How to Check a File Checksum: A Step-by-Step Guide
Say no to risky downloads! Learn how to verify the checksum of a downloaded file in 5 easy steps to ensure that the file is malware free and legitimate. Discover how comparing checksums can give you peace of mind and protect your devices from malware, data breaches and installation errors
With more than 5 billion internet users worldwide and millions of people now working remotely, downloading content has become the norm. This practice doesn’t seem like an issue until you consider the risks they pose to your business. For example, an average of 1,211 pieces of new malware variants were identified by SonicWall in 2021 alone. With this in mind, it means that the chances of downloading compromised executables and other files are now higher than ever.
To help you mitigate the chances of malware infection, we’ve previously shown you how to check if a file has a virus before downloading it and how to recognize safe download websites. But there’s more to learn. In this article, which is the second of a series of three articles on checksums, you’ll learn how to check a checksum (i.e., how to verify the checksum of a downloaded file) step by step and further secure your downloads.
What Is a Cryptographic Checksum?
A checksum is like a digital fingerprint of a file or code. It’s a calculated value made of numbers and letters used to verify the integrity of a file. One of the most common uses of checksums is confirming whether a downloaded file is corrupted or has been tampered with since it was originally created. How? This is what you’re going to learn next.
Find out more about the basic of checksum in our first article of this series “What Is a Checksum? An Easy-to-Understand Checksum Definition.”
How to Verify the Checksum of a Downloaded File in 5 Easy Steps
Some publishers provide you with their files’ checksums upfront. This means that when you go to a software vendor’s download page of a file or code, especially in the case of software packages, you’ll find a string of alphanumeric characters near the download button that looks like a load of gibberish; that’s the file’s checksum.
Let’s see how you can use it to validate files on Windows and Linux. Before we do that, it’s important to highlight that there are two ways to manually verify checksums:
- Using the built-in checksum tool available on all major operating systems.
- Using a third-party checksum calculator like Microsoft’s FCIV (File Checksum Integrity Verifier) or GtkHash.
In this guide, we’re going to use the first and more straightforward option in the Windows operating system.
1. Windows — Download the File
To show you how to verify checksum of a downloaded file, we’ll download the latest UBUNTU Mate ISO. This free, open-source operating system includes a checksum for file integrity checking purposes.
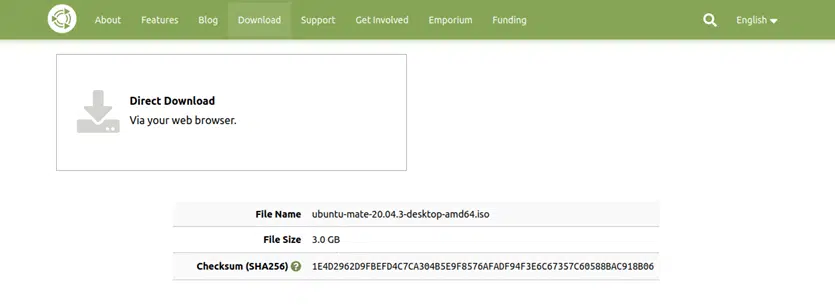
As you can see, in this case, the ISO comes with a SHA256 checksum. This means that once you’ve downloaded the image, in order to verify its integrity, you’ll have to generate the SHA-256 checksum for it.
You can find more detailed information on SHA256 and other similar cryptographic checksum algorithms in our hashing algorithms comparison article.
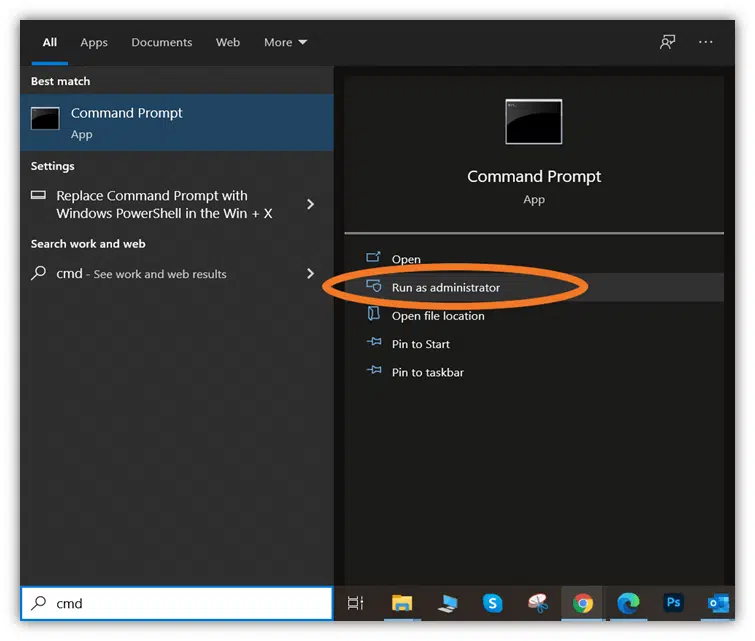
2. Open a Command Prompt
- Open the command prompt by clicking the Start button.
- Type cmd in the run bar and select Run as Administrator to launch the Command Prompt window in Admin mode.
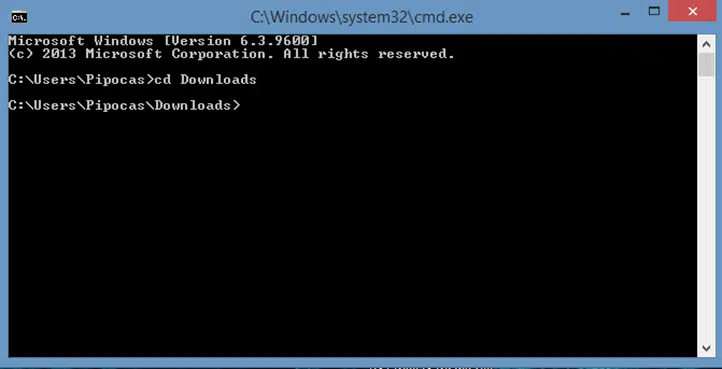
3. Go to The Directory Where the File Is Saved
Use the cd (change directory) command to navigate to the directory where you saved the downloaded ISO:
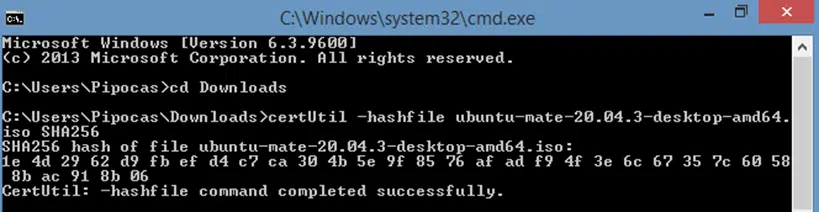
4. Type certUtil –hashfile [Filename] SHA256 to Generate the Checksum
- Type certUtil -hashfile [filename, in this case ubuntu-mate-20.04.3-desktop-amd64.iso] SHA256
- Press Enter.
This will generate the checksum. Note: An ISO is usually pretty big, so it may take some time to generate the file checksum.
5. Compare the Two Checksums
Compare the checksum displayed on the vendor’s page with the one you’ve just generated. If it matches, you’re good to go because it means that the ISO is clean and free of errors. If it doesn’t, it means the file might be corrupted or compromised. Easy right?
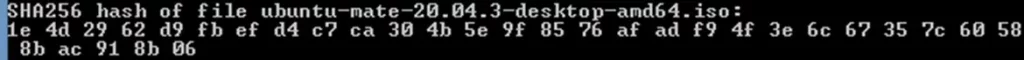
versus
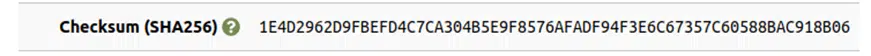
Yeah! They match.
Let’s see how it works in Linux.
1. Linux—Download the File
To simplify things and allow you to compare the two processes, we’ll use the same UBUNTU Mate ISO example.
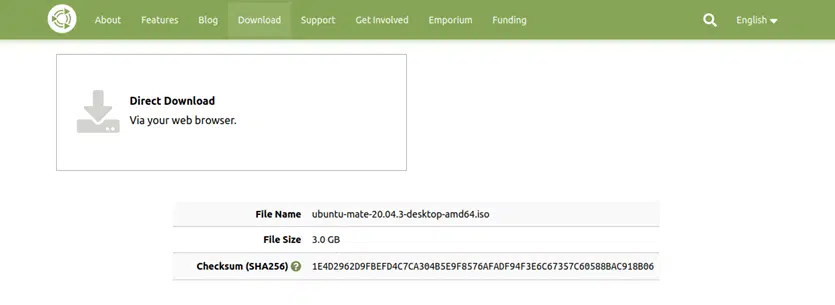
2. Open a Terminal Window
Press Ctrl+Alt+T. A terminal window will immediately pop up on your screen.
3. Go to the Directory Where the File Is Saved
Much like in the previous Windows CMD Prompt example, use the cd command to navigate to the directory where you stored the downloaded ISO. This process will look like this in Linux:
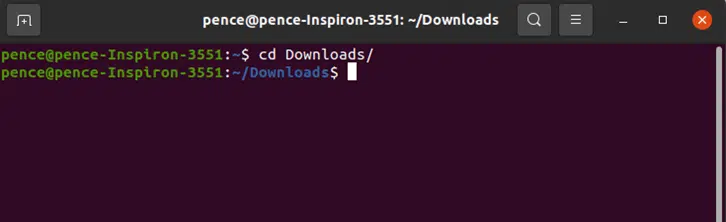
4. Type sha256sum [Filename] to Generate the Checksum
- Type sha256sum [filename] — we’re using a specific version of Ubuntu. So, in this case, you could type sha256 sum ubuntu-mate-20.04.3-desktop-amd64.iso.
- Press Enter.
This will generate the checksum:
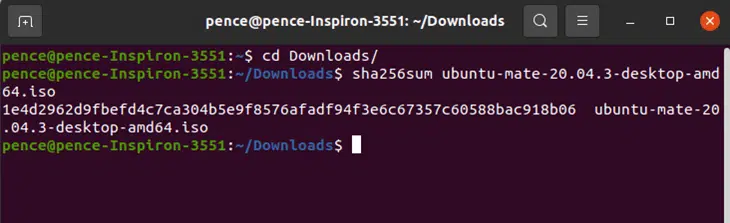
5. Compare the Two Checksums to See If They Match
It’s comparison time! You’ll now want to check the comparison on the vendor’s website against the one you generated. Does I match? If yes, you’re set because it means the ISO is unaltered and free of errors. If it doesn’t match, the file might be compromised in some way.
Let’s quickly compare your generated checksum value with the one provided on the UBUNTU Mate Download page:
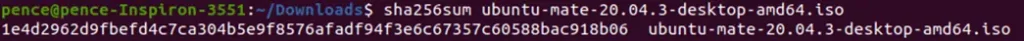
versus
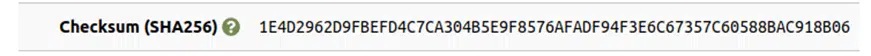
They match!
Now you’re ready to verify every file you download from those websites displaying checksums!
How Accurate Is a File Checksum?
One of the key characteristics of a checksum is that any change made to the original file, even a small one, will result in a totally different checksum algorithm. As a result, the checksum you generate for the file you download won’t match the one displayed on the publisher’s download page. This guarantees a high level of accuracy and file integrity assurance.
Final Thoughts on How to Check a File Checksum
As you can see, understanding how to check a file checksum isn’t rocket science; it’s something even users with relatively basic computer skills can manage if they know what to do. It just takes a few minutes, and it can save you from the disastrous consequences of malware infections or corrupted files installations such as data breaches.
Add the power of checksums to your download routine when possible and remember: every little thing counts in protecting the security of your device!
If you want to learn even more about how to check checksum, don’t miss our next and last article of the series. This article will serve as the ultimate step-by-step guide on how to generate an MD5 checksum to check the validity of a signed executable’s digital signature.


