Sectigo + Google Cloud KMS Code Signing

Sectigo Code Signing Certificates can now be stored in Google Cloud Key Management Service (KSM) to support cloud-based code signing
If your organization uses Google Cloud and has developers signing remotely or in the cloud, we have great news: Google Cloud Key Management Service (Cloud KMS) now integrates seamlessly with Sectigo code signing certificates.
Why use Google Cloud KSM with Sectigo? To avoid the limitations and hassles of secure USB hardware. Since June 2023, all publicly trusted code signing certificates must be generated and stored on secure hardware. This means that many developers have to manage one or more secure hardware tokens, which can be an annoyance for any business, let alone those with employees working in different geographic locations or using cloud-based DevOps systems.
Get to Know Google Cloud Key Management Service
Google Cloud KMS is a secrets storage solution that allows you to securely generate, store, and manage your public and private cryptographic keys for use in compatible services and applications. In short, organizations can digitally sign scripts, apps, and other workloads in cloud environments while simultaneously improving security and devops efficiency.
It’s a win-win for your organization’s security (and the sanity of your developers): no muss, no fuss, and no more having to track down and manage your company’s hardware tokens.
Google Cloud KMS + Sectigo = A Power Play in Software Security
Google Cloud Key Management Service now supports Sectigo code signing certificates.
With Google Cloud KMS, you can securely generate your certificate(s) cryptographic keys using Google’s fully managed FIPS 140-2 3-compliant hardware security modules (HSMs). This means you get to enjoy the benefits of a secure HSM without the hassle of managing on-prem appliances.
This key management service offers reassurance that your secrets remain secure and won’t be compromised while:
- integrating with your Google Cloud account and specified (enabled) projects.
- enabling your remote developers to sign software apps without requiring direct access to your signing keys.
- streamlining your key management tasks by allowing you to store and manage groups of keys (keyrings) simultaneously and organize them by work environment (e.g., testing, staging, and production).
Now, pair this with a Sectigo Code Signing Certificate and you’ll be golden. Sectigo, formerly Comodo CA, is a trusted name within web and software security communities.
Get Familiar with Google Cloud KMS Code Signing to See If It’s the Right Fit
Want to get a better idea of all that’s involved? Be sure to check out our guide on How to Use Google KMS With a Sectigo Code Signing Certificate, as you’ll need to set up several resources inside Google Cloud and delegate permissions.
The process can be a bit advanced, so it’s helpful if you’re already familiar with Google Cloud.
How to Start Signing in the Cloud with a Sectigo Code Signing Certificate
When purchasing a Sectigo Code Signing Certificate to use with Google Cloud KMS, be sure to select the Install on Existing HSM option when adding it to your cart. (You’ll have the ability to choose your specific HSM type momentarily.)
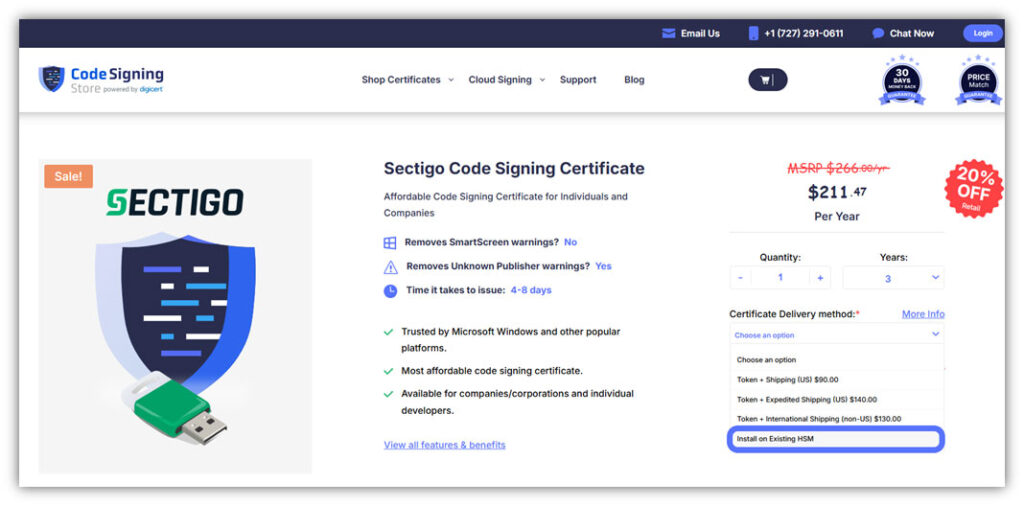
Once you complete your order, you’ll quickly move through another guided process on CertificateGeneration.com.
Choose Google Cloud KMS as Your Existing HSM Type
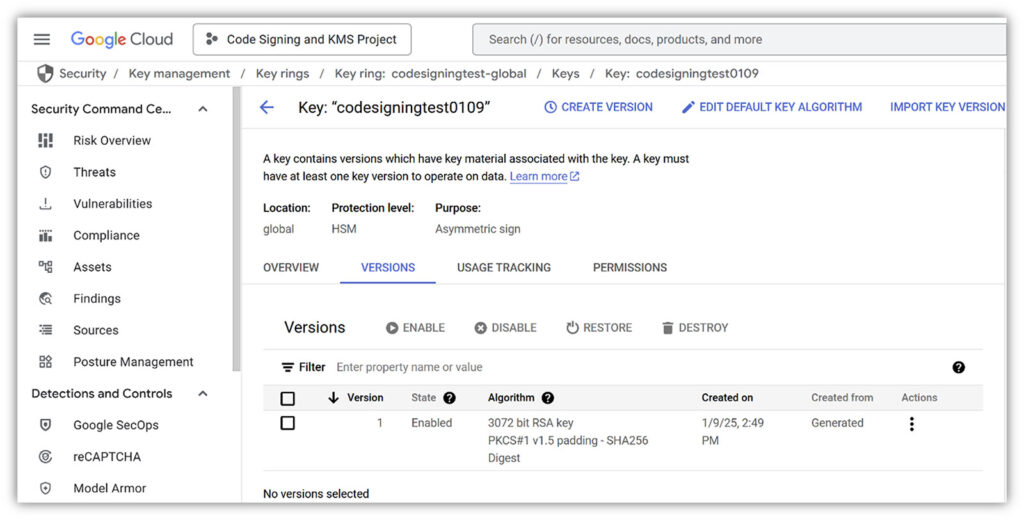
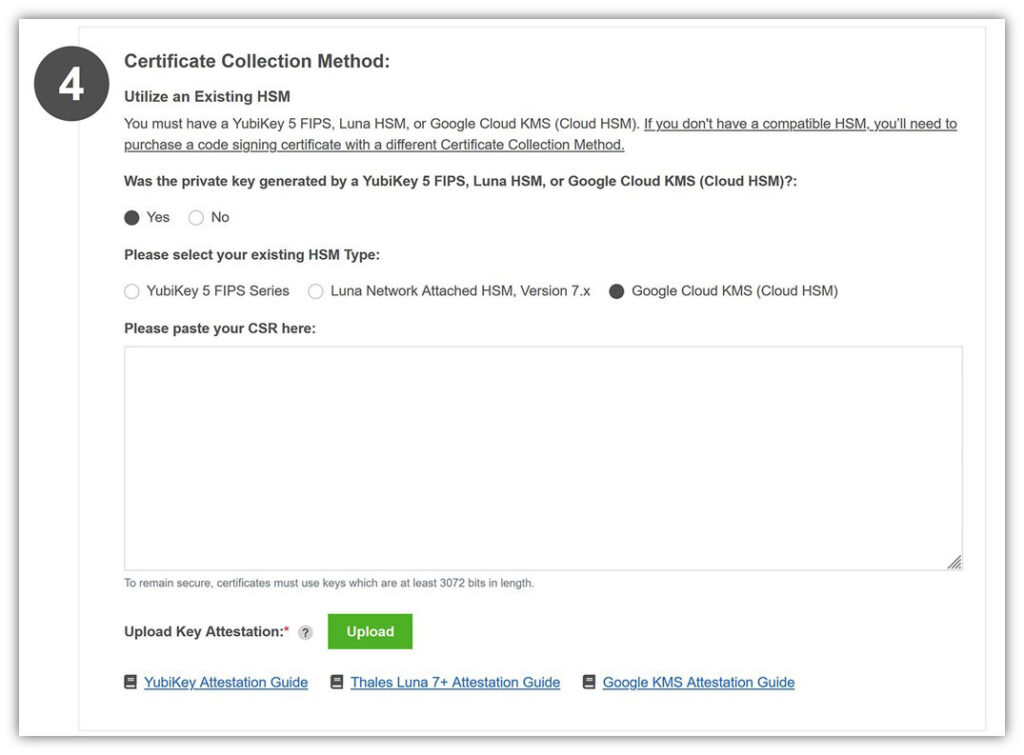
In Step 4, be sure to select Google Cloud KMS (Cloud HSM) as the Certificate Collection Method. This enables your key to be generated and stored on Cloud Cloud’s secure HSM in compliance with the code signing industry’s security baseline requirements.
Follow our guide to generate the CSR and download the key attestation in Google Cloud.
Google Cloud KMS is one of the alternative code signing certificate delivery methods you can choose from when getting a certificate from CodeSigningStore.com.


