‘SignTool Error: A Certificate Chain Processed, But Terminated in a Root Certificate Which Is Not Trusted by the Trust Provider’

Is your newly signed code displaying a warning that says it’s not trusted? Here’s how to identify the issue and what you can do to fix it
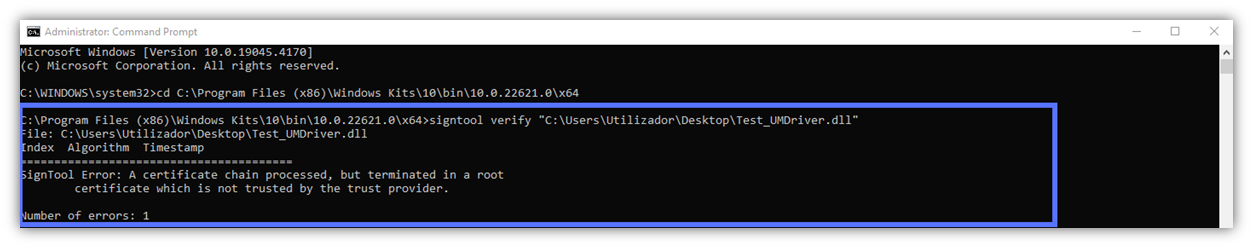
“A certificate chain processed but terminated in a root certificate which is not trusted by the trust provider.”
Did you try to verify the signature of a Windows file with SignTool.exe before releasing it to the public and wind up receiving the following error message?
The certificate hierarchy, also known as a “chain of trust” or “trust chain,” serves as the foundation of trust for your code signing certificate (and, by extension, your software). This chain of certificates provides assurance to software users that your software is authentic and hasn’t been modified by any unauthorized third parties.
Fear not. We’ll help you rectify the situation so that you can deploy your code on time.
Editor’s Note: This article is one in a series of pieces we will publish over the next few weeks that aim to help resolve code signing-related errors for SignTool, Jarsigner, Electron, and Windows.
What ‘SignTool Error: A Certificate Chain Processed, But Terminated in a Root Certificate Which Is Not Trusted by the Trust Provider’ Means
The code you are verifying has been signed. However, the root certificate included in the certificate chain isn’t trusted.
Possible Cause(s)
- The verify command typed in the CMD is incorrect. Thus, SignTool based the verification on the Windows Driver Verification Policy. Try using this instead: signtool verify file_example.exe. (NOTE: SignTool doesn’t require a hyphen [-] in front of verify.)
- The code has been signed with a self-signed certificate. Self-signed certificates are untrusted, so they’re going to always populate errors when you try to use them in external use cases.
How to Fix It
- Add /pa to the command. This way, SignTool will use the correct verification policy (i.e., Windows Default Authentication Verification Policy) to ensure that Microsoft’s Authenticode verification conditions have been met.
signtool verify /pa file_example.exe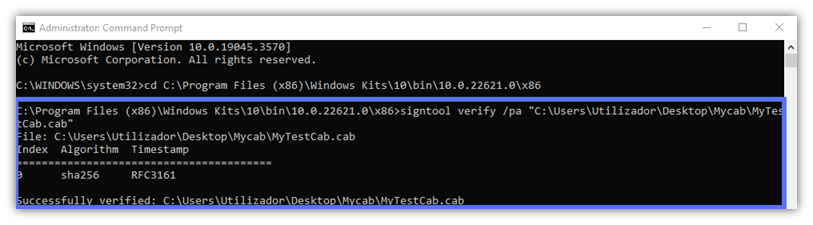
- Re-sign the code using a trusted code signing certificate. This is a publicly trusted certificate (i.e., not a self-signed certificate) that you got from a third-party CA or an authorized reseller such as CodeSigningStore.com.
Save Up to 45% on a GoGetSSL Cloud Code Signing Certificate
Digitally sign up to 1,000 signing without having to manage a physical USB token for as little as $372.69/year.
Platform(s)/Systems Affected
SignTool.exe (Windows, Visual Studio Developer Command Prompt, Visual Studio Developer PowerShell).


