Digital Identity Helps You Stay Safe on the Web
Whenever people think about digital identity in terms of online security, their thought process typically revolves around ways to protect your own digital identity. And that makes sense considering that it’s crucial for everyone — kids, teens, and adults alike — to protect their digital identities online.
However, when talking about digital identity throughout this guide, we’re going to take a bit of a different approach and focus on the other side of the coin. We’re going to focus on ways you can help your kids and teens determine the digital identities of the people or organizations they engage with online. This is a critical skill to avoid getting duped online by a cybercriminal, bully, or other unfriendly person.
Basically, what this means is we’ll talk about:
- Ways to identify legitimate websites,
- Ways you can determine whether a social media profile is real or fake,
- How to determine whether an email is legitimate or a trap, and
- How you can tell whether you’re downloading a legitimate application.
But before we can cover all of those things — many of which will be covered in the “How Tos” of Internet Safety section of the article — we first need to break down what digital identity is.
What Is Digital Identity?
While it sounds like the alter ego of superheroes, “digital identity” is actually a term that refers to info, features or characteristics that can uniquely identify you, another person, a business or an organization online.
It’s way too easy for cybercriminals to pretend to be someone else online. You can use digital identity to identify who you’re actually interacting with… before they get the chance to scam you.
Digital identity examples include things such as:
- IP addresses.
- Verified organizational information (such as verified addresses, company names, phone numbers).
- Biometrics (such as fingerprints, facial scans, and retinal scans).
- Multi-factor authentication:
- Something you know (such as a PIN or password),
- Something you have (such as a security token or a cell phone), or
- Something you are (such as a biometric).
- Public and private keys (for online communications and other data).
- Digital signatures.
- Website Whois/ Registry Directory Service (RDS) data — what name, address, phone number, email address, etc. that a domain is registered to.
- Email addresses.
- Website trust seals.
Check the website address for typos and spelling errors. These are
common among international scammers.
Why Being Able to Determine Someone’s Digital Identity Matters
The reason why understanding someone’s digital identity is so important is that it can help you and your kids/teens stay safe online. If you and your kids can differentiate real people and companies from fake ones, you’ll be less likely to fall for their scams.
When you verify the digital identities of other users and companies, you’re ensuring that you only provide your personal or financial information to legitimate companies and organizations that are trustworthy and reputable. Basically, you’re not sending your information to a random stranger or cybercriminal who can use it to commit identity fraud and other crimes.
And if your kids can identify whether the friend requests they receive on their favorite social media platform are legitimate, it can help them stay out of reach of sexual predators, identity thieves, and other cybercriminals.

Ways to Identify Digital Identity
There are a few different ways that you can determine digital identity depending on the platform or communication channel. Here are a few of the ways you can do so:
- Look for verified info about the person/organization. For example, I can easily create a social media profile with the name “Barack Obama” and a photo of Obama. But that doesn’t mean I’m actually Obama. Don’t ever trust unverified websites and profiles of celebrities and companies.
- Look out for glaring spelling & grammar issues. Check the website address for typos and spelling errors. These are common among international scammers. Legitimate businesses take the time to proofread their messages and content before publishing it in an email or on a website. (Yes, accidents happen, and even big corporations make mistakes. But scams are known for containing glaringly obvious grammar, spelling, and punctuation errors.)
- Check the site’s security certificate. Look for the website’s SSL/TLS certificate and see if it lists any organizational information. (We’ll show you how to do that in the “How-Tos” of Internet Safety section.)
- Look for website trust seals. These badges are a way to learn more about the organization that owns a website. It can help you to determine whether it’s real or fake.
- Double-check email addresses and domains. The name and email address of the sender should match. For example, if an email claims to be from an official Netflix account but the email address is something like “[email protected],” it’s a red flag. Carefully check email addresses to ensure they match entirely and aren’t off by one letter or number.
- Check for email signing information. Although not all businesses use them, email signing certificates add an additional layer of security and validation through the use of encryption and digital signatures. We’ll tell you more about those in the “How-Tos” of Internet Safety section.
- Look for verified publisher info. When downloading software on your computer, check to see if the app or software program has a verified publisher.
- Check for an email signing certificate — look to see if the email has been digitally signed by an email signing certificate. Although this isn’t common for emails from individuals, some businesses sign their emails using these digital certificates to prove their identities.
- Review the URL in embedded links — Carefully check the domains of any embedded links or buttons that the email includes before clicking on them. If the URL doesn’t match the site it’s claiming to be from, do not click on it!
Why You Should Never Trust an Unverified Identity
If a stranger walks up to you on the street and demands that you tell them your name and where you live, you wouldn’t give that information to them, right? It’s too dangerous and could result in you becoming the victim of a crime.
But the truth of the matter is that if you’re logging into an account or making a purchase on a fake website, you’re doing precisely that. This is why it’s important to teach kids and teens to take the same careful approach when it comes to providing their personal or financial information online.
You see, cybercriminals love to create fake websites that look legitimate. They use these sites to trick or manipulate people into providing their information, thinking that they’re logging into or buying from the real website. So, if you receive an email from, say, “Netflix” telling you that your account is locked and you have to log in to fix it using a link they provide, there are several steps you should take before you ever consider clicking on the link.
No site is safe from phishing scams and impersonations. For example, the Federal Trade Commission (FTC) was spoofed in a scam as recently as January 2021. In this scam, one or more cybercriminals, representing themselves as the “U.S. Trading Commission,” promoted a fraudulent “Official Personal Data Protection Fund” that promised to compensate people for their data that got leaked in various cyber incidents.

The goal of the scam was to get users to provide their personal, banking or their electronic wallet information so they could “instantly receive” a cash payment. However, like with many other cyber scams, what ended up happening instead was people got scammed out of their money and ended up paying the cybercriminals.
The Line of Death
Historically, the idea has been that only browsers could control the information in the top part of the browser window and everything below a specific point was controlled by the website owner. Everything below a certain point — known as the “line of death” — is simply untrustworthy.

However, as it turns out, cybercriminals have a lot more control of that information than people often initially realize. You see, there is information above that line that site owners can fake as well using techniques such as fake domain addresses that are designed to look like legitimate.
Let’s consider an example of how to differentiate real websites from fake one — and by “fake,” I mean illegitimate or fraudulent — in this next section.
Real vs Fake Websites
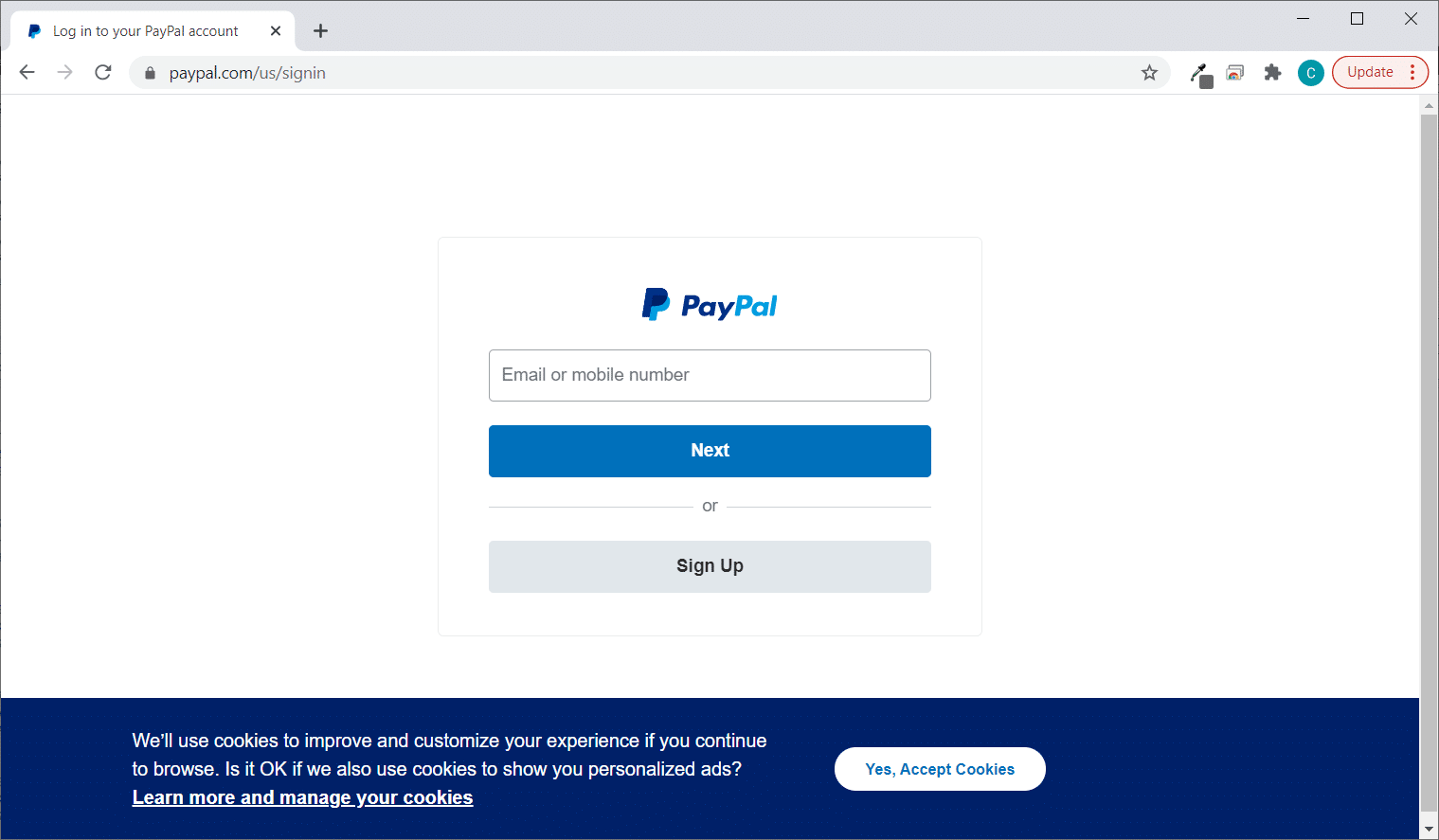
Let’s first take a look at the URL of the real PayPal website:
Now, let’s take a look at an example of a fake PayPal login site:
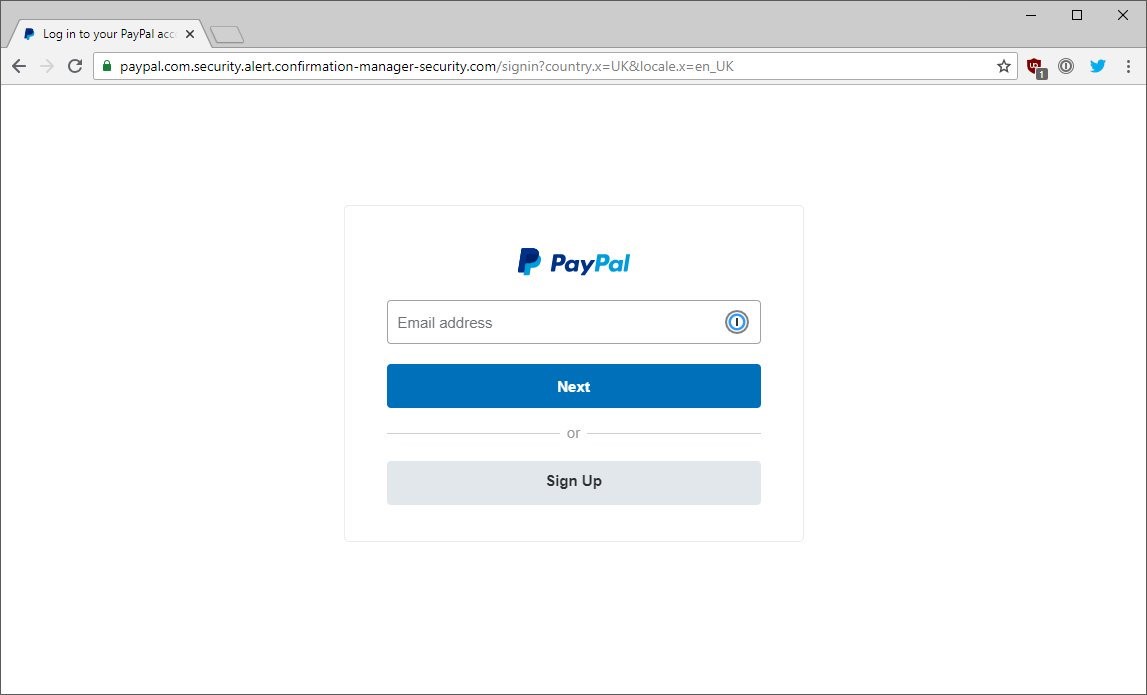
Here, you’ll see that the login form looks almost identical to the legitimate PayPal sign-in page. So, how can you tell the two screenshots apart? Look at the web address bar. In the first image, you’ll see that the website address paypal.com/us/signin is very straightforward and easy to read. The domain (paypal.com) is followed by the file path (/us/signin).
In the second screenshot, the URL is less straight-forward and a lot trickier — but it’s that way by design. The goal here is to trick users into thinking the site is legitimate when it’s not. People will see the “paypal.com” at the beginning and stop reading after that. However, if you keep reading and see all of the information that follows, you’ll realize just how big a fake it is. For example:
- The domain name is confirmation-manager-security.com.
- The “paypal.com” part is actually a combination of the fourth- and third-level subdomains.
Don’t worry, we’ll talk more about the different parts of a URL a little later in the “How to Browse the Web Safely” section. There, we’ll also cover other ways to determine an organization’s digital identity and things your kids and teens can do to stay safe while browsing the internet.


