Do You Want to Allow This App From an Unknown Publisher to Make Changes to Your Device?
Discover the meaning of this security message and how you can reduce its negative impact. Boost your downloads and give your customers peace of mind by confirming that your software is genuine and it’s really coming from you
It’s June 2022. Researchers at F5 Labs identify an Android malware “MaliBot” disguising as a cryptocurrency mining app and targeting banking customers. A few days later, Cleafy’s research team discovers a new malware (an Android banking Trojan they called Revive) targeting customers of a Spanish bank. The malware is installed by simply downloading a malicious two-factor authentication application.
With these kinds of news becoming the norm, it isn’t surprising if customers are becoming more careful at installing new apps. And when during the installation process, they see the following security warning pop up —
“Do you want to allow this app from an unknown publisher to make changes to your device?” —
they get even more cautious.
Let’s explore this warning message to learn all about it — from how you can confirm to your users that your app is safe to download to how to mitigate the impact of the unknown publisher message. The method we’ll discuss, code signing, gives an identity to your codes, increases your customers’ trust in your organization and software, and enhances your reputation. Why? Because digital identity matters.
What Does the Warning Message “Do You Want to Allow This App From an Unknown Publisher to Make Changes to Your Device?” Mean?
If you’re a Windows user, you must have seen this message at least once, probably more, when installing a new app or program.
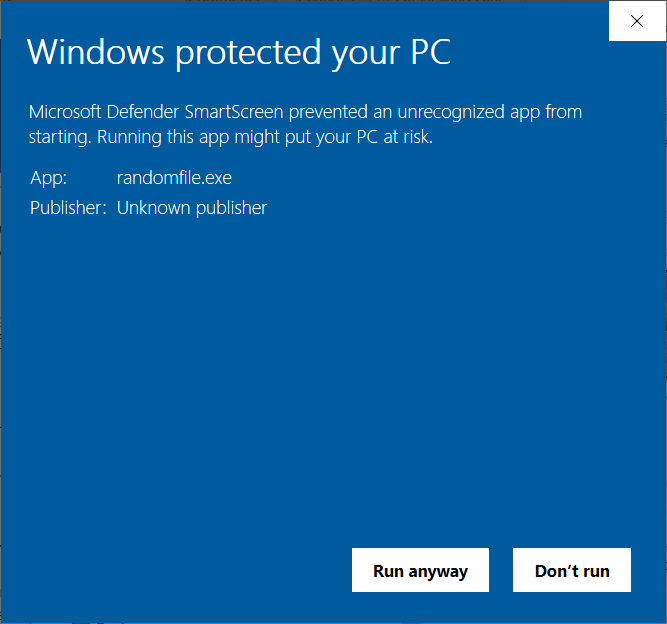
Maybe you’ve ignored it and clicked on “Run anyway” or, as a cautious user, you’ve given up on the installation and selected “Don’t Run” without asking yourself too many questions. But what does this message mean? And why is it popping up now and then?
This unknown publisher security warning is part of Microsoft Defender SmartScreen. You’ve likely seen a similar message that comes from Microsoft’s User Account Control:
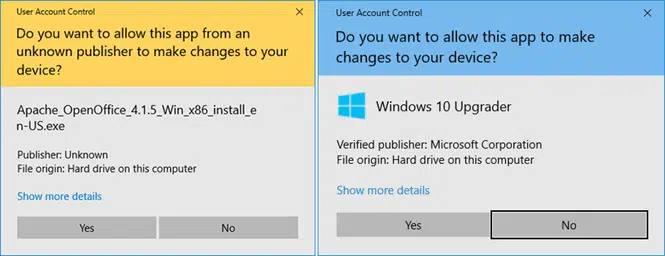
Both of these security measures help protect your device from the download of potentially malware-infected files by:
- Requesting your consent every time you attempt to perform an administrator-level task (e.g., install a new application).
- Warning you when the application or software you’re attempting to run or install is coming from an undefined (i.e., unknown) publisher.
Many customers become seriously concerned when they visualize this message, making them reluctant to install the software — and rightly so. It’s a bit like when you receive a phone call from an unknown number. It immediately sounds suspicious and puts you on alert. I don’t know you, but I never answer those calls. At the end of the day, if the caller has good intentions, why should he want to hide his identity?
The same often happens with software. So, how can you, as an organization, mitigate the impact of this security warning message? How can you show your customers that your code is safe to download and comes from a trusted source? Let’s find it out!
How Can Your Organization Mitigate This Warning? Digitally Sign Your Code
A survey conducted by Sprout Social shows that:
- 86% of Americans believe that transparency from businesses is more important than ever before.
- 73% of customers are willing to pay more for totally transparent products.
How can your software and organization be considered transparent if every time a consumer tries to download or install one, the disreputable security warning message “Do you want to allow this app from an unknown publisher to make changes to your device?” comes up? The short answer is that it can’t.
Don’t get into a flap, though. Every cloud has a silver lining, and this one has two you can choose from!
1. Use an Extended Validation (EV) Code Signing Certificate
Have you ever heard of code signing certificates? They’re digital files that developers and organizations use to digitally sign their codes (e.g., apps, executables, driver updates, patches). The certificates enable them to:
- Confirm that the program available to download is authentic and hasn’t been modified.
- Authenticate the author (e.g., organization) of the software.
They’re like the wax seal of authenticity used in Medieval Europe (and in some European countries and occasions, even now) to prove the authenticity of important, formal documents.
- A broken seal meant that the document may have been tampered with or compromised.
- An intact one confirmed to the recipient that the message inside hadn’t been altered and came from the original sender.
The digital version of a seal (i.e., a digital signature) works in much the same way. I’m not going to go into the technical mumbo jumbo this time. If you want to know more, you can discover the tech behind it by checking our article about code signing. To keep it simple, if the software or code has been signed with a valid EV code signing certificate, your Windows operating system and browser will immediately identify it as trusted.
Why? Because the EV code signing certificate provides the highest level of validation. Thus, it’ll enable your app or code to completely bypass Windows Defender SmartScreen, thanks to its rigorous check and security protocols. On top of that, it’ll also increase the security of your software and codes by allowing your developers to use two-factor authentication to sign the software (i.e., the private key is stored externally using a hardware token like a USB).
Cool, huh? And getting one isn’t even too complicated:
1. Purchase your EV code signing certificate. Place your order with a trusted certificate authority (CA) and provide them with all the information needed for the background check. This is necessary to confirm that your organization is authentic and can be trusted.
2. Get your identity verified. The CA will run some specific and detailed background checks before issuing your certificate. This way your customers will be able to verify your organization’s details every time they want to download something developed by you without worries.
3. Get your EV code signing certificate from the issuing CA. Have you received your new certificate on your hardware security token? Great! Now you’re ready to rock and roll with code signing.
4. Sign your applications and say goodbye to the security warning, “Do you want to allow this app from an unknown publisher to make changes to your device?” It’s done! Add your digital signature to your codes and apps and take your software security to the next level with the Windows Defender SmartScreen warning mitigation by helping your software be automatically trusted by Windows browsers and operating systems.
At this point, I can see the next question coming: “Is it expensive?” Well, it’s important to know that, due to the enhanced security and meticulous background check required for extended validation(you know, being the “Ferrari” of the code signing certificate), buying an EV code signing certificate will cost you a bit of money. With so much malware around and your reputation at stake, money spent on security is always well spent.
Are you a startup, small business, or independent developer publishing and selling small apps? Is money tight? Don’t despair! Do you remember when we said at the beginning of this chapter that there are two silver linings? The second one is exactly made for those like you who can’t afford the Ferrari but still want to digitally sign your software (thus providing your customers with a certain level of security and trust).
2. Use an Organizational Validation (OV) Code Signing Certificate
Much cheaper than the previously mentioned EV certificate, the OV code signing certificate is the city car of code signing certificates. Affordable, offering all the basic key features, yet still secure and reliable.
To get it, you’ll also have to go through a (less elaborate) background check by a globally recognized CA to:
- Confirm the owner of the domain linked to your organization, and
- Confirm that your company is legal and exists.
How does it differ from the EV code signing certificate? While it’ll also offer more security to your customers, allowing them to view a few details about your organization, it has a few fundamentals differences:
- It doesn’t get rid of Windows Defender SmartScreen’s unknown publisher warning message. You know what they say: you get what you pay for. With the OV certificate, you won’t get rid of the unknown publisher pop-up. However, it’ll allow your verified organizational information to display in the Windows User Account Control (UAC) pop-up and greatly reduce security warning messages. This will give your users a way to check that the software or code they’re downloading it’s really coming from you. Once your software has been downloaded enough times to become sufficiently popular with Windows Defender SmartScreen, then it’ll be classified as well known and Windows may remove the warning.
- It doesn’t use two-factor authentication (currently). When the code is signed, the certificate is stored on an encrypted file on a computer like Secure Socket Layer/Transport Layer Security (SSL/TLS) certificates. The same encrypted file can be used to sign executables and codes on any other device. NOTE: There are changings coming down from the CA/Browser Forum (i.e., the CA/B Forum, which is the industry’s regulatory body). Starting in November, , OV code signing certificates will be issued on hardware security tokens in much the same way as EV code signing certificates are now).
- It can’t be used to sign Windows 10 kernel-mode drivers. This is one of the reasons why small businesses and single individuals predominantly use this kind of certificate. Are you developing drivers for previous versions of Windows? No worries then, it’ll work just fine.
- It can be issued to individuals and organizations. While the EV certificate can only be issued to organizations, OV certificates can also be released to a single individual without a registered business. This is just sometimes known as an individual validation (IV) code signing certificate.
This doesn’t sound too bad, right? It’s cheaper, offers basic functionalities, and it does exactly what it says on the tin: your customers will be able to confirm that your company is trustworthy and check that your codes haven’t been tampered with. All this with a reduced number of ugly warnings that may scare away customers.
So, now you have two ways to minimize the impact of the “Do you want to allow this app from an unknown publisher to make changes to your device?” warning message. All you have to do now is to pick your preferred method, order your certificate, and you’re done! Still unsure? Check out our EV and OV certificates comparison table.
Final Thoughts on “Do You Want to Allow This App From an Unknown Publisher to Make Changes to Your Device?”
No matter if you choose to go with the more comprehensive EV signing certificate or the standard OV one, digitally signing your software and apps will enable you to show your customers your commitment to security.
Invest in code signing certificates to protect your code integrity and reputation, boost your downloads, and assert your organization’s digital identity to increase the trust in your brand.
From now on, secure your codes with a signing certificate. This way, your customers will never be asked again: “Do You Want to Allow This App From An Unknown Publisher to Make Changes to Your Device?”


