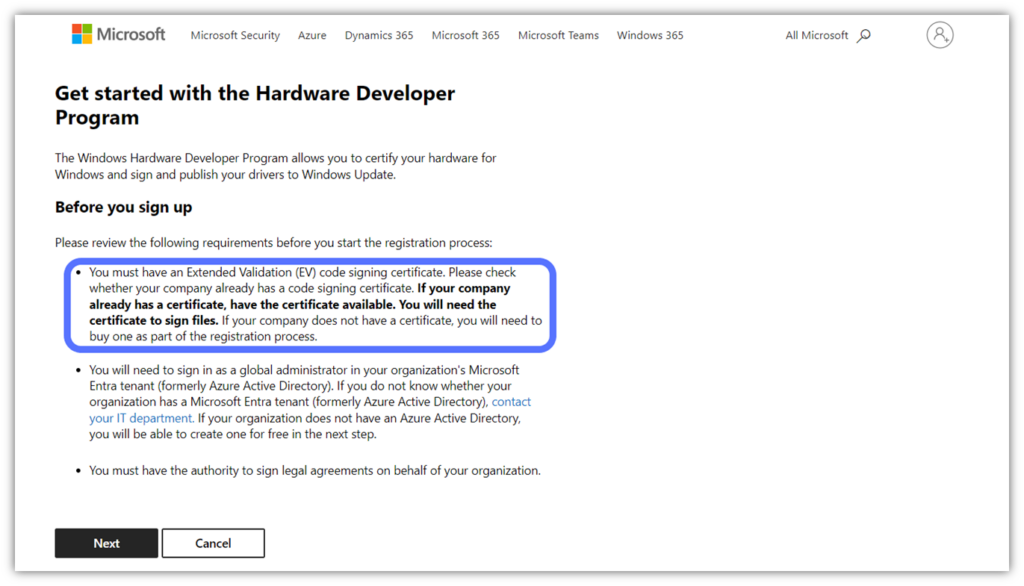
Windows Hardware Dev Program Requires an EV Certificate
If you’re someone who plans to create drivers for Windows hardware, then you must know that Windows Hardware Dev Center requires you to have an extended validation code signing certificate associated with your account. This is regardless of whether you want to use a standard code signing certificate or an EV certificate to digitally sign your drivers.
Furthermore, many kernel-mode drivers must be signed using an EV code signing certificate. The signed driver then must be uploaded to the Hardware Dev Center for Microsoft’s team to review and sign using a Microsoft CA certificate.
Save Up to 27% on an Extended Validation Code Signing Certificate
Bolster trust in your brand and meet the Windows Hardware Developer Center requirement of having an EV code signing certificate. Certificates start at $250.00/year with a 3-year purchase.
Windows Treats Signed and Unsigned Software and Drivers Differently
Whenever a software app or driver is digitally signed with a trusted code signing certificate, it indicates that:
- The software has a digital signature that’s associated with the certificate.
- The identity of the software or driver “publisher” has been verified by a publicly trusted certificate authority like Sectigo or DigiCert.
- The software is not altered, damaged, corrupted, or manipulated from its original condition. It’s safe to install and use.
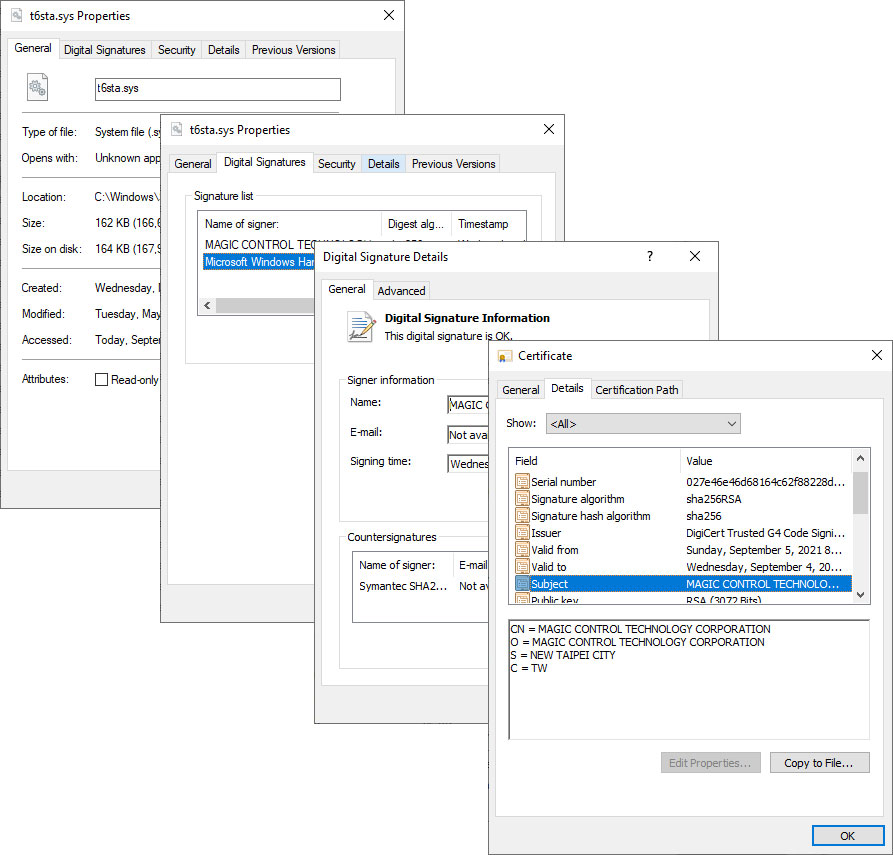
Don’t think Windows treats signed and unsigned drivers differently? Think again.
If the driver or software is not signed by a code signing certificate, or it’s been tampered with or altered in any way, then it will be treated as an unsigned file. For Windows apps, this means that Windows devices will display User Account Control (UAC) warnings whenever someone tries to install it.
The following example set of screenshots shows the difference in how digitally signed software apps (right) and unsigned apps (left) appear to users. NOTE: The screen on the right displays the same way now, regardless of whether you sign using a standard or EV code signing certificate.
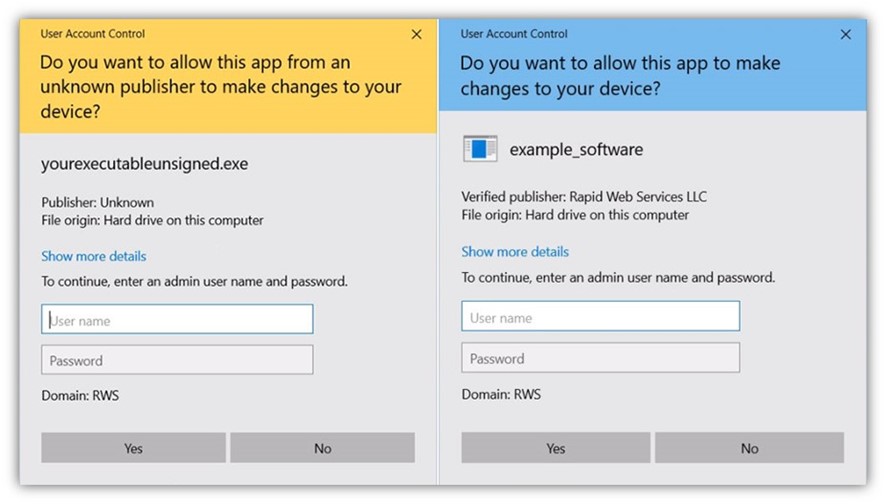
For security and safety reasons, Microsoft encourages end-users to use only digitally signed drivers and software. But what’s the alternative? Not signing your software, which leads to other serious concerns.
Unsigned Executables Put Your Products and Customers at Risk
If your software app is unsigned, there’s no way users (or their operating systems) can tell whether it’s been modified without authorization. This is worrisome when you consider that software and drivers have in-depth access to your computer system. This is usually required for software to function correctly, but it’s a huge problem if the software is malicious.
Ransomware, for example, is a malicious program that encrypts (i.e., locks) all your files and data. If you unintentionally install maliciously altered software, you’ll be in for a world of pain.
Why Use EV Code Signing Certificates in Particular?
As we mentioned previously, Microsoft changed the way its SmartScreen security feature interacts with code signing certificates. While it no longer eliminates the SmartScreen warnings, it’s still the most trusted certificate on the market.
Still trying to figure out whether to sign your software using an EV code signing certificate? It really boils down to the driver-signing and Windows Hardware Developer Center requirements.
If you’re a software developer or a publisher who hasn’t signed your software or driver, then get a signing certificate for your software to start building trust with Windows over time. In particular, if you’re a Windows driver creator, get an EV code signing certificate as it’s a requirement for setting up your Hardware Developer Program account and for signing certain types of drivers.
If you’re not a driver creator or you don’t need a Windows Hardware Dev Center account, then you can likely use a standard code signing certificate.


